What’s new in Elastic Security 7.11: prebuilt cloud detections + an enhanced UI
Elastic Security 7.11 equips security teams with prebuilt detection rules and machine learning jobs for cloud apps and hosts, streamlined SecOps workflows, enhanced usability and accessibility, and more. Let’s dive in to its most impactful enhancements.
Prebuilt detections for cloud apps and hosts
Detection rules for cloud applications
Elastic Security 7.11 delivers prebuilt detection rules that help secure the modern enterprise stack. Elastic Security research engineers have developed and tested this content to automatically detect techniques and behaviors related to attacks against cloud applications like Google Workspace, Microsoft 365, and Okta. These new detection rules complement our existing detections for IaaS technologies, such as AWS, Azure, and Google Cloud.
Centralized detection for Windows environments
Elastic Security 7.11 expands the detection rules available to spot attacks against Windows environments. Like other prebuilt Elastic security analytics content, these rules are aligned with MITRE ATT&CK®, putting a particular focus on addressing attacker techniques like persistence, privilege escalation, and lateral movement.
Cross-platform anomaly detection ML jobs
Elastic Security research engineers have updated 14 machine learning jobs to detect anomalies across a broader set of data from both Windows hosts (via Endpoint Security or Winlogbeat) and Linux hosts (via Endpoint Security or Auditbeat). These updated ML jobs are made possible by abstracted categorization fields introduced in Elastic Common Schema (ECS) 1.7, and enable users to function flexibly with any ECS-compliant source of Windows or Linux events — whether from Elastic or third-party technologies.
SUNBURST detection rules and DGA ML jobs
Elastic Security research engineers have developed a package of detection rules for spotting SUNBURST/Solorigate command-and-control activity and suspicious SolarWinds activity. To protect your organization, check out the free and open SUNBURST detection rules published on our public detection rules repo.
Elastic Security has also published an experimental package of signatureless detection methods for detecting domain generation algorithms (DGA) related to the SUNBURST attack. The package helps practitioners see through the blizzard of obfuscatory DNS calls DGAs generate to spot command-and-control connections. It’s clever stuff, applying both supervised ML trained by Elastic Security and unsupervised ML sharpened within the user environment.
Accelerated alert management workflows
MITRE ATT&CK® sub-technique context
Elastic Security 7.11 introduces support for MITRE ATT&CK sub-techniques, providing a deeper understanding of how attacks are unfolding in your organization. Our solution has long been mapped to ATT&CK tactics and techniques, and with our latest release, we are one of the first security solutions to implement support for ATT&CK sub-techniques at the detection layer.
Expanded set of rule actions
Elastic Security 7.11 greatly expands the flexibility of what the detection engine can do upon generation of an alert, streamlining SOC efficiency and bolstering effectiveness. Alert actions are now available for Jira, ServiceNow, and IBM Resilient, joining existing actions for email, webhook, PagerDuty, and Slack.

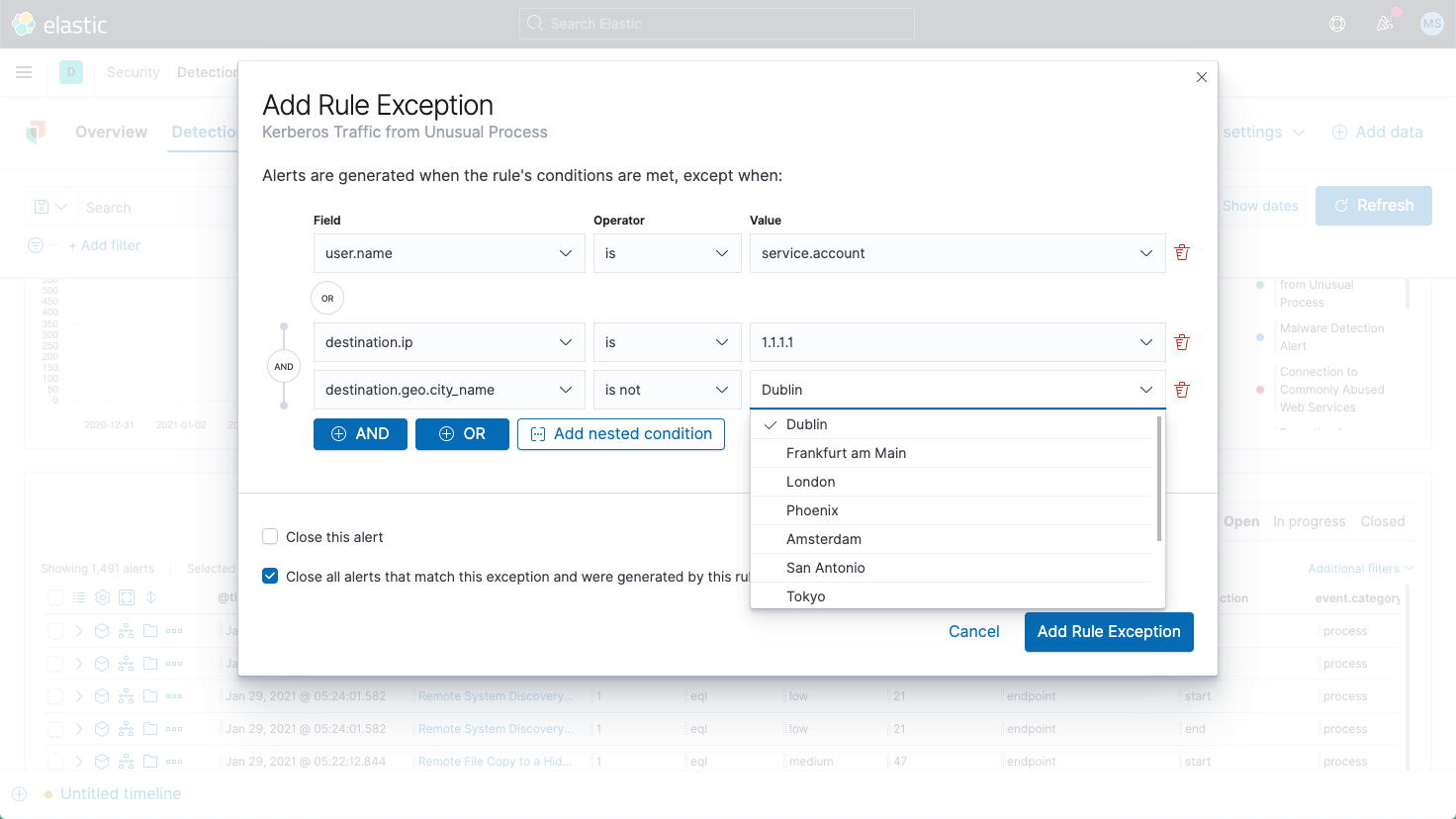
Rule exceptions for threshold rules and ML rules
Users can now create exceptions for ML and threshold rules, supporting a unified rule management experience and enabling users to create exception conditions for ML rules without modifying underlying ML jobs. If the general availability of the detection engine, now coupled with this release of rules exceptions, gets you excited, good news — there's even more to come.
Detailed alert notifications
Users can now customize alert notification details to include information from alert fields (e.g., user, IP address), enabling more useful notifications than are possible with just rule fields (e.g., rule name) alone. Security teams can implement notifications on a per-rule basis to deliver relevant context for specific alerts to third-party workflow tools like Slack and ServiceNow, accelerating analysis.
Efficient alert management
Elastic Security 7.11 streamlines alert management, helping analysts maintain velocity and address threats more quickly. Directly from the Alerts table, analysts can attach one or more alerts to a case, aligning responders and associating relevant data and notes. Updating the status of a case automatically updates the status of associated alerts. Over time, leveraging this capability builds an organizational intelligence repository.
Enhanced usability and accessibility for every analyst
Timeline, refreshed
Updates to the Timeline workspace drive efficient threat hunting, alert triage, and investigation. Experienced as a whole, these changes represent a major advancement in the usability of Timeline.
Tabbed Timeline information
Tabs on the Timeline workspace now provide quick access to filtered sets of information: Query shows all events related to the current search; Analyzer shows the Visual event analyzer; Notes provides immediate access to analyst entries; and Pinned shows events pinned or commented upon by analysts, supporting collaboration.
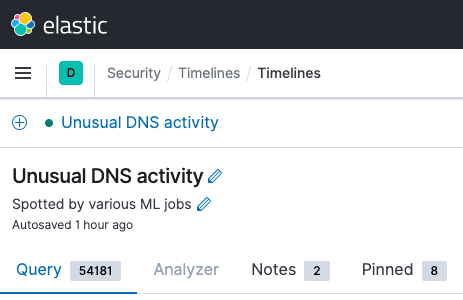
Timeline switching and updates
Analysts are free to switch between current and previous timelines, to enable both interactive and historical investigations, without needing to switch contexts or open new browser tabs. From the same area, analysts can update the Timeline query by dragging and dropping field values. An unsaved timeline workflow reminds analysts to preserve their findings.
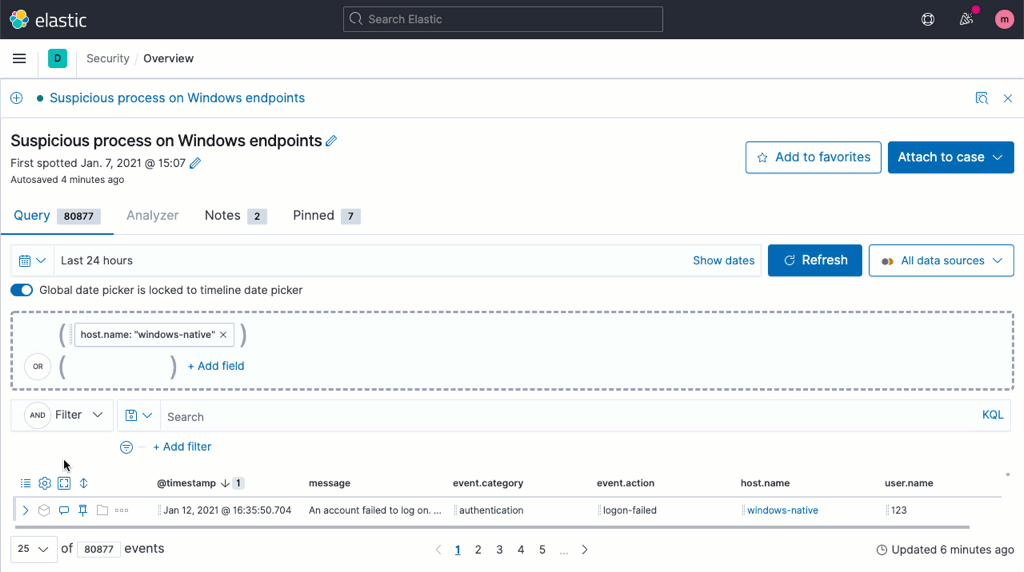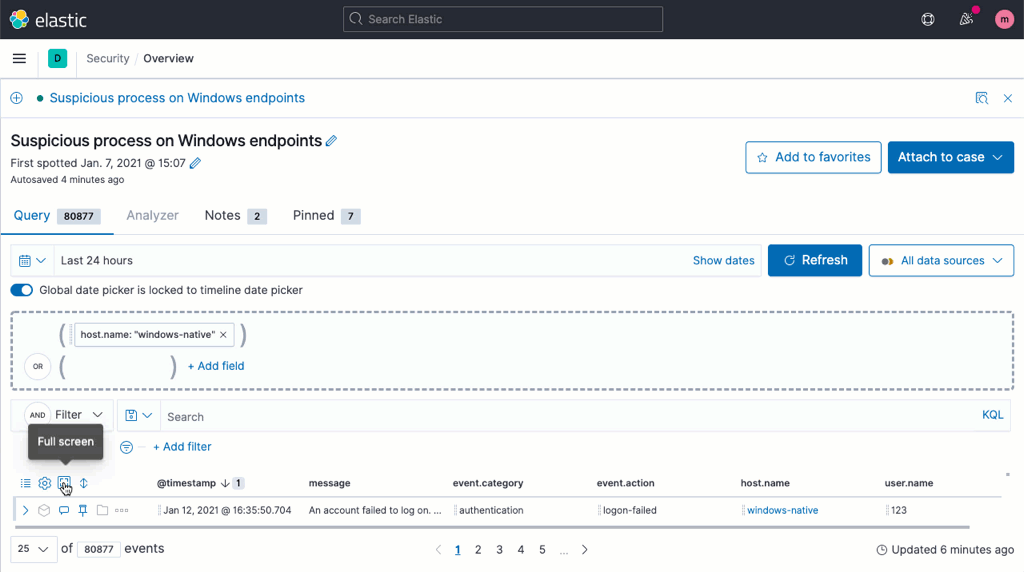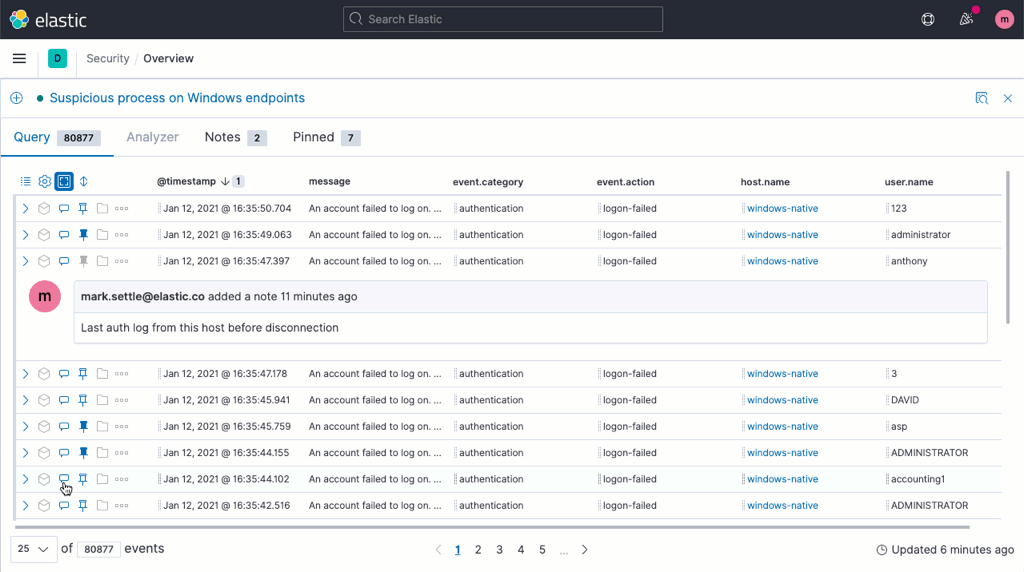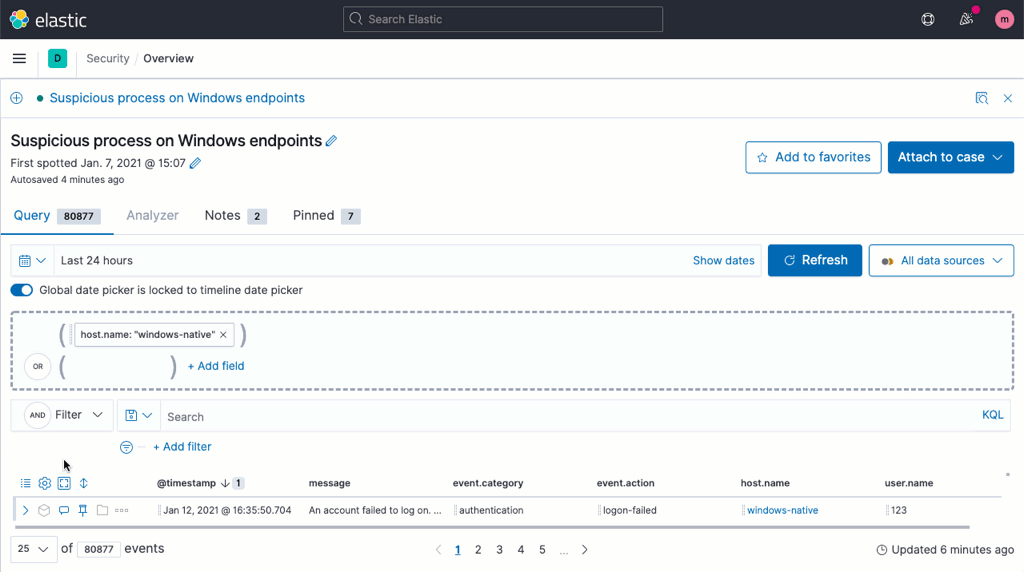
Full-screen view
In version 7.11, the full-screen view for analysts shows more events than before, improving analyst visibility.
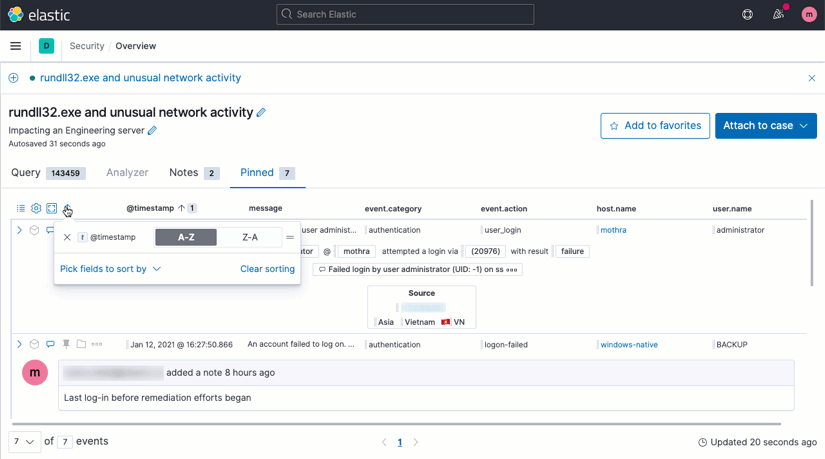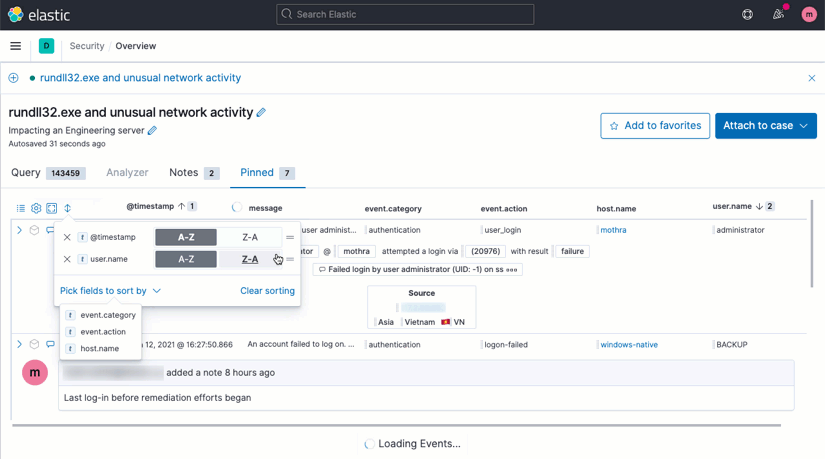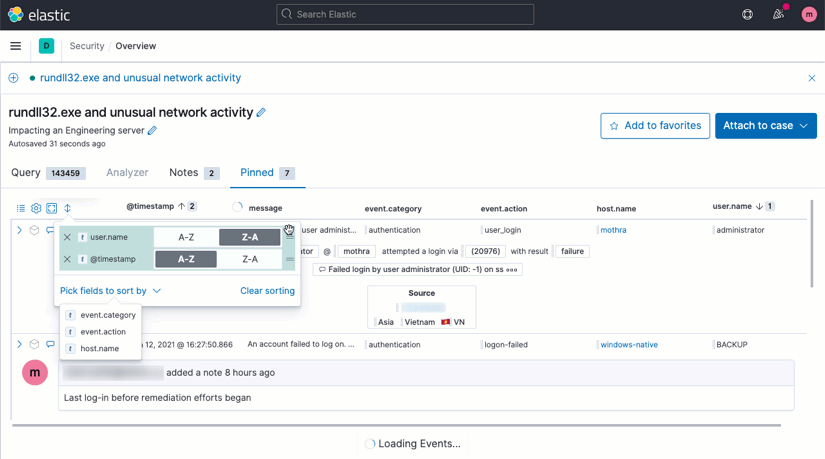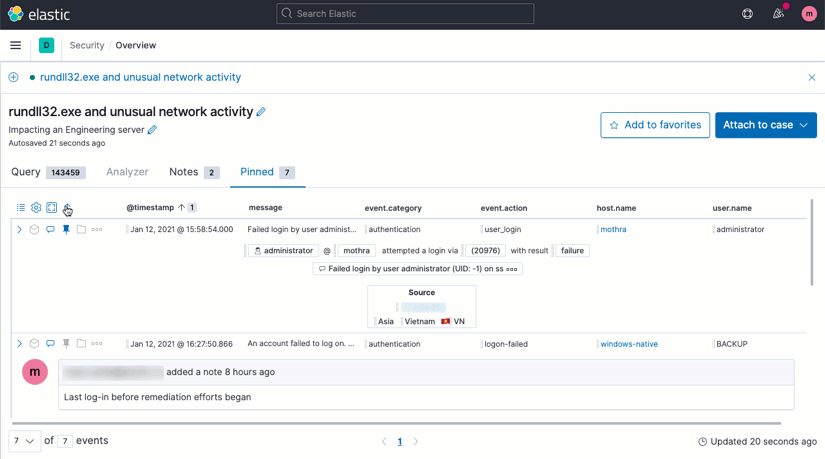
Multicolumn sorting
Making sense of your data is faster, now, with multicolumn sorting via a drag-and-drop menu or via the headers themselves.
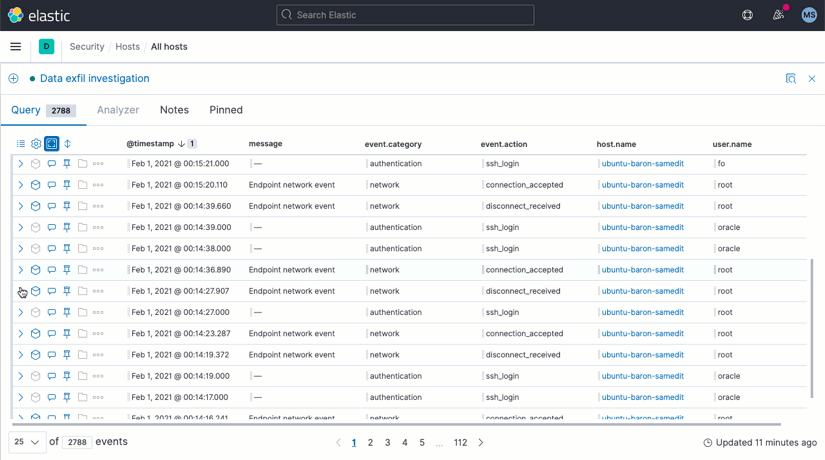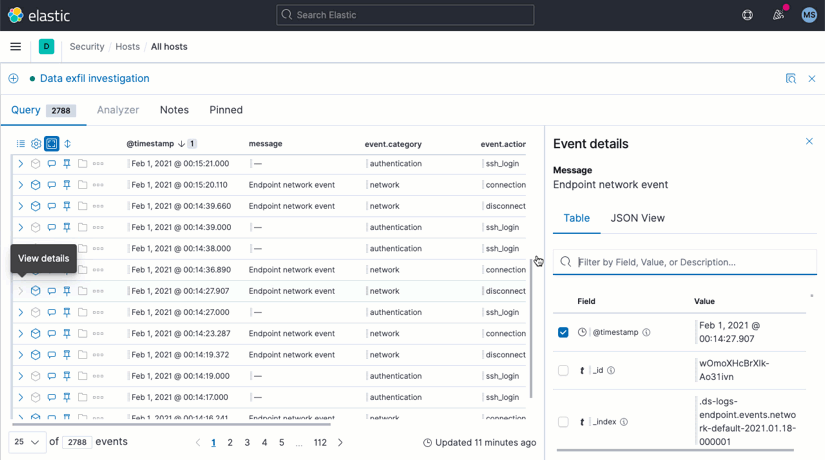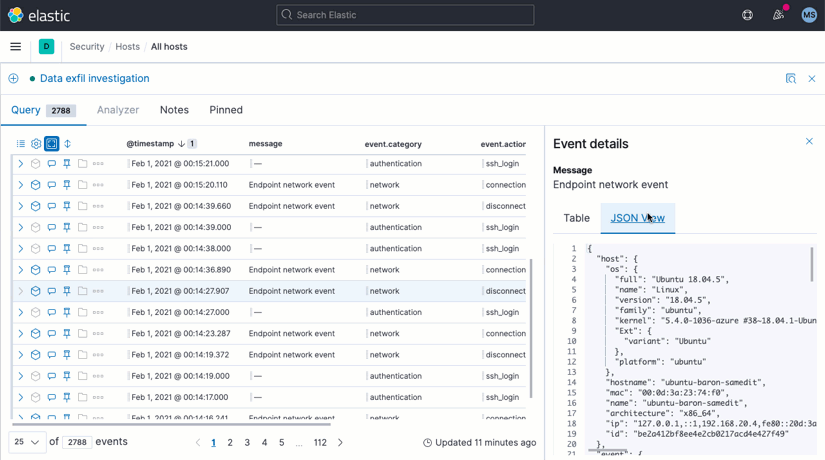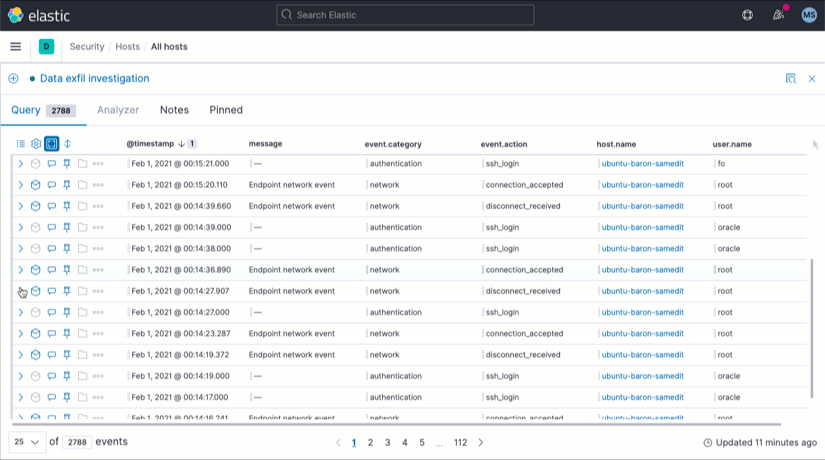
Event details view
Access event details without losing sight of surrounding data by opening the new Event details view. Less scrolling, faster analysis.
Accessible navigation for all
Elastic Security 7.11 improves accessibility, with greatly enhanced keyboard navigation and screen reader support. We undertook this project to serve users who count on accessibility being built into the tools they use every day. We suspect other power users will love it, too (hello, hotkeys!).
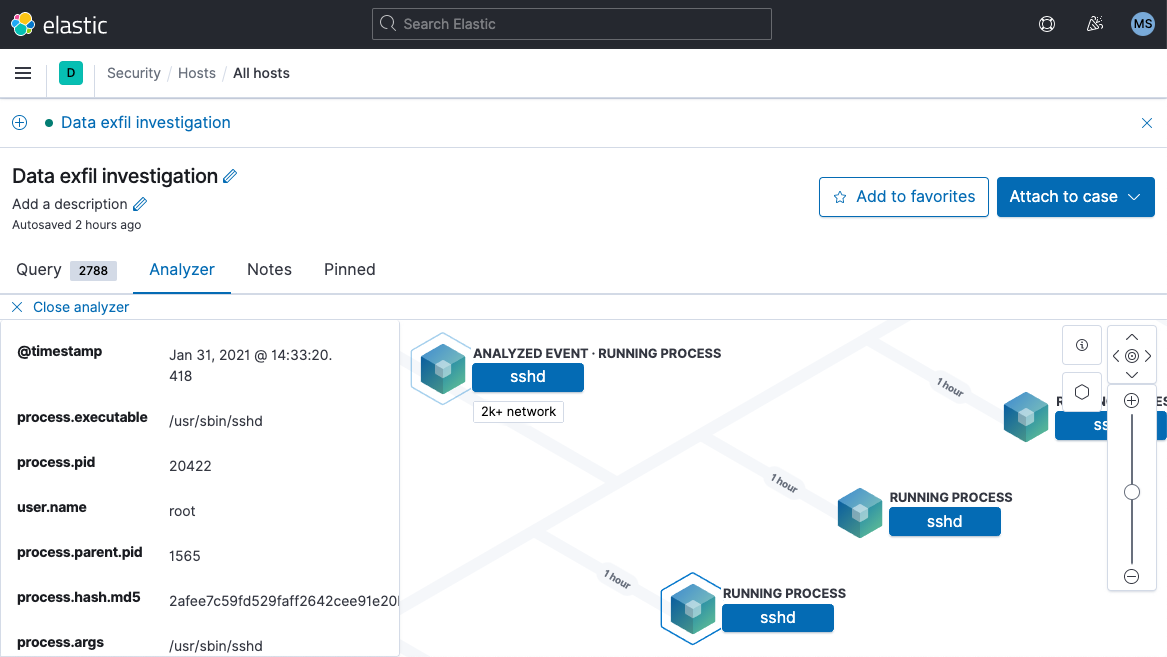
Richer host event visualization
With 7.11, our visual event analyzer is snappier and shows a richer set of information. If you’re collecting host data with Elastic Agent, visualize it here — and starting with this release, you can now explore host data collected with Winlogbeat, too.
Expanded data integrations
More data sources for Elastic Agent
Elastic Agent now collects several data sources that previously required Filebeat or Winlogbeat: Auditd, common event format (CEF), Google Santa, Google Workspace, iptables, and osquery. These integrations enable organizations to collect data and prevent malware with a single agent.
Database activity log ingestion
Elastic Security 7.11 ingests database audit logs from MySQL Enterprise and Oracle Databases. With this new insight into user database activity, security teams can monitor when a user performs a search, deletes a table, updates a value, grants new or upgraded user access, or adjusts an audit policy. Ingesting this information enables numerous security and compliance use cases, including threat hunting and monitoring for data exfiltration, insider threats, and account compromise.
Snyk vulnerability data and audit logs
Elastic Security 7.11 supports the ingestion of open source vulnerabilities reported by Snyk, enabling the identification of potential exposure during the software development lifecycle. The release also provides access to Snyk audit data, providing visibility into user activity within Snyk and supporting compliance with applicable regulatory frameworks.
Default collection of Windows events by Elastic Agent
Starting with version 7.11, new installations of Elastic Agent on Windows systems are configured by default to ingest Windows security events right out of the box. This provides instant insight into host activity, no further steps required.
Malware prevention for the masses
Registered antivirus solution with Windows
Windows now recognizes Elastic as an official antivirus solution, giving customers the option to disable Windows Defender without causing users to be warned that Windows isn’t secure. This registration also helps demonstrate compliance with any requirements related to the protection of endpoints with an antivirus solution.
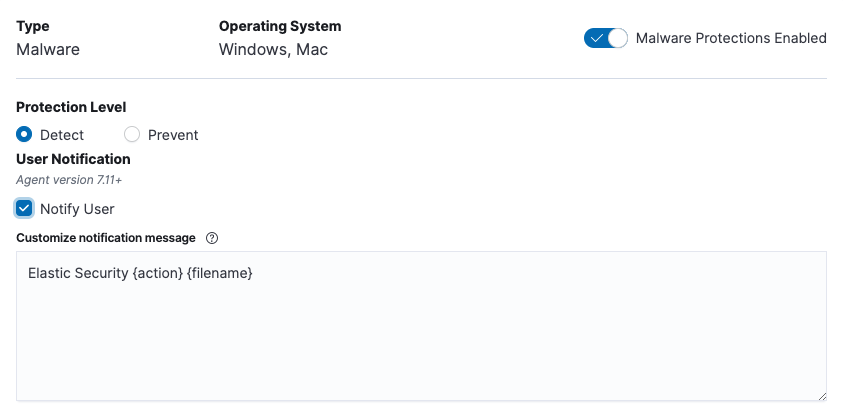
Configurable system notifications
With Elastic Security 7.11, organizations can customize the system notifications shown to users when malware is prevented — or, if the organization prefers, configure notifications not to be presented at all. For example, an organization might want to notify users that malware has been stopped and that they should contact the help desk at a specific email address or phone number for further instructions.
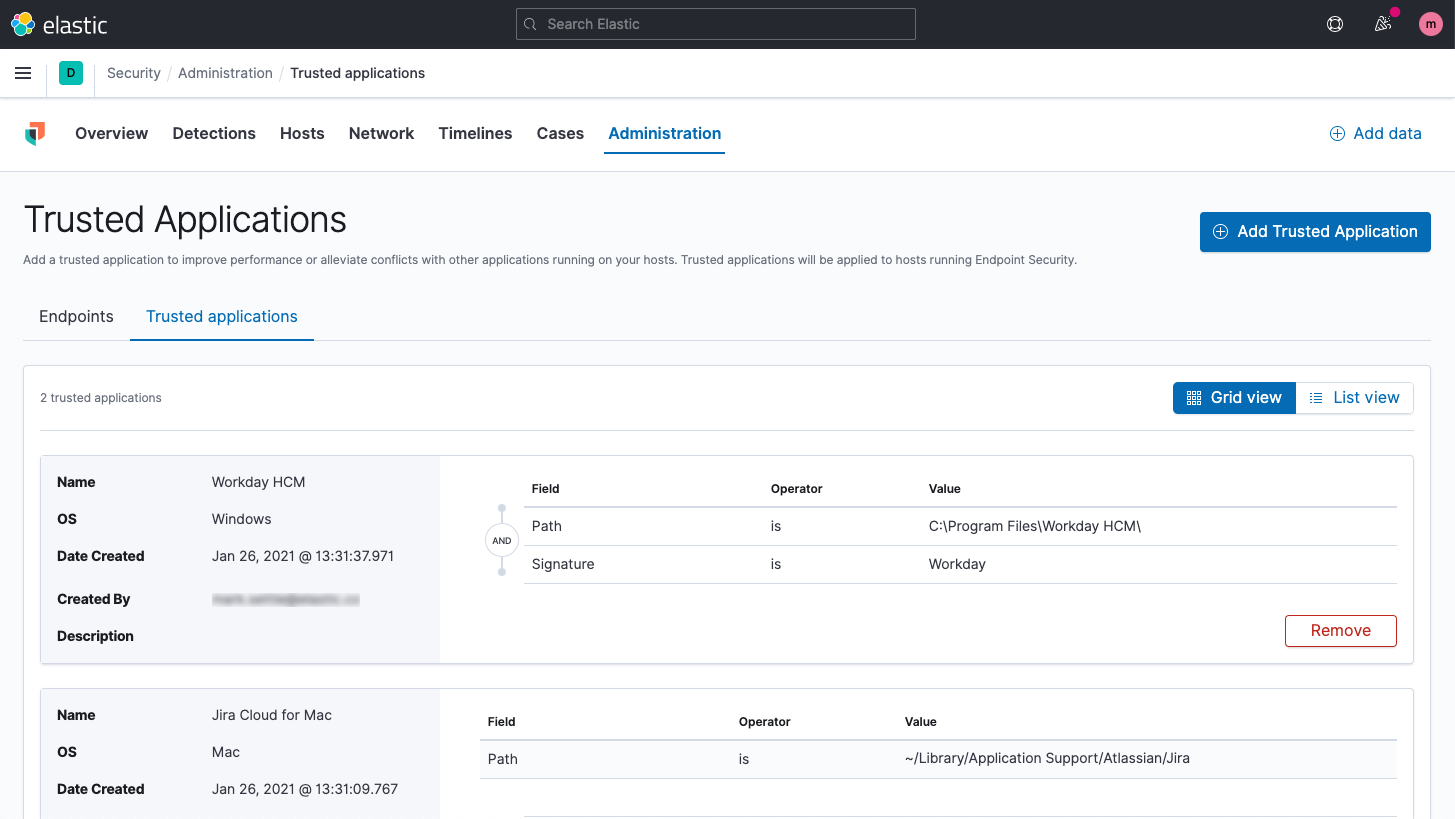
Trusted applications definable by signer
Trusted applications can now be defined in Elastic Endpoint Security for Windows systems by the software signer, path, and/or hash. The trusted application designation prevents Elastic Endpoint Security from tracking or blocking actions by specified applications, eliminating associated operational issues. It supports Windows, macOS, and Linux systems.
Streamlined lifecycle management for Elastic Endpoint Security
A collection of usability enhancements to Fleet (the administrative interface for Elastic Agent) simplify the deployment and management of Elastic Endpoint Security. A new Policies tab provides a holistic view across available and deployed agent policies. Users can quickly see information such as how many agents are operating with specific policies, with detailed lists immediately available. If users wish to view and interact with this data differently, they can create their own view with the Custom tab.
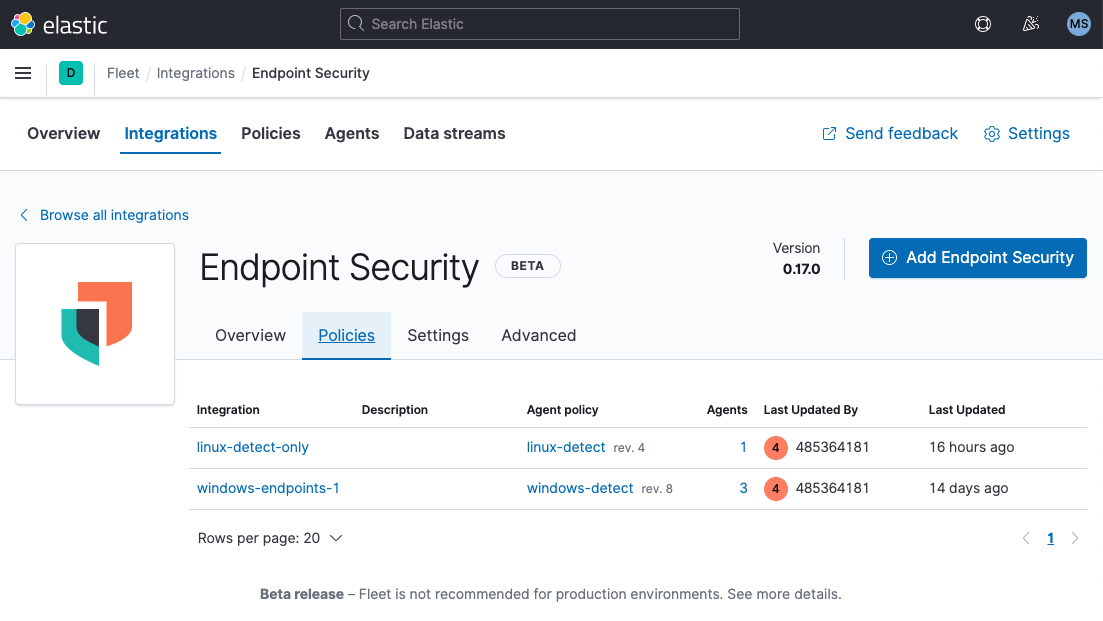
With one click, users can access policy details. And within the same workflow, if they have the requisite permissions, they can update the policy.
Improved data accessibility with searchable snapshots
Elastic 7.11 brings searchable snapshots into general availability and introduces a cold tier leveraging object stores from vendors like Amazon, Azure, GCP and MinIO. Security teams can now enjoy direct access to years of high-volume data and cost savings of up to 50%, supporting use cases like hunting, investigation, compliance, threat profiling, forensic analysis, adversary emulation, and more. Extended retention of security data ensures that even when facing extremely long dwell times, practitioners have the data they need. Data sources like cloud platforms and applications, IDS/IPS, DNS, wire data, host activity, observability data, MDM, IoT, OT — and many others typically too costly to incorporate in day-to-day operations — can be kept operationally ready at greater scale. Security teams can even apply automated detections across data that would otherwise be archived or dropped.
Get started today
Want to give Elastic Security a spin? Experience all that 7.11 has to offer on Elastic Cloud, or check out an Elastic Security demo. Already have ECS-formatted data in Elasticsearch? Just upgrade to the latest version of the Elastic Stack to start detecting and responding. Want to see it in action? Watch the best sessions from our recent ElasticON Security virtual event.