What’s new in Elastic Security 7.12: Leave threats nowhere to hide
Gain the upper hand on cyber threats with Elastic Security 7.12. The release arms practitioners with analyst-driven correlation, behavioral ransomware prevention, and more.
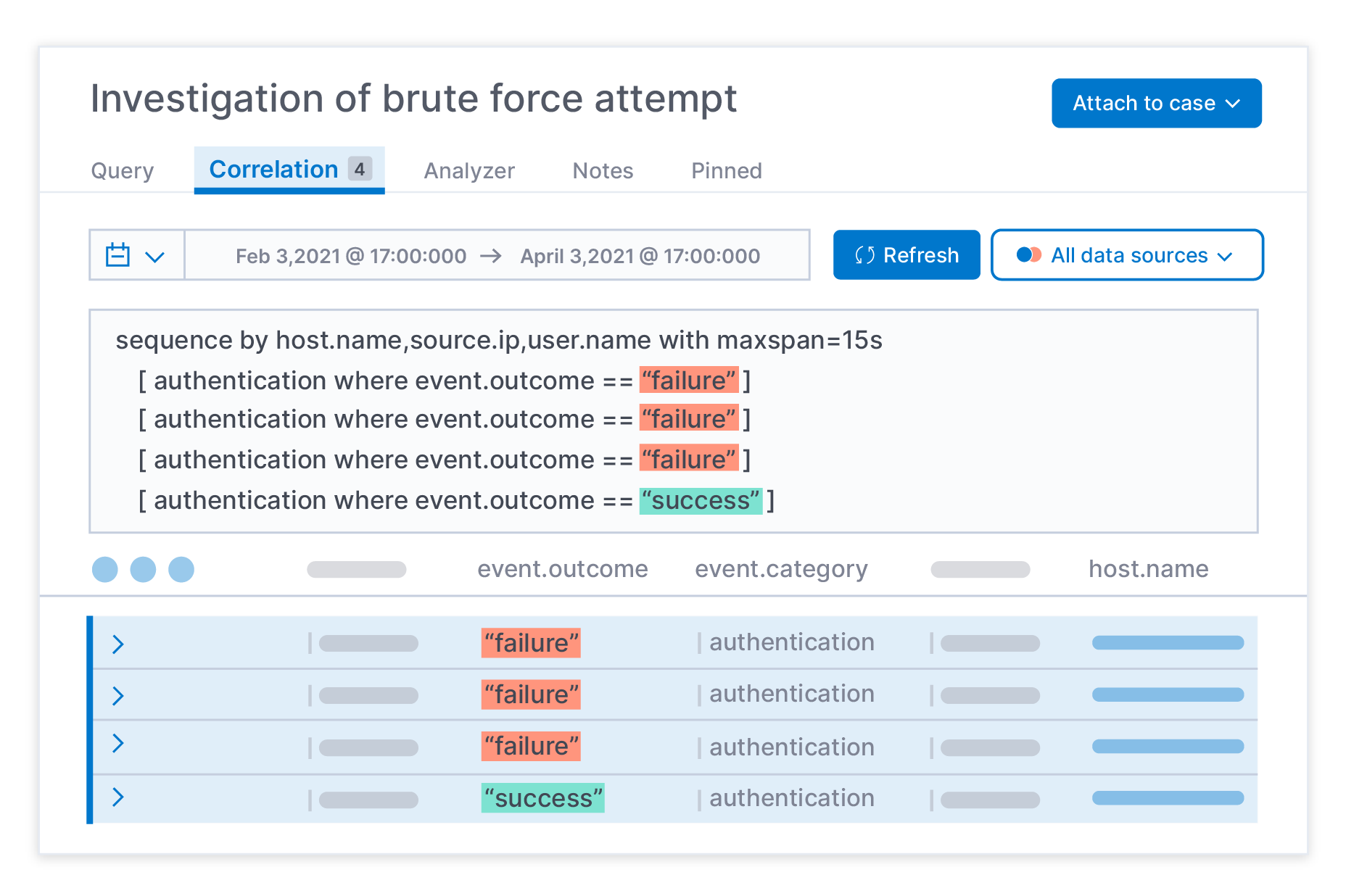
Analyst-driven correlation enables practitioners to identify attack progression and reduce false positives, applying sequence-based analysis across all data, no matter the source. It is available in the Elastic Security investigation workspace, streamlining hunting, investigation, and other workflows.
Behavioral ransomware prevention, new in 7.12, protects Windows systems. It performs advanced analysis of host process data, making it effective against an array of ransomware families. Ransomware prevention is available on Elastic Agent in just a click.
Let’s dig in to this and more.
Correlate at the speed of thought
Elastic Security 7.12 puts correlation in the hands of analysts, enabling faster and more effective hunting and investigation. It enables practitioners to explore the relationships between data points, through the power to:
- Analyze data from across your org with cross-index correlation
- Identify attack progression and reduce false positives with sequence-based analysis
- Eliminate a potential source of analyst error with case-sensitive searches
- Correlate with mathematical functions (such as string length, average value, and the difference between two values)
Imagine you’re rooting out the final footholds of a long-lingering threat by examining process behavior. A simple search for the specific process would return the data you need, but awash in a sea of innocuous activity. In contrast, using correlation to identify every instance of that same process — but only those spawned by a specific different process and that then initiated an outbound network connection — reduces noise and streamline remediation.
Analyst-driven correlation is available directly within Elastic Security. With an intuitive structure and instant syntax validation, it has a low learning curve. Information is presented in the Timeline investigation UI, providing seamless movement through analyst workflows. Data source-specific row renderers now enable analysts to understand and act upon data quickly.
This capability is driven by the analyst-friendly syntax of the Event Query Language (EQL), which is also available through the Elastic Security detection engine. Practitioners can now automate part of a recent hunt by simply copying an EQL query into a detection rule. Plus, content engineers implementing a prebuilt detection rule can quickly validate a given rule’s effectiveness and gauge how many alerts it will generate by pasting an EQL query from a detection rule into an investigation.
Stop ransomware with Elastic Agent
Behavioral ransomware prevention with Elastic Agent
Ransomware attacks continue to prove profitable and the techniques they employ are evolving quickly. Fortunately, like other forms of malware, ransomware can be detected and prevented at several stages during its lifecycle.
Elastic Security 7.12 introduces a new layer of ransomware prevention: behavioral analysis with the Elastic Agent. This ransomware prevention complements the signatureless anti-malware capabilities introduced in Elastic Security 7.9. Behavioral ransomware prevention on the Elastic Agent detects and stops ransomware attacks on Windows systems by analyzing data from low-level system processes, and is effective across an array of widespread ransomware families — including those targeting the system’s master boot record.
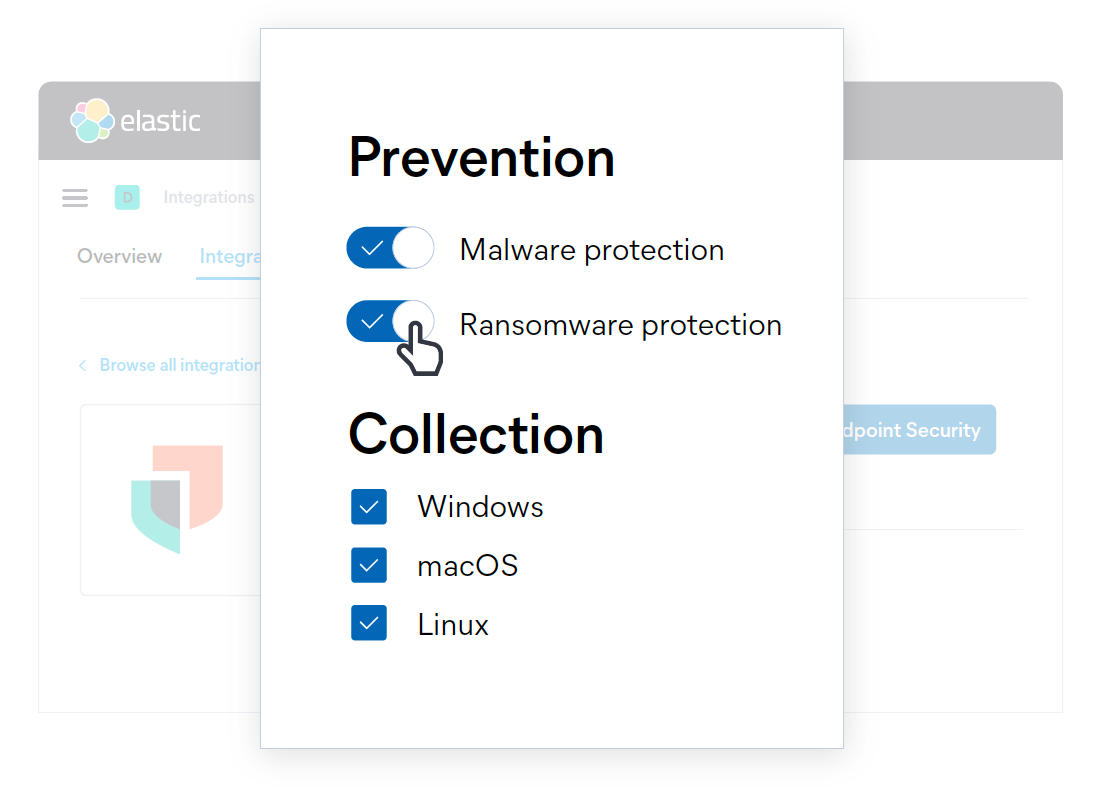 If you’d like to test the behavioral ransomware protection capabilities of Elastic Agent, a 14-day free trial of Elastic Cloud is available to all customers.
If you’d like to test the behavioral ransomware protection capabilities of Elastic Agent, a 14-day free trial of Elastic Cloud is available to all customers.
Enhanced malware protection accuracy
Two updates to the malware prevention capabilities of the Elastic Agent increase accuracy, resulting in fewer false negatives and fewer false positives.
Eliminate blind spots to increase operational value
Data management and access enhancements
Elastic Security leverages several Elastic Stack enhancements to harness data at greater scale than previously possible:
- Empower analysts to search for information in new ways, quickly and at low cost, with schema on read and runtime fields — new in this release.
- Make it financially feasible to extend the breadth and duration of data visibility with searchable snapshots — now generally available.
- Enable global analysis and detection, no matter where your information lives, with cross-cluster search — now supported across regions and providers.
Data integrations
Data connector for third-party and legacy SIEMs
Migrate data from your existing platform — the connector enables ingestion of specific data sources from Splunk Enterprise environments directly into Elasticsearch. Seamlessly ingest Apache, Nginx, Zeek, and AWS CloudTrail logs, making them available for rapid analysis within Elastic Security.
Cisco Advanced Malware Protection integration
Users of Cisco Advanced Malware Protection (AMP) can now easily ingest logs into the Elastic Stack using a brand new Filebeat module, enabling analysis of this valuable endpoint data within Elastic Security.
Pensando DSC integration
Ingest Pensando network logs and view them on prebuilt dashboards with this new developer-built and Elastic-validated Pensando module for Filebeat.
Expanded set of Elastic Agent data sources
The Elastic Agent now collects several data sources that previously required Filebeat, including Sophos XG, Microsoft Defender ATP, and Google Cloud.
ECS 1.8
Our community-developed open standard for normalized event data continues to mature and expand.
ECS categorization fields, which help enable analysts to pivot through data quickly by classifying events, include two new options and are now generally available.
ECS categorization fields, which aid automated and manual analysis methods alike, now offer Registry and Session as options, and are now generally available.
ECS documentation now offers a section on usage that provides security engineers with relevant examples to help them convert their data to ECS. Additional mapping templates are available to help users customize their data ingestion to meet specific needs of security and other use cases, like observability.
Additionally, we have bolstered our existing “user” field sets, adding support for datasets that contain information on multiple users within the same log, such as Active Directory user changes.
Stop threats at scale
Centralized detection across macOS systems
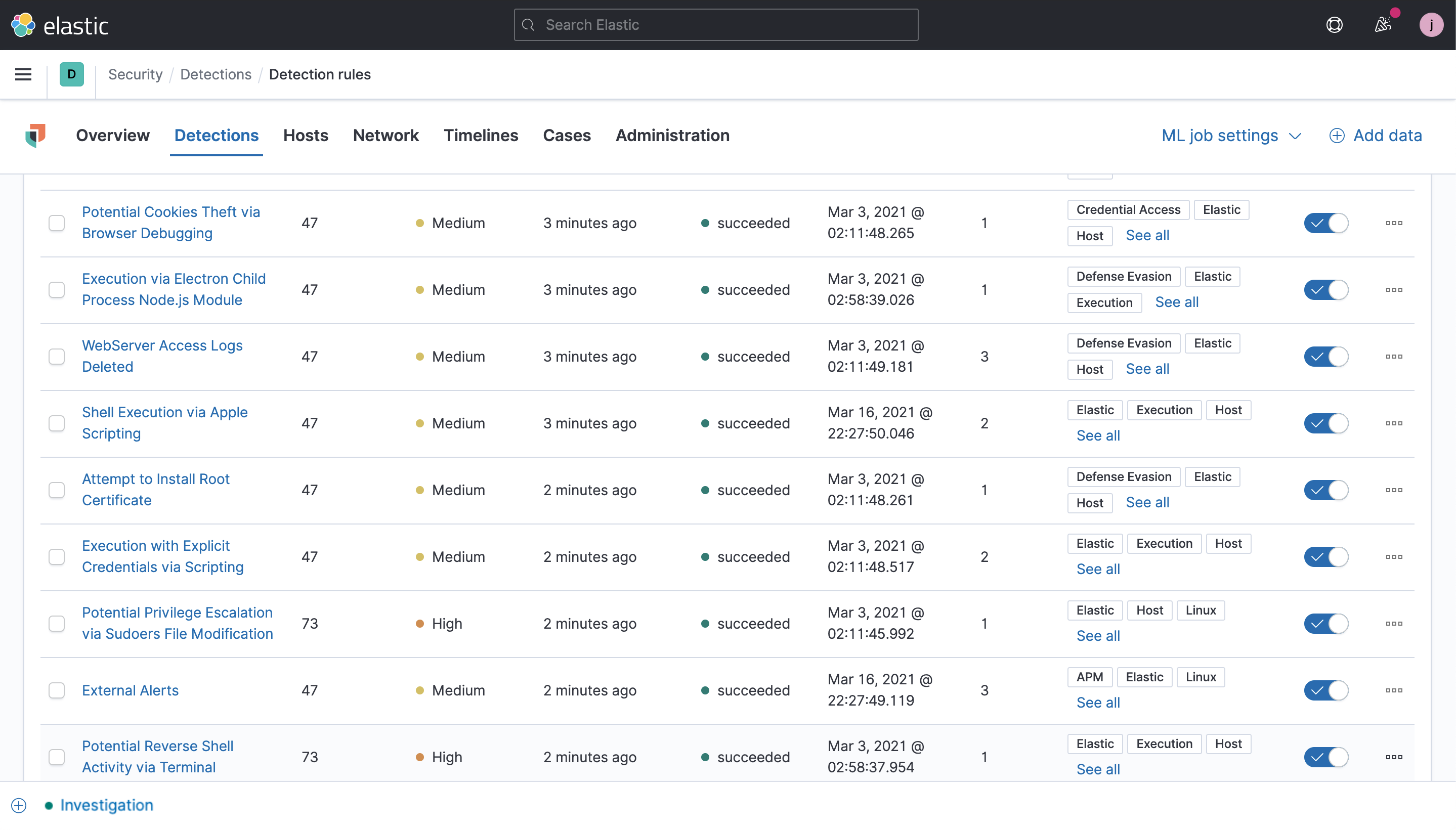
Elastic Security 7.12 adds detection rules for spotting commonly abused malware and techniques against macOS and Linux hosts and extending MITRE ATT&CK® coverage against Windows hosts.
As macOS market share continues to grow, so does its threat landscape. Version 7.12 adds several rules to detect malicious activity on macOS. We now cover several persistence techniques, suspicious system file modifications, potential theft of passwords and secrets, and much more. Thanks to these additional detection rules, we have also improved our ATT&CK coverage for macOS.
Threat intelligence modules
Seamlessly ingest threat intelligence from Abuse.ch, AlienVault OTX, and Anomali Limo via modules introduced in Elastic Security 7.12. Security teams can leverage context from these freely available sources for automated enrichment and detection using the indicator match rule type, which has been updated to surface matched values within generated alerts.
Multiple aggregations in threshold rules
Data aggregation — a powerful feature of the Elastic Stack that enables searching across massive amounts of data, looking for certain conditions, and summarizing results — allows rule authors to detect when grouped data has certain characteristics that might be interesting from a security perspective.
With 7.12, we’re significantly improving threshold-based detections by enabling grouping across multiple fields and adding a “unique count” aggregation type. Together, these updates enable users to implement new uses cases that rely on such logic, such as detecting signs of brute force activity, port scanning, and unauthorized authentication.
Arm every analyst
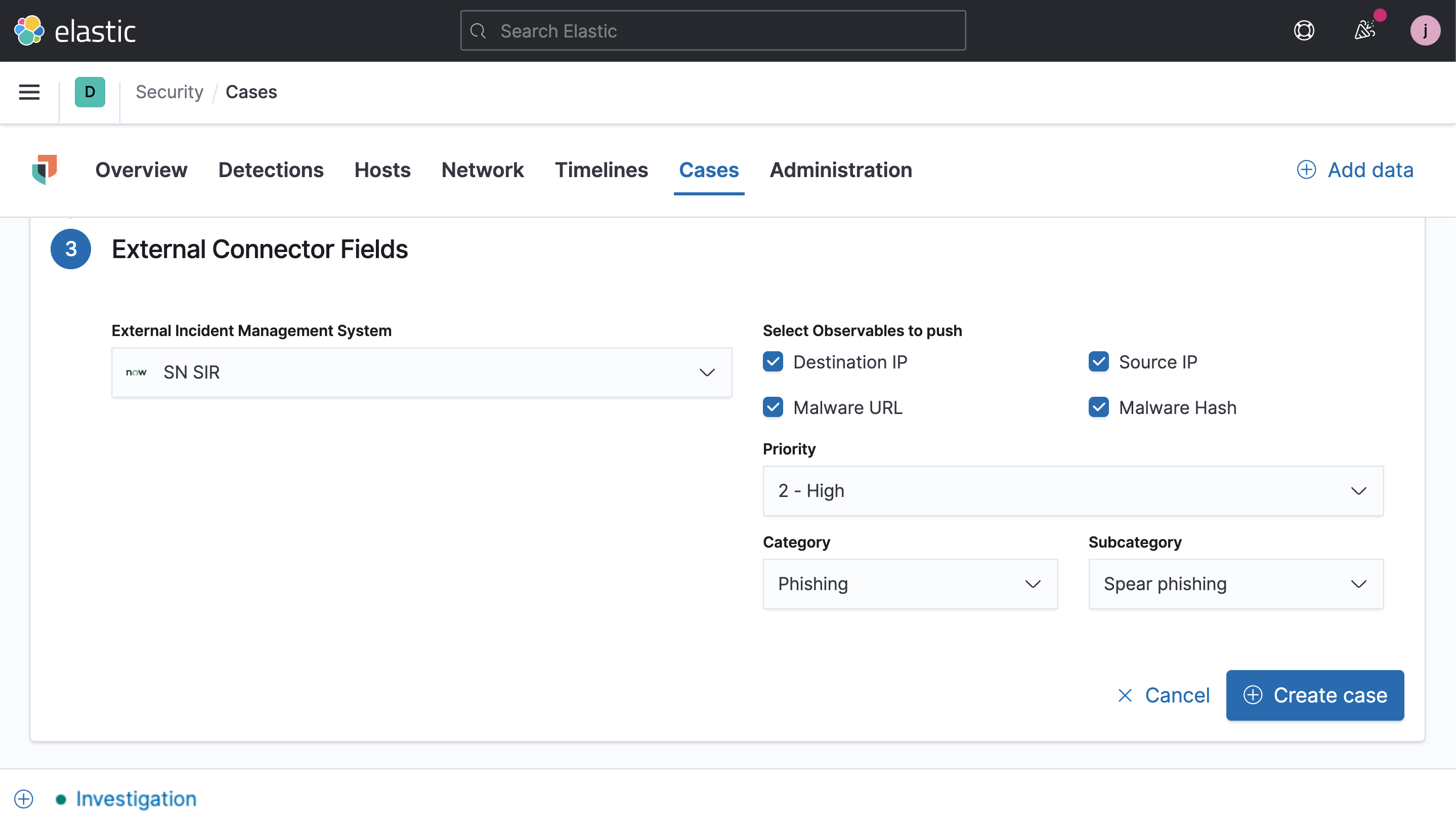
New and deeper ServiceNow integrations
Elastic is releasing a connector with ServiceNow Security Incident Response (SIR) to enable orchestration and response workflows. This integration enables users to send case information, including observables associated with the case. This case information can be used to trigger playbooks, such as data enrichment, firewall rule updates, and containment of infected hosts. Version 7.12 also deepens existing integrations with ServiceNow ITSM, allowing users to specify the incident type.
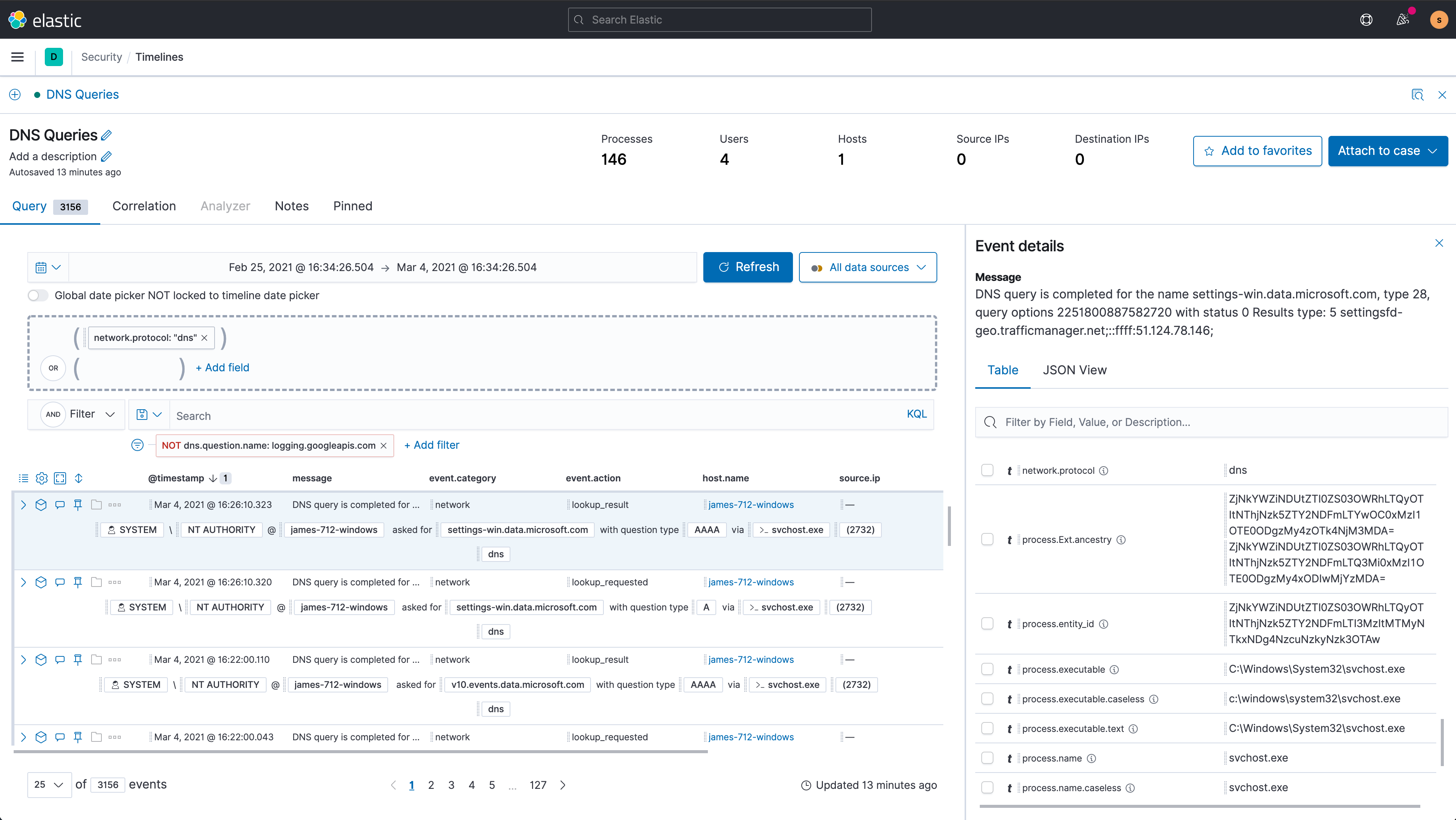
Network and host details side panel
Version 7.12 introduces a side panel providing quick access to network and host details.
Semantic rendering of endpoint data
The Elastic Security 7.12 investigation view renders host data (from Elastic Agent and other ECS-compatible sources) in a semantic format that’s faster to scan and easier to absorb.
Give Elastic Security 7.12 a spin
Want to try out all this goodness in Elastic Security? Experience all that 7.12 has to offer on Elastic Cloud, or check out an Elastic Security demo. Already have ECS-formatted data in Elasticsearch? Just upgrade to 7.12 of the Elastic Stack to start detecting and responding.
Want to see it in action? Watch the best sessions from our recent ElasticON Security virtual event.
The release and timing of any features or functionality described in this document remain at Elastic’s sole discretion. Any features or functionality not currently available may not be delivered on time or at all.