MITRE ATT&CK® round 2 APT emulation validates Elastic’s ability to eliminate blind spots
Editor’s Note — August 19, 2020: The Elastic Endpoint Security solution mentioned in this post is now referred to as Elastic Security. The broader Elastic Security solution delivers endpoint security, SIEM, threat hunting, cloud monitoring, and more. Future mentions of Elastic endpoint security will refer to the specific anti-malware protection that users can enable in Ingest Manager.
Six months ago we celebrated the joining of forces between Endgame and Elastic under the banner of Elastic Security and announced the elimination of per endpoint pricing. Simultaneously, while the newest members of Elastic Security were getting acquainted with the Elastic SIEM team, a few of our analysts were locked away in an office at MITRE HQ for round 2 of MITRE’s APT emulation. MITRE evaluated Elastic Endpoint Security (formerly Endgame), and other major endpoint security vendors based on APT29.
MITRE recently published the results of that evaluation. To make it easy for anyone to analyze and investigate the results, our team gathered all of MITRE’s raw evaluation data on vendor performance into a free and open Kibana dashboard and released a detailed blog on the process.
So what about the results for Elastic Security? While we’re excited by the results, you won’t hear us say “we won” or “we beat vendor X” because that is not the purpose of this evaluation, and it is misleading to our users. MITRE specifically cautions against making direct comparisons using their data, noting that such comparisons are complicated and encouraging anyone using the results to consider factors outside the evaluation. The evaluation is meant to provide a standardized way to understand a vendor’s scope of visibility across a single attack.
Elastic Security’s mission is to protect the world’s data from attack. We must eliminate two existential threats to securing today’s environments:
- Blind spots. Adversaries can look like the average user — to find the threat, organizations need full visibility and fidelity into all of their security-relevant data.
- Access. Enterprise-grade security has been gated off from the masses due to price and complexity. Only a small subset of users get access to these vendor solutions.
MITRE’s evaluation emphasized the blind spot challenge — emulating many of the techniques using PowerShell (through obfuscation), Windows Remote Management (WinRM), Windows Management Instrumentation (WMI), and other operating system capabilities — to blend in with the administrative users of an organization.
Eliminating blind spots
Visibility across all data and the ability to action on that data in real-time to stop damage and loss is critical to any security organization. Elastic Security is built on the Elastic Stack by the same experts that have built one of the most successful open source projects in the world for ingesting, searching, and analyzing data at massive scale. In addition, it isn’t just the ability to store and access the data — you also need fidelity in the data you collect. As adversaries blend in with common users, using living off the land techniques by leveraging PowerShell, WMI, and other operating system tools, it is imperative the data collection is built to defeat defense evasion.
Elastic performed well across all detection categories, clearly demonstrating our ability to collect and analyze the data. Elastic ranked at the top in terms of the fewest number of misses and most relevant telemetry collected. Images are included below, but remember you can always access the raw data yourself via the open Kibana dashboard.
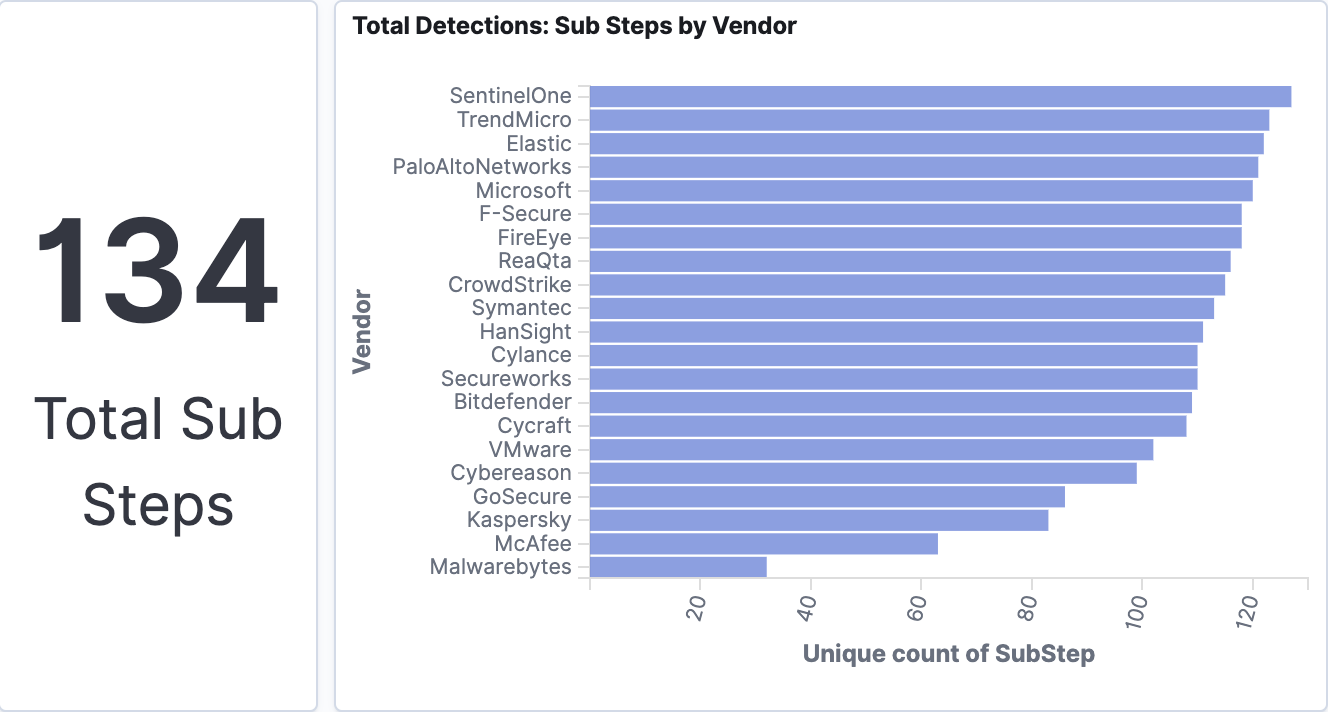
The visualization above shows the total detections by vendor and demonstrates the total coverage across the emulated APT scenario by sub-step. Elastic identified 100% of the 20 attack steps and more than 90% of the 134 sub-steps.
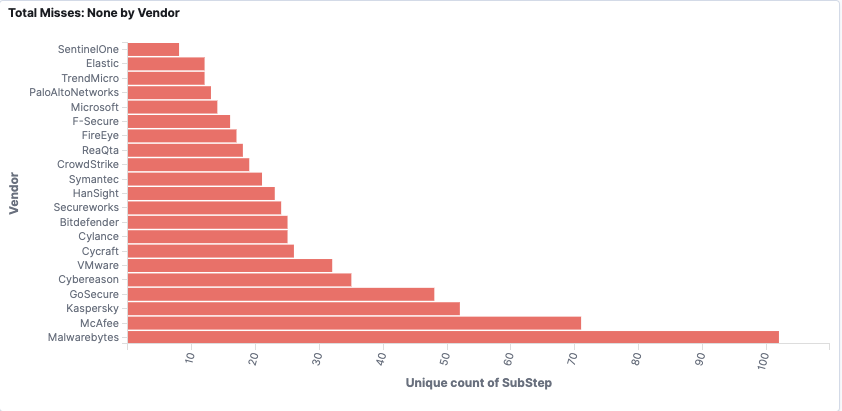
The visualization above shows vendors’ potential visibility gaps in the emulated APT scenario by sub-step. Elastic had very few overall misses in the sub-steps and identified every major step in the emulated attack.
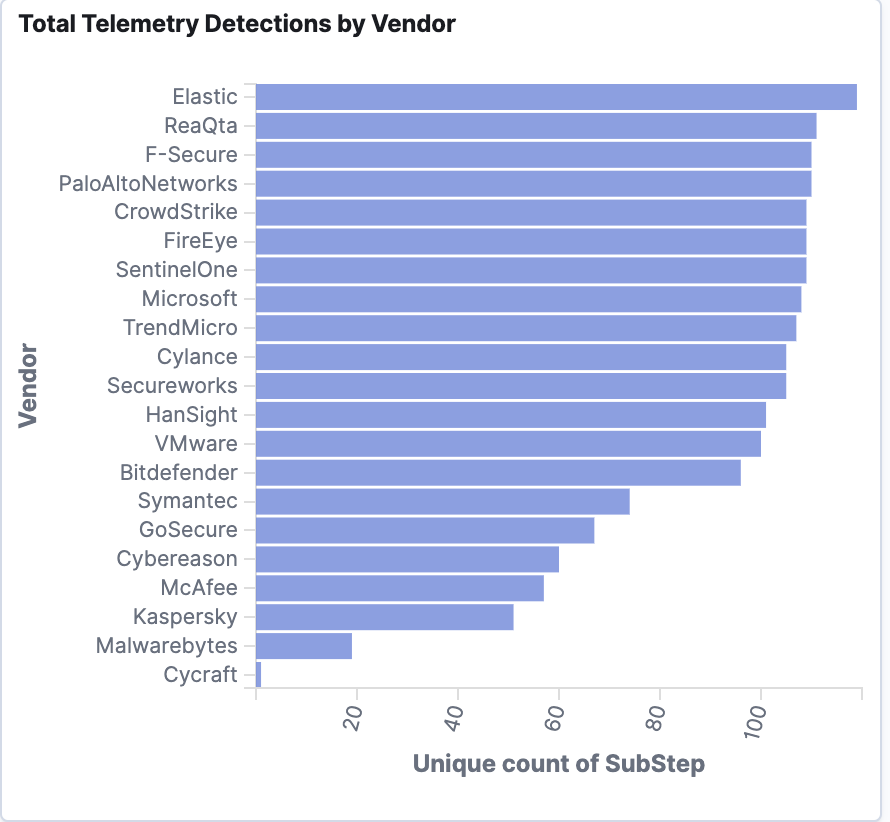
As the image above shows, Elastic Security eliminates blind spots by providing actionable telemetry for the sub-steps in the attack emulation.
Making security available to everyone
This evaluation provides further validation to existing Elastic Security customers of our commitment to focusing on the hardest problem in cybersecurity: hands-on-keyboard attackers. We hope these results continue to excite and entice people to learn more about new product developments as we work to integrate Elastic Endpoint Security capabilities directly into the Elastic Stack, making them available for anyone.
The past six months have yielded amazing advances for Elastic Security. From numerous feature-rich releases to a “Strong Performer” ranking in The Forrester Wave™: Enterprise Detection and Response Q1 2020 report. With MITRE’s evaluations executed six months ago, it’s humbling to reflect on just how far Elastic Endpoint Security has come since those tests were conducted, and how much more we have to offer security practitioners today.
Last year, we made our SIEM free and open and followed up by eliminating endpoint-based pricing. In the coming months, we will continue to add new capabilities toward our vision for converging security domains into a single, streamlined solution. We encourage you to stay connected with us as we plan to share more exciting news about new developments for Elastic Endpoint Security very soon.