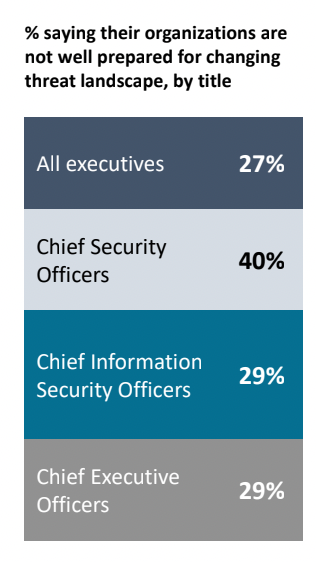
36% of CISOs see the shortage of skilled workers as their key cybersecurity challenge

According to Cybersecurity Ventures, it is estimated that 3.5 million security analyst positions remain unfilled. It’s no surprise, then, that more than a third of CISOs find the skills shortage to be their primary challenge, according to the ThoughtLab study Cybersecurity Solutions for a Riskier World.
With an estimated 3.5 million cybersecurity jobs unfilled, security operations centers are understaffed and overwhelmed
With this in mind, Elastic Training has developed the Elastic Network Security Analyst learning path focused on developing network security analyst skills. This learning path supports common use cases, such as continuous monitoring, threat prevention and detection, and investigation and incident response.
The Elastic Network Security Analyst learning path is designed for security analysts, security engineers, and cybersecurity operators responsible for analyzing network data, finding adversaries in their network traffic, and improving the efficacy of their security operations center (SOC).
The Network Security Analyst learning path consists of seven on-demand modules for self-paced learning, available for individual purchase or as part of an annual Elastic Training Subscription. Each module includes eight hours of expertly designed content and hands-on labs to create an immersive learning experience, plus more modules to come.
What specific modules are included in the Elastic Network Security Analyst learning path?
Read on to learn more about the curriculum to prepare you to become a network security analyst.
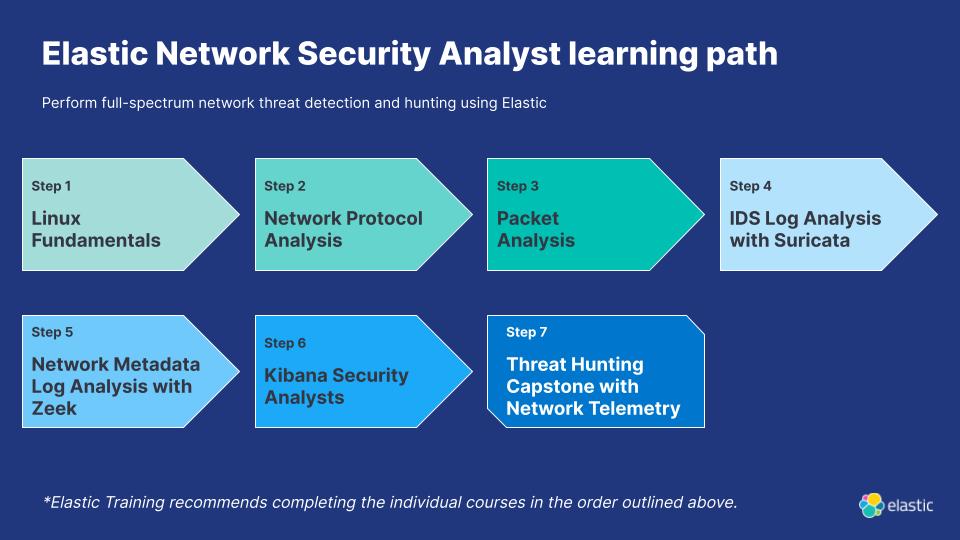
Step 1: Linux Fundamentals
Learn basic operational skills for the Linux command line.
Step 2: Network Protocol Analysis
Explore network protocols to include DHCP, ARP, ICMP, LDAP, Kerberos, SMTP, and SSH.
Step 3: Packet Analysis
Explore networking concepts and packet analysis tools including Wireshark, Stenographer, and Docket.
Step 4: Intrusion Detection System (IDS) Log Analysis with Suricata
Learn how to configure Suricata to automate detections of malicious network traffic.
Step 5: Network Metadata Log Analysis with Zeek
Explore how to install and configure Zeek to improve network security monitoring.
Step 6: Kibana for Security Analysts
Learn how to correlate different data sources and analyze what's happening in your network.
Step 7: Threat Hunting Capstone with Network Telemetry
The learning path concludes with a summary of threat hunting models and techniques, as well as an unguided hunt focused on analyzing network data and identifying malicious actors.
Boost cybersecurity performance with Elastic Training
Cybersecurity is as much about people as it is about technology. Organizations see fewer breaches and faster times to respond when they build a human layer of security and provide more effective training. Start to build more effective cybersecurity awareness and reduce risk with the Elastic Network Security Analyst learning path. And stay tuned for additional training modules to expand your threat hunting skills.

