Trusted applications
editTrusted applications
editIf you use Endpoint Security along with other antivirus (AV) software, you might need to configure the other system to trust Elastic Endpoint. Refer to Allowlist Elastic Endpoint in third-party antivirus apps for more information.
You can add Windows, macOS, and Linux applications that should be trusted. By adding these trusted applications, you can use Elastic Security without compatibility or performance issues with other installed applications on your system. Trusted applications are applied only to hosts running Endpoint Security.
You must have the built-in superuser role to access this feature. For more information, refer to Built-in users.
Trusted applications are designed to help mitigate performance issues and incompatibilities with other endpoint software. However, they create blindspots for Elastic Security. One avenue attackers use to exploit these blindspots is by DLL (Dynamic Link Library) side-loading, where they leverage processes signed by trusted vendors — such as antivirus software — to execute their malicious DLLs. Such activity appears to originate from the trusted vendor’s process.
By default, a trusted application is recognized globally across all hosts running Endpoint Security. If you have a Platinum or Enterprise subscription, you can also assign a trusted application to a specific Endpoint Security integration policy, enabling the application to be trusted by only the hosts assigned to that policy.
To add a trusted application:
- Go to Manage → Trusted applications.
- Click Add trusted application.
-
Fill in the following fields in the Add trusted application flyout:
-
Name your trusted application: Enter a name for the trusted application. -
Description(Optional): Enter a description for the trusted application. -
Select operating system: Select the appropriate operating system from the drop-down. -
Field: Select a field to identify the trusted application:-
Hash: The MD5, SHA-1, or SHA-256 hash value of the application’s executable. -
Path: The full file path of the application’s executable. -
Signature: (Windows only) The name of the application’s digital signer.To find the signer’s name for an application, go to Kibana → Discover and query the process name of the application’s executable (for example,
process.name : "mctray.exe"for a McAfee security binary). Then, search the results for theprocess.code_signature.subject_namefield, which contains the signer’s name (for example,McAfee, Inc.).
-
-
Operator: Select an operator to define the condition:-
is: Must be exactly equal toValue. This operation is required for theHashandSignaturefield types. -
matches: Can include wildcards inValue, such asC:\path\*\app.exe. This option is only available for thePathfield type. Available wildcards are?(match one character) and*(match zero or more characters).
-
-
Value: Enter the hash value, file path, or signer name. To add an additional value, click AND.You can only add a single field type value per trusted application. For example, if you try to add two
Pathvalues, you’ll get an error message. Also, an application’s hash value must be valid to add it as a trusted application. In addition, to minimize visibility gaps in the Elastic Security app, be as specific as possible in your entries. For example, combineSignatureinformation with a knownPath.
-
-
Select an option in the Assignment section to assign the trusted application to a specific integration policy:
-
Global: Assign the trusted application to all integration policies for Endpoint Security. -
Per Policy(Platinum or Enterprise subscription only): Assign the trusted application to one or more specific Endpoint Security integration policies. Select each policy in which you want the application to be trusted.You can also select the
Per Policyoption without immediately assigning a policy to the trusted application. For example, you could do this to create and review your trusted application configurations before putting them into action with a policy.
-
- Click Add trusted application. The application is added to the Trusted applications list.
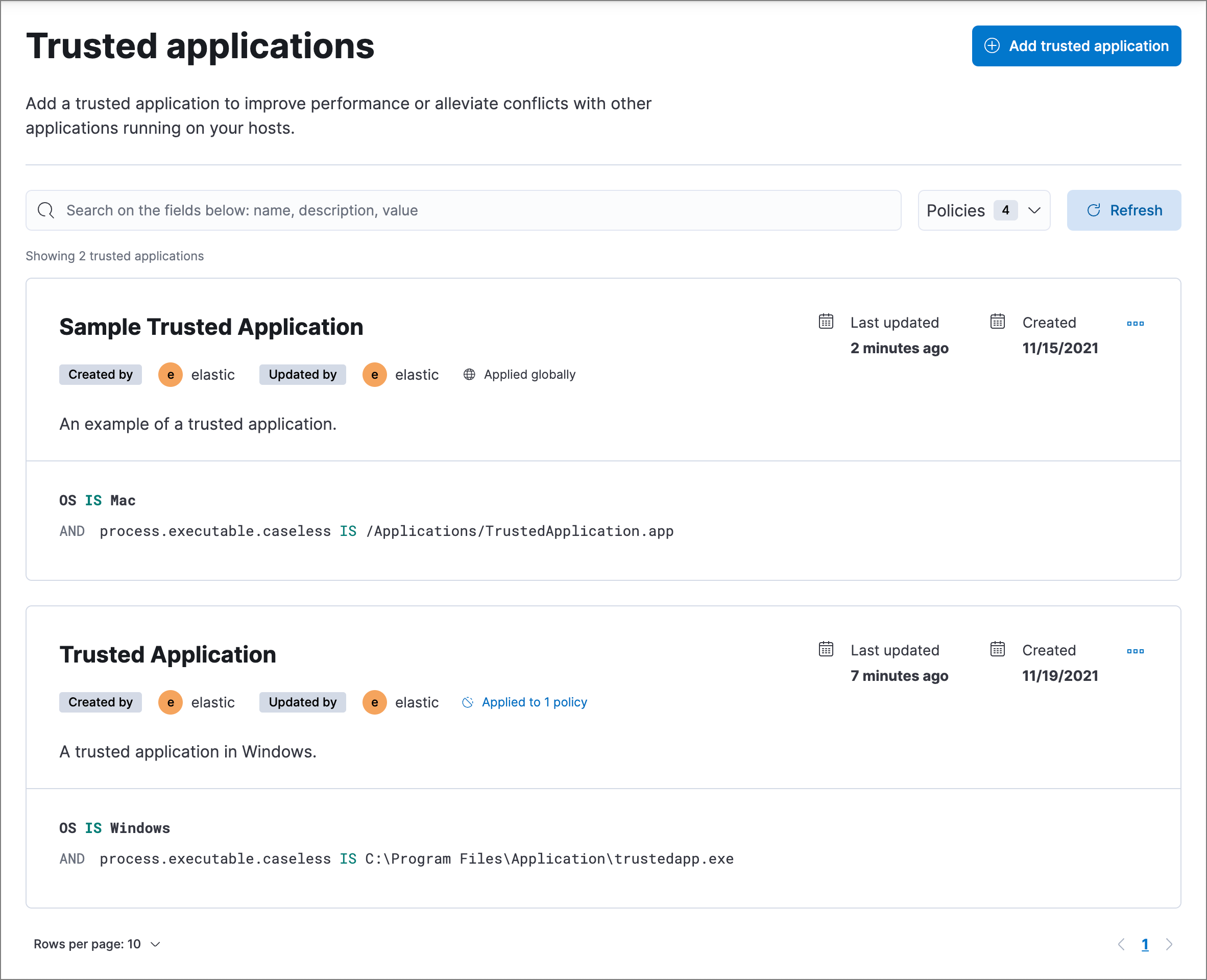
View and manage trusted applications
editThe Trusted applications list displays all the trusted applications that have been added to the Elastic Security app. To refine the Trusted applications list, use the search bar to search by name, description, or a field value.
Edit a trusted application
editYou can individually configure each trusted application. With a Platinum or Enterprise subscription, you can also change the policies applied to a trusted application.
To edit a trusted application:
- Click the actions button (…) for the trusted application you want to edit, then select Edit trusted application.
- Modify details as needed.
- Click Save.
Delete a trusted application
editYou can delete a trusted application, which removes it entirely from all Endpoint Security policies.
To delete a trusted application:
- Click the actions button (…) for the trusted application you want to delete, then select Delete trusted application.
- On the dialog that opens, verify that you are removing the correct application, then click Delete. A confirmation message is displayed.