- Elastic Security: other versions:
- Elastic Security overview
- What’s new
- Get started with Elastic Security
- Elastic Security UI
- Anomaly Detection with Machine Learning
- Detections and Alerts
- Creating detection rules
- Managing detection rules
- Monitoring and troubleshooting rule executions
- Rule exceptions and value lists
- About building-block rules
- Managing detection alerts
- Visual event analyzer
- Tuning prebuilt detection rules
- Prebuilt rule changes per release
- Prebuilt rule reference
- AWS Access Secret in Secrets Manager
- AWS CloudTrail Log Created
- AWS CloudTrail Log Deleted
- AWS CloudTrail Log Suspended
- AWS CloudTrail Log Updated
- AWS CloudWatch Alarm Deletion
- AWS CloudWatch Log Group Deletion
- AWS CloudWatch Log Stream Deletion
- AWS Config Service Tampering
- AWS Configuration Recorder Stopped
- AWS EC2 Encryption Disabled
- AWS EC2 Flow Log Deletion
- AWS EC2 Network Access Control List Creation
- AWS EC2 Network Access Control List Deletion
- AWS EC2 Snapshot Activity
- AWS Execution via System Manager
- AWS GuardDuty Detector Deletion
- AWS IAM Assume Role Policy Update
- AWS IAM Brute Force of Assume Role Policy
- AWS IAM Deactivation of MFA Device
- AWS IAM Group Creation
- AWS IAM Group Deletion
- AWS IAM Password Recovery Requested
- AWS IAM User Addition to Group
- AWS Management Console Brute Force of Root User Identity
- AWS Management Console Root Login
- AWS RDS Cluster Creation
- AWS RDS Cluster Deletion
- AWS RDS Instance/Cluster Stoppage
- AWS Root Login Without MFA
- AWS S3 Bucket Configuration Deletion
- AWS WAF Access Control List Deletion
- AWS WAF Rule or Rule Group Deletion
- Abnormally Large DNS Response
- AdFind Command Activity
- Adding Hidden File Attribute via Attrib
- Administrator Privileges Assigned to an Okta Group
- Administrator Role Assigned to an Okta User
- Adobe Hijack Persistence
- Adversary Behavior - Detected - Endpoint Security
- Anomalous Kernel Module Activity
- Anomalous Linux Compiler Activity
- Anomalous Process For a Linux Population
- Anomalous Process For a Windows Population
- Anomalous Windows Process Creation
- Apple Script Execution followed by Network Connection
- Application Added to Google Workspace Domain
- Attempt to Create Okta API Token
- Attempt to Deactivate MFA for an Okta User Account
- Attempt to Deactivate an Okta Application
- Attempt to Deactivate an Okta Network Zone
- Attempt to Deactivate an Okta Policy
- Attempt to Deactivate an Okta Policy Rule
- Attempt to Delete an Okta Application
- Attempt to Delete an Okta Network Zone
- Attempt to Delete an Okta Policy
- Attempt to Delete an Okta Policy Rule
- Attempt to Disable IPTables or Firewall
- Attempt to Disable Syslog Service
- Attempt to Modify an Okta Application
- Attempt to Modify an Okta Network Zone
- Attempt to Modify an Okta Policy
- Attempt to Modify an Okta Policy Rule
- Attempt to Remove File Quarantine Attribute
- Attempt to Reset MFA Factors for an Okta User Account
- Attempt to Revoke Okta API Token
- Attempted Bypass of Okta MFA
- Attempts to Brute Force a Microsoft 365 User Account
- Attempts to Brute Force an Okta User Account
- Azure Active Directory PowerShell Sign-in
- Azure Application Credential Modification
- Azure Automation Account Created
- Azure Automation Runbook Created or Modified
- Azure Automation Runbook Deleted
- Azure Automation Webhook Created
- Azure Blob Container Access Level Modification
- Azure Command Execution on Virtual Machine
- Azure Conditional Access Policy Modified
- Azure Diagnostic Settings Deletion
- Azure Event Hub Authorization Rule Created or Updated
- Azure Event Hub Deletion
- Azure External Guest User Invitation
- Azure Firewall Policy Deletion
- Azure Global Administrator Role Addition to PIM User
- Azure Key Vault Modified
- Azure Network Watcher Deletion
- Azure Privilege Identity Management Role Modified
- Azure Resource Group Deletion
- Azure Service Principal Addition
- Azure Storage Account Key Regenerated
- Base16 or Base32 Encoding/Decoding Activity
- Base64 Encoding/Decoding Activity
- Bypass UAC via Event Viewer
- Clearing Windows Event Logs
- Cobalt Strike Command and Control Beacon
- Command Execution via SolarWinds Process
- Command Prompt Network Connection
- Command Shell Activity Started via RunDLL32
- Component Object Model Hijacking
- Compression of Keychain Credentials Directories
- Conhost Spawned By Suspicious Parent Process
- Connection to Commonly Abused Free SSL Certificate Providers
- Connection to Commonly Abused Web Services
- Connection to External Network via Telnet
- Connection to Internal Network via Telnet
- Creation of Hidden Files and Directories
- Creation or Modification of Domain Backup DPAPI private key
- Creation or Modification of a new GPO Scheduled Task or Service
- Credential Acquisition via Registry Hive Dumping
- Credential Dumping - Detected - Endpoint Security
- Credential Dumping - Prevented - Endpoint Security
- Credential Manipulation - Detected - Endpoint Security
- Credential Manipulation - Prevented - Endpoint Security
- DNS Activity to the Internet
- DNS Tunneling
- Default Cobalt Strike Team Server Certificate
- Delete Volume USN Journal with Fsutil
- Deleting Backup Catalogs with Wbadmin
- Deletion of Bash Command Line History
- Direct Outbound SMB Connection
- Disable Windows Firewall Rules via Netsh
- Domain Added to Google Workspace Trusted Domains
- Encoded Executable Stored in the Registry
- Encoding or Decoding Files via CertUtil
- Encrypting Files with WinRar or 7z
- Endpoint Security
- Enumeration of Administrator Accounts
- Enumeration of Kernel Modules
- Execution from Unusual Directory - Command Line
- Execution of File Written or Modified by Microsoft Office
- Execution of File Written or Modified by PDF Reader
- Execution of Persistent Suspicious Program
- Execution via MSSQL xp_cmdshell Stored Procedure
- Execution via Regsvcs/Regasm
- Execution via TSClient Mountpoint
- Execution via local SxS Shared Module
- Execution with Explicit Credentials via Apple Scripting
- Exploit - Detected - Endpoint Security
- Exploit - Prevented - Endpoint Security
- Exporting Exchange Mailbox via PowerShell
- External Alerts
- FTP (File Transfer Protocol) Activity to the Internet
- File Deletion via Shred
- File Permission Modification in Writable Directory
- File and Directory Discovery
- GCP Firewall Rule Creation
- GCP Firewall Rule Deletion
- GCP Firewall Rule Modification
- GCP IAM Custom Role Creation
- GCP IAM Role Deletion
- GCP IAM Service Account Key Deletion
- GCP Logging Bucket Deletion
- GCP Logging Sink Deletion
- GCP Logging Sink Modification
- GCP Pub/Sub Subscription Creation
- GCP Pub/Sub Subscription Deletion
- GCP Pub/Sub Topic Creation
- GCP Pub/Sub Topic Deletion
- GCP Service Account Creation
- GCP Service Account Deletion
- GCP Service Account Disabled
- GCP Service Account Key Creation
- GCP Storage Bucket Configuration Modification
- GCP Storage Bucket Deletion
- GCP Storage Bucket Permissions Modification
- GCP Virtual Private Cloud Network Deletion
- GCP Virtual Private Cloud Route Creation
- GCP Virtual Private Cloud Route Deletion
- Google Workspace API Access Granted via Domain-Wide Delegation of Authority
- Google Workspace Admin Role Assigned to a User
- Google Workspace Admin Role Deletion
- Google Workspace Custom Admin Role Created
- Google Workspace MFA Enforcement Disabled
- Google Workspace Password Policy Modified
- Google Workspace Role Modified
- Halfbaked Command and Control Beacon
- Hex Encoding/Decoding Activity
- High Number of Okta User Password Reset or Unlock Attempts
- High Number of Process and/or Service Terminations
- Hosts File Modified
- Hping Process Activity
- IIS HTTP Logging Disabled
- IPSEC NAT Traversal Port Activity
- IRC (Internet Relay Chat) Protocol Activity to the Internet
- Image File Execution Options Injection
- ImageLoad via Windows Update Auto Update Client
- Inbound Connection to an Unsecure Elasticsearch Node
- Incoming DCOM Lateral Movement via MSHTA
- Incoming DCOM Lateral Movement with MMC
- Incoming DCOM Lateral Movement with ShellBrowserWindow or ShellWindows
- Incoming Execution via PowerShell Remoting
- Incoming Execution via WinRM Remote Shell
- InstallUtil Process Making Network Connections
- Installation of Custom Shim Databases
- Installation of Security Support Provider
- Interactive Terminal Spawned via Perl
- Interactive Terminal Spawned via Python
- Kerberos Cached Credentials Dumping
- Kerberos Traffic from Unusual Process
- Kernel Module Removal
- LSASS Memory Dump Creation
- Lateral Movement via Startup Folder
- Lateral Tool Transfer
- Launch Agent Creation or Modification and Immediate Loading
- LaunchDaemon Creation or Modification and Immediate Loading
- Local Scheduled Task Commands
- Local Service Commands
- MFA Disabled for Google Workspace Organization
- Malware - Detected - Endpoint Security
- Malware - Prevented - Endpoint Security
- Microsoft 365 Exchange Anti-Phish Policy Deletion
- Microsoft 365 Exchange Anti-Phish Rule Modification
- Microsoft 365 Exchange DKIM Signing Configuration Disabled
- Microsoft 365 Exchange DLP Policy Removed
- Microsoft 365 Exchange Malware Filter Policy Deletion
- Microsoft 365 Exchange Malware Filter Rule Modification
- Microsoft 365 Exchange Management Group Role Assignment
- Microsoft 365 Exchange Safe Attachment Rule Disabled
- Microsoft 365 Exchange Safe Link Policy Disabled
- Microsoft 365 Exchange Transport Rule Creation
- Microsoft 365 Exchange Transport Rule Modification
- Microsoft 365 Teams Custom Application Interaction Allowed
- Microsoft 365 Teams External Access Enabled
- Microsoft 365 Teams Guest Access Enabled
- Microsoft Build Engine Loading Windows Credential Libraries
- Microsoft Build Engine Started an Unusual Process
- Microsoft Build Engine Started by a Script Process
- Microsoft Build Engine Started by a System Process
- Microsoft Build Engine Started by an Office Application
- Microsoft Build Engine Using an Alternate Name
- Microsoft IIS Connection Strings Decryption
- Microsoft IIS Service Account Password Dumped
- Mimikatz Memssp Log File Detected
- Mknod Process Activity
- Modification of Boot Configuration
- Modification or Removal of an Okta Application Sign-On Policy
- Mounting Hidden or WebDav Remote Shares
- MsBuild Making Network Connections
- Mshta Making Network Connections
- Multi-Factor Authentication Disabled for an Azure User
- NTDS or SAM Database File Copied
- Net command via SYSTEM account
- Netcat Network Activity
- Network Connection via Certutil
- Network Connection via Compiled HTML File
- Network Connection via MsXsl
- Network Connection via Registration Utility
- Network Connection via Signed Binary
- Network Sniffing via Tcpdump
- New ActiveSyncAllowedDeviceID Added via PowerShell
- Nmap Process Activity
- Nping Process Activity
- Okta Brute Force or Password Spraying Attack
- Outbound Scheduled Task Activity via PowerShell
- PPTP (Point to Point Tunneling Protocol) Activity
- Peripheral Device Discovery
- Permission Theft - Detected - Endpoint Security
- Permission Theft - Prevented - Endpoint Security
- Persistence via Folder Action Script
- Persistence via Hidden Run Key Detected
- Persistence via Kernel Module Modification
- Persistence via Login or Logout Hook
- Persistence via Microsoft Office AddIns
- Persistence via Microsoft Outlook VBA
- Persistence via TelemetryController Scheduled Task Hijack
- Persistence via Update Orchestrator Service Hijack
- Persistence via WMI Event Subscription
- Persistent Scripts in the Startup Directory
- Port Forwarding Rule Addition
- Possible Consent Grant Attack via Azure-Registered Application
- Possible FIN7 DGA Command and Control Behavior
- Possible Okta DoS Attack
- Potential Application Shimming via Sdbinst
- Potential Command and Control via Internet Explorer
- Potential Credential Access via Windows Utilities
- Potential DLL SideLoading via Trusted Microsoft Programs
- Potential DNS Tunneling via Iodine
- Potential DNS Tunneling via NsLookup
- Potential Disabling of SELinux
- Potential Evasion via Filter Manager
- Potential Modification of Accessibility Binaries
- Potential Password Spraying of Microsoft 365 User Accounts
- Potential Process Herpaderping Attempt
- Potential Remote Desktop Tunneling Detected
- Potential SSH Brute Force Detected
- Potential Secure File Deletion via SDelete Utility
- Potential SharpRDP Behavior
- Potential Shell via Web Server
- Potential Windows Error Manager Masquerading
- PowerShell spawning Cmd
- Privilege Escalation via Named Pipe Impersonation
- Privilege Escalation via Windir Environment Variable
- Process Activity via Compiled HTML File
- Process Discovery via Tasklist
- Process Execution from an Unusual Directory
- Process Injection - Detected - Endpoint Security
- Process Injection - Prevented - Endpoint Security
- Process Injection by the Microsoft Build Engine
- Process Termination followed by Deletion
- Program Files Directory Masquerading
- Prompt for Credentials with OSASCRIPT
- Proxy Port Activity to the Internet
- PsExec Network Connection
- Public IP Reconnaissance Activity
- Query Registry via reg.exe
- RDP (Remote Desktop Protocol) from the Internet
- RDP (Remote Desktop Protocol) to the Internet
- RDP Enabled via Registry
- RPC (Remote Procedure Call) from the Internet
- RPC (Remote Procedure Call) to the Internet
- Ransomware - Detected - Endpoint Security
- Ransomware - Prevented - Endpoint Security
- Rare AWS Error Code
- Registry Persistence via AppCert DLL
- Registry Persistence via AppInit DLL
- Remote Desktop Enabled in Windows Firewall
- Remote Execution via File Shares
- Remote File Copy to a Hidden Share
- Remote File Copy via TeamViewer
- Remote File Download via Desktopimgdownldr Utility
- Remote File Download via MpCmdRun
- Remote File Download via PowerShell
- Remote File Download via Script Interpreter
- Remote SSH Login Enabled via systemsetup Command
- Remote Scheduled Task Creation
- Remote System Discovery Commands
- Remotely Started Services via RPC
- Renamed AutoIt Scripts Interpreter
- Roshal Archive (RAR) or PowerShell File Downloaded from the Internet
- SMB (Windows File Sharing) Activity to the Internet
- SMTP on Port 26/TCP
- SMTP to the Internet
- SQL Traffic to the Internet
- SSH (Secure Shell) from the Internet
- SSH (Secure Shell) to the Internet
- SUNBURST Command and Control Activity
- Scheduled Task Created by a Windows Script
- Scheduled Tasks AT Command Enabled
- Security Software Discovery using WMIC
- Service Command Lateral Movement
- Setgid Bit Set via chmod
- Setuid Bit Set via chmod
- Shell Execution via Apple Scripting
- Shortcut File Written or Modified for Persistence
- Socat Process Activity
- SolarWinds Process Disabling Services via Registry
- Spike in AWS Error Messages
- Startup Folder Persistence via Unsigned Process
- Startup or Run Key Registry Modification
- Strace Process Activity
- Sudoers File Modification
- Suspicious .NET Code Compilation
- Suspicious Activity Reported by Okta User
- Suspicious Cmd Execution via WMI
- Suspicious Endpoint Security Parent Process
- Suspicious Execution - Short Program Name
- Suspicious Execution via Scheduled Task
- Suspicious Explorer Child Process
- Suspicious Image Load (taskschd.dll) from MS Office
- Suspicious ImagePath Service Creation
- Suspicious MS Office Child Process
- Suspicious MS Outlook Child Process
- Suspicious Managed Code Hosting Process
- Suspicious PDF Reader Child Process
- Suspicious PowerShell Engine ImageLoad
- Suspicious Powershell Script
- Suspicious Print Spooler Point and Print DLL
- Suspicious PrintSpooler SPL File Created
- Suspicious PrintSpooler Service Executable File Creation
- Suspicious Process Execution via Renamed PsExec Executable
- Suspicious Process from Conhost
- Suspicious RDP ActiveX Client Loaded
- Suspicious SolarWinds Child Process
- Suspicious WMI Image Load from MS Office
- Suspicious WMIC XSL Script Execution
- Suspicious WerFault Child Process
- Suspicious Zoom Child Process
- Svchost spawning Cmd
- System Log File Deletion
- System Shells via Services
- TCP Port 8000 Activity to the Internet
- Telnet Port Activity
- Threat Detected by Okta ThreatInsight
- Timestomping using Touch Command
- Tor Activity to the Internet
- Trusted Developer Application Usage
- UAC Bypass Attempt via Elevated COM Internet Explorer Add-On Installer
- UAC Bypass Attempt via Privileged IFileOperation COM Interface
- UAC Bypass Attempt via Windows Directory Masquerading
- UAC Bypass Attempt with IEditionUpgradeManager Elevated COM Interface
- UAC Bypass via DiskCleanup Scheduled Task Hijack
- UAC Bypass via ICMLuaUtil Elevated COM Interface
- UAC Bypass via Windows Firewall Snap-In Hijack
- Uncommon Registry Persistence Change
- Unusual AWS Command for a User
- Unusual Child Process from a System Virtual Process
- Unusual Child Process of dns.exe
- Unusual Child Processes of RunDLL32
- Unusual City For an AWS Command
- Unusual Country For an AWS Command
- Unusual DNS Activity
- Unusual Executable File Creation by a System Critical Process
- Unusual File Modification by dns.exe
- Unusual Linux Network Activity
- Unusual Linux Network Connection Discovery
- Unusual Linux Network Port Activity
- Unusual Linux Network Service
- Unusual Linux Process Calling the Metadata Service
- Unusual Linux Process Discovery Activity
- Unusual Linux System Information Discovery Activity
- Unusual Linux System Network Configuration Discovery
- Unusual Linux System Owner or User Discovery Activity
- Unusual Linux User Calling the Metadata Service
- Unusual Linux Username
- Unusual Linux Web Activity
- Unusual Login Activity
- Unusual Network Activity from a Windows System Binary
- Unusual Network Connection via RunDLL32
- Unusual Network Destination Domain Name
- Unusual Parent Process for cmd.exe
- Unusual Parent-Child Relationship
- Unusual Persistence via Services Registry
- Unusual Process Execution - Temp
- Unusual Process Execution Path - Alternate Data Stream
- Unusual Process For a Linux Host
- Unusual Process For a Windows Host
- Unusual Process Network Connection
- Unusual Service Host Child Process - Childless Service
- Unusual Sudo Activity
- Unusual Web Request
- Unusual Web User Agent
- Unusual Windows Network Activity
- Unusual Windows Path Activity
- Unusual Windows Process Calling the Metadata Service
- Unusual Windows Remote User
- Unusual Windows Service
- Unusual Windows User Calling the Metadata Service
- Unusual Windows User Privilege Elevation Activity
- Unusual Windows Username
- User Account Creation
- User Added as Owner for Azure Application
- User Added as Owner for Azure Service Principal
- User Discovery via Whoami
- VNC (Virtual Network Computing) from the Internet
- VNC (Virtual Network Computing) to the Internet
- Virtual Machine Fingerprinting
- Volume Shadow Copy Deletion via VssAdmin
- Volume Shadow Copy Deletion via WMIC
- WMI Incoming Lateral Movement
- Web Application Suspicious Activity: No User Agent
- Web Application Suspicious Activity: POST Request Declined
- Web Application Suspicious Activity: Unauthorized Method
- Web Application Suspicious Activity: sqlmap User Agent
- WebServer Access Logs Deleted
- Whoami Process Activity
- Windows CryptoAPI Spoofing Vulnerability (CVE-2020-0601 - CurveBall)
- Windows Network Enumeration
- Windows Script Executing PowerShell
- Windows Script Interpreter Executing Process via WMI
- Windows Suspicious Script Object Execution
- Zoom Meeting with no Passcode
- Investigate events
- Cases (beta)
- Elastic Security APIs
- Detections API
- Exceptions API
- Lists API
- Detection Alerts Migration API
- Timeline API
- Cases API
- Create case
- Add comment
- Update case
- Update comment
- Find cases
- Get case
- Get all case comments
- Get comment
- Get all case activity
- Get tags
- Get reporters
- Get status
- Delete comment
- Delete all comments
- Delete case
- Set default Elastic Security UI connector
- Update case configurations
- Get current connector
- Find connectors
- Push case
- Add external details to case
- Actions API (for pushing cases to external systems)
- Elastic Security fields and object schemas
- Enable process analyzer after an upgrade
- Release Notes
Release Notes
editRelease Notes
edit7.11.2
editBug fixes and enhancements
edit- Updates warning message when no indices match provided index patterns (#93094).
-
Fixes rule edit bug with
max_signals(#92748). - Fixes issue where the file name in a value modal list would be truncated (#91952).
- Adds an overflow text wrap for rule descriptions (#91945).
- Fixes issue in detection search where searching with the timestamp override field would yield a 400 error(#91597).
-
Replaces
partial failurewithwarningfor rule statuses (#91167). - Fixes "Error loading data" displaying under Analyze Event (#91718).
Known issues
editWhen upgrading from 7.11.0 or 7.11.1 to 7.11.2, certain connectors, including those that connect to Jira, ServiceNow, and IBM Resilient, are not properly migrated during the upgrade process, causing them to be deleted.
Impacts include:
- Security detection rules that have been configured to use the affected connectors as part of their rule actions will no longer create these actions.
- Kibana Alerting and Action alerts that have been configured to use the affected connectors will no longer create these actions.
- Security Case workflow users will need to recreate external connectors before cases can be pushed or updated via the affected connectors.
- Open cases that were previously connected to third-party systems via the affected connectors will need to be re-connected after the connector(s) are recreated.
It is recommended to consider delaying the upgrade to 7.11.2, and instead upgrade to 7.12.0 once it is released.
7.11.0
editBreaking changes
editReferential integrity issues when deleting value lists
The /api/lists DELETE API has been updated to check for references before removing the specified resource(s) from value lists and will now return a 409 conflict if any references exist. Set the new ignoreReferences query param to true to maintain the behavior of deleting value list(s) without performing any additional checks.
Bug fixes and enhancements
edit- Corrects look-back time logic now displays whatever unit the user selects (#81383).
- Fixes a bug where mapping browser fields were automatically reduced (#81675).
- Allows both status data for enabled and disabled rules are now fetchable (#81783).
- Allows autorefresh to be toggled in Advanced Settings (#82062).
- Makes severity and risk score overrides more flexible (#83723).
- Improves DE query build times for large lists (#85051).
- Adds skeleton exceptions list tab to all rules page (#85465).
- Fixes export on exceptions functionality list view (#86135).
- Fixes exception list table referential deletion (#87231).
- Disables delete button for endpoint exceptions (#87694).
Known issues
edit-
The Elastic Endpoint Security rule will report a failure status until the Endpoint sends an alert for the first time. At that point, the next rule execution will succeed.
logs-endpoint.alerts-*index pattern does not get created until the Endpoint sends the first alert (#90401). - In the Alert Details Summary view, values for some fields appear truncated. You’ll only be able to see the first character (#90539).
7.10.1
editBug fixes and enhancements
edit7.10.0
editPost upgrade requirements
editWhen upgrading the Elastic Stack to version 7.10.0 from a previous minor version (7.9.x), perform the following:
-
Grant
view_index_metadatapermissions to any Elastic Security users. This is required to enable event correlation rules. Other previously activated detection rules will continue to run after upgrade.
Breaking changes
editSignals template updated for rollover indices
The create_index_route now checks if the template needs to be upgraded
before creating the index. If the index already exists and the template was upgraded,
the index rolls over so that the write index has the upgraded mapping.
This breaks the old mappings that have risk_score mapped as a keyword.
In the new mapping, signal.rule.risk_score is a float. After rolling over,
there is a conflict between the old and new signal.rule.risk_score for some
features, such as aggregations.
This requires the view_index_metadata permission in Kibana. See (#80019) for details.
Connect incident fields allowed when cases are sent
You can now specify connector incident fields when cases are sent. This includes: * Jira: issue type, priority, and parent issue in the case of a subtask. * IBM Resilient: issue types, and severity. * ServiceNow: urgency, severity, and impact.
See (#77327) for details.
Bug fixes and enhancements
edit- Adds Metadata and Discovery Analysis Jobs to Security Integration (#76023).
- Improves Alert Telemetry for the Security app (#77200).
- Allows passwords to be visible on security screens (#77394).
- Groups features for role management (#78152).
- Warns users when security is not configured (#78545).
- Enhancements for saved object management workflows (#75444).
- Adds EQL search strategy for security (#78645).
- Fetches related events from specified devices (#78780).
- Excludes cloud alias index from EQL query (#81551).
- Telemetry: Displays collected security event sample (#78963).
- Analyze Events: Requests data from new event API (#78782).
- Detections: Handle conflicts on alert status update (#75492).
Known issues
edit-
If you edit a rule while that rule is running, the rule fails. Subsequent successful runs will retain the previous failure message (#82320).
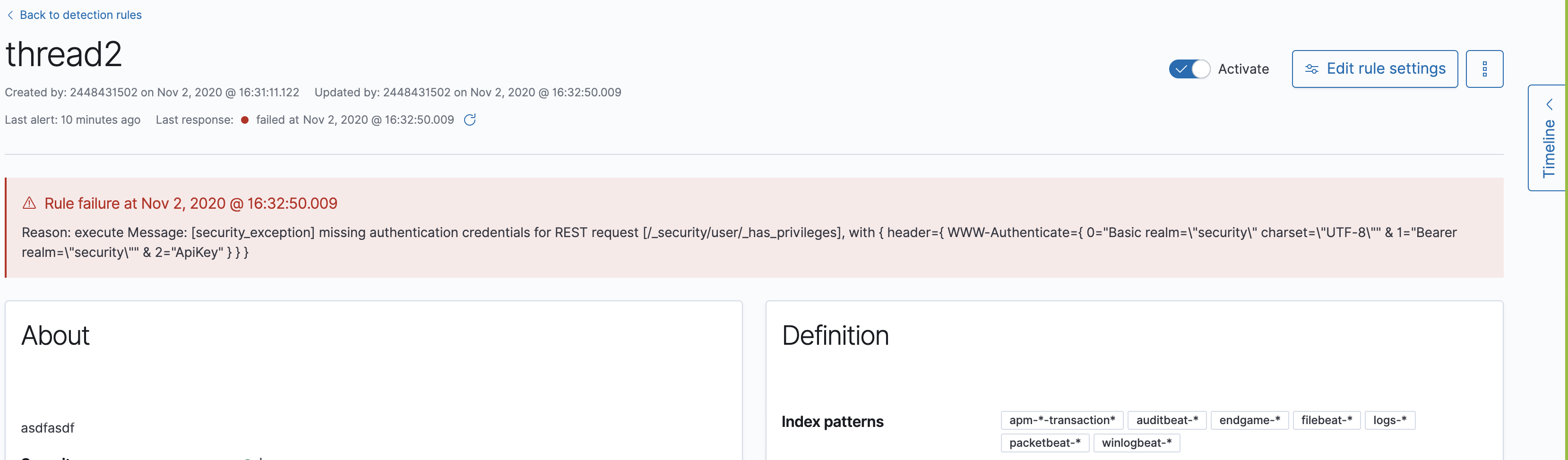
-
When adding a rule exception, you cannot select value lists of type
ip_range. Lists of typeip_rangewill not appear in the Add Exception dropdown as possible values after selecting the is in list operator. (#79511).
7.9.1
editPost upgrade requirements
editAfter upgrading the Elastic Stack to version 7.9.0 and 7.9.1 from a previous minor release (7.8.x, 7.7.x, and so on), you need to:
- Enable access to the Detections page. Previously activated detection rules continue to run after upgrading, and this is only required to enable the UI.
- Enable the process analyzer. This is only required if you want to view graphical representations of process relationships.
Bug fixes and enhancements
edit- Fixes closing alerts via exceptions (#76145).
- Fixes selecting all alerts issue (#75945).
- Fixes issues when exceptions are no longer associated with a rule (#76012).
- Prevents adding exceptions to unsupported rule types (#75802).
- Corrects error messages for insufficient machine learning permissions (#74582).
-
Increases permissions granularity for the
.listssystem index (#75378).
7.9.0
editBreaking changes
editActions API
When you create a ServiceNow connector via the Actions API:
-
The
casesConfigurationobject is obsolete. Instead, useincidentConfiguration. -
To see ServiceNow connectors in the UI, you must use the
isCaseOwnedfield.
These changes only apply to ServiceNow connectors.
Known issues
edit-
After changing the
xpack.encryptedSavedObjects.encryptionKeysetting value and restarting Kibana, you must restart all detection rules (#74393). - When selecting all alerts on the Detections page, some alerts are not marked as selected in the UI (#75194).
- When creating rules, if you have more than one Timeline template the template drop-down list is truncated (#75196).
- Exceptions cannot be added to or viewed in imported rules when the exception list has been deleted or does not exist in the Kibana space (#75182).
- Updates to a Timeline may not be saved when you immediately close the Timeline or navigate to a different page (#75292).
Bug fixes and enhancements
edit-
Fixes rule tags to accept special characters and keywords:
AND,OR,(,),", and*(#74003). - Fixes broken link from the Network map to Kibana index management (#73757).
-
Fixes unresponsive Timeline issues when dragging the
process.hash.sha256field to Timeline (#72142). - Fixes Timeline page scrolling with saved queries issue (#69433).
- Fixes a UI issue with opening and closing alerts (#69217).
- Fixes display of long rule reference URLs (#68640).
On this page
- 7.11.2
- Bug fixes and enhancements
- Known issues
- 7.11.0
- Breaking changes
- Bug fixes and enhancements
- Known issues
- 7.10.1
- Bug fixes and enhancements
- 7.10.0
- Post upgrade requirements
- Breaking changes
- Bug fixes and enhancements
- Known issues
- 7.9.1
- Post upgrade requirements
- Bug fixes and enhancements
- 7.9.0
- Breaking changes
- Known issues
- Bug fixes and enhancements