Manage detection alerts
editManage detection alerts
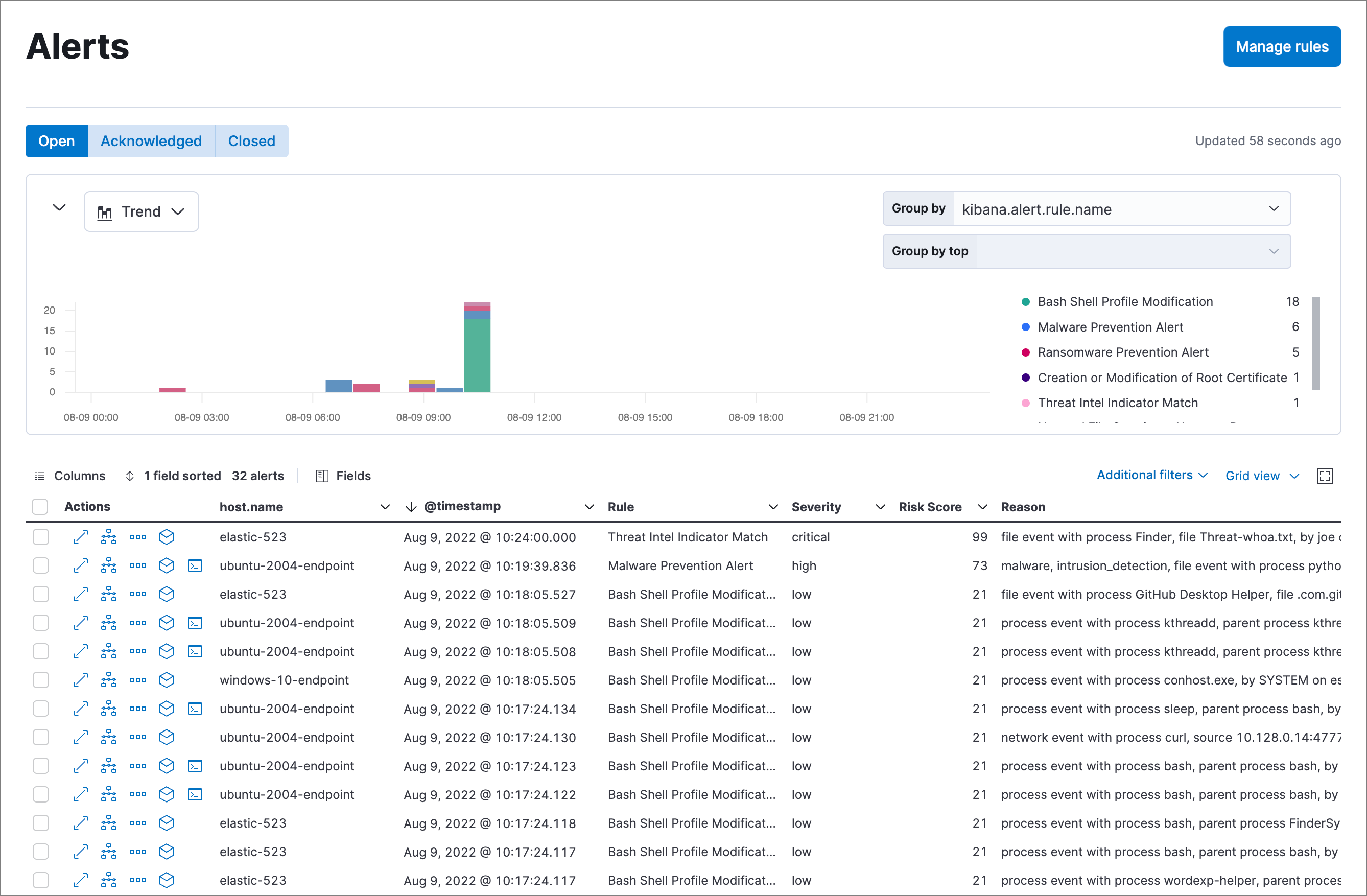
editThe Alerts page displays all detection alerts. From the Alerts page, you can filter alerts, view alerting trends, change the status of alerts, add alerts to cases, and start investigating and analyzing alerts.
View and filter detection alerts
editThe Alerts page offers various ways for you to organize and triage detection alerts as you investigate suspicious events. You can:
-
View an alert’s details. Click the View details button from the Alerts table to open the alert details flyout. Learn more at View detection alert details.
-
Filter for a specific rule in the KQL bar (for example,
kibana.alert.rule.name :"SSH (Secure Shell) from the Internet"). KQL autocomplete is available for.alerts-security.alerts-*indices. - Use the date and time filter to define a specific time range. By default, this filter is set to search the last 24 hours.
- Visualize and group alerts by specific parameters in the visualization section. Use the menu on the left to select a view type (Trend, Table, or Treemap), and use the menus on the right to select the ECS fields used for grouping alerts. Refer to Visualize detection alerts for more on each view type.
-
Hover over a value in the data grid to display available inline actions, such as Filter In, Filter Out, and Add to timeline investigation. Click the expand button to open a full context menu of options, including Show top values, Copy to Clipboard, and View rule details. The available options vary based on the type of data.
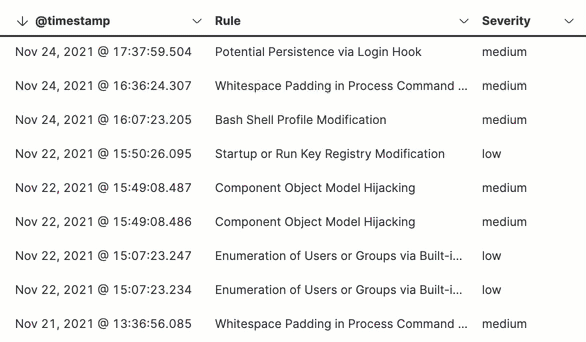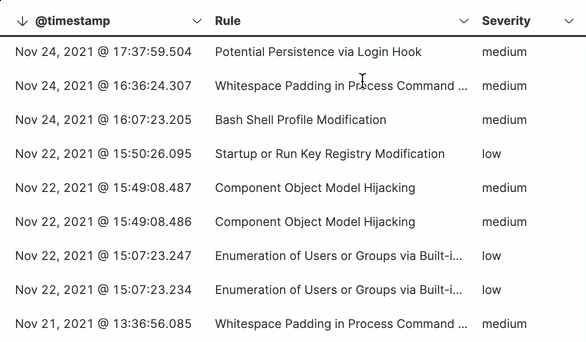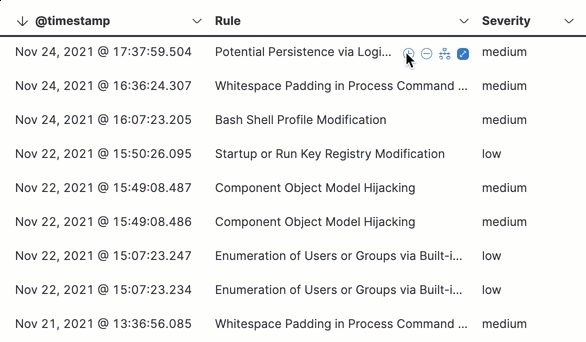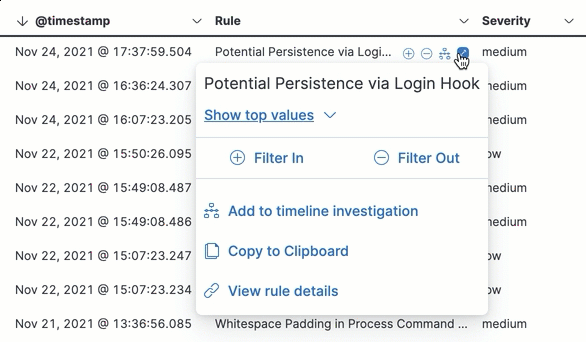
-
Filter alert results to include building block alerts or to only show alerts from indicator match rules by selecting the Additional filters drop-down. By default, building block alerts are excluded from the Overview and Alerts pages. You can choose to include building block alerts on the Alerts page, which expands the number of alerts.
When updating alert results to include building block alerts, the Security app searches the
.alerts-security.alerts-<Kibana space>index for thekibana.alert.building_block_typefield. When looking for alerts created from indicator match rules, the app searches the same index forkibana.alert.rule.type:'threat_match'.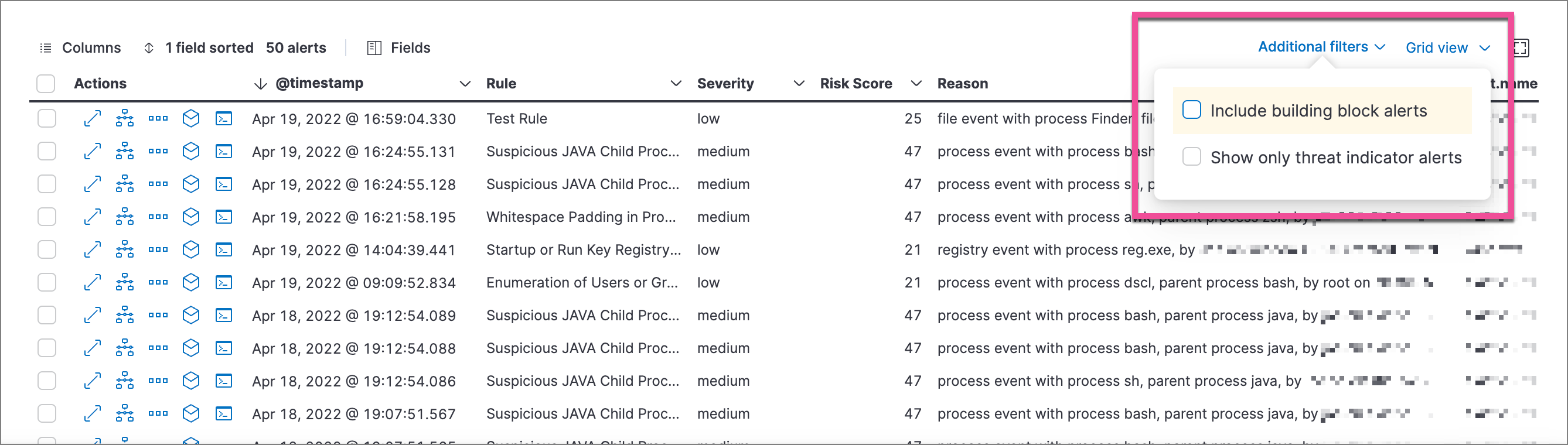
- View detection alerts generated by a specific rule. Go to Manage → Rules, then select a rule name in the table. The rule details page displays a comprehensive view of the rule’s settings, and the Alerts table under the Trend histogram displays the alerts associated with the rule, including alerts from any previous or deleted revision of that rule.
Customize the Alerts table
editUse the toolbar buttons in the upper-left of the Alerts table to customize the columns you want displayed:
- Columns: Reorder the columns.
- x fields sorted: Sort the table by one or more columns.
- Fields: Select the fields to display in the table. You can also add runtime fields to detection alerts and display them in the Alerts table.
Click the Full screen button in the upper-right to view the table in full-screen mode.
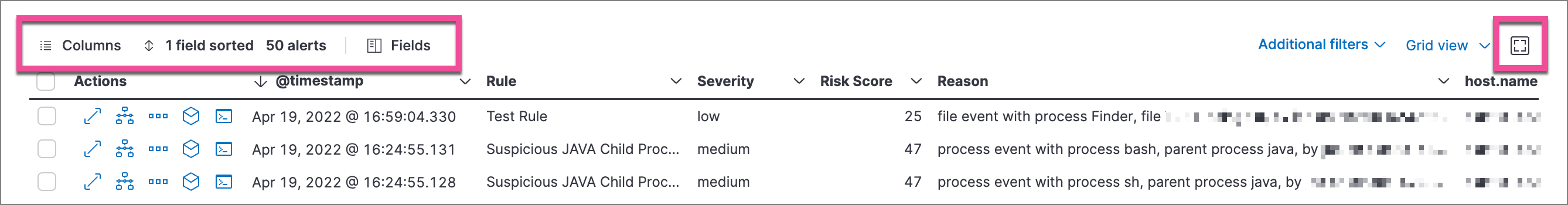
Use the view options drop-down in the upper-right of the Alerts table to control how alerts are displayed:
- Grid view: Displays alerts in a traditional table view with columns for each field
- Event rendered view: Display alerts in a descriptive event flow that includes relevant details and context about the event.
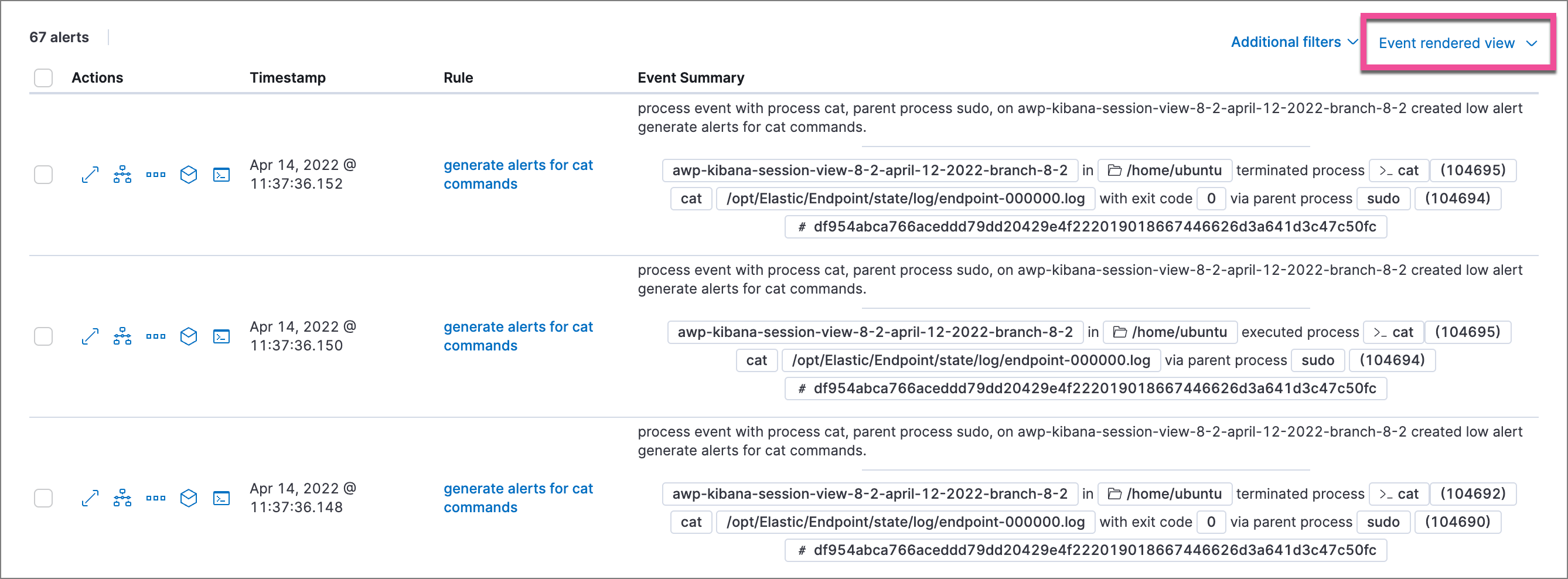
If you’re in the grid view, you can still view the event rendering for a specific alert by clicking the link in the Event Summary column, if a link is available. Some events do not have event renderings.
Take actions on an alert
editFrom the Alerts table or the alert details flyout, you can:
- Add detection alerts to cases
- Change an alert’s status
- Add a rule exception from an alert
- Add an endpoint exception from an alert
- Isolate an alert’s host
- Perform response actions on an alert’s host (Alert details flyout only)
- Run Osquery against an alert
- View alerts in Timeline
- Visually analyze an alert’s process relationships
Change an alert’s status
editYou can set an alert’s status to indicate whether it needs to be investigated (Open), is under active investigation (Acknowledged), or has been resolved (Closed). By default, the Alerts page displays open alerts. To filter alerts that are Acknowledged or Closed, select the appropriate status in the upper-left corner of the Alerts page. This filters all of the results displayed on the page (the Count table, Trend histogram, and Alerts table).
To change an alert’s status, do one of the following:
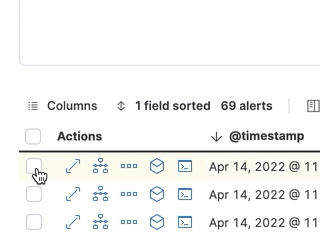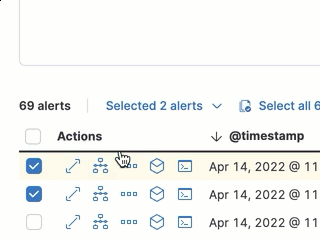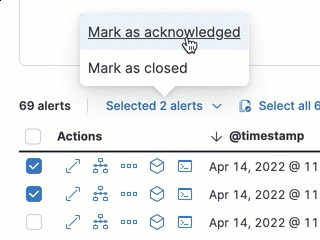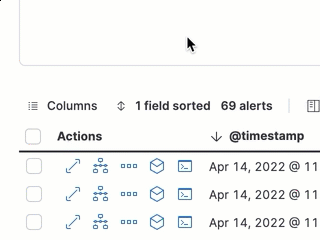
- In the alert’s row, click the More actions menu (…) in the Alerts table, then select the appropriate status (Mark as open, Mark as acknowledged, or Mark as closed).
- In the Alerts table, select all the alerts you want to change, click on the drop-down at the upper-left above the table, and then select Mark as open, Mark as acknowledged, or Mark as closed.
- In the alert details flyout, click Take action and select Mark as open, Mark as acknowledged, or Mark as closed.
Add a rule exception from an alert
editYou can add exceptions to the rule that generated an alert directly from the Alerts table. Exceptions prevent a rule from generating alerts even when its criteria are met.
To add an exception, click the More actions menu (…) in the Alerts table, then select Add exception. Alternatively, select Take action → Add rule exception in the alert details flyout.
For information about exceptions and how to use them, refer to Rule exceptions and value lists.
View alerts in Timeline
editTo view an alert in Timeline, click the Investigate in timeline button in the Alerts table. Alternatively, select Take action → Investigate in timeline in the alert details flyout.
When you send an alert generated by a threshold rule to Timeline, all matching events are listed in the Timeline, even ones that did not reach the threshold value. For example, if you have an alert generated by a threshold rule that detects 10 failed login attempts, when you send that alert to Timeline, all failed login attempts detected by the rule are listed.
Suppose the rule that generated the alert uses a Timeline template. In this case, when you investigate the alert in Timeline, the dropzone query values defined in the template are replaced with their corresponding alert values.
Example
This Timeline template uses the host.name: "{host.name}" dropzone filter in
the rule. When alerts generated by the rule are investigated in Timeline, the
{host.name} value is replaced with the alert’s host.name value. If the
alerts’s host.name value is Windows-ArsenalFC, the Timeline dropzone query
is host.name: "Windows-ArsenalFC".
Refer to Investigate events in Timeline for information on creating Timelines and Timeline templates. For information on how to add Timeline templates to rules, refer to Create a detection rule.