Secure your deployments on Elastic Cloud with Google Cloud Private Service Connect
We are pleased to announce the general availability of the Google Cloud Private Service Connect integration with Elastic Cloud. Elastic Cloud VPC connectivity is now available to all customers across all subscription tiers and cloud providers (AWS, Microsoft Azure, and Google Cloud).
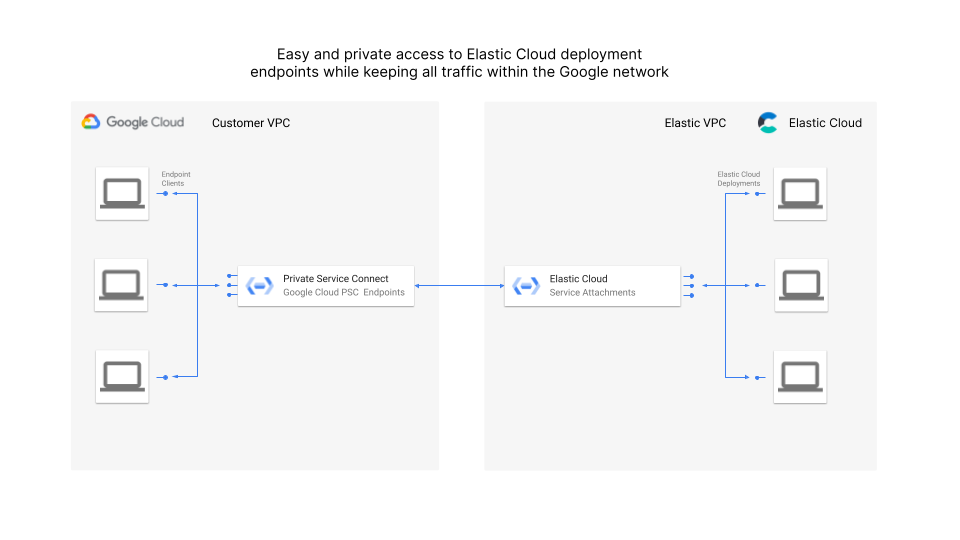
Private Service Connect allows you to create private and secure connections from your clients running in your Google Cloud environments to your Elastic Cloud deployment endpoints running on Google Cloud. Private Service Connect provides service endpoints in your virtual private cloud (VPC) that provide private connectivity and policy enforcement, allowing you to easily connect to services like Elastic Cloud. All the traffic remains within the Google network, and it’s easy to set up and scale.
 Prerequisite: Obtain a static IP on Google Cloud for assigning to the endpoint.
Prerequisite: Obtain a static IP on Google Cloud for assigning to the endpoint.
Step 1: Create a Private Service Connect endpoint using the Elastic Cloud service attachment
Create a Private Service Connect Endpoint using the service attachment URI for the region your deployment is hosted on in Elastic Cloud.
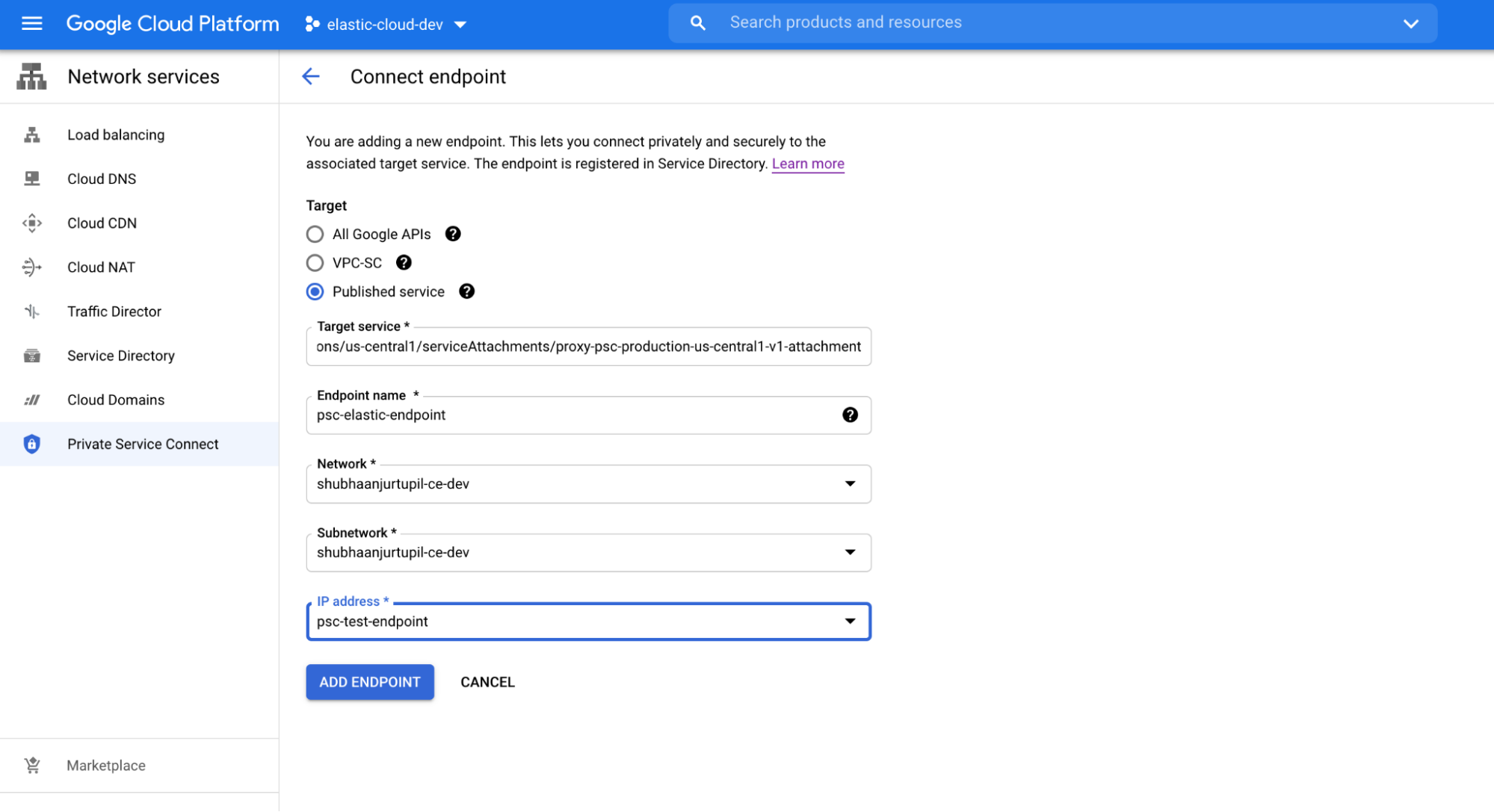
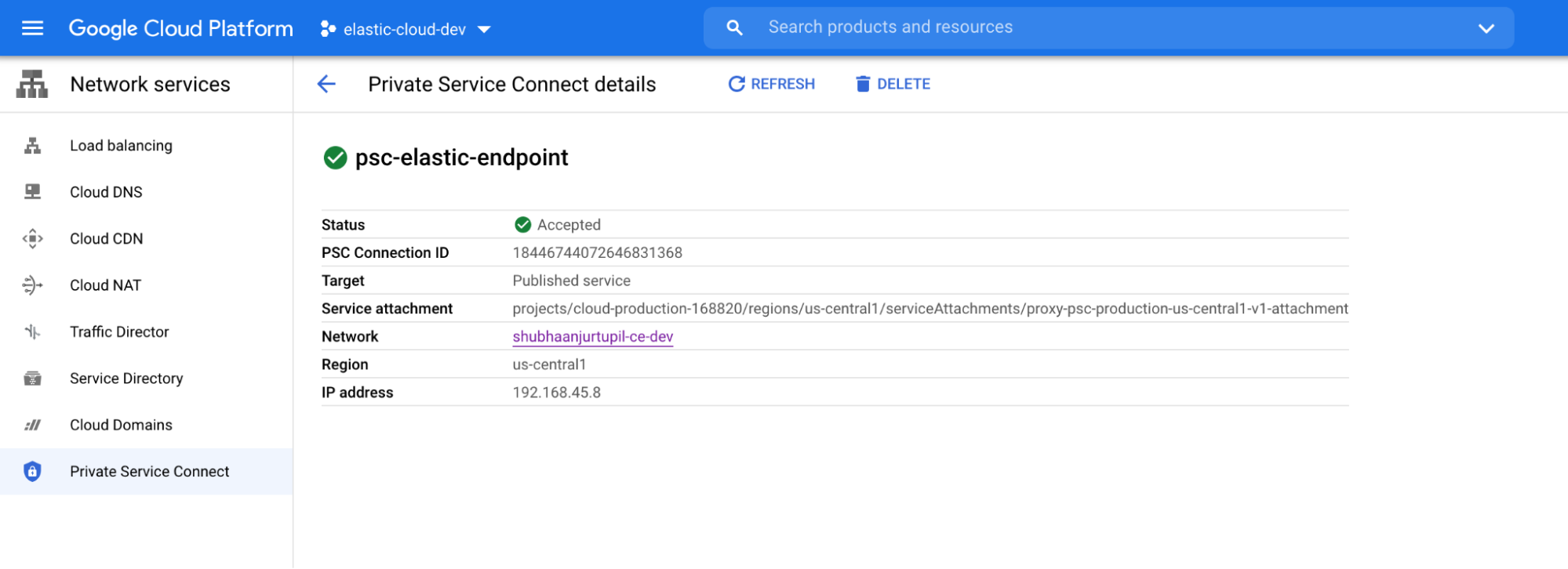
Once you create the endpoint, it will be accepted automatically in a few seconds.
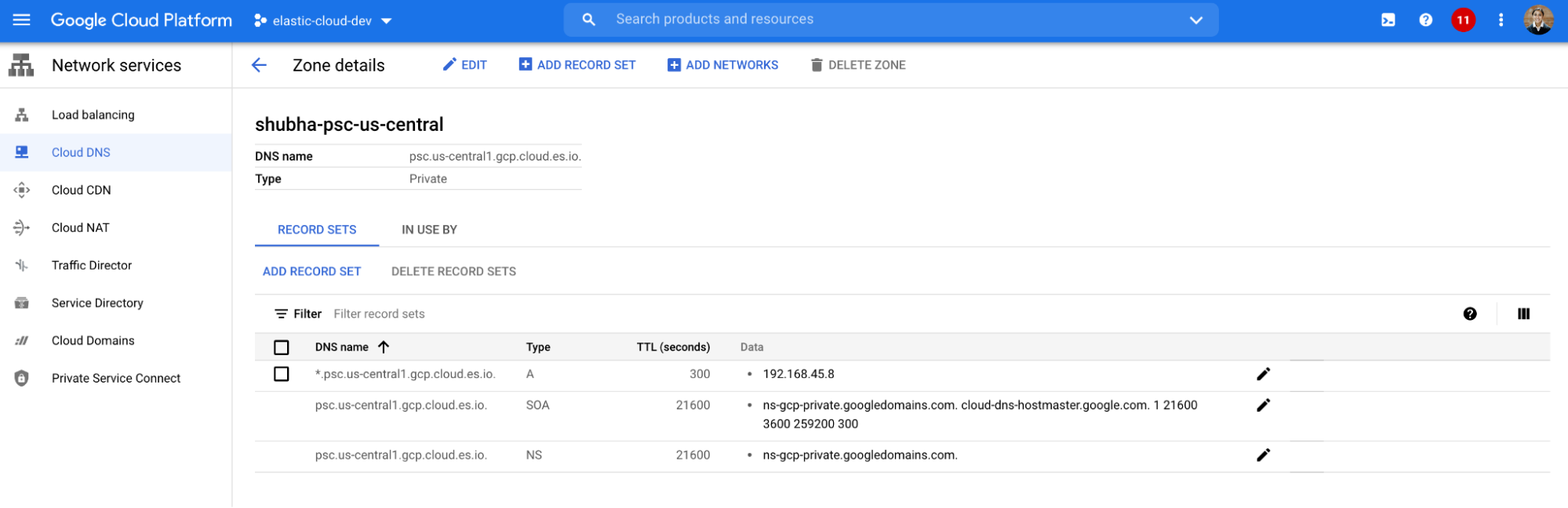
Step 2: Create a domain name service (DNS) record for the Private Service Connect endpoint
Create a private DNS zone using the zone name for the region. Add an A name record to resolve to the IP address of the Private Service Connect endpoint, and add your network to the private hosted zone. This will help with accessing the endpoint using a friendly domain name.
Step 3: Configure the necessary information for Elastic Cloud to allow traffic only from the explicitly allowed endpoints.
Create a traffic filter of type Private Service Connect endpoint using the endpoint ID created in Step 1.
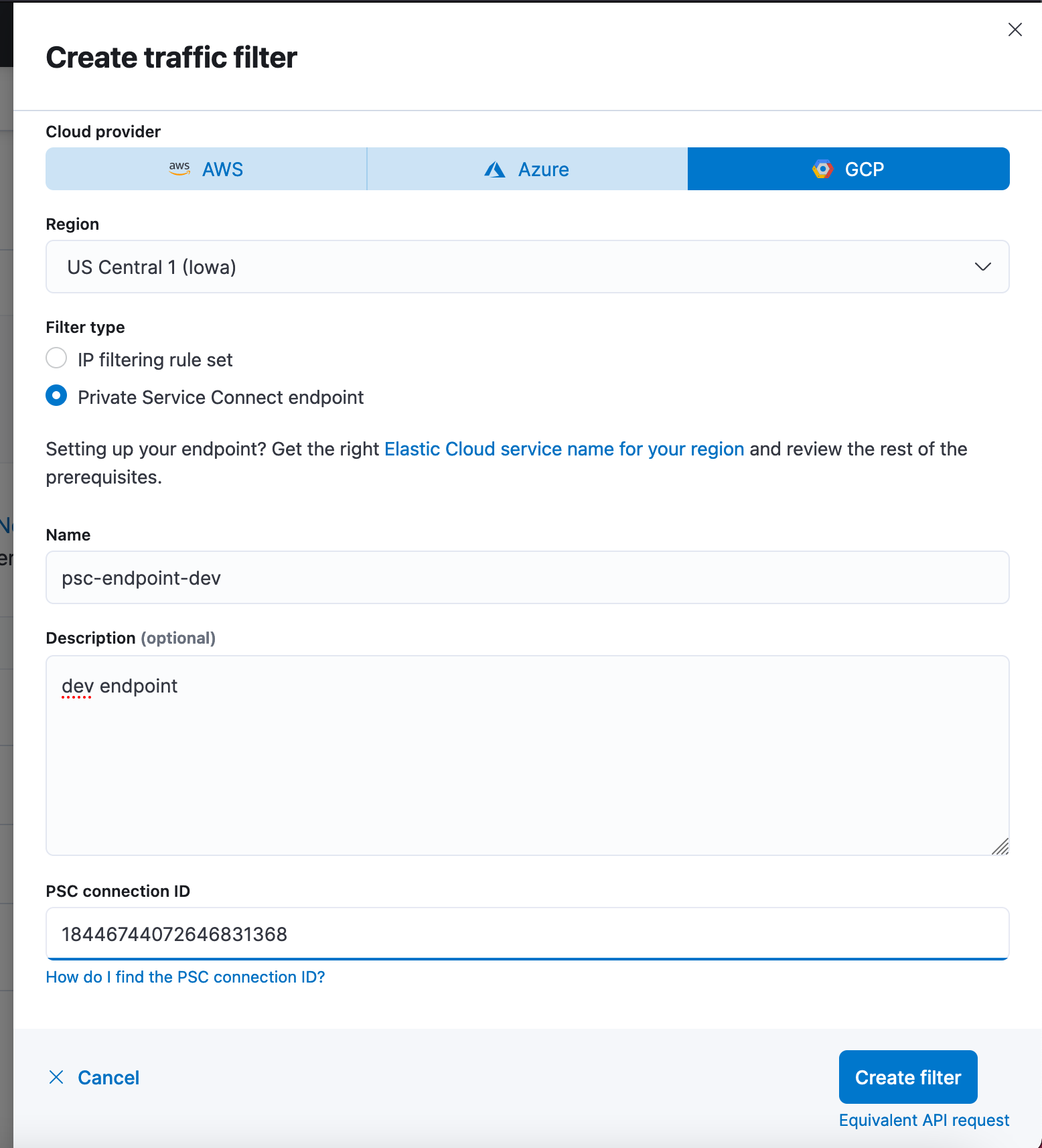
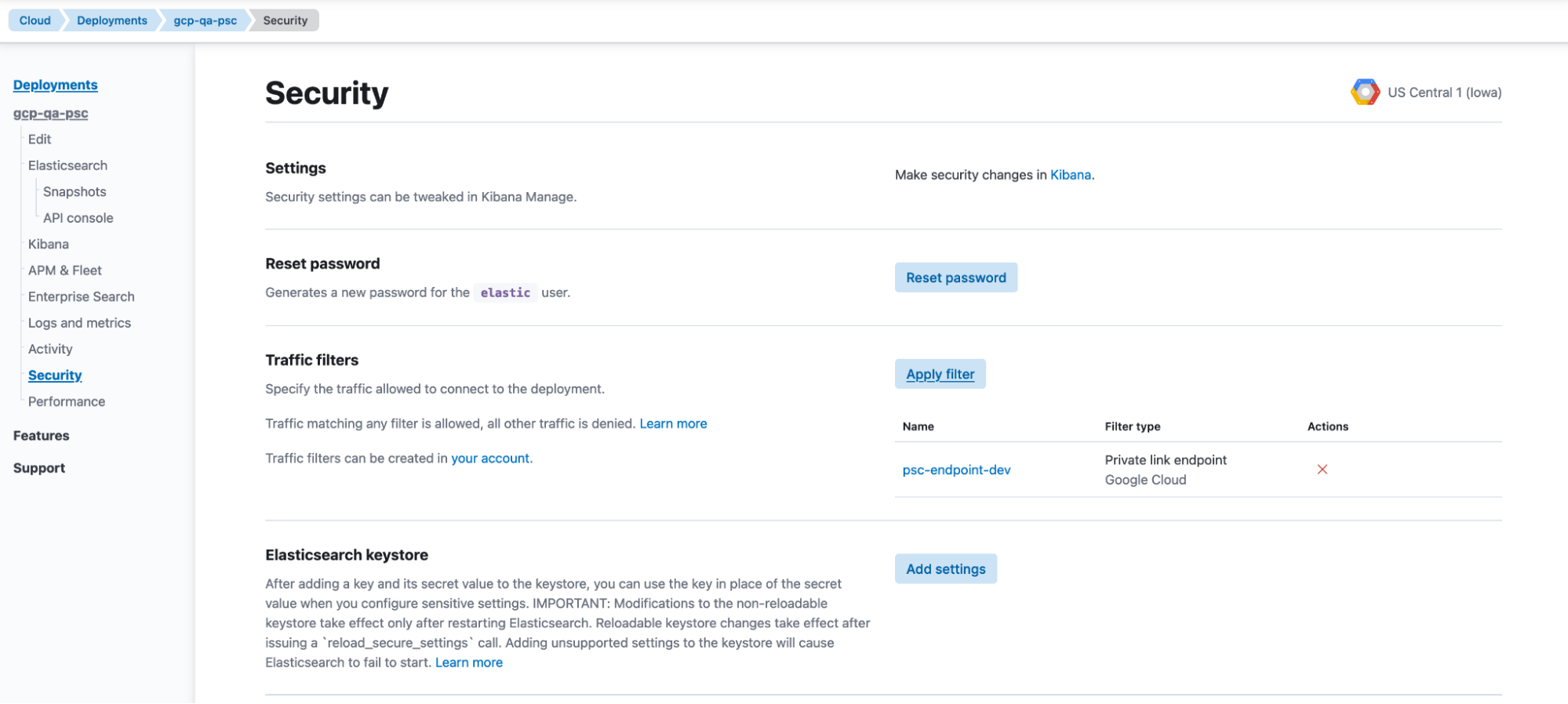
Associate the traffic filter to one or more deployments
You can associate this traffic filter with one or more deployments hosted in the region, and only traffic from explicitly allowed VPC (though the Private Connect endpoints) will be allowed to the respective deployment endpoints.
Getting started
If you’re ready to use Private Service Connect with your Elastic deployment, visit Elastic Cloud (Elasticsearch Managed Service) through the Google Cloud Marketplace and follow the steps outlined in the Google Cloud private Service Connect documentation. As a special treat, we have a coupon that you can request, which will be applied against your Google Cloud billing account. For more information, check out our Get Started Guide or try our self-paced Qwiklab.