Manage detection rules
editManage detection rules
editThe Rules page allows you to view and manage all prebuilt and custom detection rules.
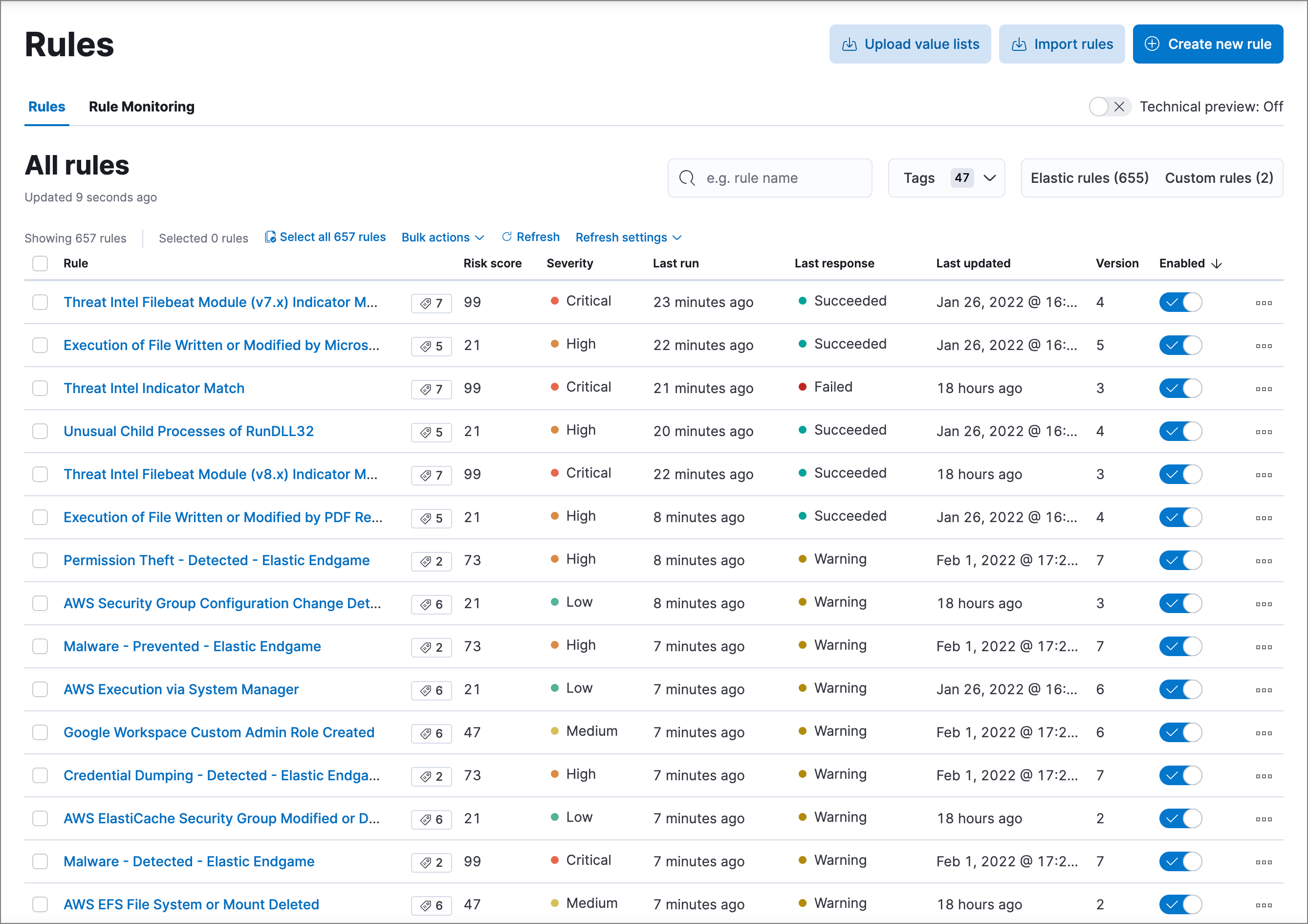
You can sort the rules by clicking the Rule, Last updated, or Enabled column header.
To sort by any other column, switch on the Technical preview toggle above the table. This experimental table view allows advanced sorting capabilities. If you experience performance issues when working with the table, you can turn this setting off.
On the Rules page, you can:
Load and activate prebuilt Elastic rules
editTo load the Elastic Security app’s prebuilt rules, go to Detect → Rules → Load Elastic prebuilt rules and Timeline templates).
You can then activate whichever rules you want. If you delete any prebuilt rules, a button appears that enables you to reload all of the deleted ones.
-
Apart from the Elastic Endpoint rule, prebuilt rules are not activated by default. If you want to modify a prebuilt rule, you must first duplicate it, then make your changes to the duplicated rule. All Elastic prebuilt rules are tagged with the word
Elastic.To learn how to enable detection rules in Elastic Security, watch the tutorial at the end of this topic.
- Automatic updates of Elastic prebuilt rules are supported for the current Elastic Security version and the latest three previous minor releases. For example, if you’re on Elastic Security 8.10, you’ll be able to use the Rules UI to update your prebuilt rules until Elastic Security 8.14 is released. After that point, you can still manually download and install updated prebuilt rules, but you must upgrade to the latest Elastic Security version to receive automatic updates.
Select and duplicate all prebuilt rules
edit- Go to Detect → Rules.
- In the All rules table, click Select all (number) rules.
- Click Bulk actions → Duplicate.
- Select the Custom rules tab.
You can then modify the duplicated rules and, if required, delete the prebuilt ones.
Download latest prebuilt Elastic rules
editAs of Elastic Stack >=7.13.0, you can download the latest version of Elastic prebuilt rules outside of a regular release cycle. This feature ensures you have the latest detection capabilities before upgrading to the latest Elastic Stack.
To download the latest version of prebuilt rules:
- In Kibana, go to Management → Integrations.
- Search for "Prebuilt Security Detection Rules."
-
Select the integration, then select the Settings tab. The integration settings page is displayed.
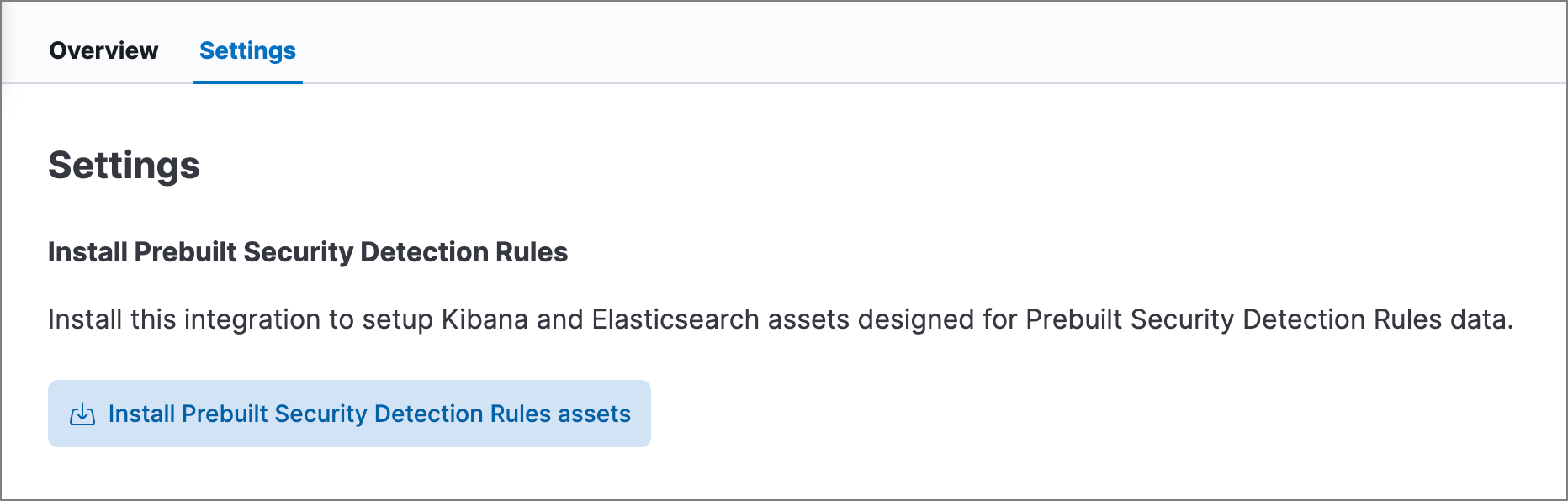
- Click Install Prebuilt Security Detection Rules assets.
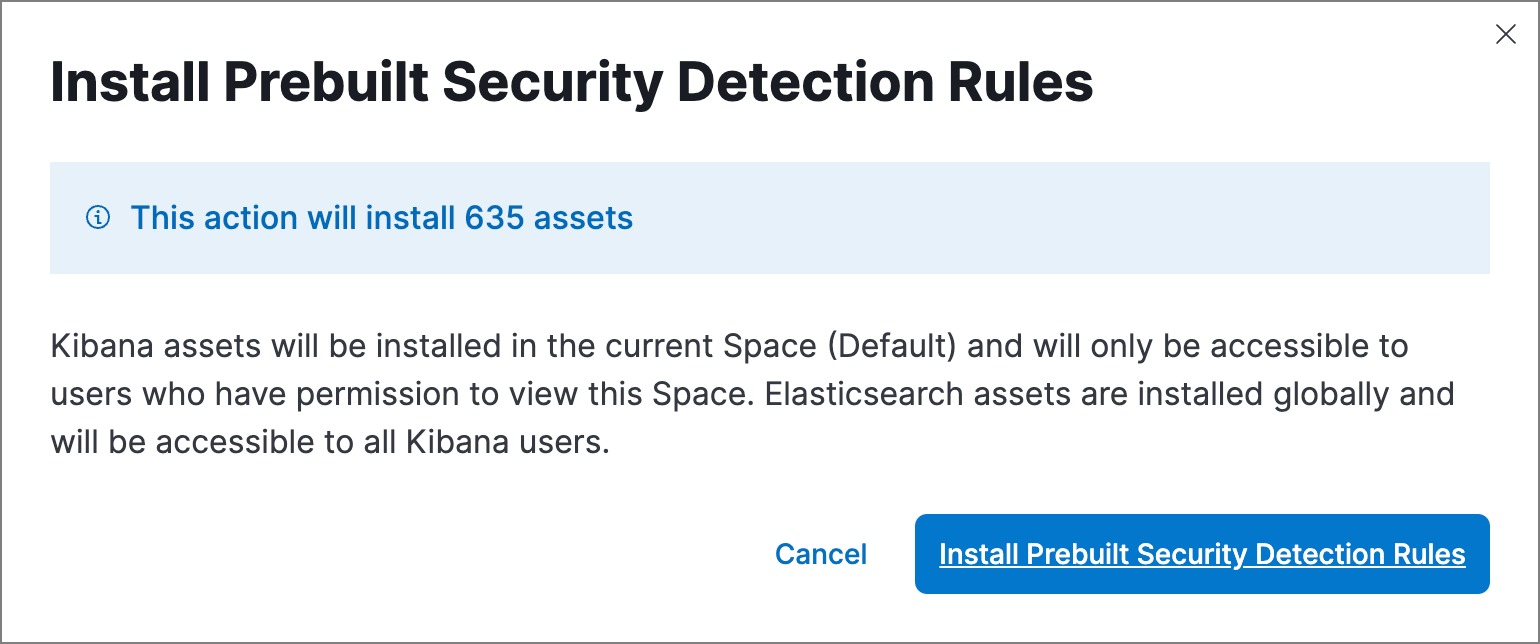
-
Click Install Prebuilt Security Detection Rules to confirm the installation.
Modify existing rules settings
editYou can edit an existing rule’s settings, and can edit index patterns and tags for multiple rules at once.
For prebuilt Elastic rules, you can’t modify most settings. You can only edit rule actions and add exceptions.
- Go to Detect → Rules.
-
Do one of the following:
- Edit a single rule: Select the All actions menu (…) on a rule, then select Edit rule settings. The Edit rule settings view opens, where you can modify the rule’s settings.
-
Edit multiple rules: Select all the rules you want to edit, then select an action from the Bulk actions menu:
- Index patterns: Add or delete the index patterns used by all selected rules.
- Tags: Add or delete tags on all selected rules.
- On the flyout that opens, update the settings.
- If available, select Overwrite all selected x to overwrite the settings on the rules. For example, if you’re adding tags to multiple rules, selecting Overwrite all selected rules tags removes all the rules' original tags and replaces them with the tags you specify.
- Click Save.
Manage rules
editYou can duplicate, enable, disable, and delete rules:
- Go to Detect → Rules.
-
Do one of the following:
- Select the All actions menu (…) on a rule, then select an action.
- Select all the rules you want to modify, then select an action from the Bulk actions menu.
- To enable or disable a single rule, switch on the rule’s Enabled toggle.
Export and import rules
editYou can export detection rules to an .ndjson file, which you can then import into another Elastic Security environment. The following configuration items are also included in the .ndjson file:
- Actions
- Exception lists
Although detection rule actions are included in the exported file, the connectors used by the actions are not included. Use the Saved Objects UI in Kibana (Stack Management → Kibana → Saved Objects) to export and import any necessary connectors before you export and import the detection rules.
Similarly, any value lists used for rule exceptions are not included in rule exports or imports. Use the Upload value lists UI (Detect → Rules → Upload value lists) to export and import value lists separately.
To export and import detection rules:
- Go to Detect → Rules.
-
To export rules:
- In the All rules table, select the rules you want to export.
-
Select Bulk actions → Export, then save the exported file.
You cannot export Elastic prebuilt rules.
-
To import rules:
You need at least
Readprivileges for theAction and Connectorsfeature to import rules with actions. If you’re importing rules without actions,Action and Connectorsfeature privileges are not required. Refer to Enable and access detections for more information.- Click Import rules.
-
Drag and drop the file that contains the detection rules.
Imported rules must be in an
.ndjsonfile. -
(Optional) Select Overwrite existing detection rules with conflicting "rule_id" to update existing rules if they match the
rule_idvalue of any rules in the import file. Configuration data included with the rules, such as actions, is also overwritten. -
(Optional) Select Overwrite existing exception lists with conflicting "list_id" to replace existing exception lists with exception lists from the import file if they have a matching
list_idvalue. - Click Import rule.
Tutorial: Enable detection rules
editTo learn how to enable detection rules in Elastic Security, watch the following tutorial.