Articles

Security operations: Cloud monitoring and detection with Elastic Security
As companies migrate to cloud, so too do opportunist adversaries. That's why our Elastic Security team members have created free detection rules for protecting users' cloud platforms like AWS and Okta. Learn more in this blog post.

Adversary tradecraft 101: Hunting for persistence using Elastic Security (Part 2)
Learn how Elastic Endpoint Security and Elastic SIEM can be used to hunt for and detect malicious persistence techniques at scale.
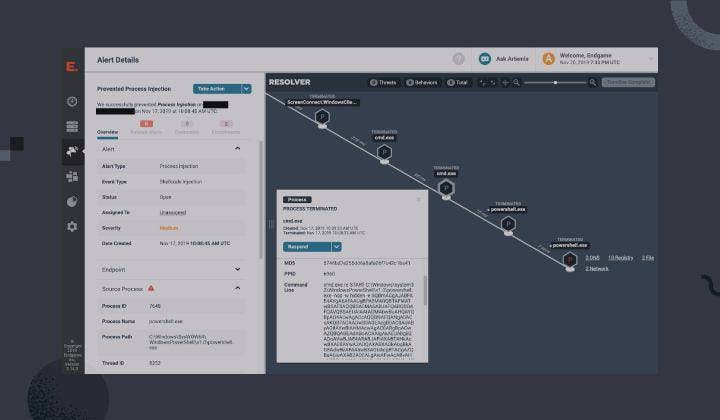
Ransomware, interrupted: Sodinokibi and the supply chain
Learn how Elastic Endpoint Security's behavior-based protections prevented a targeted ransomware attack on multiple endpoints.

Testing your Okta visibility and detection with Dorothy and Elastic Security
Dorothy is a tool for security teams to test their visibility and detection capabilities for their Okta environment. IAM solutions are frequently targeted by adversaries but poorly monitored. Learn how to get started with Dorothy in this post.

Adversary tradecraft 101: Hunting for persistence using Elastic Security (Part 1)
Learn how Elastic Endpoint Security and Elastic SIEM can be used to hunt for and detect malicious persistence techniques at scale.
