Top priorities of today’s cybersecurity leader
The role of a security leader requires navigating a complex web of responsibilities while protecting the organization from an increasingly dynamic threat environment. Balancing time between strategic and operational initiatives is challenging. After all, it’s easy to default to tackling the “on fire” problems first for obvious reasons. More challenging, however, is allotting time for forward-looking initiatives that may ultimately save your security team time and effort — and increase your security posture — in the long run.
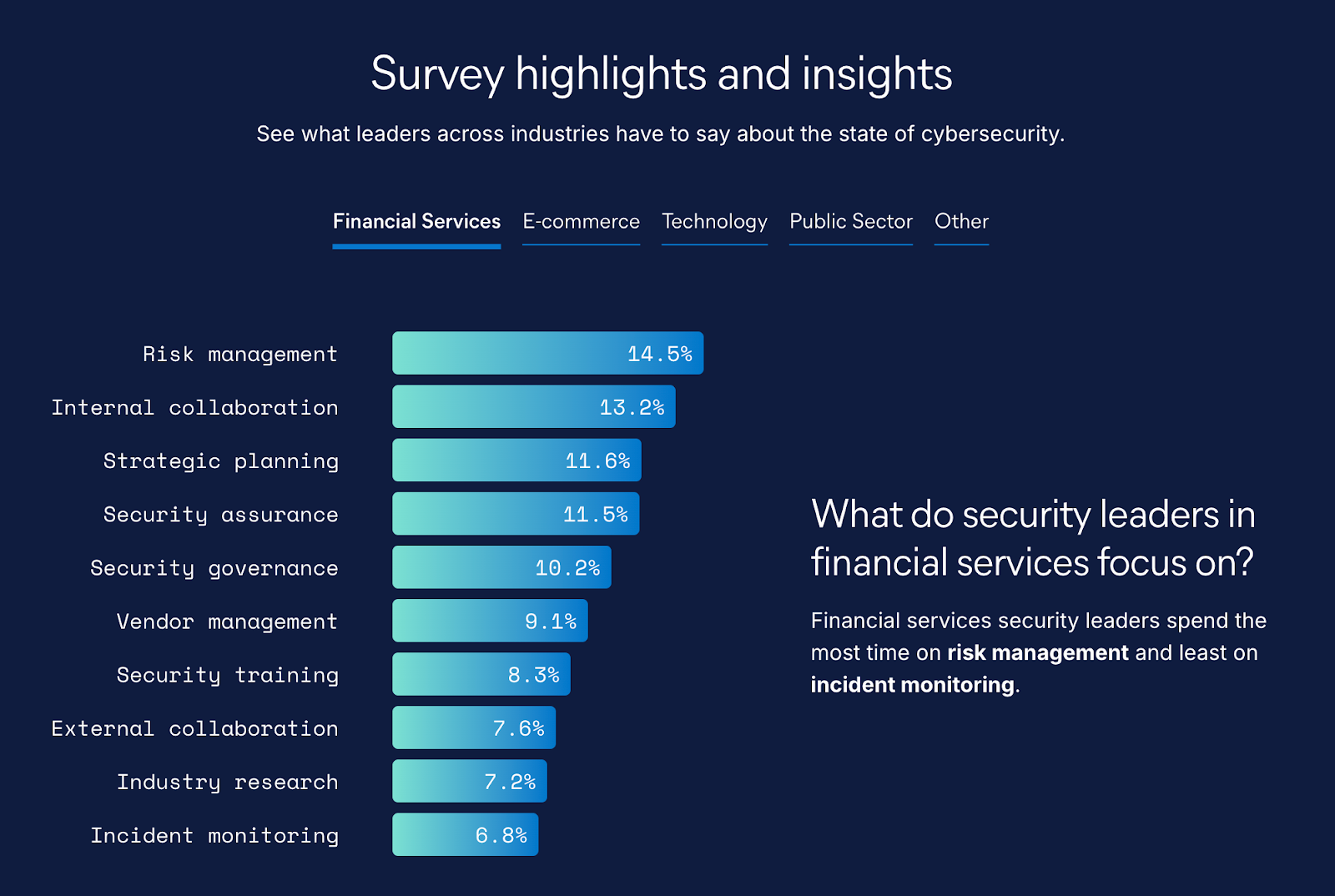
Accounting for both the reactive and proactive job functions a security leader must juggle, here are the top 10 responsibilities of today’s security leader.
Security leader responsibilities
1. Risk management
Identifying, detecting, and responding to threats that could potentially disrupt business operations or compromise sensitive data is core to a security leader’s role. This involves a thorough understanding of the organization's threat vectors and implementing measures that balance security needs with business objectives. Prioritizing risk management helps preemptively address vulnerabilities before they can escalate into crises.
2. Internal collaboration
Cybersecurity is a team sport. Effective security leaders understand the importance of internal collaboration across departments, including IT, legal, finance, HR, executive management, and external partnerships with vendors and industry peers. By fostering a culture of communication and cooperation, security leaders ensure that cybersecurity initiatives are aligned with broader business goals, address evolving threats, and align everyone in the organization on their personal role in maintaining security.
3. Strategic planning
Security leaders must develop a clear, forward-thinking strategy that addresses emerging or anticipated threats (to the extent this is possible), technological advancements, and regulatory changes. A forward-looking plan will naturally align with the organization’s overall mission. It might also include proposed investments in new technologies, suggested architectural implementation, cybersecurity maturity assessment, and active collaboration with other business units to ensure security is integrated across all functions.
4. Security assurance
Continuously monitoring and validating the effectiveness of security controls and protocols ensures that security measures are functioning as intended and that the organization’s defenses are resilient against attacks. Regular audits, penetration testing, and vulnerability assessments are critical components of security assurance, helping you to proactively identify and address any potential weaknesses and strengthen your overall security posture.
5. Security governance
As the central framework that defines how security policies, procedures, and standards are developed, implemented, and enforced within an organization, security leaders must ensure that governance structures are robust and adaptable — enabling the organization to respond swiftly to new threats and regulatory requirements. Good governance also involves establishing clear lines of responsibility and accountability within your cybersecurity team.
6. Vendor, tech, and third-party management
In today’s interconnected world, third-party vendors’ various services (and the outside security risks they may bring) are a part of most organizations’ IT landscape. Effective vendor management is crucial for minimizing associated risks. You’ll need to continuously evaluate the security practices of your vendors, enforce strict contractual obligations, and monitor vendor performance. This is to ensure that this component of the supply chain does not become a weak link in your security posture.
7. Security training
Human error remains one of the most significant threats to cybersecurity. To mitigate this, security leaders must prioritize training that empowers employees to act as the first line of defense against cyber threats. Regular training programs should be designed to keep all staff updated on the latest security practices, potential threats, and their roles in safeguarding the organization’s assets.
8. External collaboration
No organization can tackle cybersecurity challenges alone. Security leaders are increasingly recognizing the value of external collaboration, whether with industry peers, government agencies, or dedicated threat research teams. By sharing information on threats and best practices, you can improve your defenses and help contribute to the broader cyber defense community.
9. Industry research
Staying informed about the latest trends, technologies, and threats in cybersecurity is essential. Industry research helps leaders make informed decisions about the tools and strategies they employ. Keeping up with research, industry reports, and market trends can help ensure that the organization’s cybersecurity practices are cutting-edge and effective.
10. Incident monitoring
Despite best efforts in threat prevention, incidents happen. Continuous monitoring allows security leaders to detect and respond to security breaches as quickly as possible. This priority includes deploying advanced monitoring tools, implementing a rapid response protocol, and establishing playbooks for handling a variety of scenarios.
Prioritizing when everything’s a priority
If everything’s a priority, then nothing truly is . . .
Your role as a security leader is more critical and multifaceted than ever before. While time and resource restraints make it impossible to excel in every one of the above categories, it’s important to understand weaknesses and work to improve upon them. Identifying areas that need more dedication is the first step. Reallocating time away from other priorities (that may seem more pressing) is the second and more difficult step.
Of course, your priorities as a security leader will vary based on your organization type and size, industry, and region. That’s why we surveyed 130 CISOs, CSOs, and equivalent roles across industries and regions to capture their top priorities. See how peers in your industry are prioritizing their time — as well as their levels of stress and autonomy — through this interactive security leaders webpage.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.


