Streamlining threat intelligence reporting with Elastic AI Assistant
Giving valuable time back to threat intel analysts
_(2).jpg)
Empowering analysts with AI-driven reporting
In the ever-evolving landscape of cybersecurity, threat analysts are constantly inundated with new threat intelligence (TI) data. The challenge lies not only in understanding and mitigating these threats but also in efficiently documenting and reporting them. Traditional methods of threat intel reporting can be time-consuming and often require meticulous attention to detail. To address this, we introduced a streamlined approach using Elastic AI Assistant for Security to help with the process of writing these reports. This method uses markdown templates and the Elastic AI Assistant's knowledge base to produce comprehensive and efficient reports.
Transforming threat intel documentation and reporting
Threat analysts play a crucial role in identifying and mitigating potential threats. However, the process of documenting these threats can be laborious. By using Elastic AI Assistant for Security, analysts can focus more on analyzing threats and less on the tedious aspects of reporting. By using Elastic AI Assistant for Security, we can pull relevant information from open source threat reporting and format that information using templates stored in the AI Assistant’s knowledge base. This approach is not a replacement for threat analysts but a tool to enhance their efficiency.
Using Elastic AI Assistant for Security, threat intel professionals are able to analyze the information on the topic they’re reporting on in a standardized format conducive to their reporting workflow. This saves an enormous amount of time by removing many of the manual steps of gathering and normalizing threat data for specific reporting.
Nine steps to produce threat reporting
Every threat intel program will have its own processes for producing threat reporting. At Elastic, we’ve broken this process down into the nine steps below. However, the basic concepts of using Elastic AI Assistant can be modified and incorporated into virtually any workflow for producing threat reporting:
Understand the types of reports needed.
Create templates for each of those report types.
Use Elastic AI Assistant to store those templates in the knowledge base.
Develop a method for gathering threat reporting and data.
Feed threat data to Elastic AI Assistant for the appropriate templates.
Provide additional context or data.
Analyze the threat data within the report template for accuracy and understanding.
Provide the relevance, impact, and any recommendations.
Publish the report.
Using these workflows requires some setup for Elastic AI Assistant. Specific documentation for Elastic AI Assistant for Security is also available. Now, let’s dive deeper into each of the nine steps.
1. Understand the types of reports needed
Every threat intelligence program is going to be different with different types of reporting requirements. Understanding the stakeholders and how they’re going to consume and use threat intel reporting is critical to a successful program. Some programs may only need one or two types of reports, while others may need many more than that. At Elastic, we use several types of templates to cater to different reporting needs. These include:
Intelligence report (INTREP): INTREPs provide a comprehensive overview of a specific threat, including detailed analysis and mitigation steps. This is our most common type of report. It can deal with anything from the discovery of a new malware family to a recent update of threat actor tactics, techniques, and procedures (TTPs.)
Significant activity report (SIGACT): These reports focus on specific, significant threat activities or incidents. Typically, this type of report will be produced to describe a widely publicized event, such as a large data breach or geopolitical event.
Threat trend report (TTR): TTRs analyze trends in threat activities over a period of time, helping to identify patterns and predict future threats. TTRs typically stem from other report types when several reports share common characteristics over time, such as repeated use of a specific TTP or attack themes that happen around certain times of year, such as tax season.
Threat actor profiles (TAP): TAPs profile specific threat actors, detailing their TTPs, historical activities, and potential targets. These reports are regularly updated when new information about a threat actor comes to light and help analysts understand how those threat groups operate and what potential future targets may be.
FLASH reports: These reports are meant for topics that need to be disseminated quickly. Typically a FLASH report is used as a way to get information out to a wider audience while additional analysis takes place. It is not uncommon for a FLASH report to later be converted into a longer report of another type once additional analysis is complete.
2. Create Markdown templates
The second step in this process is to create markdown templates for the different threat intel report types. These templates serve as a standardized format that ensures consistency and comprehensiveness in reporting. They will also allow the Elastic AI Assistant to put the appropriate information into the appropriate places, saving time and tedious effort for analysts.
There are a number of different ways to create these templates, but the best approach is the approach that works most efficiently for each specific threat intel program. At Elastic, we use Google Docs to create our templates using the branding, style, images, and sections that work for our needs. We then use the Markdown conversion tool built into Google Docs to convert our templates to the Markdown format.
The process for other threat intel programs may look different, but the important part is that all of the templates for threat reporting are converted to Markdown so that Elastic AI Assistant can process them.
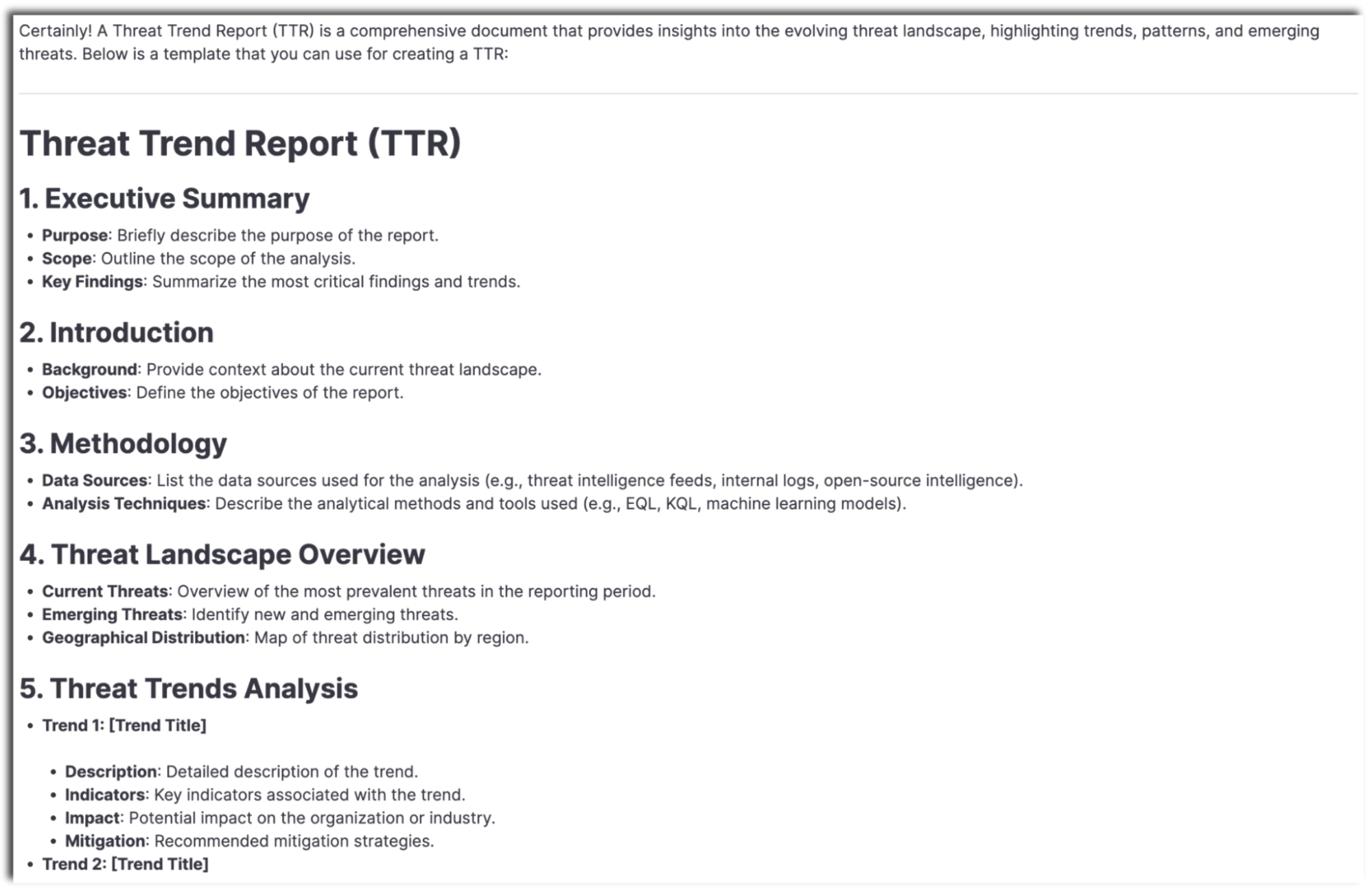
Fun fact: If you need help crafting templates or specific types of reporting in Markdown, Elastic AI Assistant can help out with that, too! Try something like “You are an expert threat intelligence analyst. Help me develop templates that can be used for threat intelligence reporting of the following types: Intelligence report (INTREP), significant activity report (SIGACT), and threat trend report (TTR).”
You can fine-tune the prompt to add in additional report types, specific sections necessary in each report, or formatting options.
3. Use the Elastic AI Assistant to store templates in the knowledge base
Once the markdown templates are created, the next step is to store them in Elastic AI Assistant's knowledge base (KB). This allows analysts to quickly retrieve and use these templates when needed.
Steps to store templates:
1. Access the Elastic AI Assistant: Open the Elastic AI Assistant interface. This can be done by clicking AI Assistant in the top right corner of Kibana. This will open a new prompt.
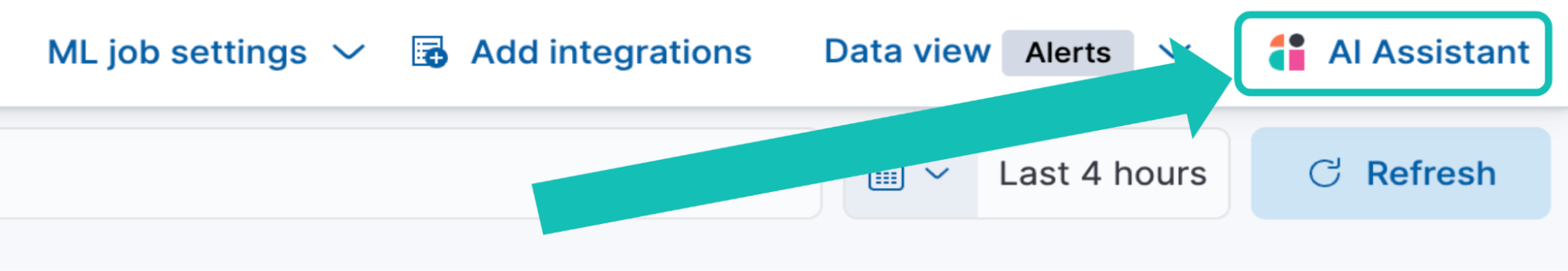
2. Store the template: There are multiple ways to store things in Elastic AI Assistant’s knowledge base for future reference. In version 8.16.0, Elastic made some really great improvements to how the KB is managed and used. Storing things in the KB is now easier than ever, and managing items is simple as well:
From the Elastic AI Assistant, navigate to the KB management page by clicking in the upper right corner of the assistant window. Then, click Knowledge Base.
From here, you can see all items already added to the KB as well as a button in the upper right corner that will allow you to directly upload items. Click + New to add an item to the KB. This will give you a dropdown that looks like this:
For our purposes, select Document. For more details on different types of information that can be added to a KB, you can reference the AI Assistant Knowledge Base documentation.
Clicking Document will give you a new panel where you can directly add information to the KB. You’ll need to give the KB entry a few specific pieces of information:
Name
Sharing (permissions)
Markdown text
Required knowledge
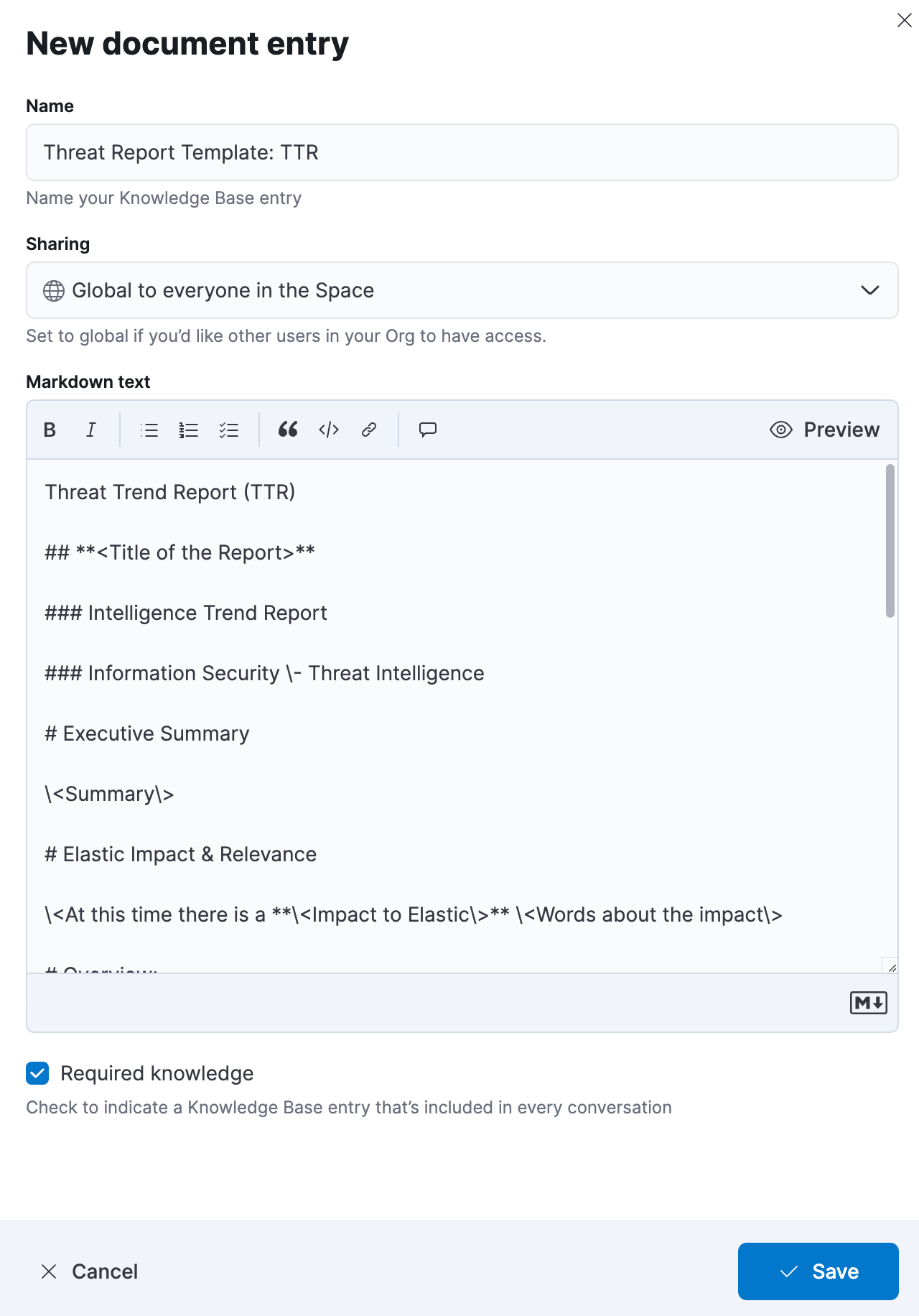
The name is the title that the KB will use in order to reference the item. So, in our case, it’s something along the lines of “Threat Report Template: TTR.”
Sharing allows us to specify who will have access to the KB item with many available options depending on the individual setup and situation (more information about KB permissions here). For this example, I’ve allowed everyone who has access to the space to be able to view this KB item.
The Markdown text field is where we’re going to paste our Markdown template we previously created.
The last step is to check the box that says “Required knowledge” — this will let the assistant use these templates to produce reporting without specific prompting. It is possible to leave this unchecked, but prompts asking for reports will need to specify that content should be retrieved from the knowledge base. After you’ve checked the box, click Save.
Once you save the KB item, you should see a list of all of your KB items under Security AI settings > Knowledge Base.
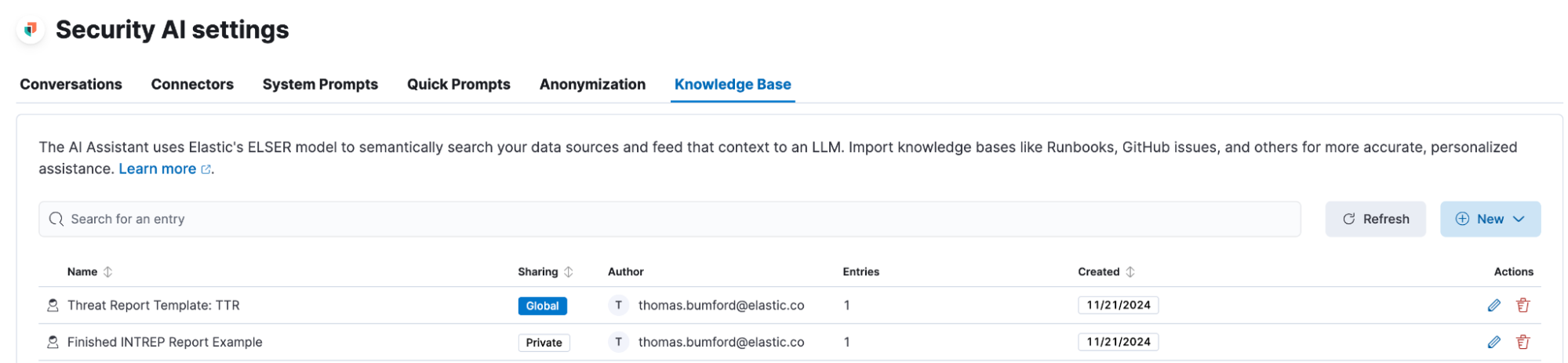
You can also delete or edit these items from here if you need to make any changes.
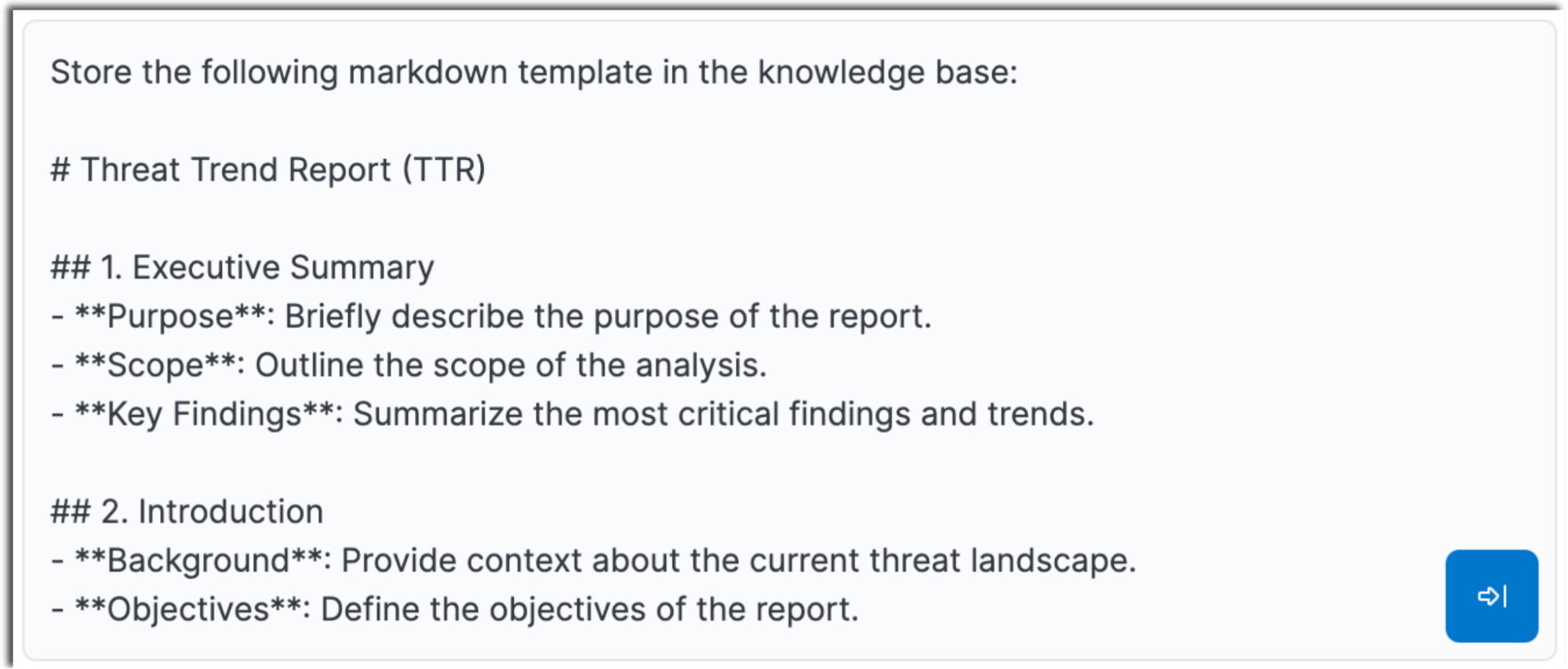
The original method to store items in the KB was to tell the Elastic AI Assistant to do it directly. For example:
Use the following prompt to store the template: Store the following Markdown template in the knowledge base: <insert Markdown template here>
Now, the fun part begins!
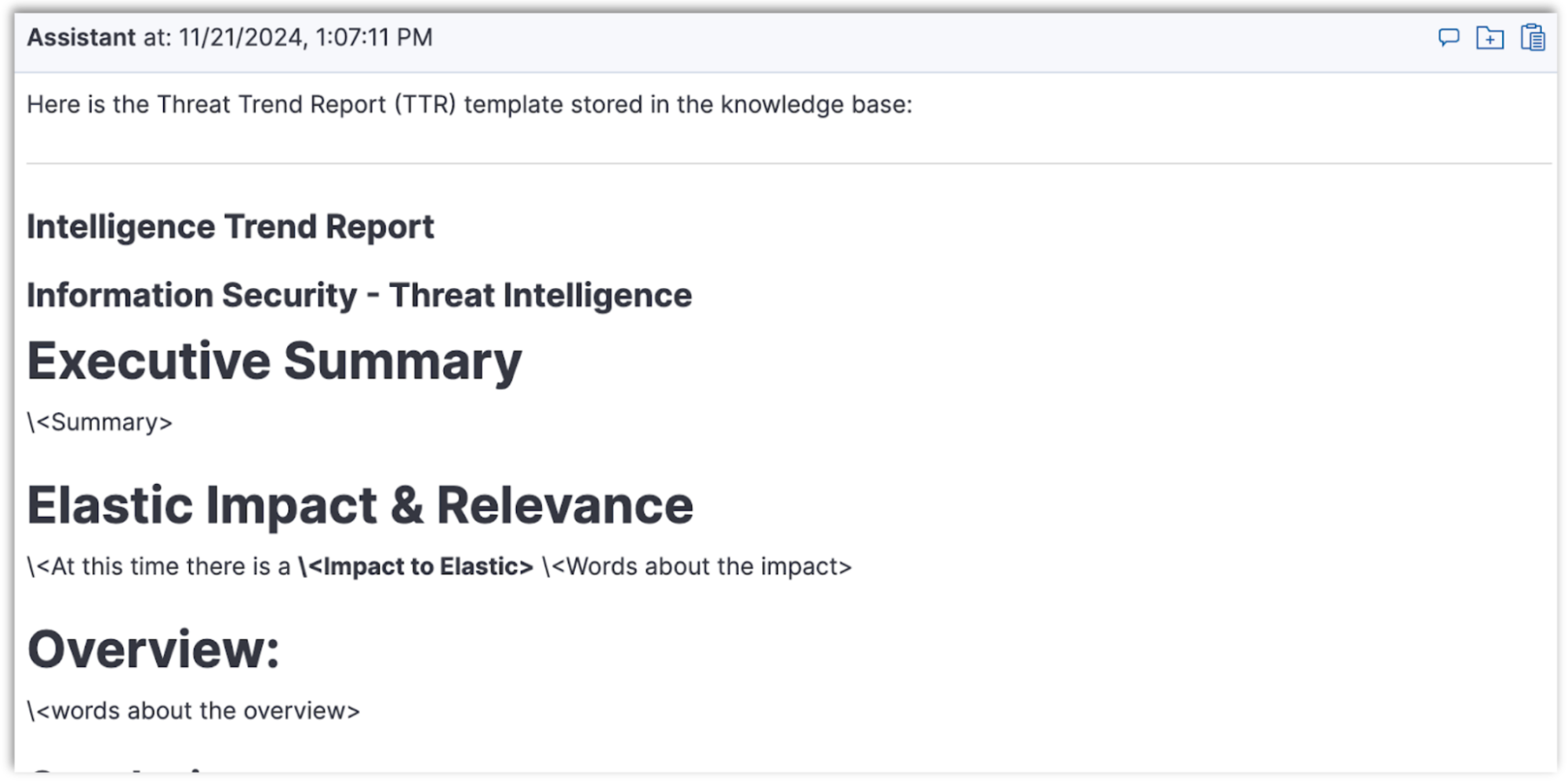
3. Verify Storage: Confirm that the template has been successfully stored by querying the knowledge base. Try this prompt: Show me the TTR Threat Report Template stored in your knowledge base.
The Elastic AI Assistant should return a message showing you the template without any information filled in:
4. Develop a method for gathering threat reporting and data
Establish a systematic approach for gathering threat intelligence data from various sources, such as threat feeds, security blogs, and incident reports. This ensures that the data is comprehensive and up to date. This will vary greatly from program to program and be at least slightly dependent on the sources available. There are several methods that work well for this from manually scanning news sites to automating the process through RSS feeds or even ingesting threat reporting into a threat intelligence platform (TIP.)
At the end of the day, as long as there is a process for gathering open source reporting and other threat data, it will work for these workflows. At Elastic, we have a process that uses RSS feeds to aggregate open source reporting and threat data to one place where it can all be used systematically (be on the lookout for another blog coming soon on how we’re doing this!).
Having a defined process for collecting this information adds efficiency to the process and allows for a number of interesting analysis opportunities relevant to the external threat landscape.
5. Feed threat data to Elastic AI Assistant for the appropriate templates
The next step is to feed the information from the specific threat articles being analyzed to the Elastic AI Assistant — either manually or in an automated fashion (check out these examples for inspiration). This is where the magic happens. The prompt should look something like this:
“Using the <template name> template stored in your knowledge base, analyze the following information and create a new <report type> report from the information.”
Note: The words “stored in your knowledge base” aren’t needed unless the knowledge was submitted as “not required.”
Feel free to get more granular with the prompts as well, such as telling the AI Assistant to leave fields blank if the relevant information isn’t present in the data provided. For example purposes, we’re using a report published by Elastic Security Labs on the XZ / liblzma backdoor, 500ms to midnight: XZ / liblzma backdoor.
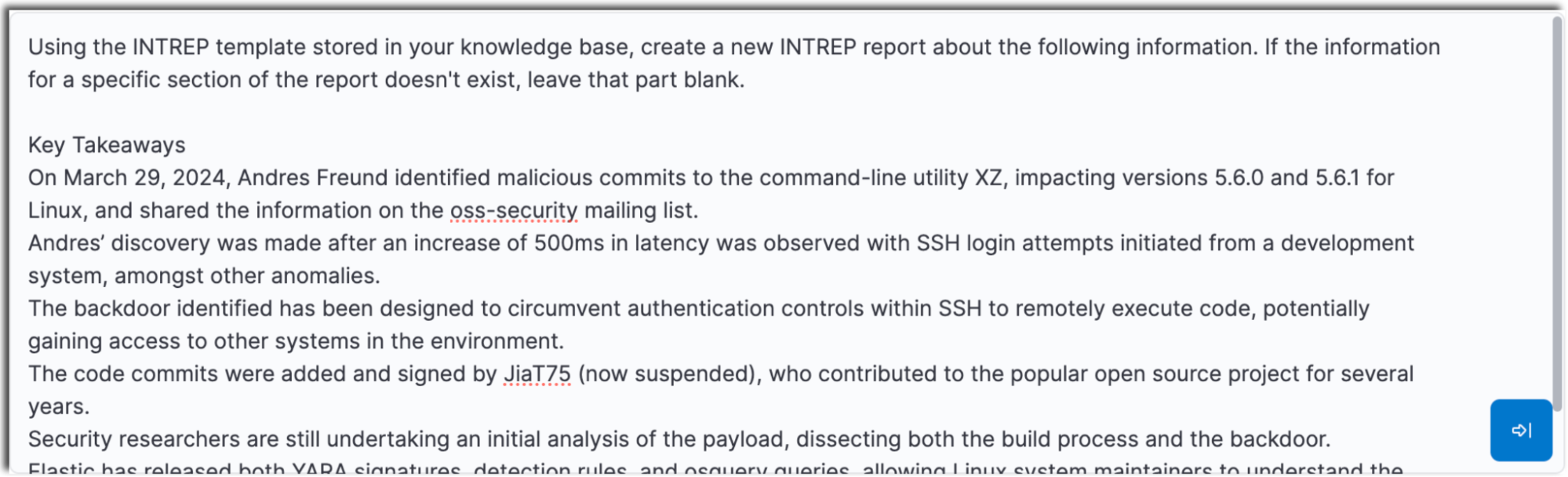
The assistant will then populate your template with the information from the threat data you’ve provided.
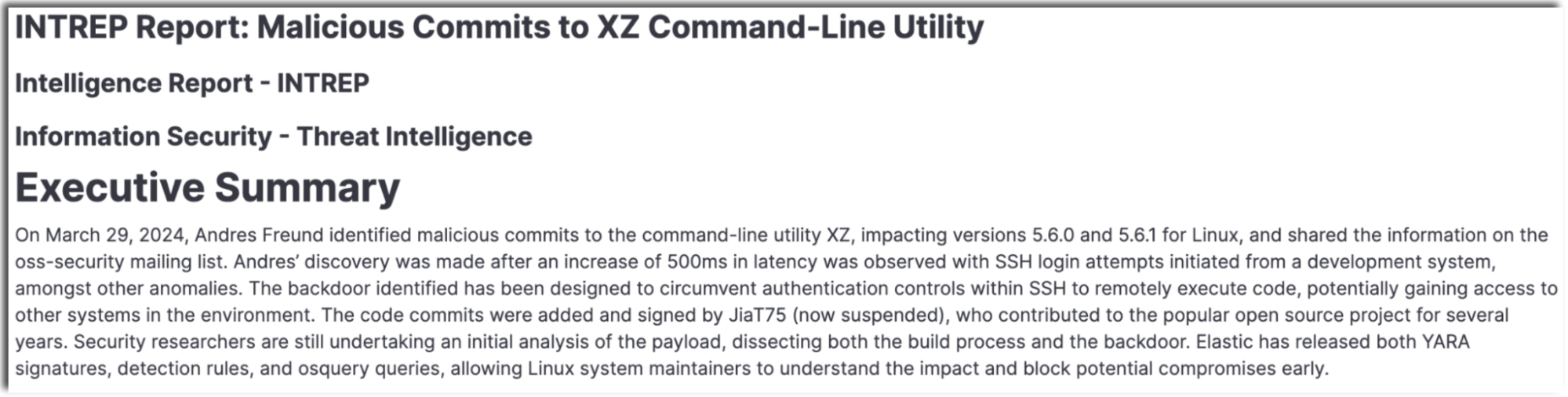
6. Provide additional context or data
What if we’ve got multiple reports or data sources about the same event and want to include information from all of them? Elastic AI Assistant can handle that as well. Simply repeat the process in the same AI Assistant chat with the additional information. Try this as a prompt:
“That looks good. Please include this information as well: <insert additional reporting source or data>”
Elastic AI Assistant will then take the additional information and incorporate it into the same templated report it previously provided.
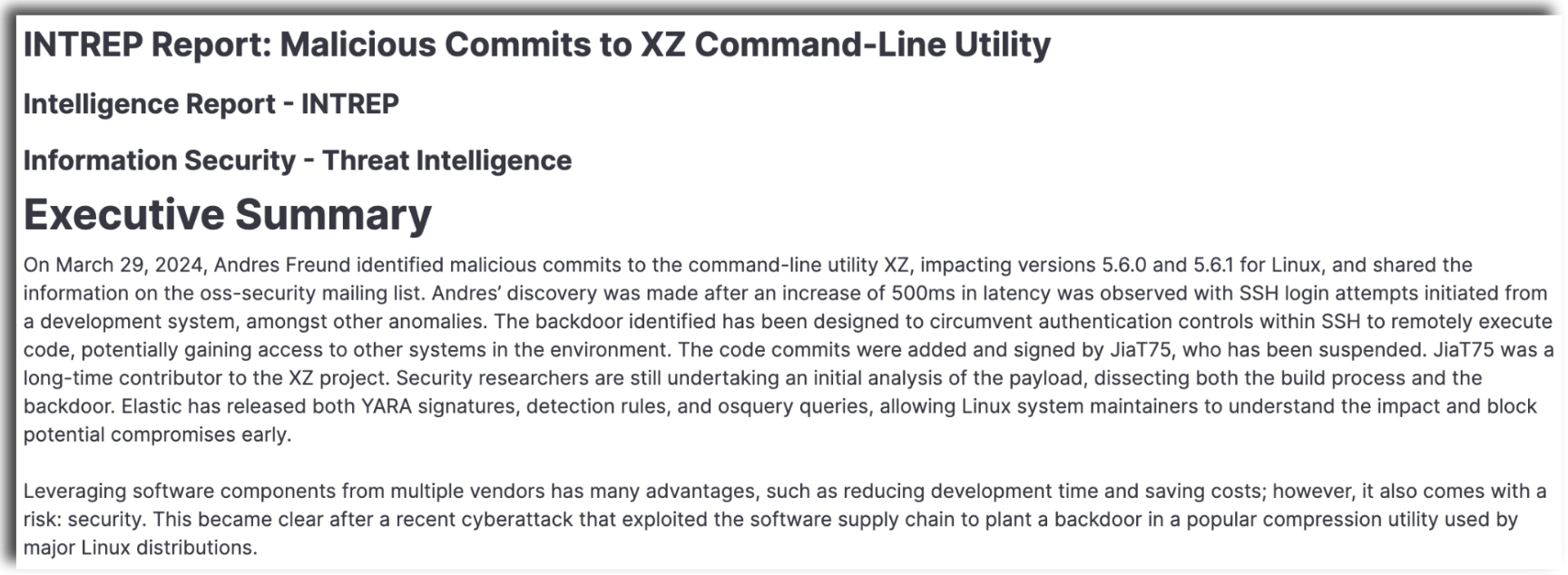
This can be done with multiple reports and data sources and is a great way to include insights from different sources and perspectives without duplicating information.
7. Analyze the threat data within the report template for accuracy and understanding
Once the template is populated, analysts review the report to ensure its accuracy and comprehensiveness. This step is crucial for maintaining the integrity of the report. Elastic AI Assistant is great at gathering data and putting it into the correct format and sections, but it is not perfect and 100% accuracy cannot be guaranteed.
Reading through the report carefully in its current state ensures that the information provided has been correctly formatted to the template, while also giving the analyst an opportunity to gain better understanding of the topic and begin analysis.
8. Provide relevance, impact, and any recommendations
As efficient and smart as Elastic AI Assistant is, there are certain things that are just not meant to be done by a machine. And that’s where the value of a good analyst comes in. The analyst should have a solid understanding of the environment, organization, and technical factors that are relevant to the event being analyzed.
At this point, analysts will need to add their insights on the relevance, potential impact, and recommendations based on the threat data. This step uses the expertise of the analysts to provide actionable intelligence. Essentially, this is the step of taking threat data and turning it into something that is useful for internal stakeholders of the organization.
9. Prepage, review, and publish the report
Now that most or all of the analysis is complete, it's time to put the report into a presentable format. This will differ greatly from program to program, depending on the methods used for dissemination and style guidelines. At Elastic, we take the report in Markdown format and import it into Google Docs for stylistic edits like adding pictures and formatting. But for other programs, this could be accomplished in basically any platform that the analyst would normally use to write and prepare reports. The important part is that the information has been gathered, analyzed, and put into a template that can be easily moved into another platform for publication.
Once the report has been drafted, this is it — the moment we’ve all been waiting for. It’s time to give the report one (or many) final read throughs, fix any formatting issues, add a good picture or two, and publish! The workflows for review and dissemination will be unique to each individual threat intelligence program and will likely need to take several things into account:
Who is this going to? Which individual stakeholders or teams would benefit from this report?
Where should it live? What location would be best for the audience to ingest the report? Is it a messaging platform, a wiki page, an email blast, or somewhere else?
When should it be sent? Timing is everything, especially when publishing to centralized locations. Consider things like time zones, working hours, and vacation schedules when deciding when to publish and disseminate. Criticality of the information will also need to be taken into account to ensure that the report is still valuable when it’s received. It can definitely be a balancing act but should be considered when it’s time to publish.
Are there any metrics to collect that can help drive the intelligence program forward? Many programs disseminate reporting and end the process there. Understanding what happens to a report after it’s been published can be a great value to a threat intelligence program. Who’s been reading the reports? How often do they read it? How quickly are the reports read once they’ve been published? The answers to all of these questions can help shape future reporting, dissemination workflows, and other aspects of the entire process to produce a better product.
At Elastic, we use the logging already available for our dissemination channels (messaging platforms, shared drives, and wiki pages) to produce dashboards that show things like engagement rates, follow-up activities, and other metrics about reports we produce. By understanding which reports are being read more or less often, we can tailor the analysis conducted to the topics and threats that stakeholders are reading and using.
Elastic AI Assistant enhances efficiency and effectiveness
Elastic AI Assistant offers a powerful tool for enhancing threat intelligence reporting. By following these steps, analysts can produce high-quality reports more efficiently. This approach not only saves time but also ensures that threat intel reports are thorough and consistent. While Elastic AI Assistant aids in the reporting process, the expertise and insights of threat analysts remain irreplaceable — making this a valuable tool for enhancing their efficiency and effectiveness without losing the insights and knowledge gained from the threat analyst.
Want to try Elastic AI Assistant for yourself? Download our free version and streamline threat intelligence report creation!
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.