Manage detection alerts
editManage detection alerts
editThe Alerts page displays all detection alerts. From the Alerts table, you can filter alerts, change an alert’s status, and start investigating and analyzing alerts in Timeline.
From Timelines, you can create cases to track issues and share information with colleagues.
View and filter detection alerts
editThe Alerts page offers various ways for you to organize and triage detection alerts as you investigate suspicious events. You can:
-
Filter for a specific rule in the KQL bar (for example,
signal.rule.name :"SSH (Secure Shell) from the Internet").
KQL autocomplete for .siem-signals-* indices is available on the
Alerts and Rule details pages, and in Timeline when either All or
Detection alerts is selected.
- Use the date and time filter to define a specific time range. By default, this filter is set to search the last 24 hours.
- View detection alerts generated by a specific rule. To do this, go to Detect → Rules, and then select a rule name in the All rules table. The Rules detail page displays a comprehensive view of the rule’s details, and alert details are displayed in the Alerts table beneath the Trend histogram. Alternatively, you can go to Detect → Alerts → Manage detection rules, and then click on a rule name in the All rules table to view the alerts associated with the rule.
-
Use the Stack by drop-down in the Trend histogram to select specific parameters to visualize the individual counts. For example, if you select
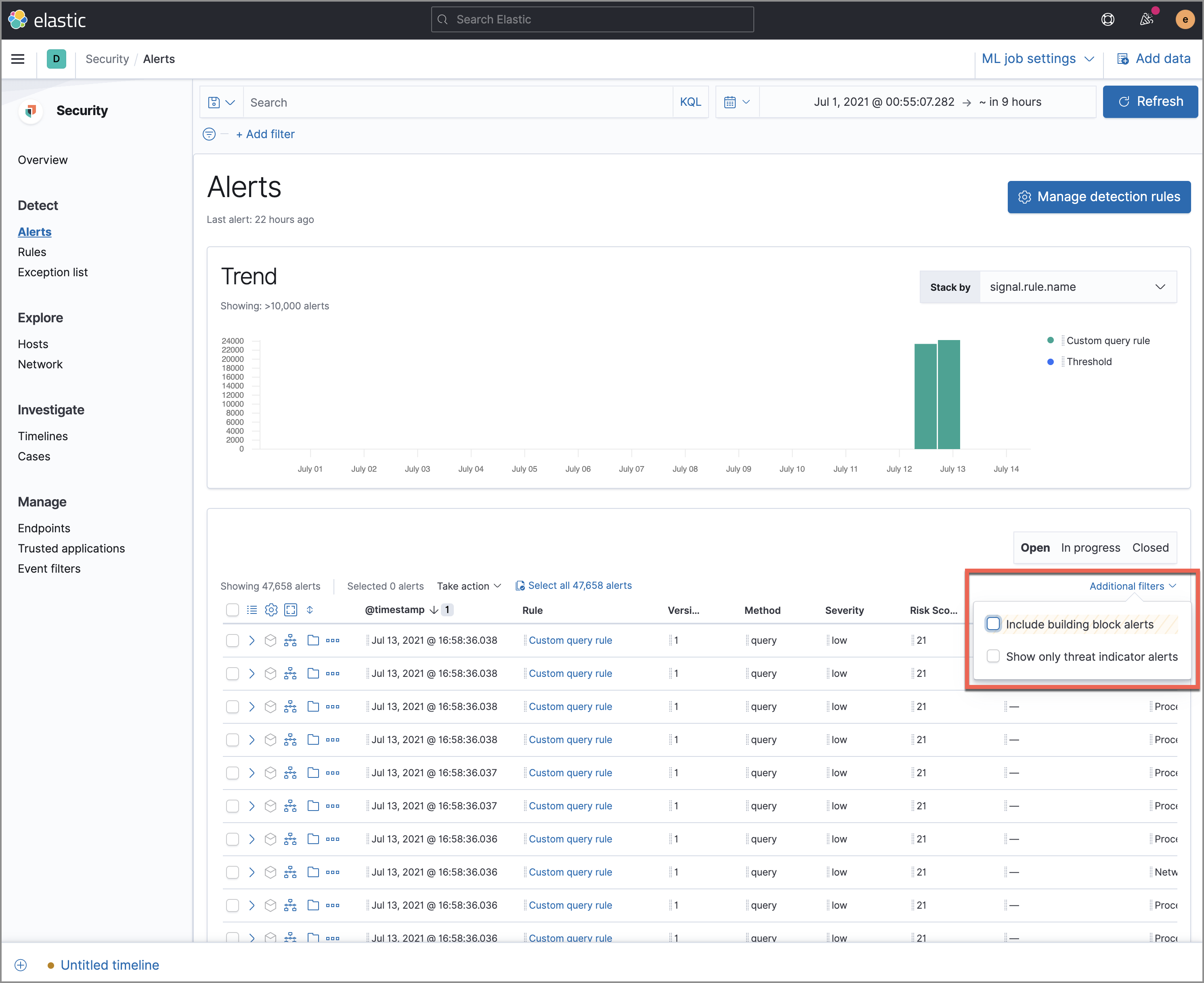
signal.rule.name, the histogram displays the total counts by alert name. - Filter alert results to include building block alerts or to only show alerts from indicator match rules, select the Additional filters drop-down. By default, building block alerts are excluded from the Alerts table; therefore, including them expands the number of alerts.
When updating alert results to include building block alerts, the Security app searches the .siem-signals-<Kibana space> index for the signal.rule.building_block_type field. When looking for alerts created from indicator match rules, the app searches the same index for the signal.rule.threat_mapping field.
Customize the Alerts table
editUse the buttons in the upper left corner of the Alerts table to customize the columns you want displayed and to view the table in full-screen mode.
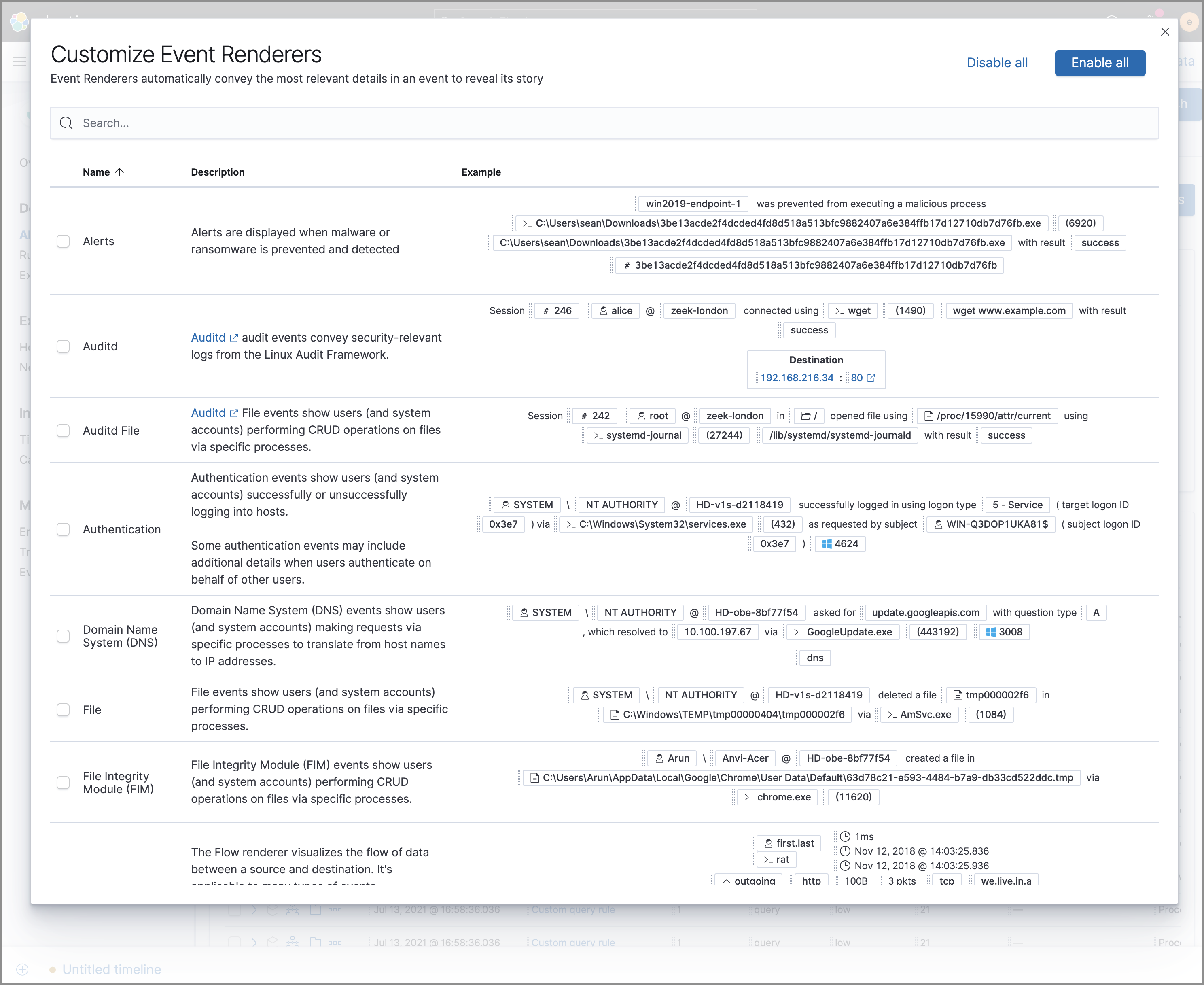
Click the Customize Event Renderers button to enable event renderers within the Alerts table. When enabled, event renderers show relevant details that provide more context about the event. For example, if you enable the Flow Event Renderer, the Alerts table shows details that describe the data flow between a source and destination — such as hosts, ports, protocol, direction, duration, amount transferred, process, and geographic location.
All event renderers are disabled by default. To switch between event views in the Alerts table, you can enable individual event renderers or click Enable all. Closing the Customize Event Renderers page saves your configurations.
View alert details
editTo further inspect an alert, click the View details button from the Alerts table. The Alert details flyout appears and provides several options to view alert data.
The Alert details flyout contains the following informational tabs:
Summary
The Summary tab provides an overview of the alert and shows relevant threat intelligence details. Use this information to analyze what generated the alert, so you can triage its relevance and resolve it as appropriate.
The Summary tab always begins with a list of general alert details. These details are conveyed as a curated list of fields containing essential and available information about the alert. Within this section, you can find the alert’s current status, locate the rule that produced the alert, learn the alert’s severity, and more. You can use these details to start forming a sense of what caused the alert and then continue your investigation by checking out available threat intelligence on the alert.
Elastic Security collects threat intelligence data for all alerts. Fields that show threat intelligence data are appended with an informational icon and placed after general alert details on the Summary tab.
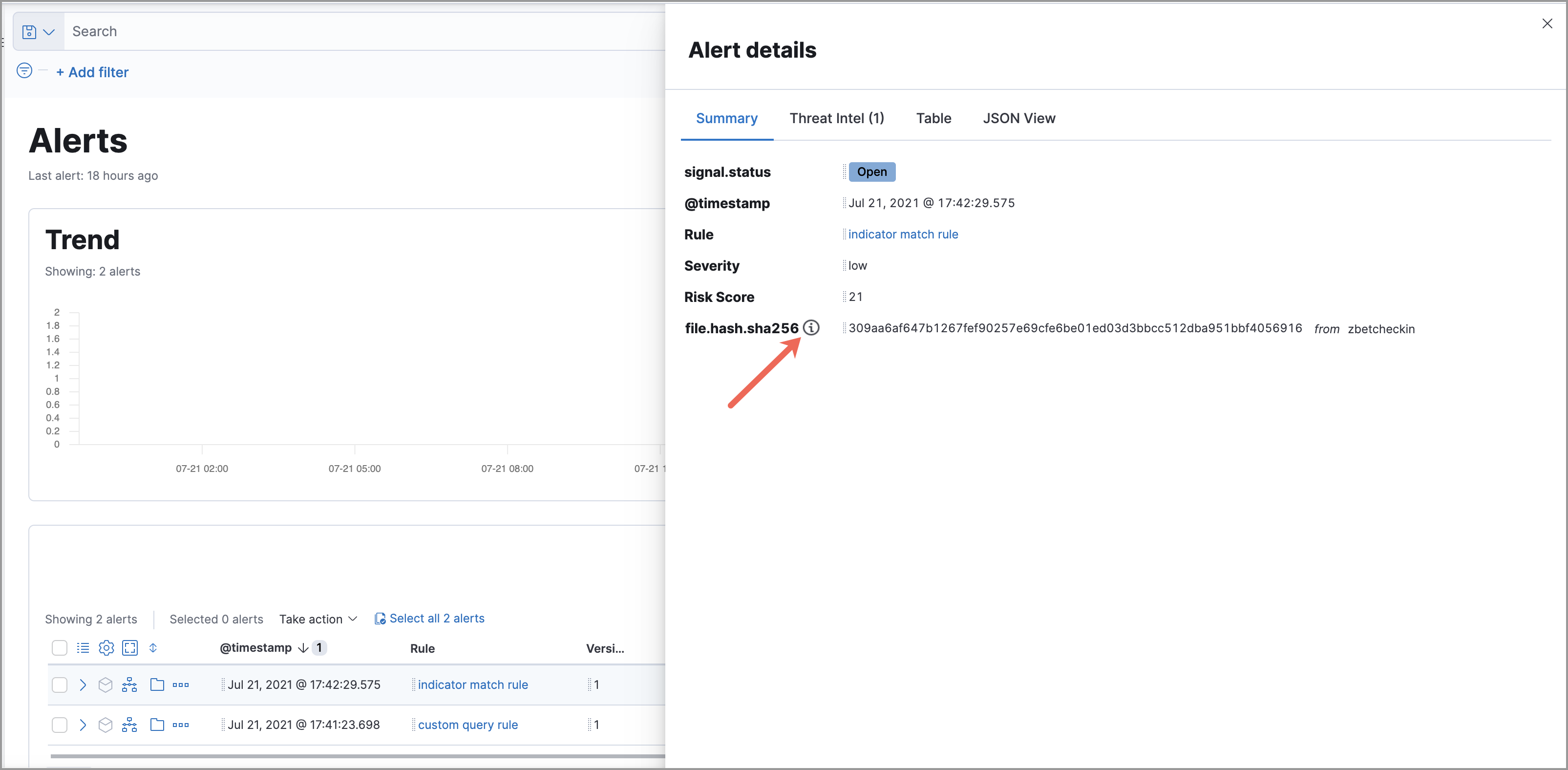
When gathering threat intelligence, Elastic Security queries indicator data from the past 30 days to find threat intelligence for the following fields. If these fields aren’t present, Elastic Security does not perform the query and no additional threat intelligence is displayed.
To learn more about the query, select the Threat Intel tab, then click the Inspect icon next to the threat you want to inspect.
-
file.hash.md5: The MD5 hash -
file.hash.sha1: The SHA1 hash -
file.hash.sha256: The SHA256 hash -
file.pe.imphash: Imports in a PE file -
file.elf.telfhash: Imports in an ELF file -
file.hash.ssdeep: The SSDEEP hash -
source.ip: The IP address of the source (IPv4 or IPv6) -
destination.ip*: The event’s destination IP address -
url.full: The full URL of the event source -
registry.path: The full registry path, including the hive, key, and value
Additional threat intelligence data is generated for indicator match alerts when indicators are matched with source events, as outlined by the conditions in the relevant indicator match rule.
Threat Intel
Shows the number of individual threats matching the alert in reverse chronological order, with the most recent threats at the top. Each threat is labelled with values from the matched.field and matched.atomic fields. All mapped fields are displayed for each matched threat.
If the alert does not contain threat intelligence data, the Threat Intel tab displays a message that none is available and provides a link to Threat Intel module documentation. The event enrichment query uses the indices specified in the securitySolution:defaultThreatIndex advanced setting. For more information, see Update default Elastic Security threat intelligence indices.
Table
Shows the alert details in table format. Alert details are organized into field value pairs.
JSON View
Shows the alert details in JSON format.
Change an alert’s status
editYou can set an alert’s status to indicate whether it needs to be investigated (Open), is under active investigation (In progress), or resolved (Closed). By default, the Alerts table displays open alerts. To filter alerts that are In progress or Closed, select the appropriate status in the upper-right corner of the Alerts table.
To change an alert’s status, do one of the following:
- In the alert’s row, click the More actions button, then select the appropriate status (Mark in progress, Close alert, or Open alert).
- In the Alerts table, select all the alerts you want to change, then select Take action → Close selected, Open selected, or Mark in progress.
Add alerts to cases
editFrom the Alerts table, you can attach one or more alerts to a case by clicking the Add to case button. From here, you can choose to add the alert to a new case or attach it to an existing one. You can add an unlimited amount of alerts from any rule type. If you attach the alert to a case that has been configured to sync its status with associated alerts, the alert’s status updates any time the case’s status is modified.
Once you’ve added an alert to a case, you can only remove it through the Elastic Security Cases API.
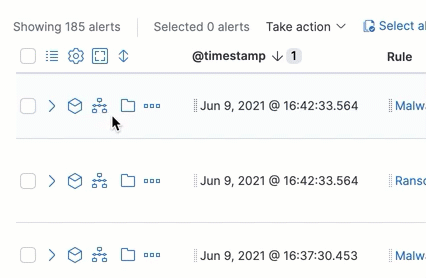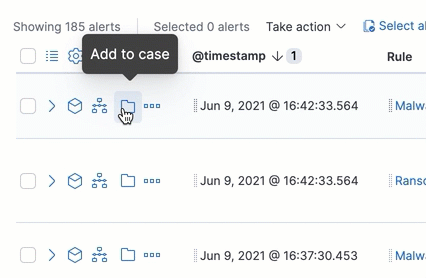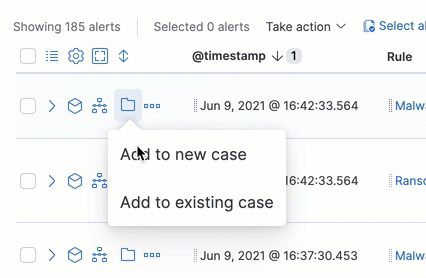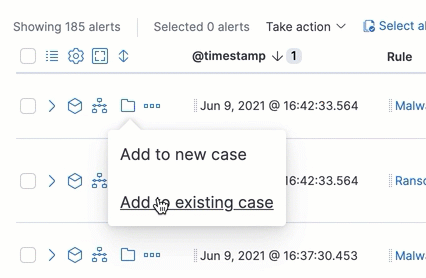
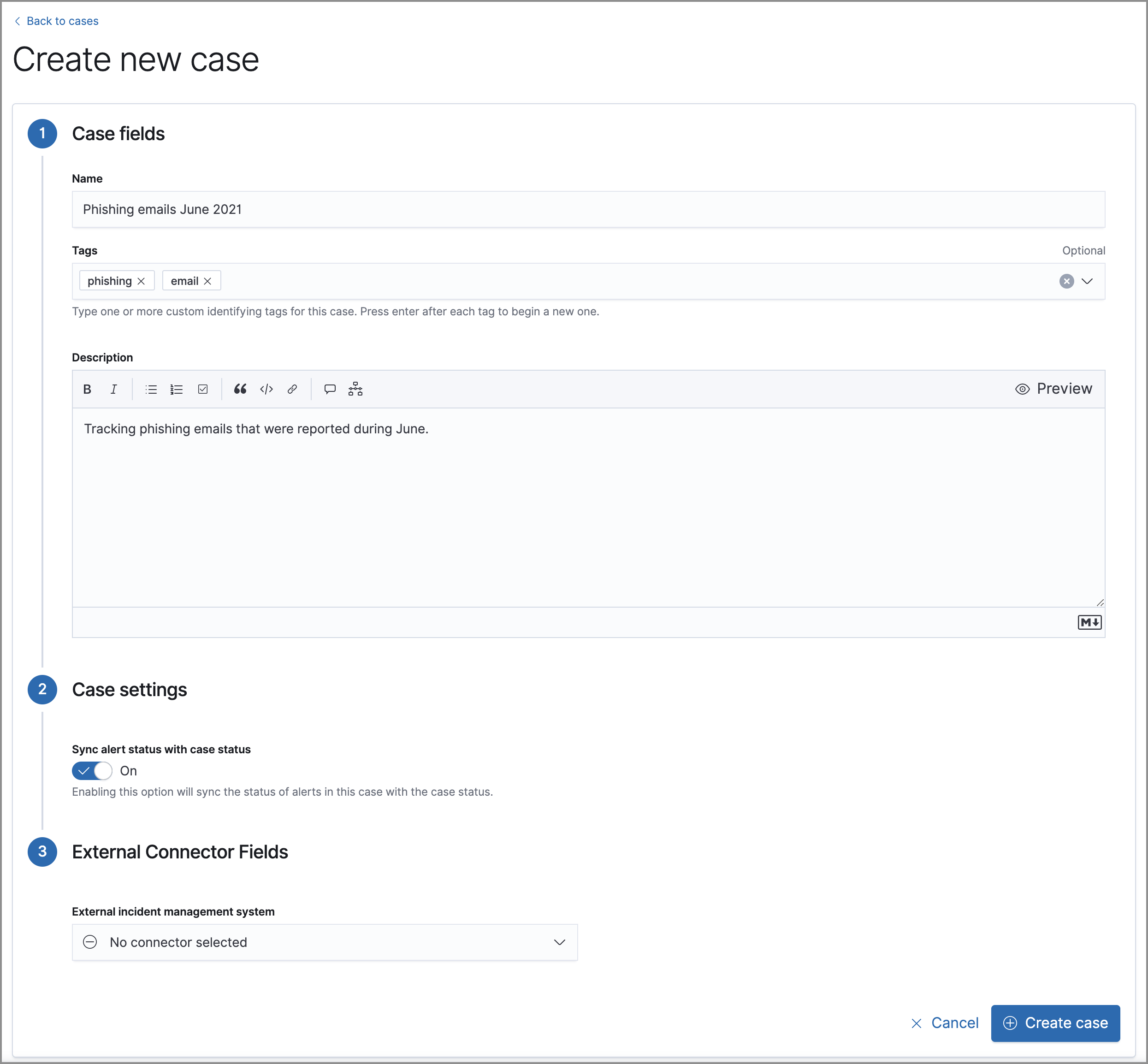
Add an alert to a new case
editTo add an alert to a new case:
- Select Add to case → Add to a new case.
- In the Create a new case pane, give your case a name, add relevant tags, and include a case description.
- Specify whether you want to sync the status of associated alerts. It is enabled by default; however, you can toggle this setting on or off at any time. If it remains enabled, the alert’s status updates whenever the case’s status is modified.
-
Select a connector. If you’ve previously added one, that connector displays as the default selection. Otherwise, the default setting is
No connector selected. - Click Create case after you’ve completed all of the required fields. A notification message that confirms the case was successfully created displays. Click the link inside the notification or go to the Cases page to view your case.
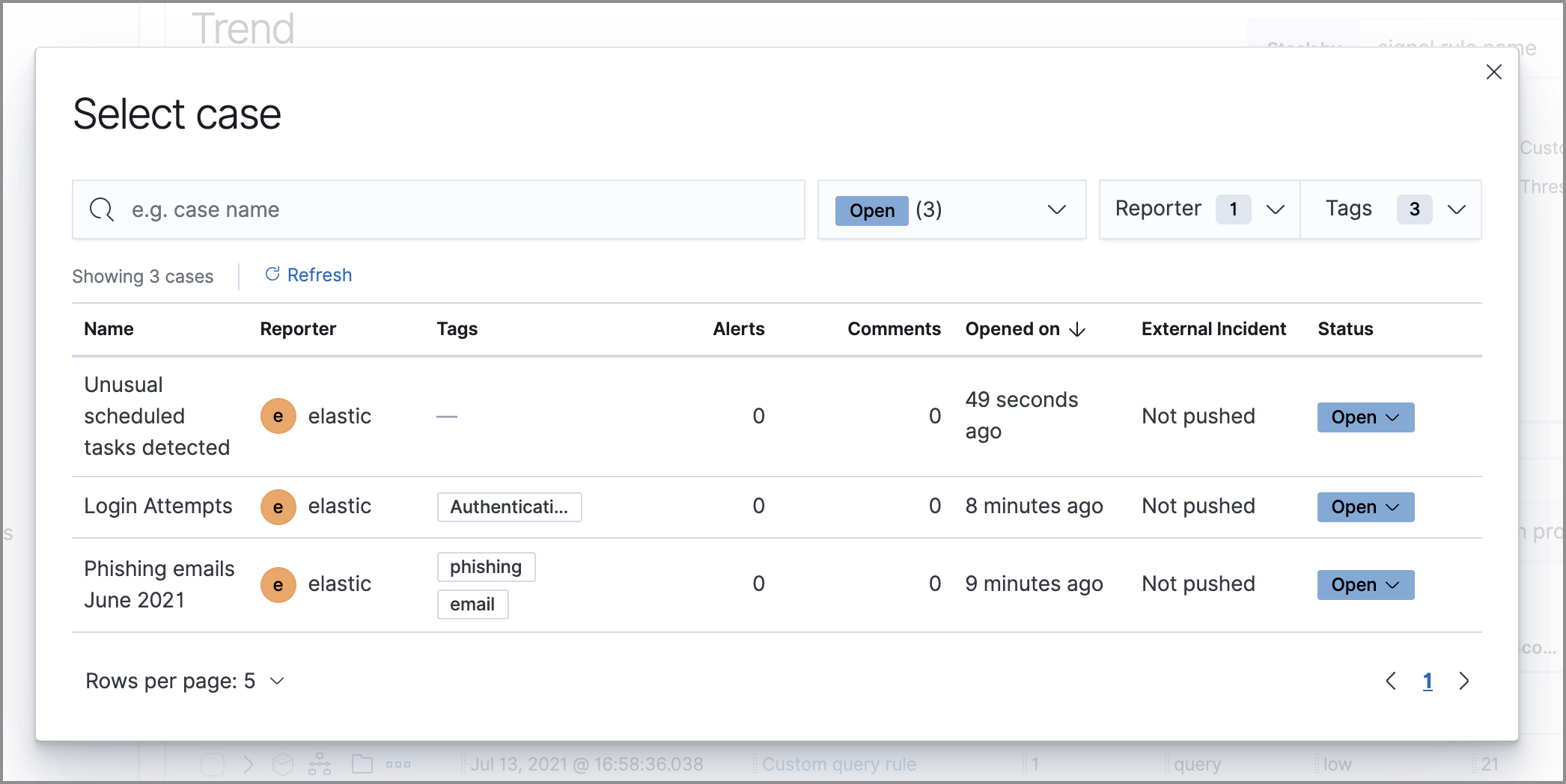
Add an alert to an existing case
editTo attach an alert to an existing case:
- Select Add to case → Add to existing case.
- From the Select case pane, select the appropriate case for which to attach an alert. A confirmation message displays with an option to view the updated case. Click on the link in the notification or go to the Cases page to view the case’s details.
Send alerts to Timeline
editTo view an alert in Timeline, click the Investigate in timeline button.
When you send an alert generated by a threshold rule to Timeline, all matching events are listed in the Timeline, even ones that did not reach the threshold value. For example, if you have an alert generated by a threshold rule that detects 10 failed login attempts, when you send that alert to Timeline, all failed login attempts detected by the rule are listed.
Suppose the rule that generated the alert uses a Timeline template. In this case, when you investigate the alert in Timeline, the dropzone query values defined in the template are replaced with their corresponding alert values.
Example
This Timeline template uses the host.name: "{host.name}" dropzone filter in
the rule. When alerts generated by the rule are investigated in Timeline, the
{host.name} value is replaced with the alert’s host.name value. If the
alerts’s host.name value is Windows-ArsenalFC, the Timeline dropzone query
is host.name: "Windows-ArsenalFC".
See Investigate events in Timeline for information on creating Timelines and Timeline templates. For information on how to add Timeline templates to rules, see Create a detection rule.
Add rule exceptions
editYou can add exceptions to the rule that generated the alert directly from the Alerts table. Exceptions prevent a rule from generating alerts even when its criteria are met.
To add an exception, click the actions button (three dots) and then select Add exception.
For information about exceptions and how to use them, see Rule exceptions and value lists.
Visually analyze process relationships
editFor process events that are detected by Elastic Endpoint, you can open a visual mapping to view a hierarchal timeline of when these events occurred. For more information, see Visual event analyzer.