What’s new in 7.15
editWhat’s new in 7.15
editHere are the highlights of what’s new and improved in the latest version of Elastic Security.
For detailed information about this release, see the Release notes.
Other versions: 7.14 | 7.13 | 7.12 | 7.11 | 7.10 | 7.9
7.15
editNew features
editMalicious behavior protection for Linux, Windows, and macOS hosts
Malicious behavior protection detects and stops threats by monitoring the behavior of system processes for suspicious activity. It leverages existing malware and ransomware prevention with dynamic prevention of post-execution behavior. Malicious behavior is available for customers with a Platinum or Enterprise license.
Memory threat protection for Windows hosts
Memory threat protection detects and stops many of the techniques used for process injection via shellcode, where an attacker attempts to avoid detection by executing an attack from memory instead of from on-disk, where most detection tools operate. Adversaries leverage in-memory attacks to evade common defensive technologies. Elastic Security also stops sub-techniques such as thread execution hijacking, asynchronous procedure call, process hollowing, and process doppelgänging. Memory threat protection is available for customers with a Platinum or Enterprise license.
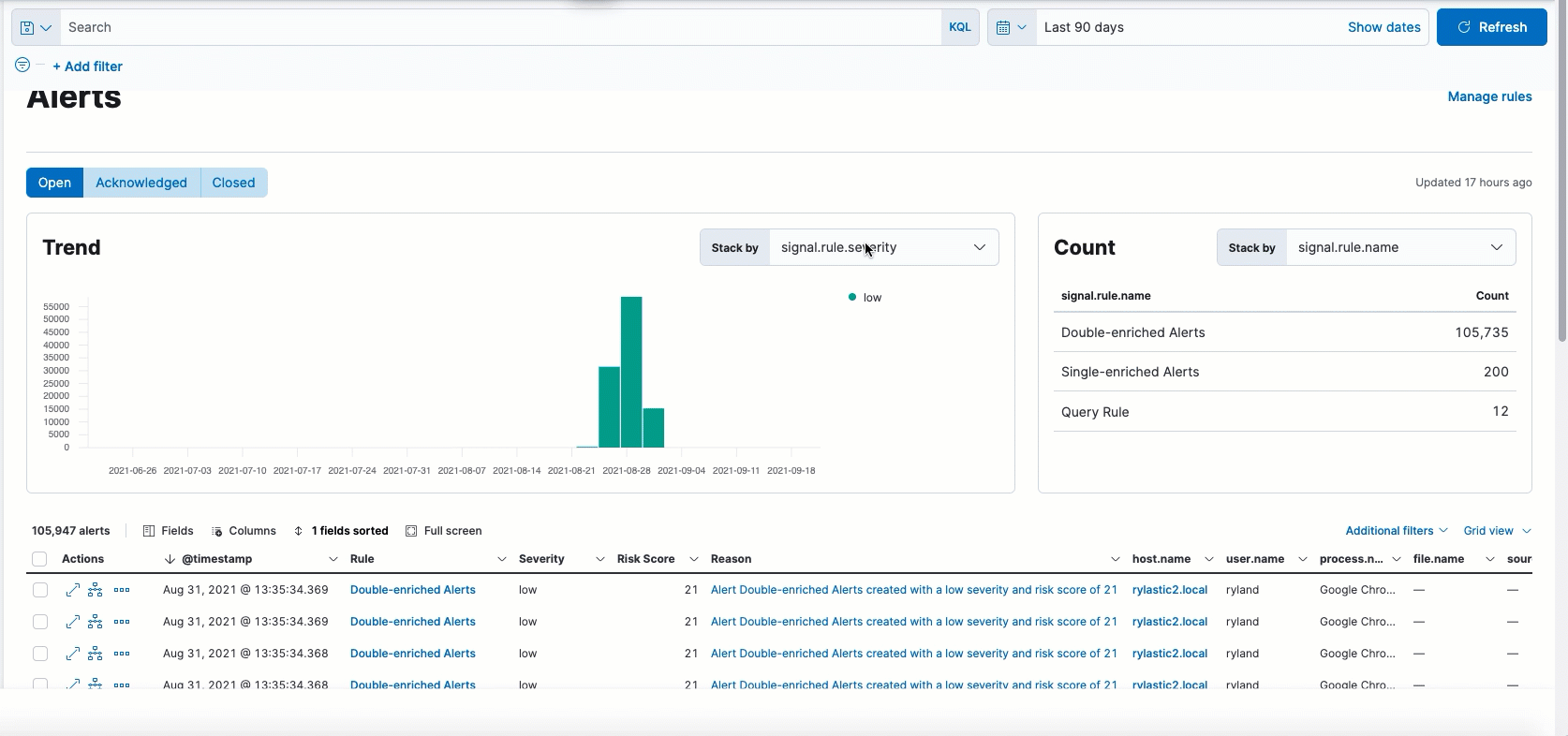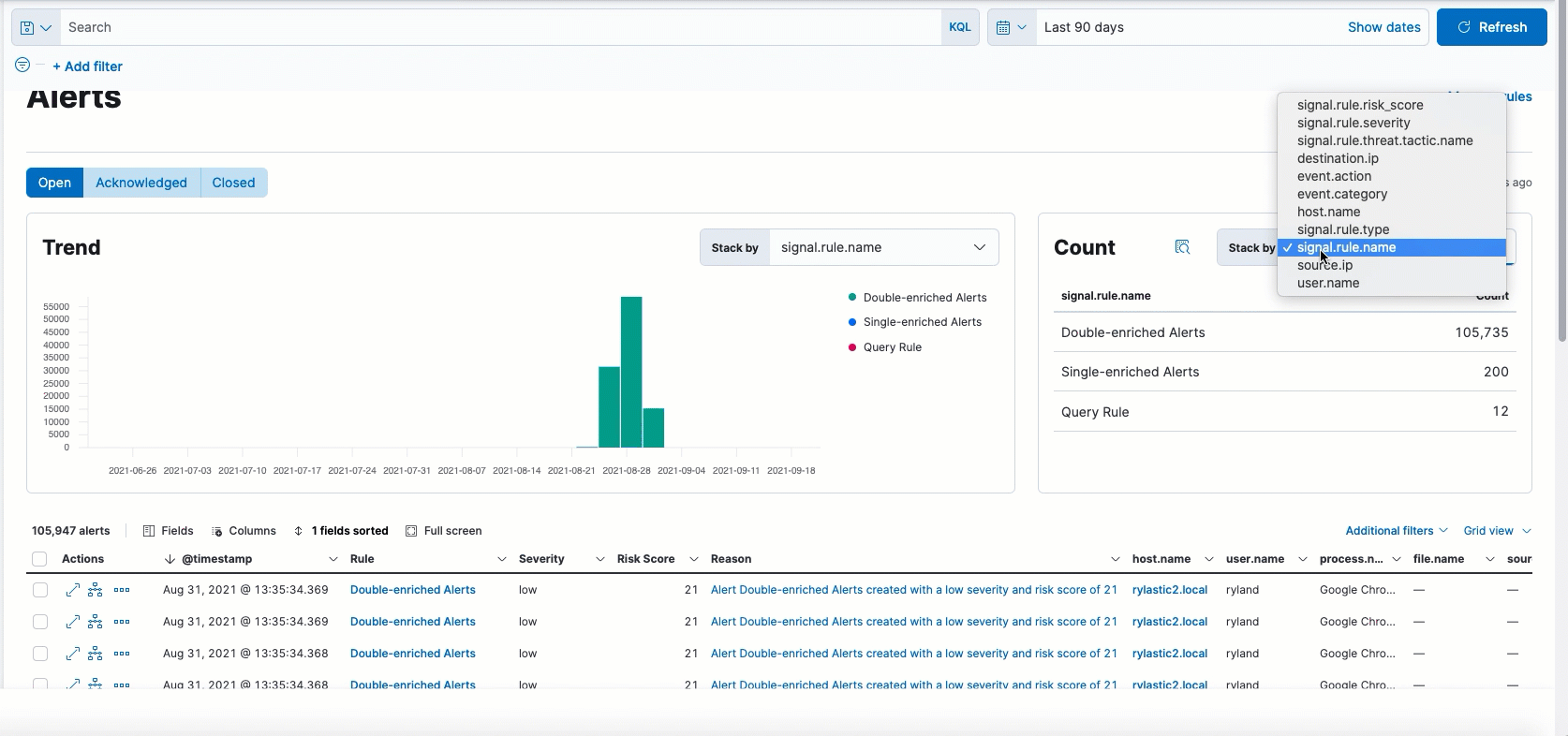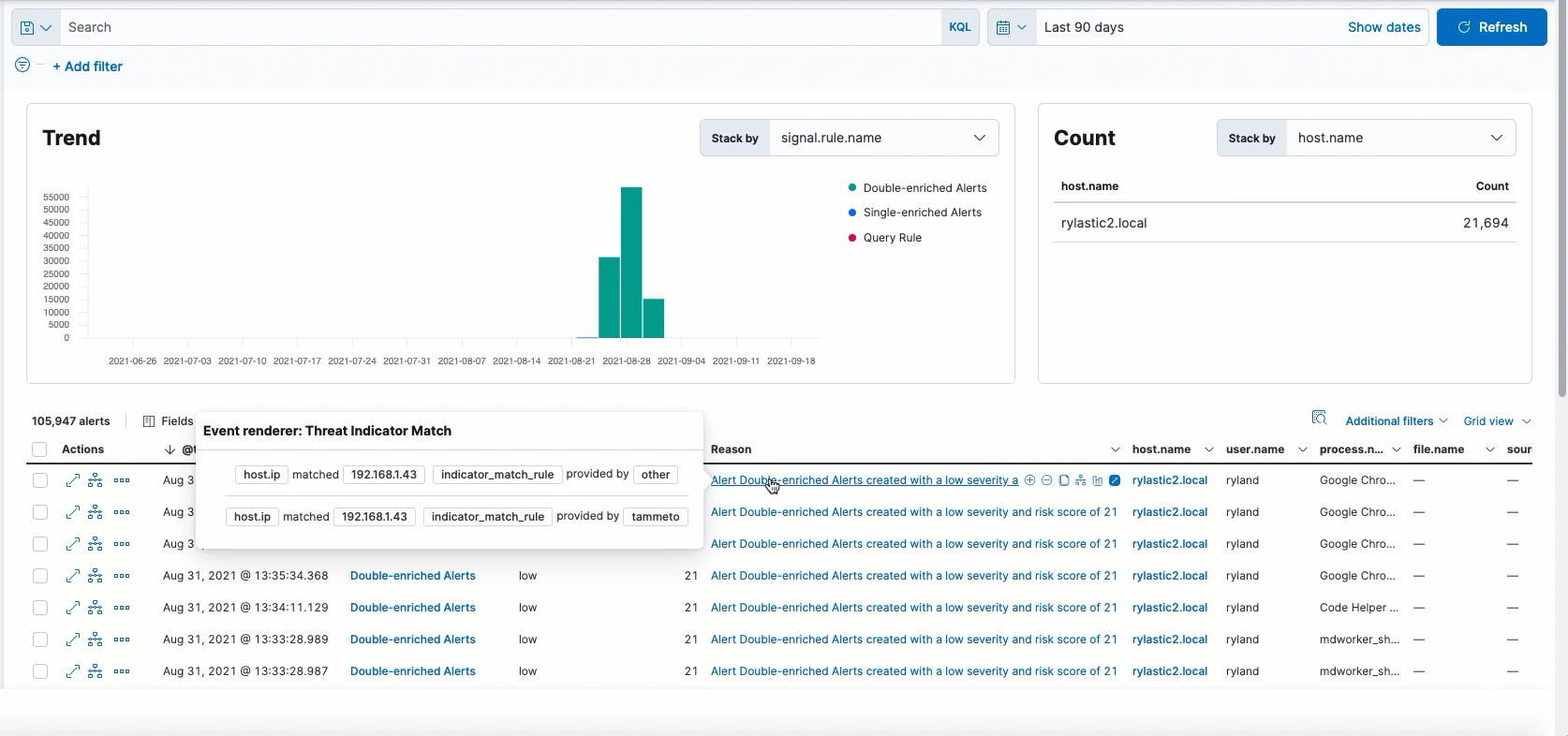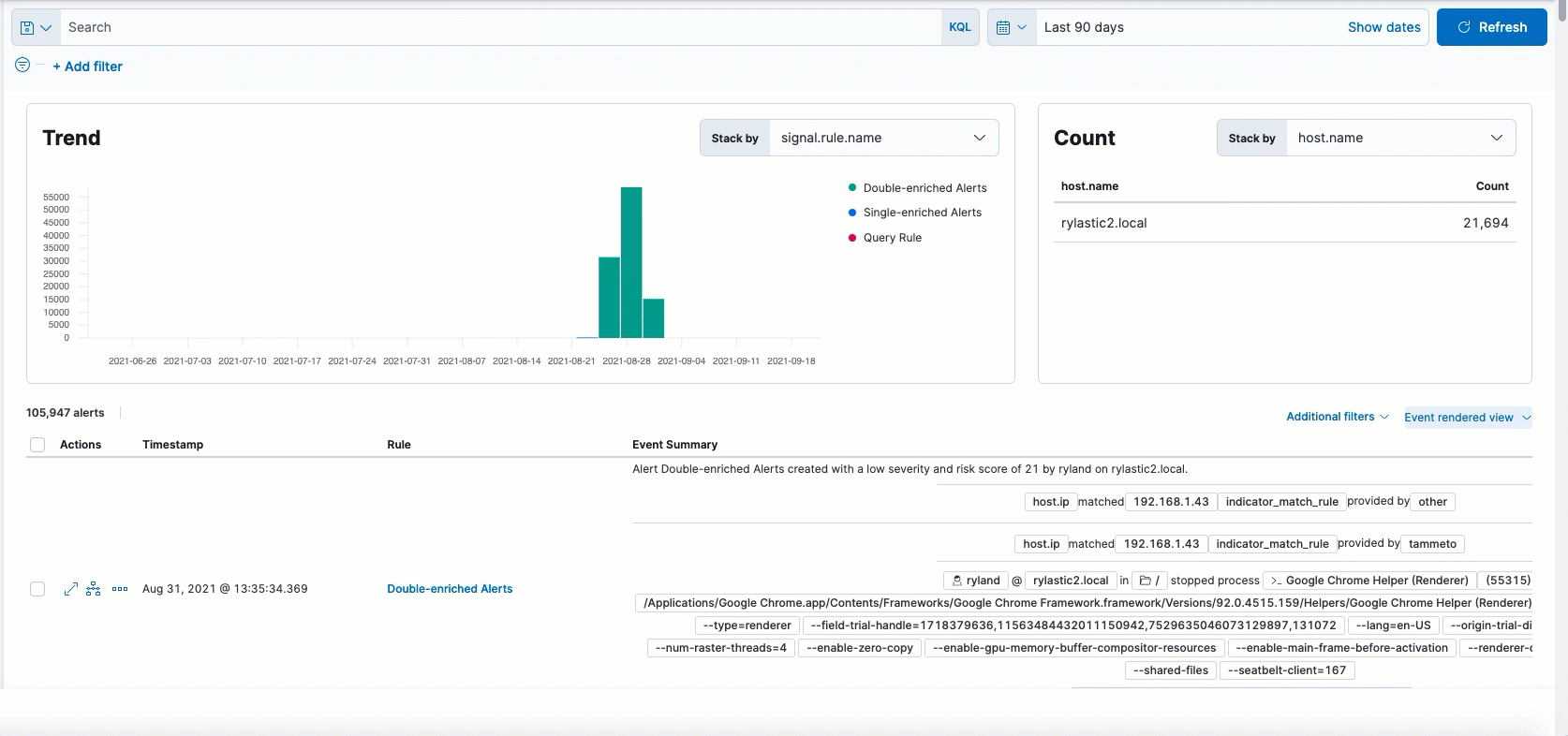
Enhanced Alerts page view
The Alerts page has several new enhancements, all designed to help triage alerts faster. A few of these include:
-
Updated alert statuses (
Open,Acknowledged, andClosed) - New options to group alerts by specific parameters and view individual alert counts
- New options to customize the Alerts table view
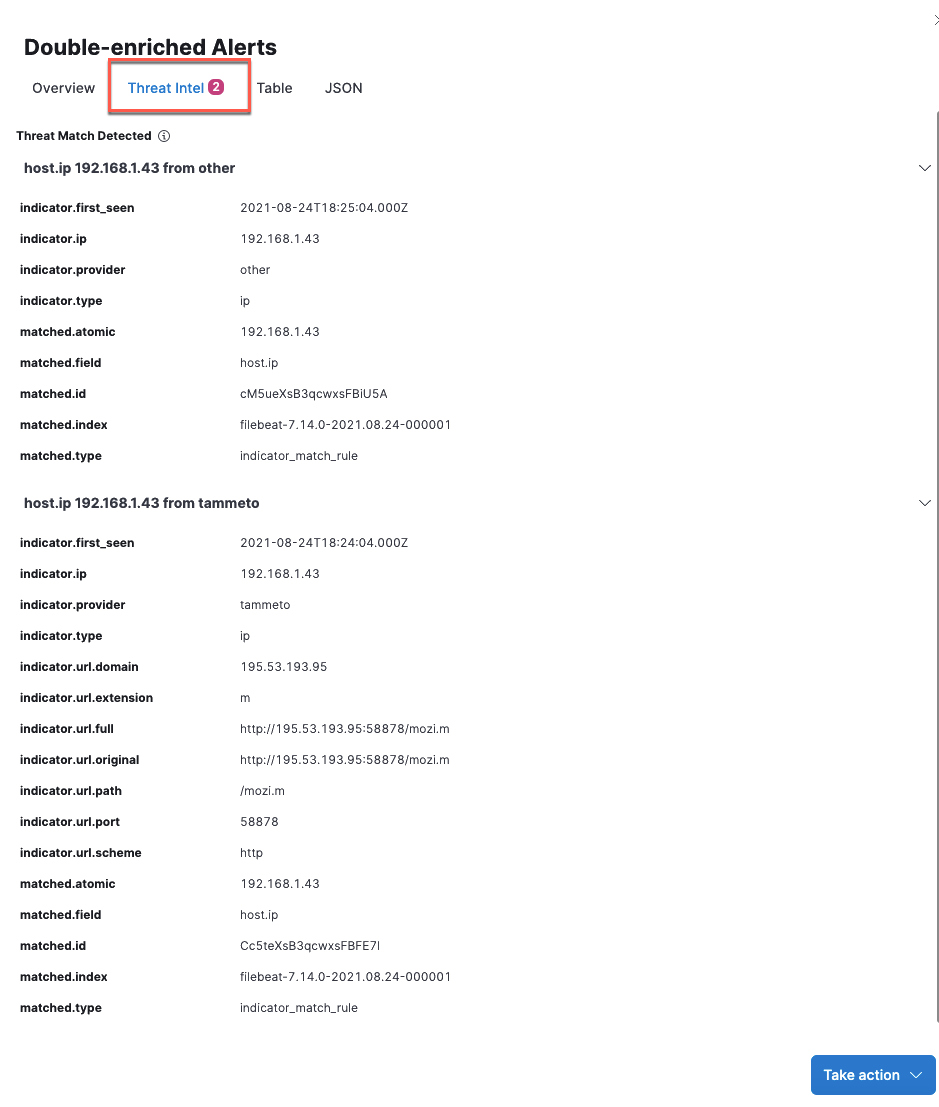
Threat intelligence data enhancements
The following enhancements have been made to alerts enriched with threat intel data:
-
The
securitySolution:defaultThreatIndexadvanced setting allows you to define threat intelligence indices that Elastic Security will use when collecting threat indicators. The setting controls features that query threat indices, such as the Threat Intelligence view on the Overview page and the default indicator index values for indicator match rules. - The event enrichment query performance has been improved.
- UX enhancements to the Threat Intel tab in the Alert details flyout allow you to view threat matches and their correlating details.
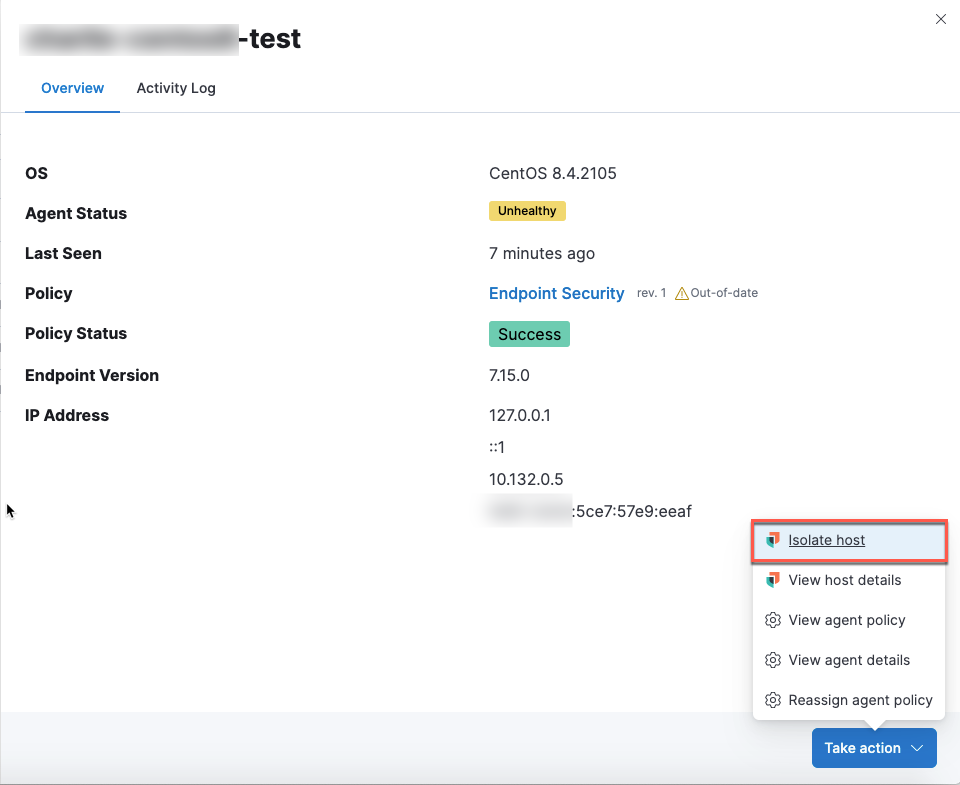
Host isolation for all operating systems
Host isolation, which allows analysts to respond to malicious activity by isolating a host from a network, was introduced for Windows and macOS hosts in Elastic Stack 7.14. In Elastic Stack 7.15, this feature is now available for Linux hosts, making the feature compatible with all operating systems.
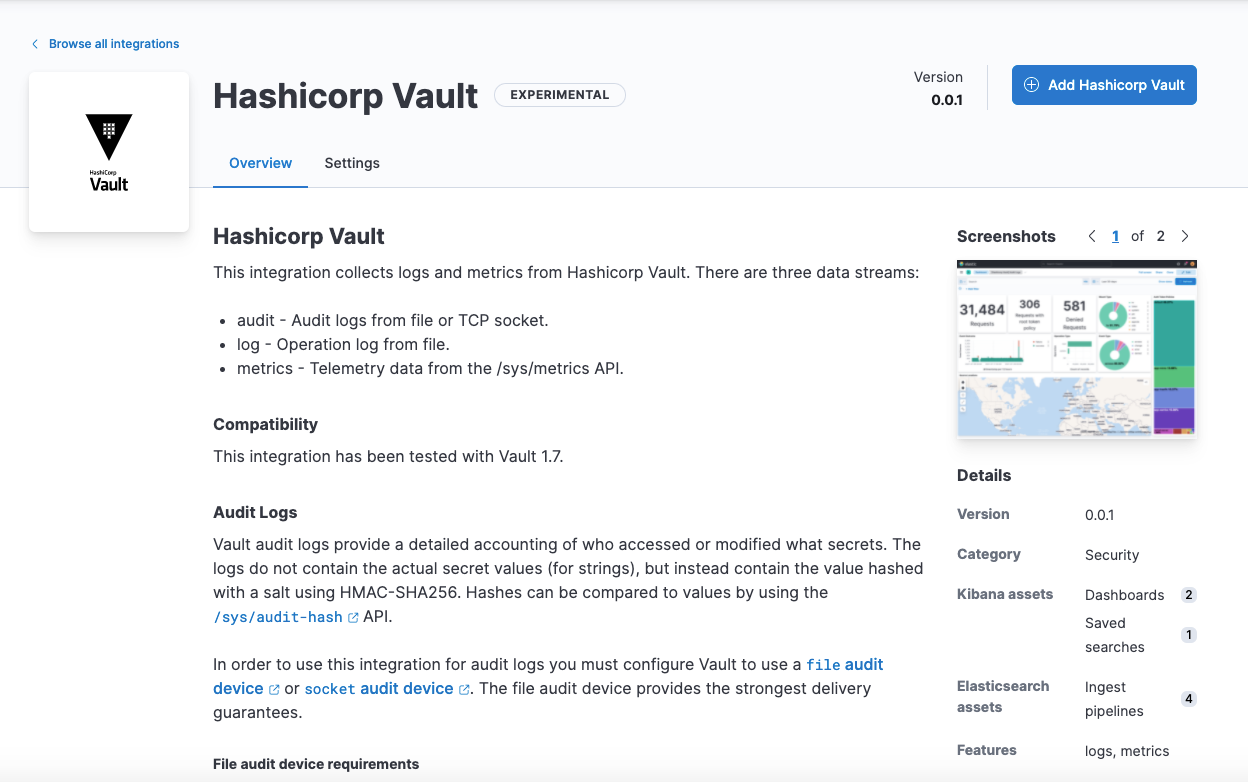
New third-party integrations
Elastic Security introduces the following new integrations in 7.15:
- CrowdStrike Falcon
- Cloudflare
- Palo Alto Networks Cortex XDR
- VMware Carbon Black EDR
- Hashicorp Vault
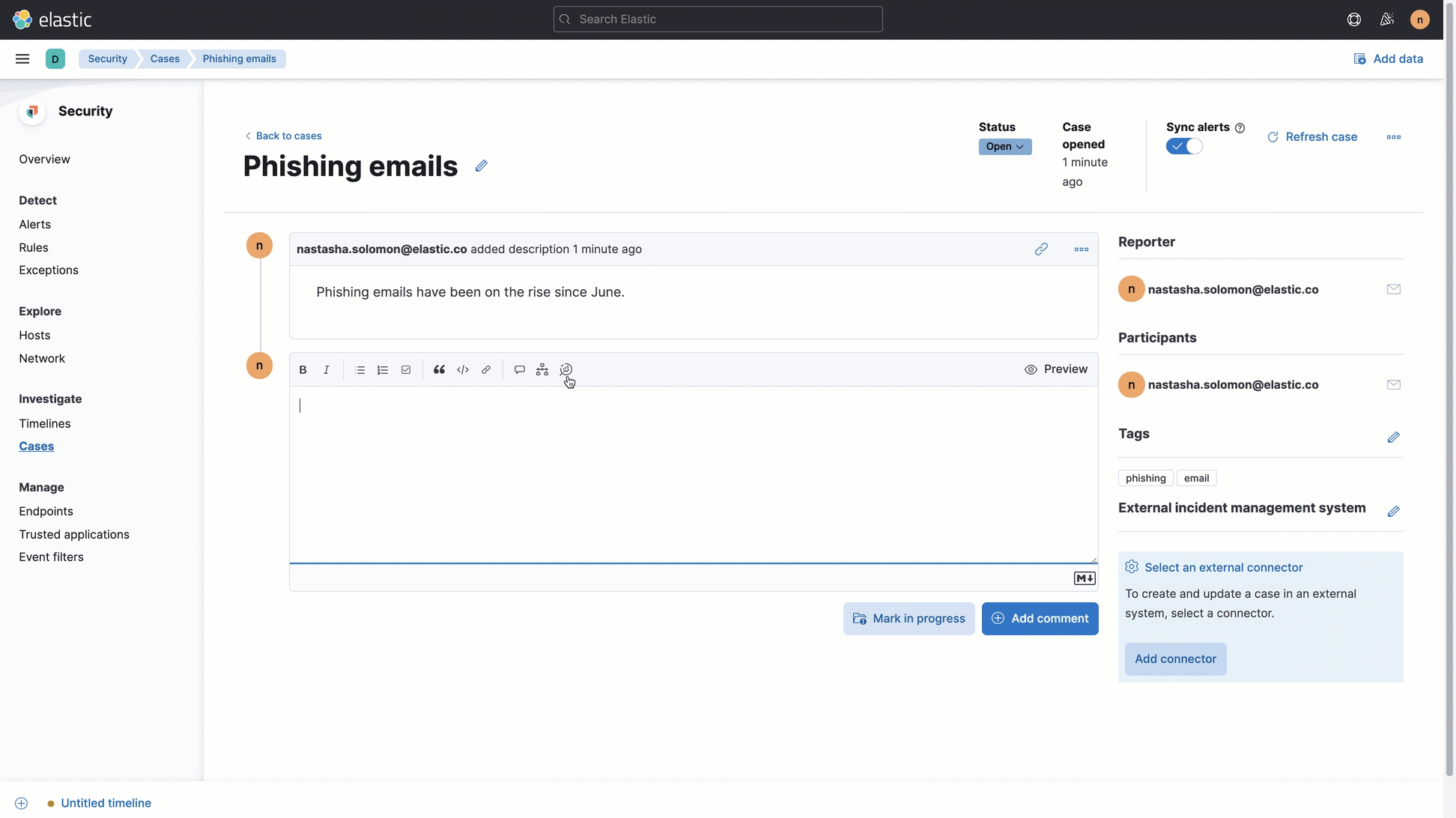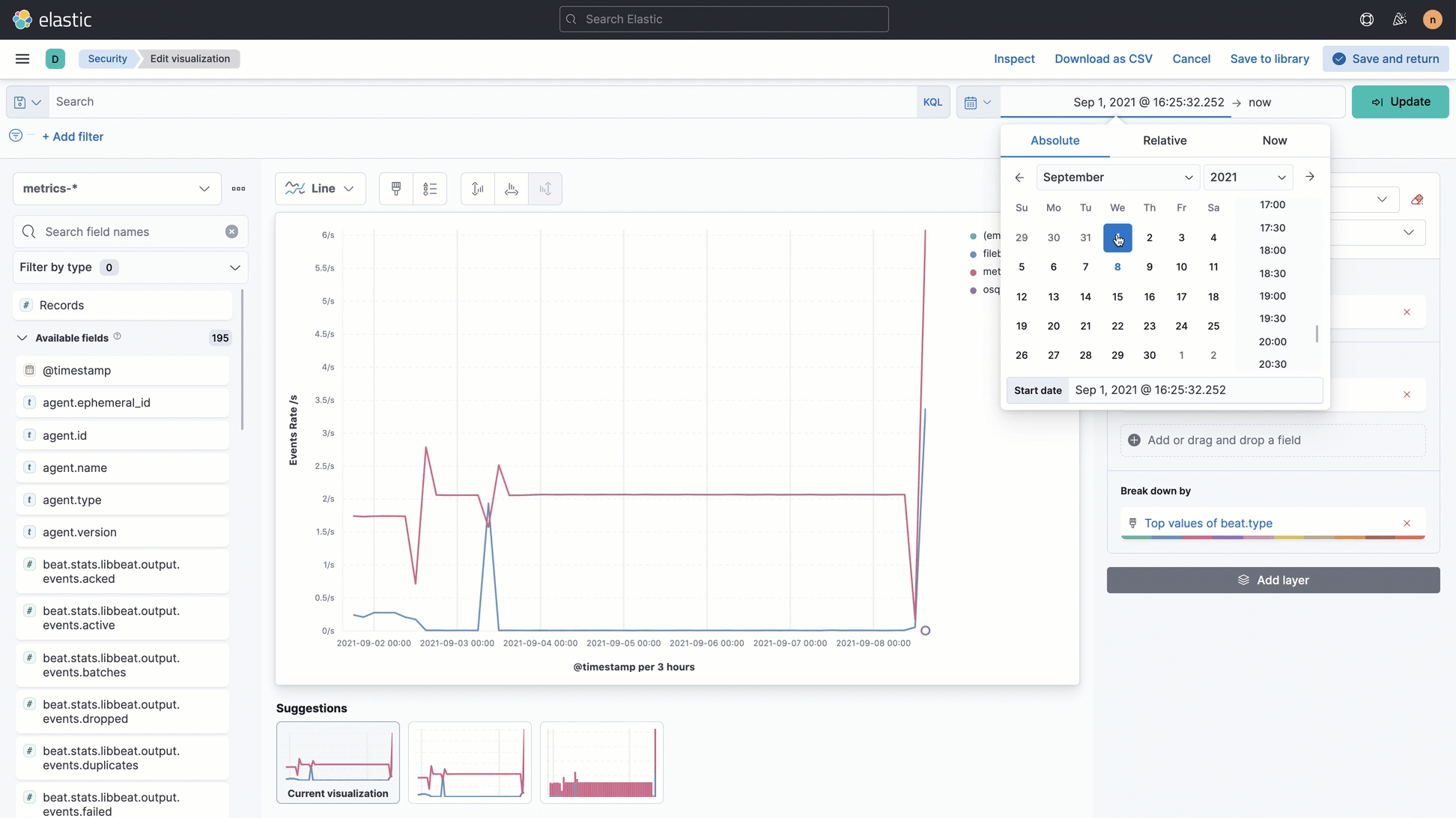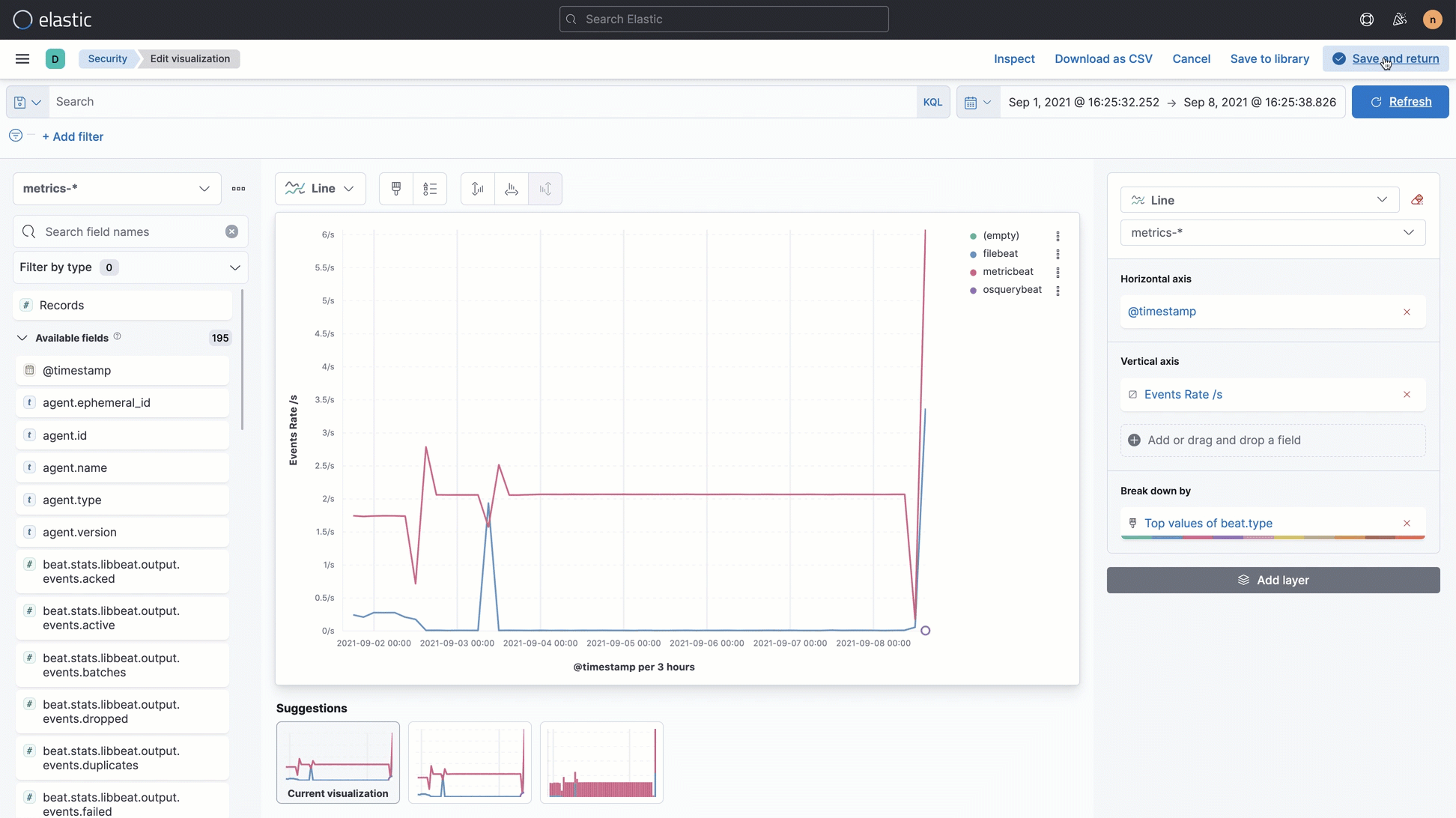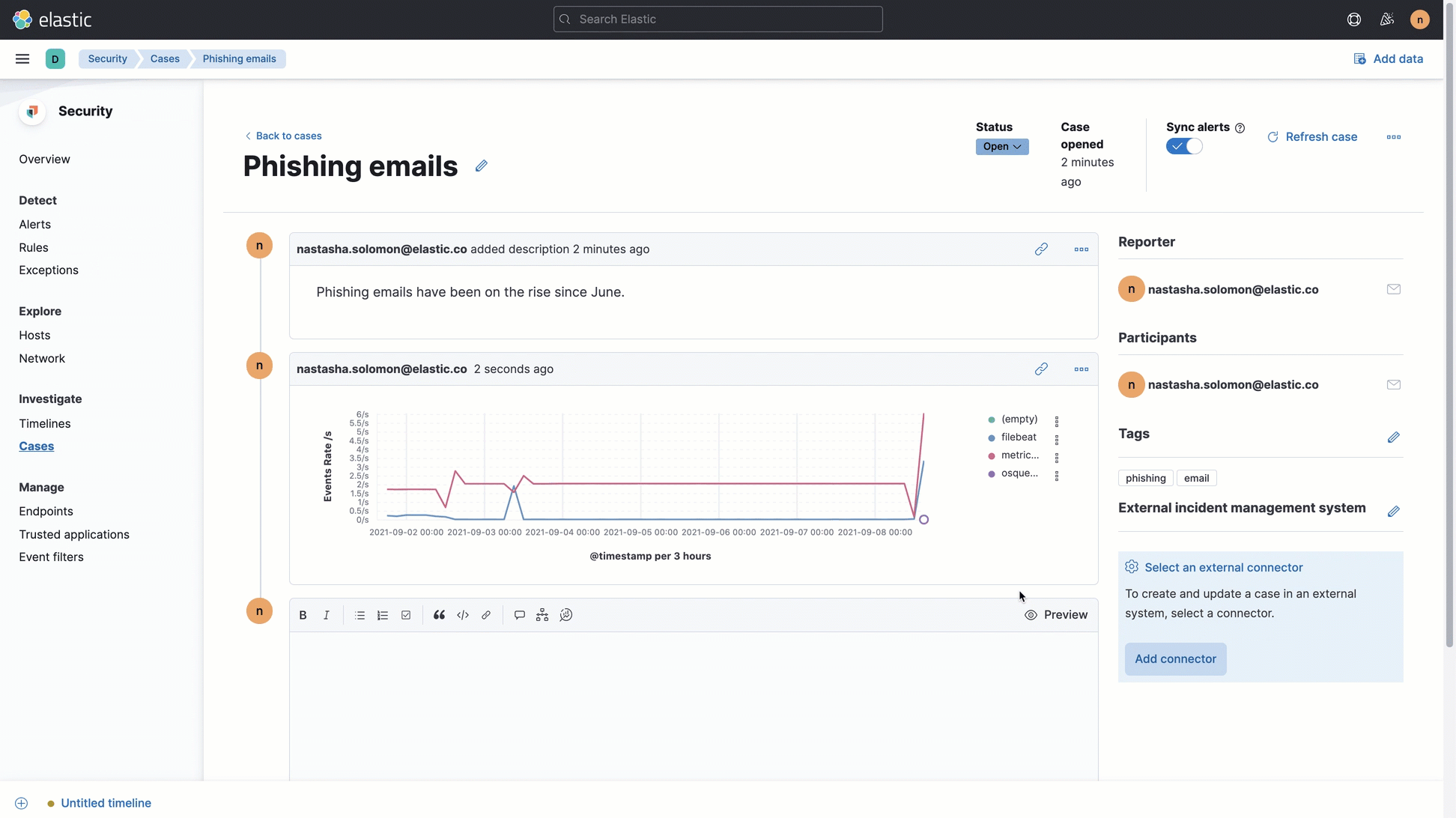
Add a Lens visualization to an existing case (beta)
Add a Lens visualization to your case to portray event and alert data through charts and graphs.