Required roles and privileges
editRequired roles and privileges
editBeginning with Elastic Stack version 8.1, you no longer require the built-in elastic superuser credentials to use Fleet and Integrations.
Assigning the Kibana feature privileges Fleet and Integrations grants access to these features:
-
all - Grants full read-write access.
-
read - Grants read-only access.
The built-in editor role grants the following privileges, supporting full read-write access to Fleet and Integrations:
-
Fleet:
All -
Integrations:
All
The built-in viewer role grants the following privileges, supporting read-only access to Fleet and Integrations:
-
Fleet::
None -
Integrations::
Read
You can also create a new role that can be assigned to a user to grant access to Fleet and Integrations.
Create a role for Fleet
editTo create a new role with full access to use and manage Fleet and Integrations:
- In Kibana, go to Management → Stack Management.
- In the Security section, select Roles.
- Select Create role.
- Specify a name for the role.
- Leave the Elasticsearch settings at their defaults, or refer to Security privileges for descriptions of the available settings.
- In the Kibana section, select Add Kibana privilege.
- In the Spaces menu, select * All Spaces. Since many Integrations assets are shared across spaces, the users needs the Kibana privileges in all spaces.
- Expand the Management section.
- Set Fleet privileges to All.
- Set Integrations privileges to All.
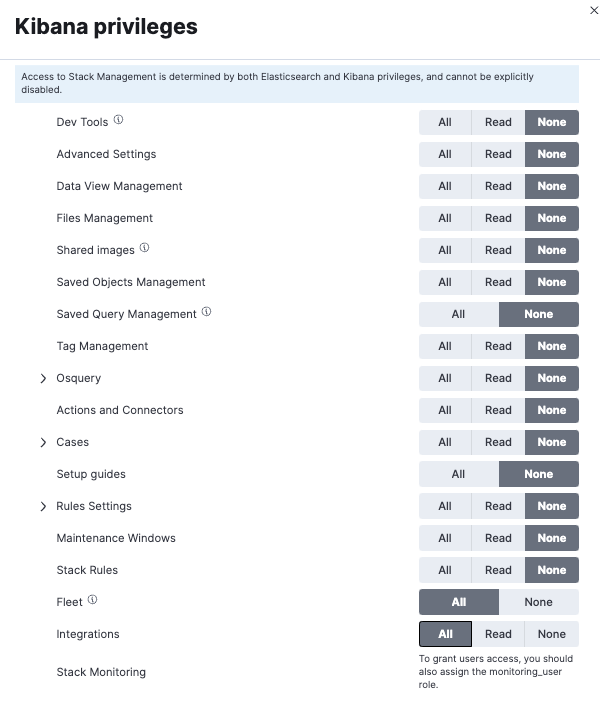
To create a read-only user for Integrations, follow the same steps as above but set the Fleet privileges to None and the Integrations privileges to Read.
Read-only access to Fleet is not currently supported but is planned for development in a later release.