Author
Seth Goodwin
Elastic Security Labs Team Principal Research Engineer, Intelligence
Articles

TOLLBOOTH: What's yours, IIS mine
REF3927 abuses publicly disclosed ASP.NET machine keys to compromise IIS servers and deploy TOLLBOOTH SEO cloaking modules globally.

WARMCOOKIE One Year Later: New Features and Fresh Insights
A year later: Elastic Security Labs re-examines the WARMCOOKIE backdoor.

Taking SHELLTER: a commercial evasion framework abused in-the-wild
Elastic Security Labs detected the recent emergence of infostealers using an illicitly acquired version of the commercial evasion framework, SHELLTER, to deploy post-exploitation payloads.

The Shelby Strategy
An analysis of REF8685's abuse of GitHub for C2 to evade defenses.

From South America to Southeast Asia: The Fragile Web of REF7707
REF7707 targeted a South American foreign ministry using novel malware families. Inconsistent evasion tactics and operational security missteps exposed additional adversary-owned infrastructure.

Under the SADBRIDGE with GOSAR: QUASAR Gets a Golang Rewrite
Elastic Security Labs share details about the SADBRIDGE loader and GOSAR backdoor, malware used in campaigns targeting Chinese-speaking victims.

Katz and Mouse Game: MaaS Infostealers Adapt to Patched Chrome Defenses
Elastic Security Labs breaks down bypass implementations from the infostealer ecosystem’s reaction to Chrome 127's Application-Bound Encryption scheme.

BITS and Bytes: Analyzing BITSLOTH, a newly identified backdoor
Elastic Security Labs identified a novel Windows backdoor leveraging the Background Intelligent Transfer Service (BITS) for C2. This malware was found during a recent activity group tracked as REF8747.

Elastic catches DPRK passing out KANDYKORN
Elastic Security Labs exposes an attempt by the DPRK to infect blockchain engineers with novel macOS malware.

Introducing the REF5961 intrusion set
The REF5961 intrusion set discloses three new malware families targeting ASEAN members. The threat actor leveraging this intrusion set continues to develop and mature their capabilities.

The DPRK strikes using a new variant of RUSTBUCKET
Watch out! We’ve recently discovered a variant of RUSTBUCKET. Read this article to understand the new capabilities we’ve observed, as well as how to identify it in your own network.

Initial research exposing JOKERSPY
Explore JOKERSPY, a recently discovered campaign that targets financial institutions with Python backdoors. This article covers reconnaissance, attack patterns, and methods of identifying JOKERSPY in your network.

Elastic charms SPECTRALVIPER
Elastic Security Labs has discovered the P8LOADER, POWERSEAL, and SPECTRALVIPER malware families targeting a national Vietnamese agribusiness. REF2754 shares malware and motivational elements of the REF4322 and APT32 activity groups.

Update to the REF2924 intrusion set and related campaigns
Elastic Security Labs is providing an update to the REF2924 research published in December of 2022. This update includes malware analysis of the implants, additional findings, and associations with other intrusions.

NETWIRE Dynamic Configuration Extraction
Elastic Security Labs discusses the NETWIRE trojan and is releasing a tool to dynamically extract configuration files.

SiestaGraph: New implant uncovered in ASEAN member foreign ministry
Elastic Security Labs is tracking likely multiple on-net threat actors leveraging Exchange exploits, web shells, and the newly discovered SiestaGraph implant to achieve and maintain access, escalate privilege, and exfiltrate targeted data.

Exploring the REF2731 Intrusion Set
The Elastic Security Labs team has been tracking REF2731, an 5-stage intrusion set involving the PARALLAX loader and the NETWIRE RAT.

Detection rules for SIGRed vulnerability
The SIGRed vulnerability impacts all systems leveraging the Windows DNS server service (Windows 2003+). To defend your environment, we recommend implementing the detection logic included in this blog post using technology like Elastic Security.

Doing time with the YIPPHB dropper
Elastic Security Labs outlines the steps collect and analyze the various stages of the REF4526 intrusion set. This intrusion set uses a creative approach of Unicode icons in Powershell scripts to install a loader, a dropper, and RAT implants.

ICEDIDs network infrastructure is alive and well
Elastic Security Labs details the use of open source data collection and the Elastic Stack to analyze the ICEDID botnet C2 infrastructure.
Extracting Cobalt Strike Beacon Configurations
Part 2 - Extracting configurations from Cobalt Strike implant beacons.

CUBA Ransomware Campaign Analysis
Elastic Security observed a ransomware and extortion campaign leveraging a combination of offensive security tools, LOLBAS, and exploits to deliver the CUBA ransomware malware.

LUNA Ransomware Attack Pattern Analysis
In this research publication, we'll explore the LUNA attack pattern — a cross-platform ransomware variant.

Exploring the QBOT Attack Pattern
In this research publication, we'll explore our analysis of the QBOT attack pattern — a full-featured and prolific malware family.

Playing defense against Gamaredon Group
Learn about the recent campaign of a Russia-based threat group known as Gamaredon Group. This post will review these details and provide detection strategies.

FORMBOOK Adopts CAB-less Approach
Campaign research and analysis of an observed FORMBOOK intrusion attempt.
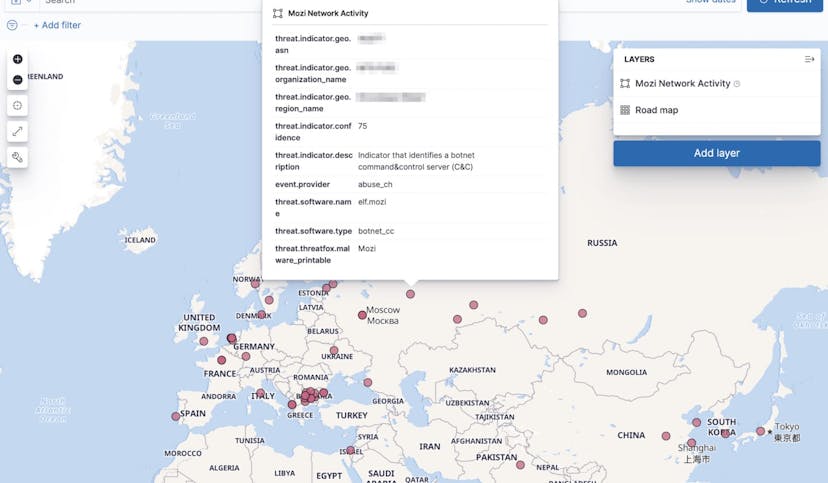
Collecting and operationalizing threat data from the Mozi botnet
The Mozi botnet is an ongoing malware campaign targeting unsecured and vulnerable networking devices. This post will showcase the analyst journey of collecting, analyzing, and operationalizing threat data from the Mozi botnet.
Collecting Cobalt Strike Beacons with the Elastic Stack
Part 1 - Processes and technology needed to extract Cobalt Strike implant beacons