Configure the Endpoint Security integration policy
editConfigure the Endpoint Security integration policy
editAfter the Elastic Agent is installed with the Endpoint Security integration, several protections features — including preventions against malware, ransomware, memory threats, and malicious behavior — are automatically enabled on protected hosts (a Platinum or Enterprise license feature). If needed, you can update the integration policy to configure protection settings, event collection, antivirus settings, and trusted applications to meet your organization’s security needs.
You must have admin permissions in Kibana to configure an integration policy.
To configure the integration policy:
- In the Elastic Security app, go to Manage → Endpoints to view the Endpoints list.
- From the Policy column, select the integration policy you want to configure. The integration policy configuration page appears.
-
Review the following settings on the Policy settings tab and configure them as appropriate:
-
Click the Trusted applications tab to review the list of trusted applications assigned to this integration policy. On this tab, you can:
- Expand and view a trusted application — Click the arrow next to the application’s name.
- View full details for a trusted application — Click the actions button (…), then select View full details.
- Unassign a trusted application (Platinum or Enterprise subscription) — Click the actions button (…), then select Remove from policy. This does not delete the trusted application; this just unassigns it from the current policy.
- Assign an existing trusted application (Platinum or Enterprise subscription) — Click Assign trusted application to policy, then select an application from the Assign trusted applications flyout. This view lists any existing trusted applications that aren’t already assigned to the current policy.
You can’t create new trusted applications while configuring an integration policy. To create a new trusted application, go to Manage → Trusted applications.
Malware protection
editMalware prevention on the Elastic Agent detects and stops malicious attacks by using a machine learning model that looks for static attributes to determine if a file is malicious or benign.
By default, malware protection is enabled on Windows, macOS, and Linux hosts. To disable malware protection, switch the Malware protections enabled toggle off.
Malware protection levels are:
- Detect: Detects malware on the host and generates an alert. The agent will not block malware. You must pay attention to and analyze any malware alerts that are generated. Notifications do not appear by default. Select the Notify User option to enable them.
-
Prevent (Default): Detects malware on the host, blocks it from executing, and generates an alert. Notifications appear by default. Deselect the Notify User option to disable them.
Platinum and Enterprise customers can customize these notifications using the
Elastic Security {action} {filename}syntax.
Ransomware protection
editBehavioral ransomware prevention detects and stops ransomware attacks on Windows systems by analyzing data from low-level system processes. It is effective across an array of widespread ransomware families — including those targeting the system’s master boot record.
Ransomware protection is a paid feature and is enabled by default if you have a Platinum or Enterprise license. If you upgrade to a Platinum or Enterprise license from Basic or Gold, ransomware protection will be disabled by default.
Ransomware protection levels are:
- Detect: Detects ransomware on the host and generates an alert. The Elastic Agent will not block ransomware. Select the Notify User option to enable user notifications.
-
Prevent (Default): Detects ransomware on the host, blocks it from executing, and generates an alert. User notifications are enabled by default. Deselect the Notify User option to disable them.
Platinum and Enterprise customers can customize these notifications using the
Elastic Security {action} {filename}syntax.
Memory threat protection
editMemory threat protection detects and stops in-memory threats, such as shellcode injection, which are used to evade traditional file-based detection techniques.
Memory threat protection is a paid feature and is enabled by default if you have a Platinum or Enterprise license. If you upgrade to a Platinum or Enterprise license from Basic or Gold, memory threat protection will be disabled by default.
Memory threat protection levels are:
- Detect: Detects memory threat activity on the host and generates an alert. The Elastic Agent will not block the in-memory activity. Select the Notify User option to enable user notifications.
-
Prevent (Default): Detects memory threat activity on the host, forces the process or thread to stop, and generates an alert. User notifications are enabled by default. Deselect the Notify User option to disable them.
Platinum and Enterprise customers can customize these notifications using the
Elastic Security {action} {rule}syntax.
Malicious behavior protection
editMalicious behavior protection detects and stops threats by monitoring the behavior of system processes for suspicious activity. Behavioral signals are much more difficult for adversaries to evade than traditional file-based detection techniques.
Malicious behavior protection is a paid feature and is enabled by default if you have a Platinum or Enterprise license. If you upgrade to a Platinum or Enterprise license from Basic or Gold, malicious behavior protection will be disabled by default.
Malicious behavior protection levels are:
- Detect: Detects malicious behavior on the host and generates an alert. The Elastic Agent will not block the malicious behavior. Select the Notify User option to enable user notifications.
-
Prevent (Default): Detects malicious behavior on the host, forces the process to stop, and generates an alert. User notifications are enabled by default. Deselect the Notify User option to disable them.
Platinum and Enterprise customers can customize these notifications using the
Elastic Security {action} {rule}syntax.
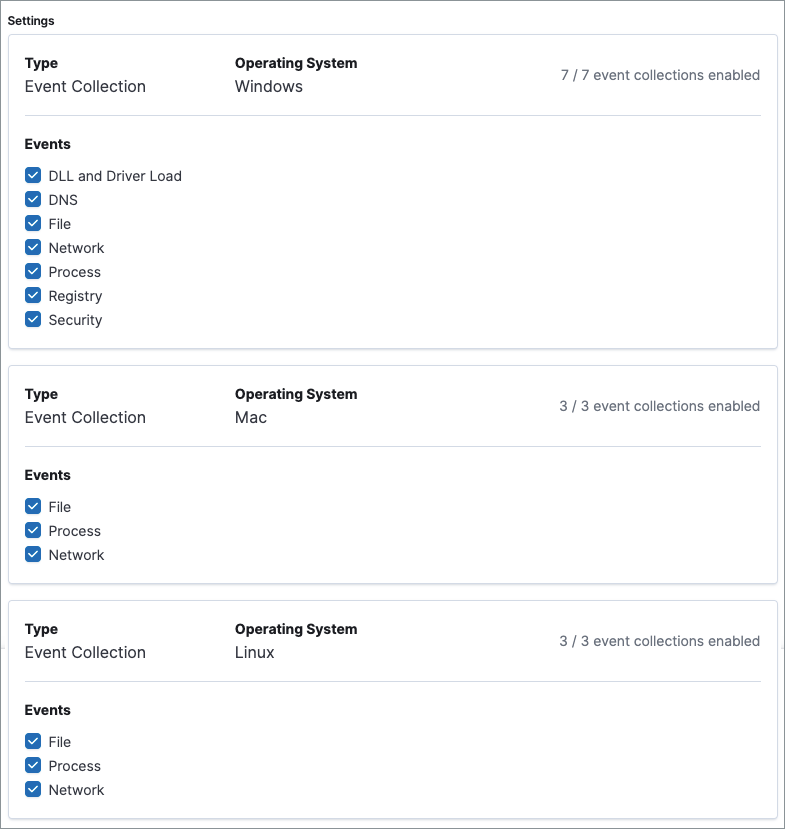
Event collection
editIn the Settings section, review the events that Elastic Agent will collect on each operating system. By default, all event data is collected. If you no longer want to collect a specific type of event, deselect it.
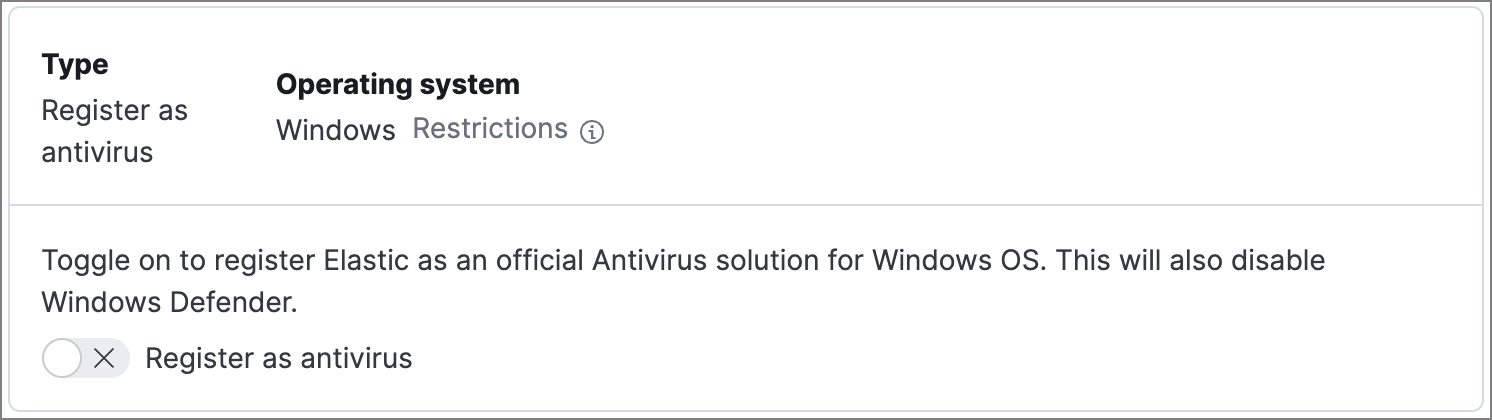
Register Elastic Security as antivirus (optional)
editIf you download the Elastic Agent version 7.10 or later on Windows 7 or above, you can configure Elastic Security as your antivirus software by switching the Register as antivirus toggle on.
Advanced policy settings (optional)
editUsers with unique configuration and security requirements can select Show Advanced Settings to configure the policy to support advanced use cases. Hover over each setting to view its description.
Advanced settings are not recommended for most users.
Save the general policy settings
editAfter you have configured the general settings on the Policy settings tab, click Save. A confirmation message appears.