Topic
Security research
10 December 2024
Exploring AWS STS AssumeRoot
Explore AWS STS AssumeRoot, its risks, detection strategies, and practical scenarios to secure against privilege escalation and account compromise using Elastic's SIEM and CloudTrail data.

Streamlining Security: Integrating Amazon Bedrock with Elastic
This article will guide you through the process of setting up the Amazon Bedrock integration and enabling Elastic's prebuilt detection rules to streamline your security operations.

Cups Overflow: When your printer spills more than Ink
Elastic Security Labs discusses detection and mitigation strategies for vulnerabilities in the CUPS printing system, which allow unauthenticated attackers to exploit the system via IPP and mDNS, resulting in remote code execution (RCE) on UNIX-based systems such as Linux, macOS, BSDs, ChromeOS, and Solaris.

Storm on the Horizon: Inside the AJCloud IoT Ecosystem
Wi-Fi cameras are popular due to their affordability and convenience but often have security vulnerabilities that can be exploited.

Code of Conduct: DPRK’s Python-fueled intrusions into secured networks
Investigating the DPRK’s strategic use of Python and carefully crafted social engineering, this publication sheds light on how they breach highly secure networks with evolving and effective cyber attacks.

Dismantling Smart App Control
This article will explore Windows Smart App Control and SmartScreen as a case study for researching bypasses to reputation-based systems, then demonstrate detections to cover those weaknesses.

Introducing a New Vulnerability Class: False File Immutability
This article introduces a previously-unnamed class of Windows vulnerability that demonstrates the dangers of assumption and describes some unintended security consequences.

情報窃取から端末を守る
本記事ではElastic Securityにおいて、エンドポイント保護を担っているElastic Defendに今年(バージョン8.12より)新たに追加された、キーロガーおよびキーロギング検出機能について紹介します。

Protecting your devices from information theft
In this article, we will introduce the keylogger and keylogging detection features added this year to Elastic Defend (starting from version 8.12), which is responsible for endpoint protection in Elastic Security.

500ms to midnight: XZ / liblzma backdoor
Elastic Security Labs is releasing an initial analysis of the XZ Utility backdoor, including YARA rules, osquery, and KQL searches to identify potential compromises.

Unveiling malware behavior trends
An analysis of a diverse dataset of Windows malware extracted from more than 100,000 samples revealing insights into the most prevalent tactics, techniques, and procedures.

Monitoring Okta threats with Elastic Security
This article guides readers through establishing an Okta threat detection lab, emphasizing the importance of securing SaaS platforms like Okta. It details creating a lab environment with the Elastic Stack, integrating SIEM solutions, and Okta.

Ransomware in the honeypot: how we capture keys with sticky canary files
This article describes the process of capturing encryption keys from ransomware using Elastic Defend ransomware protection.

Starter guide to understanding Okta
This article delves into Okta's architecture and services, laying a solid foundation for threat research and detection engineering. Essential reading for those aiming to master threat hunting and detection in Okta environments.

Doubling Down: Detecting In-Memory Threats with Kernel ETW Call Stacks
With Elastic Security 8.11, we added further kernel telemetry call stack-based detections to increase efficacy against in-memory threats.

Google Cloud for Cyber Data Analytics
This article explains how we conduct comprehensive cyber threat data analysis using Google Cloud, from data extraction and preprocessing to trend analysis and presentation. It emphasizes the value of BigQuery, Python, and Google Sheets - showcasing how to refine and visualize data for insightful cybersecurity analysis.

Signaling from within: how eBPF interacts with signals
This article explores some of the semantics of UNIX signals when generated from an eBPF program.

Streamlining ES|QL Query and Rule Validation: Integrating with GitHub CI
ES|QL is Elastic's new piped query language. Taking full advantage of this new feature, Elastic Security Labs walks through how to run validation of ES|QL rules for the Detection Engine.

Disclosing the BLOODALCHEMY backdoor
BLOODALCHEMY is a new, actively developed, backdoor that leverages a benign binary as an injection vehicle, and is a part of the REF5961 intrusion set.

Introducing the REF5961 intrusion set
The REF5961 intrusion set discloses three new malware families targeting ASEAN members. The threat actor leveraging this intrusion set continues to develop and mature their capabilities.

Inside Microsoft's plan to kill PPLFault
In this research publication, we'll learn about upcoming improvements to the Windows Code Integrity subsystem that will make it harder for malware to tamper with Anti-Malware processes and other important security features.

Peeling back the curtain with call stacks
In this article, we'll show you how we contextualize rules and events, and how you can leverage call stacks to better understand any alerts you encounter in your environment.
Into The Weeds: How We Run Detonate
Explore the technical implementation of the Detonate system, including sandbox creation, the supporting technology, telemetry collection, and how to blow stuff up.

Upping the Ante: Detecting In-Memory Threats with Kernel Call Stacks
We aim to out-innovate adversaries and maintain protections against the cutting edge of attacker tradecraft. With Elastic Security 8.8, we added new kernel call stack based detections which provide us with improved efficacy against in-memory threats.

Click, Click… Boom! Automating Protections Testing with Detonate
To automate this process and test our protections at scale, we built Detonate, a system that is used by security research engineers to measure the efficacy of our Elastic Security solution in an automated fashion.

Exploring the Future of Security with ChatGPT
Recently, OpenAI announced APIs for engineers to integrate ChatGPT and Whisper models into their apps and products. For some time, engineers could use the REST API calls for older models and otherwise use the ChatGPT interface through their website.

Elastic Global Threat Report Multipart Series Overview
Each month, the Elastic Security Labs team dissects a different trend or correlation from the Elastic Global Threat Report. This post provides an overview of those individual publications.

Effective Parenting - detecting LRPC-based parent PID spoofing
Using process creation as a case study, this research will outline the evasion-detection arms race to date, describe the weaknesses in some current detection approaches and then follow the quest for a generic approach to LRPC-based evasion.

Hunting for Suspicious Windows Libraries for Execution and Defense Evasion
Learn more about discovering threats by hunting through DLL load events, one way to reveal the presence of known and unknown malware in noisy process event data.

Sandboxing Antimalware Products for Fun and Profit
This article demonstrates a flaw that allows attackers to bypass a Windows security mechanism which protects anti-malware products from various forms of attack.

NETWIRE Dynamic Configuration Extraction
Elastic Security Labs discusses the NETWIRE trojan and is releasing a tool to dynamically extract configuration files.

Finding Truth in the Shadows
Let's discuss three benefits that Hardware Stack Protections brings beyond the intended exploit mitigation capability, and explain some limitations.

Vulnerability summary: Follina, CVE-2022-30190
Elastic is deploying a new malware signature to identify the use of the Follina vulnerability. Learn more in this post.

Get-InjectedThreadEx – Detecting Thread Creation Trampolines
In this blog, we will demonstrate how to detect each of four classes of process trampolining and release an updated PowerShell detection script – Get-InjectedThreadEx

EMOTET Dynamic Configuration Extraction
Elastic Security Labs discusses the EMOTET trojan and is releasing a tool to dynamically extract configuration files using code emulators.

Analysis of Log4Shell vulnerability & CVE-2021-45046
In this post, we cover next steps the Elastic Security team is taking for users to continue to protect themselves against CVE-2021-44228, or Log4Shell.

Deep dive into the TTD ecosystem
This is the first in a series focused on the Time Travel Debugging (TTD) technology developed by Microsoft that was explored in detail during a recent independent research period.

KNOTWEED Assessment Summary
KNOTWEED deploys the Subzero spyware through the use of 0-day exploits for Adobe Reader and the Windows operating system. Once initial access is gained, it uses different sections of Subzero to maintain persistence and perform actions on the host.

Detecting Exploitation of CVE-2021-44228 (Log4j2) with Elastic Security
This blog post provides a summary of CVE-2021-44228 and provides Elastic Security users with detections to find active exploitation of the vulnerability in their environment. Further updates will be provided to this post as we learn more.

Detection rules for SIGRed vulnerability
The SIGRed vulnerability impacts all systems leveraging the Windows DNS server service (Windows 2003+). To defend your environment, we recommend implementing the detection logic included in this blog post using technology like Elastic Security.

Elastic's response to the Spring4Shell vulnerability (CVE-2022-22965)
Provide executive-level details about CVE-2022-22965, a recently-disclosed remote code execution (RCE) vulnerability also known as “Spring4Shell”.

Detecting and responding to Dirty Pipe with Elastic
Elastic Security is releasing detection logic for the Dirty Pipe exploit.
Getting the Most Out of Transformers in Elastic
In this blog, we will briefly talk about how we fine-tuned a transformer model meant for a masked language modeling (MLM) task, to make it suitable for a classification task.

Hunting For In-Memory .NET Attacks
As a follow up to my DerbyCon presentation, this post will investigate an emerging trend of adversaries using .NET-based in-memory techniques to evade detection

Hunting In Memory
Threat Hunters are charged with the difficult task of sifting through vast sources of diverse data to pinpoint adversarial activity at any stage in the attack.
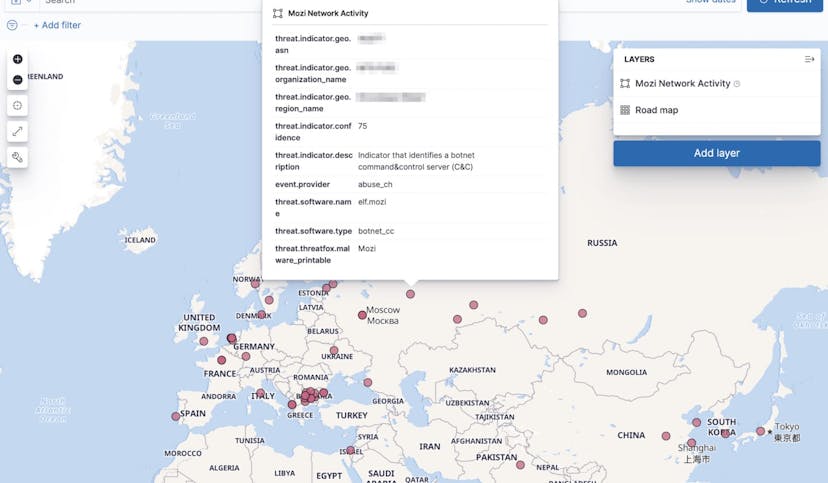
Collecting and operationalizing threat data from the Mozi botnet
The Mozi botnet is an ongoing malware campaign targeting unsecured and vulnerable networking devices. This post will showcase the analyst journey of collecting, analyzing, and operationalizing threat data from the Mozi botnet.

Detection and response for the actively exploited ProxyShell vulnerabilities
In the last week, Elastic Security has observed the exploitation of Microsoft Exchange vulnerabilities associated with ProxyShell. Review the post to find newly released details about this activity.

Nimbuspwn: Leveraging vulnerabilities to exploit Linux via Privilege Escalation
Microsoft 365 Defender team released a post detailing several identified vulnerabilities. These vulnerabilities allow adversarial groups to escalate privileges on Linux systems, allowing for deployment of payloads, ransomware, or other attacks.

Testing your Okta visibility and detection with Dorothy and Elastic Security
Dorothy is a tool for security teams to test their visibility and detection capabilities for their Okta environment. IAM solutions are frequently targeted by adversaries but poorly monitored. Learn how to get started with Dorothy in this post.

Embracing offensive tooling: Building detections against Koadic using EQL
Find new ways to build behavioral detections against post-exploitation frameworks such as Koadic using Event Query Language (EQL).

Practical security engineering: Stateful detection
By formalizing stateful detection in your rules, as well as your engineering process, you increase your detection coverage over future and past matches. In this blog post, learn why stateful detection is an important concept to implement.
