Packetbeat quick start: installation and configuration
editPacketbeat quick start: installation and configuration
editThe best way to understand the value of a network packet analytics system like Packetbeat is to try it on your own traffic.
This guide describes how to get started quickly with network packets analytics. You’ll learn how to:
- install Packetbeat on each system you want to monitor
- specify the network devices and protocols to sniff
- parse the packet data into fields and send it to Elasticsearch
- visualize the packet data in Kibana
Before you begin
edit-
You need Elasticsearch for storing and searching your data, and Kibana for visualizing and managing it.
To get started quickly, spin up a deployment of our hosted Elasticsearch Service. The Elasticsearch Service is available on AWS, GCP, and Azure. Try it out for free.
-
On most platforms, Packetbeat requires the libpcap packet capture library. Depending on your OS, you might need to install it:
sudo apt-get install libpcap0.8
sudo yum install libpcap
You probably do not need to install libpcap.
You probably do not need to install libpcap.
You probably do not need to install libpcap.
Download and install a packet sniffing library, such as Npcap, that implements the libpcap interfaces.
If you use Npcap, make sure you install it in WinPcap API-compatible mode. If you plan to capture traffic from the loopback device (127.0.0.1 traffic), also select the option to support loopback traffic.
Step 1: Install Packetbeat
editYou can install Packetbeat on dedicated servers, getting the traffic from mirror ports or tap devices, or you can install it on your existing application servers.
To download and install Packetbeat, use the commands that work with your system:
curl -L -O https://artifacts.elastic.co/downloads/beats/packetbeat/packetbeat-7.10.2-amd64.deb sudo dpkg -i packetbeat-7.10.2-amd64.deb
curl -L -O https://artifacts.elastic.co/downloads/beats/packetbeat/packetbeat-7.10.2-x86_64.rpm sudo rpm -vi packetbeat-7.10.2-x86_64.rpm
curl -L -O https://artifacts.elastic.co/downloads/beats/packetbeat/packetbeat-7.10.2-darwin-x86_64.tar.gz tar xzvf packetbeat-7.10.2-darwin-x86_64.tar.gz
brew tap elastic/tap brew install elastic/tap/packetbeat-full
This command installs the most recently released default distribution of
Packetbeat. To install the OSS distribution, specify
elastic/tap/packetbeat-oss.
curl -L -O https://artifacts.elastic.co/downloads/beats/packetbeat/packetbeat-7.10.2-linux-x86_64.tar.gz tar xzvf packetbeat-7.10.2-linux-x86_64.tar.gz
- Download the Packetbeat Windows zip file from the downloads page.
-
Extract the contents of the zip file into
C:\Program Files. -
Rename the
packetbeat-<version>-windowsdirectory toPacketbeat. - Open a PowerShell prompt as an Administrator (right-click the PowerShell icon and select Run As Administrator).
-
From the PowerShell prompt, run the following commands to install Packetbeat as a Windows service:
PS > cd 'C:\Program Files\Packetbeat' PS C:\Program Files\Packetbeat> .\install-service-packetbeat.ps1
If script execution is disabled on your system, you need to set the
execution policy for the current session to allow the script to run. For
example:
PowerShell.exe -ExecutionPolicy UnRestricted -File .\install-service-packetbeat.ps1.
Other installation options
editStep 2: Connect to the Elastic Stack
editConnections to Elasticsearch and Kibana are required to set up Packetbeat.
Set the connection information in packetbeat.yml. To locate this
configuration file, see Directory layout.
Specify the cloud.id of your Elasticsearch Service, and set cloud.auth to a user who is authorized to set up Packetbeat. For example:
cloud.id: "staging:dXMtZWFzdC0xLmF3cy5mb3VuZC5pbyRjZWM2ZjI2MWE3NGJmMjRjZTMzYmI4ODExYjg0Mjk0ZiRjNmMyY2E2ZDA0MjI0OWFmMGNjN2Q3YTllOTYyNTc0Mw==" cloud.auth: "packetbeat_setup:YOUR_PASSWORD"
|
This examples shows a hard-coded password, but you should store sensitive values in the secrets keystore. |
-
Set the host and port where Packetbeat can find the Elasticsearch installation, and set the username and password of a user who is authorized to set up Packetbeat. For example:
output.elasticsearch: hosts: ["myEShost:9200"] username: "packetbeat_internal" password: "YOUR_PASSWORD"
This examples shows a hard-coded password, but you should store sensitive values in the secrets keystore.
-
If you plan to use our pre-built Kibana dashboards, configure the Kibana endpoint. Skip this step if Kibana is running on the same host as Elasticsearch.
The hostname and port of the machine where Kibana is running, for example,
mykibanahost:5601. If you specify a path after the port number, include the scheme and port:http://mykibanahost:5601/path.The
usernameandpasswordsettings for Kibana are optional. If you don’t specify credentials for Kibana, Packetbeat uses theusernameandpasswordspecified for the Elasticsearch output.To use the pre-built Kibana dashboards, this user must be authorized to view dashboards or have the
kibana_adminbuilt-in role.
To learn more about required roles and privileges, see Grant users access to secured resources.
You can send data to other outputs, such as Logstash, but that requires additional configuration and setup.
Step 3: Configure sniffing
editIn packetbeat.yml, configure the network devices and protocols to
capture traffic from.
-
Set the sniffer type. By default, Packetbeat uses
pcap, which uses the libpcap library and works on most platforms.On Linux, set the sniffer type to
af_packetto use memory-mapped sniffing. This option is faster than libpcap and doesn’t require a kernel module, but it’s Linux-specific:packetbeat.interfaces.type: af_packet
-
Specify the network device to capture traffic from. For example:
packetbeat.interfaces.device: eth0
On Linux, specify
packetbeat.interfaces.device: anyto capture all messages sent or received by the server where Packetbeat is installed. Theanysetting does not work on macOS.To see a list of available devices, run:
packetbeat devices
packetbeat devices
./packetbeat devices
packetbeat devices
./packetbeat devices
PS C:\Program Files\Packetbeat> .\packetbeat.exe devices 0: \Device\NPF_{113535AD-934A-452E-8D5F-3004797DE286} (Intel(R) PRO/1000 MT Desktop Adapter)In this example, there’s only one network card, with the index 0, installed on the system. If there are multiple network cards, remember the index of the device you want to use for capturing the traffic.
Modify the
devicesetting to point to the index of the device:packetbeat.interfaces.device: 0
For more information about these settings, see Traffic sniffing.
-
In the
protocolssection, configure the ports where Packetbeat can find each protocol. If you use any non-standard ports, add them here. Otherwise, use the default values.packetbeat.protocols: - type: dhcpv4 ports: [67, 68] - type: dns ports: [53] - type: http ports: [80, 8080, 8081, 5000, 8002] - type: memcache ports: [11211] - type: mysql ports: [3306,3307] - type: pgsql ports: [5432] - type: redis ports: [6379] - type: thrift ports: [9090] - type: mongodb ports: [27017] - type: cassandra ports: [9042] - type: tls ports: [443, 993, 995, 5223, 8443, 8883, 9243]
To test your configuration file, change to the directory where the
Packetbeat binary is installed, and run Packetbeat in the foreground with
the following options specified: sudo ./packetbeat test config -e. Make sure
your config files are in the path expected by Packetbeat (see
Directory layout), or use the -c flag to specify the path to the config
file. Depending on your OS, you might run into file ownership issues when you
run this test. See
Config File Ownership and Permissions
for more information.
For more information about configuring Packetbeat, also see:
- Configure Packetbeat
- Config file format
-
packetbeat.reference.yml: This reference configuration file shows all non-deprecated options. You’ll find it in the same location aspacketbeat.yml.
Step 4: Set up assets
editPacketbeat comes with predefined assets for parsing, indexing, and visualizing your data. To load these assets:
-
Make sure the user specified in
packetbeat.ymlis authorized to set up Packetbeat. -
From the installation directory, run:
packetbeat setup -e
packetbeat setup -e
./packetbeat setup -e
packetbeat setup -e
./packetbeat setup -e
PS > .\packetbeat.exe setup -e
-eis optional and sends output to standard error instead of the configured log output.
This step loads the recommended index template for writing to Elasticsearch and deploys the sample dashboards for visualizing the data in Kibana.
A connection to Elasticsearch (or Elasticsearch Service) is required to set up the initial environment. If you’re using a different output, such as Logstash, see Load the index template manually and Load Kibana dashboards.
Step 5: Start Packetbeat
editBefore starting Packetbeat, modify the user credentials in
packetbeat.yml and specify a user who is
authorized to publish events.
To start Packetbeat, run:
sudo service packetbeat start
If you use an init.d script to start Packetbeat, you can’t specify command
line flags (see Command reference). To specify flags, start Packetbeat in
the foreground.
Also see Packetbeat and systemd.
sudo service packetbeat start
If you use an init.d script to start Packetbeat, you can’t specify command
line flags (see Command reference). To specify flags, start Packetbeat in
the foreground.
Also see Packetbeat and systemd.
|
You’ll be running Packetbeat as root, so you need to change ownership
of the configuration file, or run Packetbeat with |
To have launchd start elastic/tap/packetbeat and then restart it at login,
run:
brew services start elastic/tap/packetbeat-full
To run Packetbeat in the foreground instead of running it as a background service, run:
|
You’ll be running Packetbeat as root, so you need to change ownership
of the configuration file, or run Packetbeat with |
|
You’ll be running Packetbeat as root, so you need to change ownership
of the configuration file, or run Packetbeat with |
PS C:\Program Files\packetbeat> Start-Service packetbeat
By default, Windows log files are stored in C:\ProgramData\packetbeat\Logs.
Packetbeat should begin streaming data to Elasticsearch.
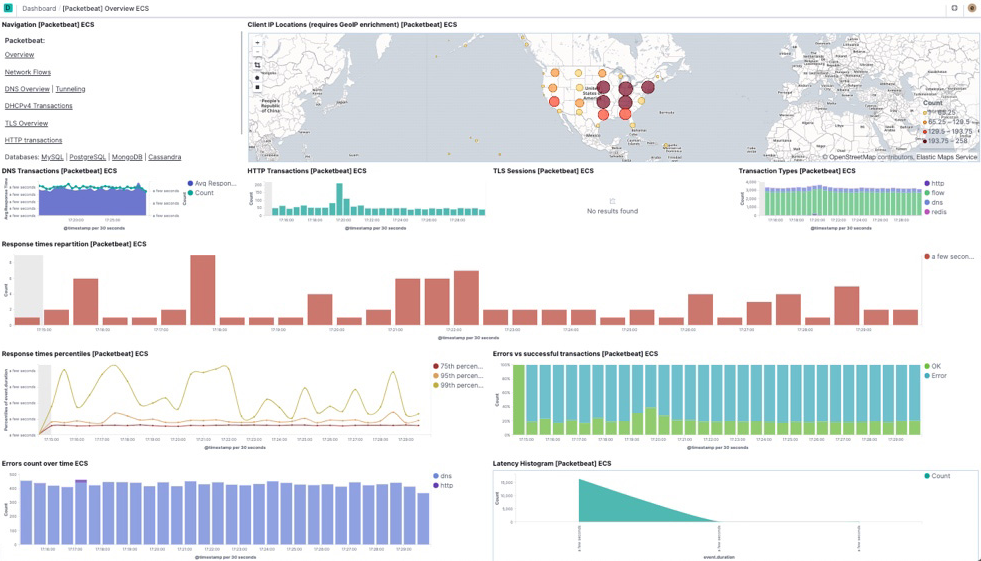
Step 6: View your data in Kibana
editPacketbeat comes with pre-built Kibana dashboards and UIs for visualizing log
data. You loaded the dashboards earlier when you ran the setup command.
To open the dashboards:
-
Launch Kibana:
- Log in to your Elastic Cloud account.
- Navigate to the Kibana endpoint in your deployment.
Point your browser to http://localhost:5601, replacing
localhostwith the name of the Kibana host. -
In the side navigation, click Discover. To see Packetbeat data, make sure the predefined
packetbeat-*index pattern is selected.If you don’t see data in Kibana, try changing the time filter to a larger range. By default, Kibana shows the last 15 minutes.
- In the side navigation, click Dashboard, then select the dashboard that you want to open.
The dashboards are provided as examples. We recommend that you customize them to meet your needs.
To populate the client locations map in the overview dashboard, follow the steps described in Enrich events with geoIP information.
What’s next?
editNow that you have your data streaming into Elasticsearch, learn how to unify your logs, metrics, uptime, and application performance data.
-
Ingest data from other sources by installing and configuring other Elastic Beats:
Elastic Beats To capture Infrastructure metrics
Logs
Windows event logs
Uptime information
Application performance metrics
Audit events
-
Use the Observability apps in Kibana to search across all your data:
Elastic apps Use to Explore metrics about systems and services across your ecosystem
Tail related log data in real time
Monitor availability issues across your apps and services
Monitor application performance
Analyze security events