Set up Enterprise Search with Active Directory user authentication
editSet up Enterprise Search with Active Directory user authentication
editThis feature is not available for all Elastic subscription levels. Refer to the subscriptions pages for Elastic Cloud and Elastic Stack. To change your subscription level or start a trial, see Elastic subscription.
The following documentation describes the process of configuring Elasticsearch and Kibana:
Within your Enterprise Search configuration settings, make sure that:
-
any
auth.sourceconfigurations are removed -
kibana.hostis set -
kibana.external_urlis set.
Configure Enterprise Search role mappings for Active Directory users
editWhen a user is logged in to Enterprise Search in Kibana via Active Directory, the following metadata properties would be populated:
-
ldap_dn: user’s distinguished name -
ldap_groups: the distinguished name of each of the groups that were resolved for the user.
Based on those metadata fields, it is possible to create role mappings that apply to groups of users. For example, members of the group called Administrators would get admin permissions to Workplace Search:
PUT _security/role_mapping/workplace_search_admin_ad
{
"roles": ["enterprise-search-workplace-search-admin"],
"rules" : {
"field" : {
"groups" : "CN=Administrators,CN=Builtin,DC=example,DC=org"
}
},
"enabled": true
}
While members of the group called Users would get user permissions:
PUT _security/role_mapping/workplace_search_user_ad
{
"roles": ["enterprise-search-workplace-search-user"],
"rules" : {
"field" : {
"CN=Users,CN=Builtin,DC=example,DC=org"
}
},
"enabled": true
}
Users can also be mapped in Users and Roles in Enterprise Search UI in Kibana:
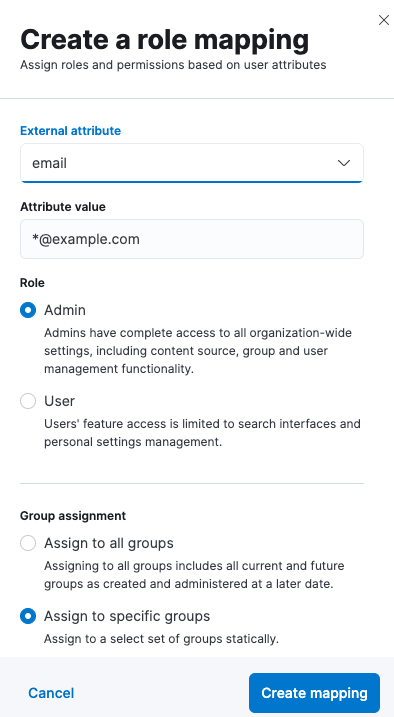
Mapping can use common Elasticsearch user attributes, such as username and email, but also anything provided in metadata that is returned by the Active Directory provider. Here is an example of metadata:
{
"ldap_dn" : "CN=adminuser,CN=Users,DC=dummy,DC=example,DC=org",
"displayName" : "Admin User",
"ldap_groups" : [
"CN=Administrators,CN=Builtin,DC=dummy,DC=example,DC=org",
"CN=Domain Users,CN=Users,DC=dummy,DC=example,DC=org",
"CN=Users,CN=Builtin,DC=dummy,DC=example,DC=org"
],
"name" : "adminuser",
"cn" : "adminuser",
"userPrincipalName" : "adminuser@dummy.example.org"
}
In Elasticsearch, the Active Directory realm that provided this metadata would be configured as follows:
xpack:
security:
authc:
realms:
active_directory:
ad1:
order: 1
domain_name: dummy.example.org
url: ldap://ad.dummy.example.org:389
bind_dn: "administrator@dummy.example.org"
metadata:
- cn
- name
- displayName
- userPrincipalName
For more information about configuring metadata returned by an Active Directory realm, see User metadata in Active Directory realms.