SIEM
editSIEM
editThis functionality is in beta and is subject to change. The design and code is less mature than official GA features and is being provided as-is with no warranties. Beta features are not subject to the support SLA of official GA features.
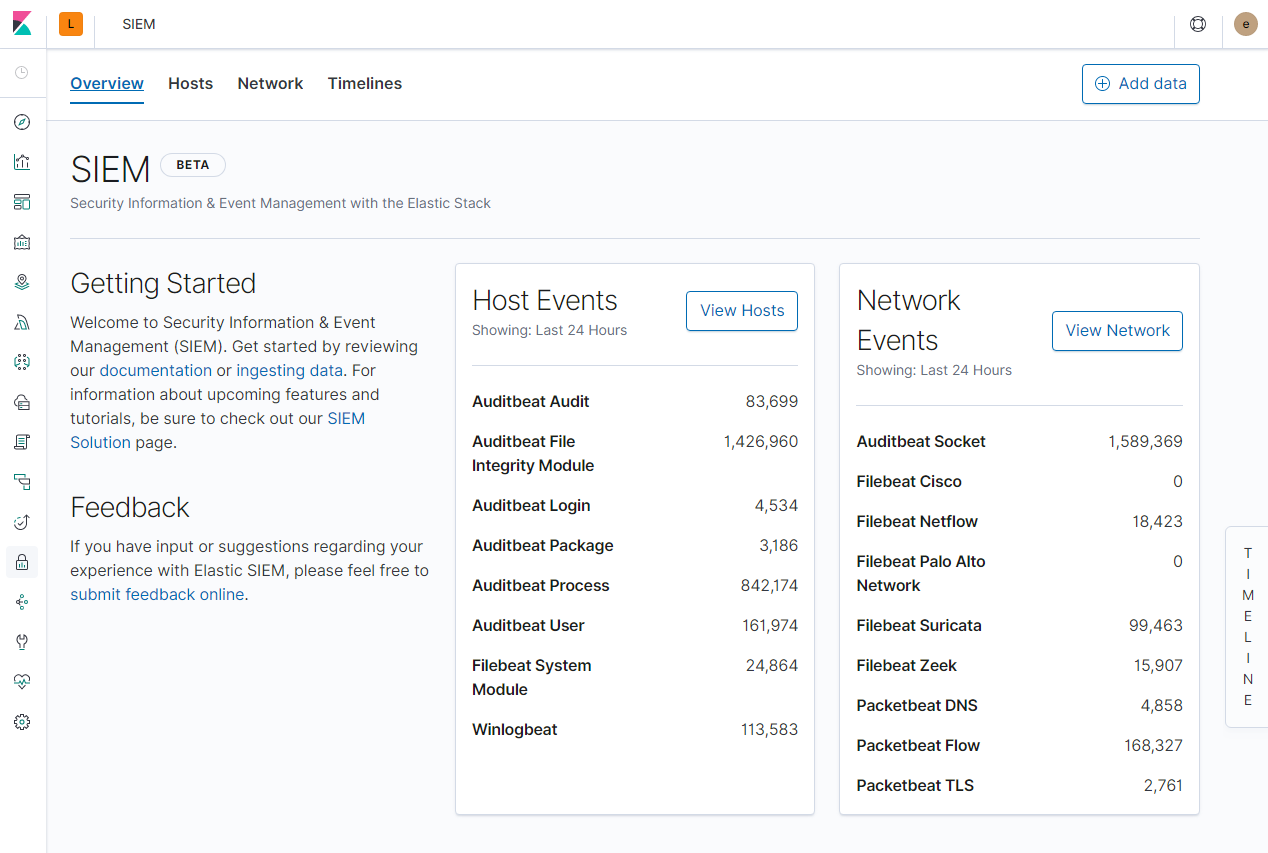
The SIEM app in Kibana provides an interactive workspace for security teams to triage events and perform initial investigations. It enables analysis of host-related and network-related security events as part of alert investigations or interactive threat hunting.
Add data
editKibana provides step-by-step instructions to help you add data. The SIEM Guide is a good source for more detailed information and instructions.
Beats
editAuditbeat, Filebeat, Winlogbeat, and Packetbeat send security events and other data to Elasticsearch.
The default index patterns for SIEM events are auditbeat-*, winlogbeat-*,
filebeat-*, endgame-*, and packetbeat-*`. You can change the default index patterns in
Kibana > Management > Advanced Settings > siem:defaultIndex.
Elastic Endpoint Sensor Management Platform
editThe Elastic Endpoint Sensor Management Platform (SMP) ships host and network events directly to the SIEM application, and is fully ECS compliant.
Elastic Common Schema (ECS) for normalizing data
editThe Elastic Common Schema (ECS) defines a common set of fields to be used for storing event data in Elasticsearch. ECS helps users normalize their event data to better analyze, visualize, and correlate the data represented in their events.
SIEM can ingest and normalize events from ECS-compatible data sources.