A CISO’s perspective: Why I’ve read the Elastic Global Threat Report

It’s that time of year again. Fall leaves are turning colors, families are gearing up for the holidays, and many vendors are releasing different reports during cybersecurity month. Our researchers at Elastic Security Labs released the 2023 Global Threat Report last week after months of analysis on more than 1 billion data points. As the CISO of Elastic®, my team and I leveraged last year’s report findings and predictions to strategize for the changing threat landscape. This year, I expect our team will dig further on the new threat research discoveries and predictions. In particular, my team and I are taking note of the following insights while preparing for the next year.
Key threat research from the report
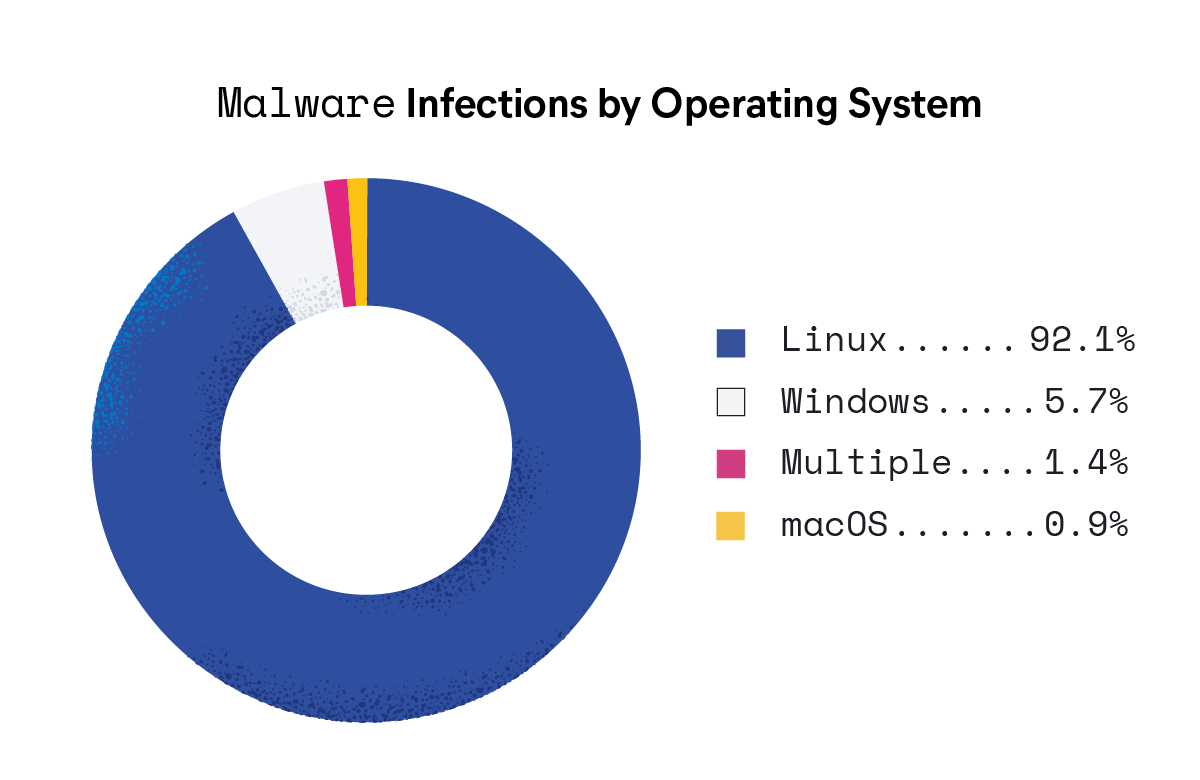
Malware threat: Linux dominance
This report reveals that almost all observed malware infections — 92% — occurred on Linux systems. This is relevant as we continue to expand our use of cloud environments that mostly run on Linux boxes and underscores the urgency for security professionals to address Linux security within their organizations. Additionally, the report provides valuable insights into the prevalence and diversification of ransomware — specifically, a launch into ransomware-as-a-service (RaaS) families.
Cloud security threat: focus on the basics
With enterprises transitioning to cloud-based environments, the report emphasizes that threat actors are taking advantage of misconfigurations, lax access controls, unsecured credentials, and a lack of the principle of least privilege (PoLP). Security teams must take note of basic security hygiene issues to protect their environment and work towards implementing the security features supported by cloud providers while monitoring for common credential abuse attempts.
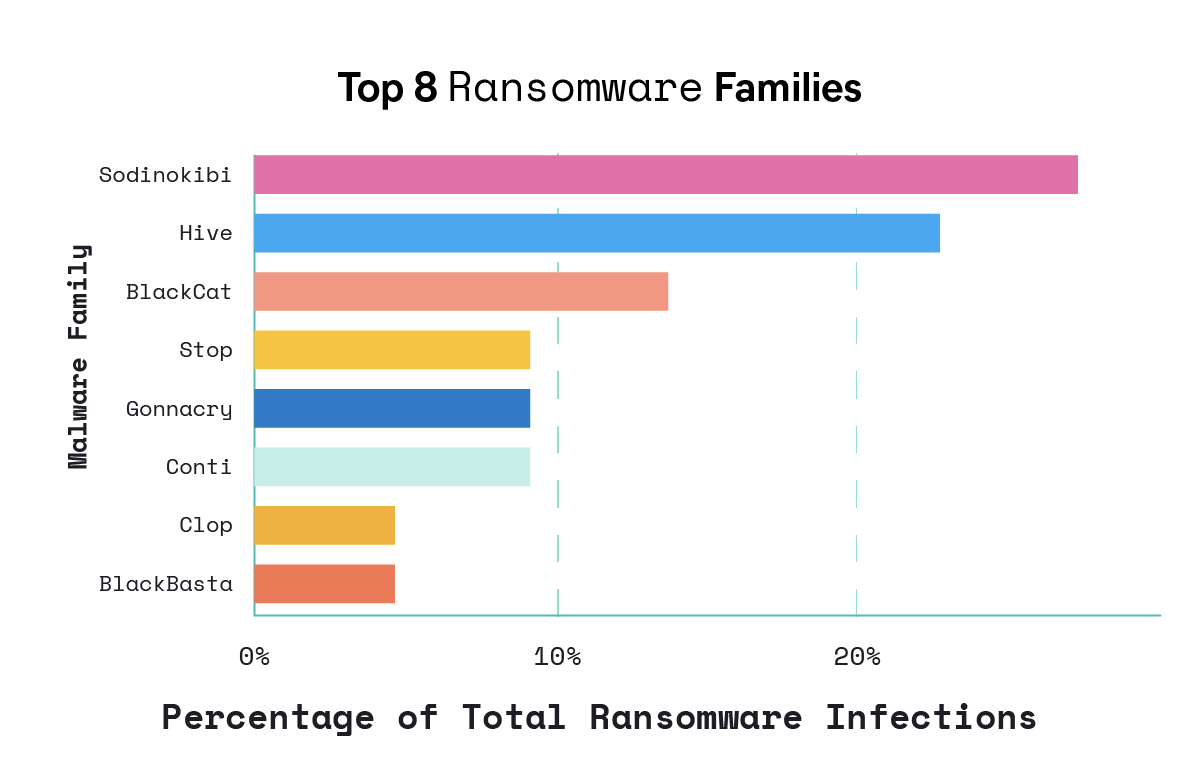
Malware threat: malware-as-a-service
The report points out that the majority of malware observed comprises a small number of highly prevalent ransomware families (featured below) and commercial off-the-shelf (COTS) tools. This is a significant concern, as financially motivated threat communities are increasingly adopting malware-as-a-service (MaaS) capabilities. We need to recognize the importance of developing security functions with a broad view of low-level behaviors to expose threats that might otherwise go unnoticed.
Open security threat: reducing costs
It’s also a rising trend that open-source tools are being used in attacks, as seen in Elastic Security Labs articles on r77 rootkit and JOKERSPY. Open source tools are widely available and often legitimate software applications with sanctioned purposes. They are commonly used by security professionals, system administrators, and developers. As a result, the use of such tools can fly under the radar easily, making it challenging for security professionals to distinguish between legitimate and malicious use.
In response to these challenges, security professionals need to adopt a multifaceted approach to security. This includes proactive threat intelligence, anomaly detection, behavioral analysis, and continuous monitoring. Staying informed about emerging open source tools and their potential applications in attacks is crucial.
Endpoint behavior threat: defense tampering
The report underscores that sophisticated threat groups are adopting tactics to evade security measures by withdrawing to edge devices and platforms where visibility is minimal. It highlights the need for security professionals to evaluate the tamper-resistant nature of their endpoint security sensors and consider monitoring projects to track vulnerable device drivers used to disable security technologies.
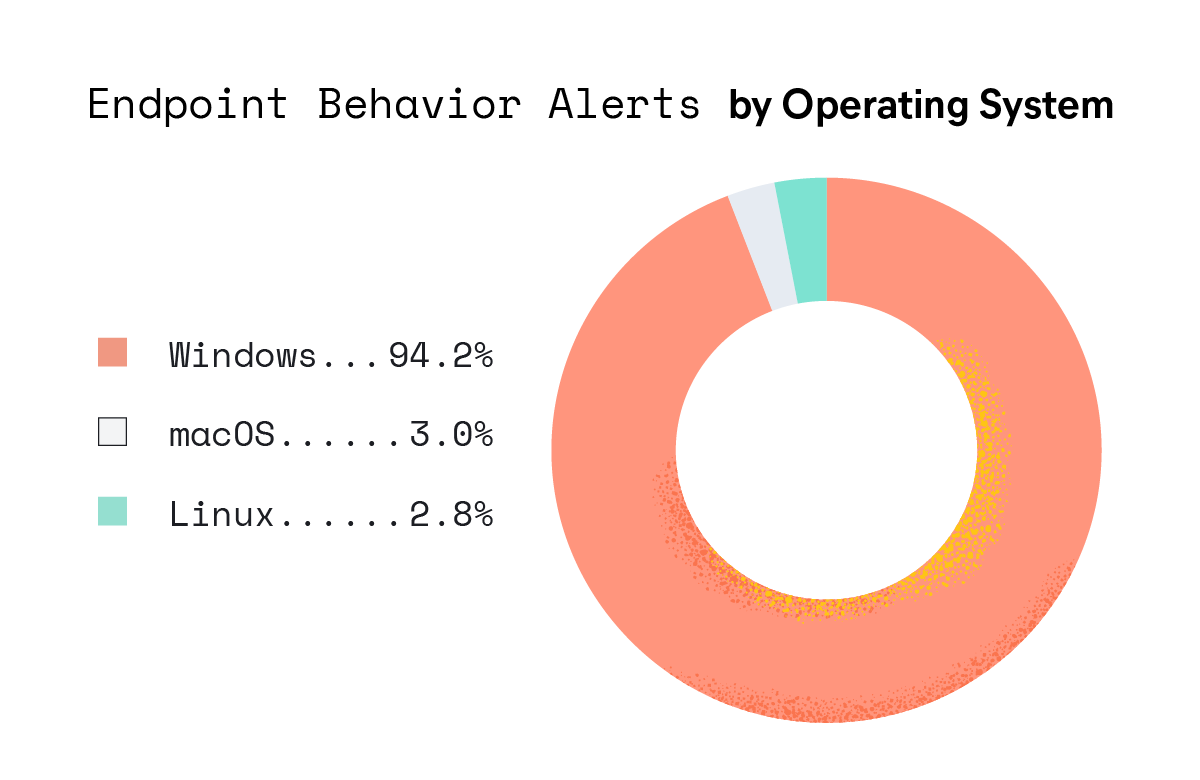
Stay ahead of threats
The Elastic Global Threat Report paints a picture of a borderless threat landscape. Adversaries have transformed into criminal enterprises, seeking to monetize their attack strategies. Open source tools and commodity malware like RaaS and the use of AI have lowered the entry barriers for attackers. But there is a silver lining: the rise of automated detection and response systems that empower all engineers to better defend their infrastructures.
As security professionals, we have to stay abreast of the threat landscape. Collaboration within the security community to share threat information and develop effective countermeasures is essential to address these growing challenges. Reports like the Elastic Global Threat Report help educate us and ultimately raise the water level in the security industry. Reading the 2023 Global Threat Report not only sheds light on emerging trends, but it also equips us with the knowledge required to make informed decisions about our security strategies. Join us for a deeper discussion of the insights in this webinar.













