Elastic Cloud Enterprise 2.3 is now available: Featuring role-based access control
We are happy to announce that Elastic Cloud Enterprise (ECE) version 2.3 is now available, bringing one of the most anticipated features, role-based access control (RBAC), into general availability. The addition of RBAC capabilities to ECE allows organizations to safely expand self-service access to ECE for a larger group of users, and relieve some of the operational load off of ECE admins.
ECE 2.3 is available for immediate download.
Role-based access control: More users your way
ECE was built to allow users to manage Elastic Stack deployments at scale, whether managing just a few deployments or thousands. When managing these deployments, many customers wanted to have more fine-grained control over deployment access and management privileges. Now with RBAC on ECE, you can onboard additional users who can perform basic operations without handing over admin user credentials.
"As an Elastic Cloud Enterprise customer, we've been very pleased about the general availability of role-based access control in the latest 2.3 release," said Todd Coleman, CEO, eStruxture Data Centers. "ECE has been a key component to the success of our rapidly scaling and changing business, ensuring that our teams of experts have proper access to the actionable data that they need to solve problems is key to the continued growth of our company."
ECE 2.3 introduces four pre-configured roles that apply to platform and deployments.
The pre-configured roles for RBAC on ECE include the following:
- Platform Admin: Full permissions to manage all platform assets and deployments; equivalent to the default admin user
- Platform Viewer: Read-only permissions to all platform assets and deployments; equivalent to the default read-only user
- Deployments Admin: Create and manage deployments, without any access to platform level assets
- Deployments Viewer: Read-only permissions to existing deployments, without any access to platform level assets
The pre-configured roles are meant to better separate platform level assets, such as repositories, runners, allocators, deployment templates, etc., and managed deployments. This approach is meant to easily delegate permissions to users and teams, supporting a more self-service approach.
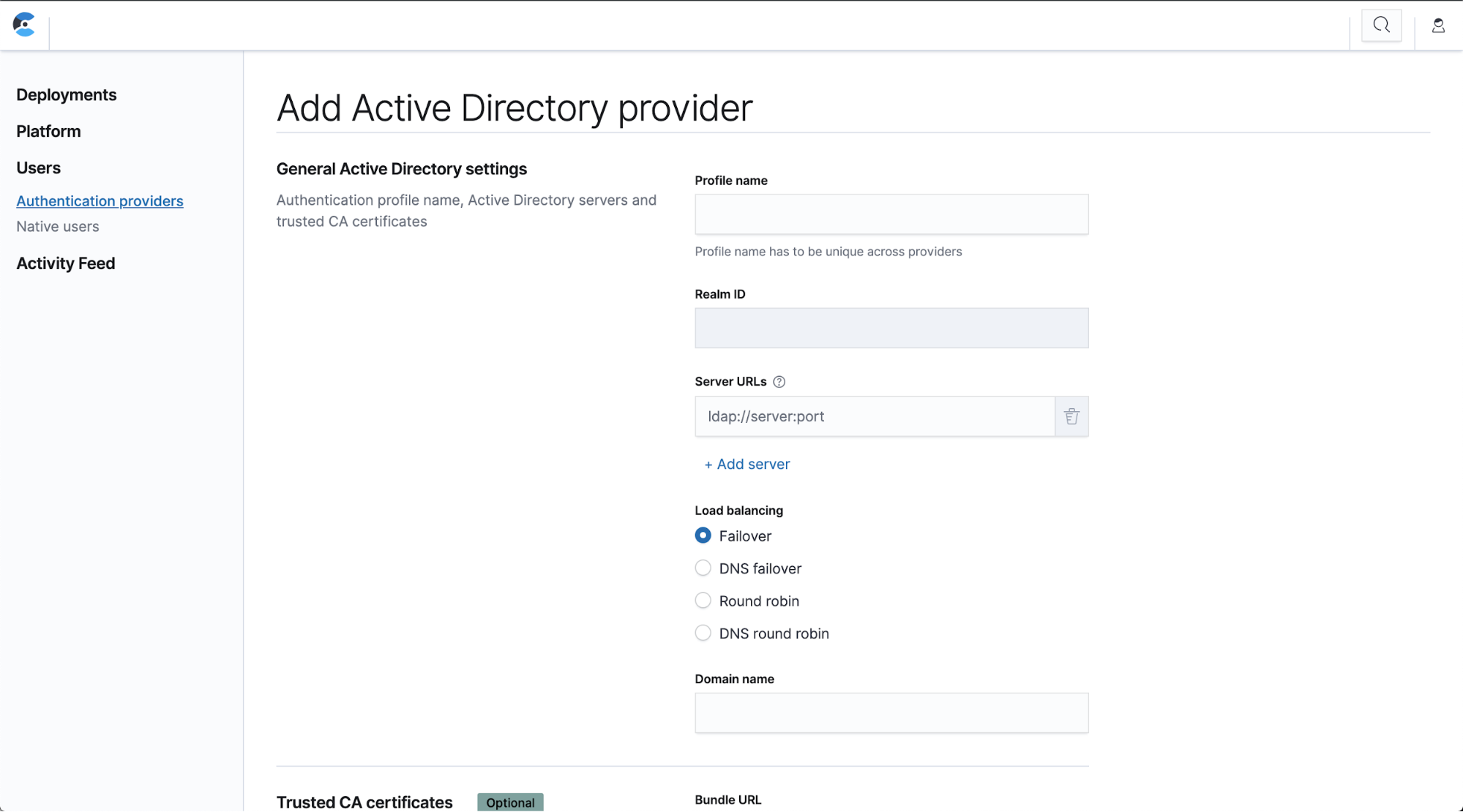
Active Directory, SAML, and LDAP integration
Many customers already have existing identity providers with users, groups, and team structures defined that need to be mapped to different permission sets. With RBAC in ECE 2.3, we streamline that integration by allowing you to plug in users from Active Directory, SAML, or LDAP, making onboarding even easier.
Future improvements
Version 2.3 is the first step towards providing production-ready RBAC in ECE. We intend to bring even more granularity to access control and privileges with customizable deployment-level permissions and greater abilities to separate users by teams.
Check out our in-depth blog about RBAC on ECE and dive into setting up RBAC, using practical advice and API examples.
Additional improvements in ECE 2.3
In addition to RBAC, ECE 2.3 contains a few stability improvements and bug fixes, including:
- Elasticsearch heap dumps: Customers can now create Elasticsearch heap dumps under Operations > Capture heap dump. These require snapshots to be enabled and allow you to download heap dumps when troubleshooting.
- Advanced deployment activity pane: When viewing the activity for a deployment users now have more flexibility when filtering and searching for specific events.
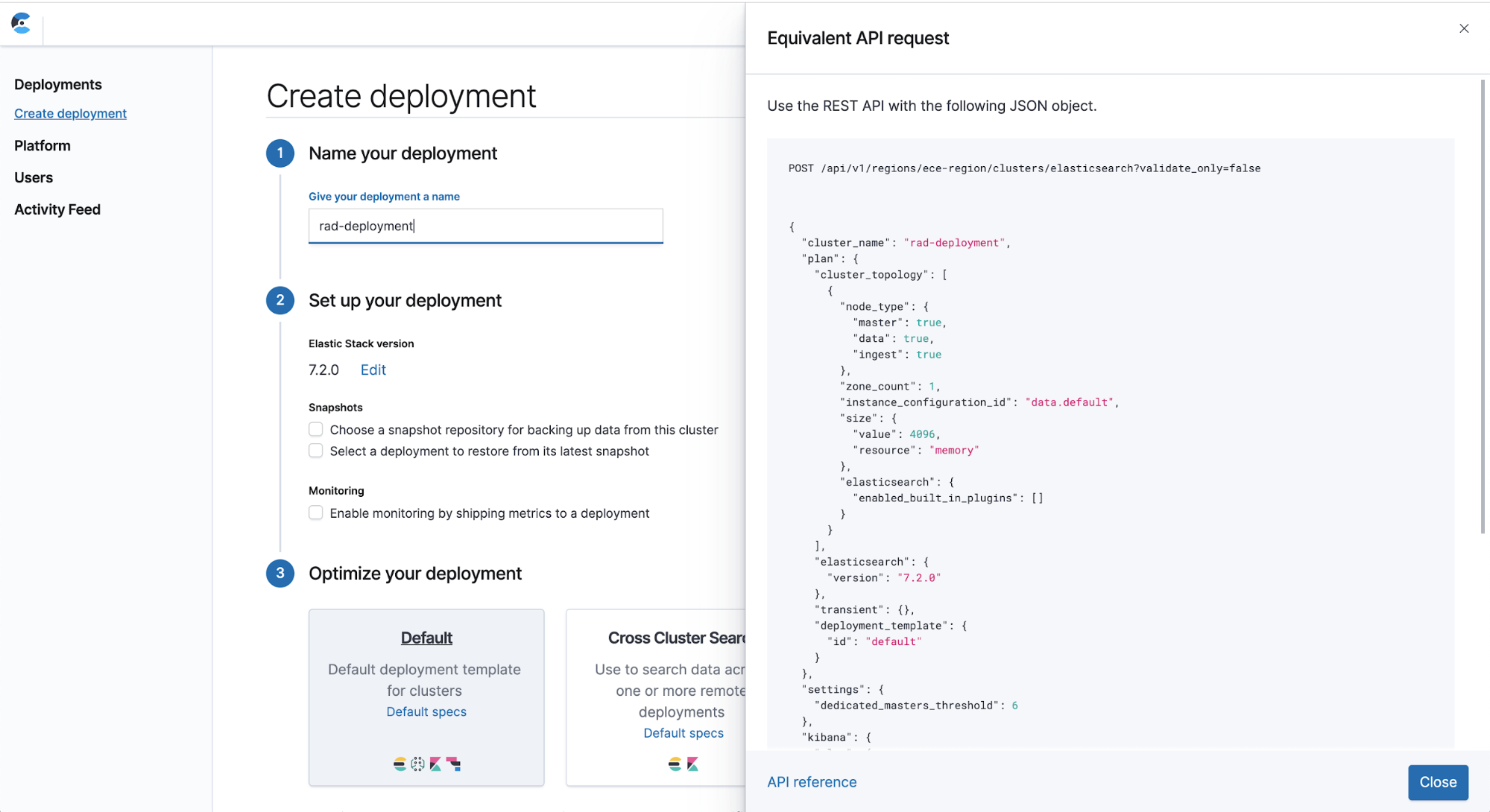
- Deployment REST API payload example: We now offer an easy way to get an example directly from within the UI. By clicking on Equivalent API request next to Create deployment, you can see an example you can copy and paste to create a deployment using the ECE REST API.
For a complete list of changes in ECE 2.3, be sure to check out the release notes. Interested in managing Elasticsearch at scale? You can also try out ECE for free with our 30-day trial.