The 2024 Elastic Global Threat Report: Visibility enhanced
Elastic Security Labs discovers that threat actors are taking advantage of readily available abused security tools and misconfigured environments.
.jpg)
Elastic Security Labs has released the 2024 Elastic Global Threat Report, surfacing the most pressing threats, trends, and recommendations to help keep organizations safe for the upcoming year. Threat actors are finding success from the use of offensive security tools (OSTs), a misconfiguration of cloud environments, and a growing emphasis on Credential Access. This report explores key telemetry from over a billion data points with emphasis on malware trends, adversary tactics, cloud security, and generative AI curated by Elastic Security Labs.
“Understanding the top techniques in the cloud is invaluable to a cloud native company like us,” said Raymond Schippers, the security engineering director for detection and response at Canva, “but we get the most value out of the threat profiles. Most vendors just release a name but having the diamond models helps us understand how you are attributing activity to an adversary. The Global Threat Report provides a great sanity check to ensure that our priorities are aligned with what adversary activity is occurring.”
Download the 2024 Elastic Global Threat Report to gain an in-depth understanding of the threat landscape.
Insights to know from 2024
For your benefit, we’ve distilled the report into a quick overview below. If you’d like additional context, you can check out more highlights and documents on our threat research page.
Malware observed shows adversaries are using off-the-shelf tools to abuse — including generative AI
Within our malware analysis, researchers found that OSTs like Cobalt Strike and Metasploit made up ~54% of observed alerts.
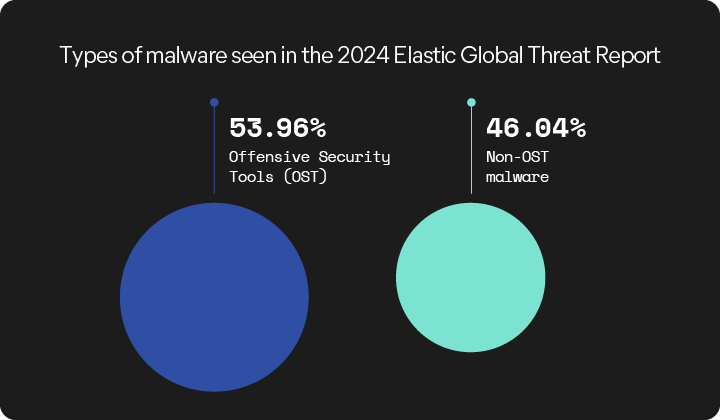
Threat actors abuse these legitimate security tools, and security teams need to understand what malicious usage of these tools looks like. The better you understand OST capabilities, the better you’ll understand malware.
For a deeper dive into how adversaries are abusing Cobalt Strike, check out Elastic Security Labs’ breakdown on REF0657 and the protections created for Elastic Security: Unmasking a Financial Services Intrusion.
Since its debut, the debate around generative AI has been prevalent. Between the suite of defensive AI capabilities we’ve released and research we published back in May, Elastic is no stranger to this conversation either. A lot of organizations are falling victim to fear, and they ask us for our stance on the technology.
Why we’re not worried about generative AI
It’s true that generative AI will provide some assistance to adversaries — social engineering attacks have increased in quality, although our researchers did not observe a notable increase in infection rates over the last year. Defenders can also anticipate a boost in malware development because of recent advances in large language model (LLM) applications. The good news is that this operates like all malware, and this advance can be counteracted by keeping up to date on threats and tuning your protection library.
On the flip side, generative AI has had the greatest impact with defenders. Summarizing collections of security events, automating complex analytical and management tasks, and ranking suggested courses of action are just a few examples of practical ways these technologies are closing the distance between observation and decision.
Generative AI is not providing overwhelming advantages to threat actors and we don’t anticipate that changing any time soon; however, security teams should be aware of and regularly audit their environments — especially for configuration and user errors.
Enterprises are misconfiguring cloud environments, allowing threat actors to thrive
It’s a story that everyone is familiar with: security professionals are stretched far too thin. An abundance of alerts, an overworked analyst, teams trying to navigate complicated environments . . . Unfortunately this has resulted in an overreliance on built-in security controls. Our telemetry indicated that many teams are using cloud platforms without implementing additional, necessary protections.
These insights were discovered in our new section on cloud security posture management (CSPM). Our researchers analyzed the Center for Internet Security (CIS) benchmarks, which are shared by enterprises around the world to identify some of the most common misconfigurations in cloud environments. These benchmarks were compared with environments seen in our telemetry, and these closely overlap with the most commonly observed techniques targeting cloud environments.
Because the Elastic Global Threat Report analyzes cloud telemetry based on cloud service providers (CSPs), we are able to break down the largest misconfigurations by CSP. It’s important for readers to understand that this is not a discussion on which CSP is the safest, but a report on how security teams are configuring their instances.
One of the most prevalent issues was around storage and is seen with nearly 47% of Microsoft Azure failures tied to storage accounts and 30% of Amazon Web Services (AWS) failures coming from S3 checks. Google Cloud users aren’t free from misconfigurations either with nearly 44% of failed checks coming from BigQuery — specifically a lack of customer managed encryption.
Security teams must ensure that cloud resources are protected appropriately and audited regularly. One of the largest takeaways from the CSPM section is the fact that more than 50% of S3 checks that failed did so because of multifactor authentication misconfigurations:
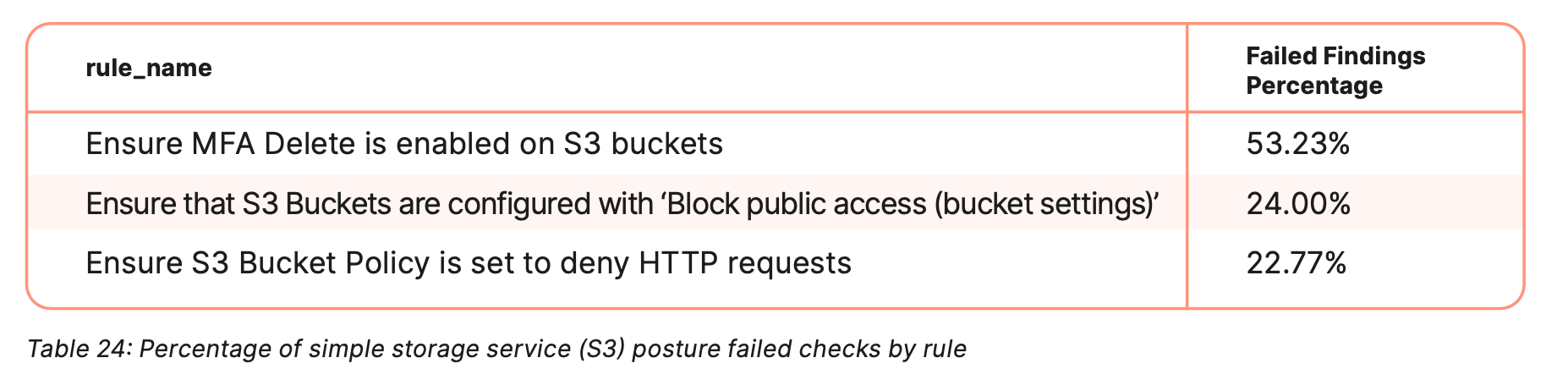
While it can feel like a Herculean effort, it is crucial for security teams to remember that security tools must be tuned and audited regularly. The InfoSec team here at Elastic knows how difficult this is and have written a blog detailing how they rolled out organization-wide, phishing-resistant MFA.
In the wake of successful counters for Defense Evasion, attackers are leaning into legitimate credentials to infiltrate
Continuing a multiyear trend and reflecting the impact of security tools on adversaries, we observed a majority of behaviors related to Defense Evasion. This emphasis is seen in our telemetry across both endpoints and cloud environments, albeit in slightly different ways.
Credential Access in the cloud
With the prevalence of cloud infrastructure on the technology landscape, it’s no surprise that Elastic Security Labs reports heavily on behaviors observed across CSPs. Below are the main tactics according to MITRE ATT&CK standards, observed in cloud environments across the last year.
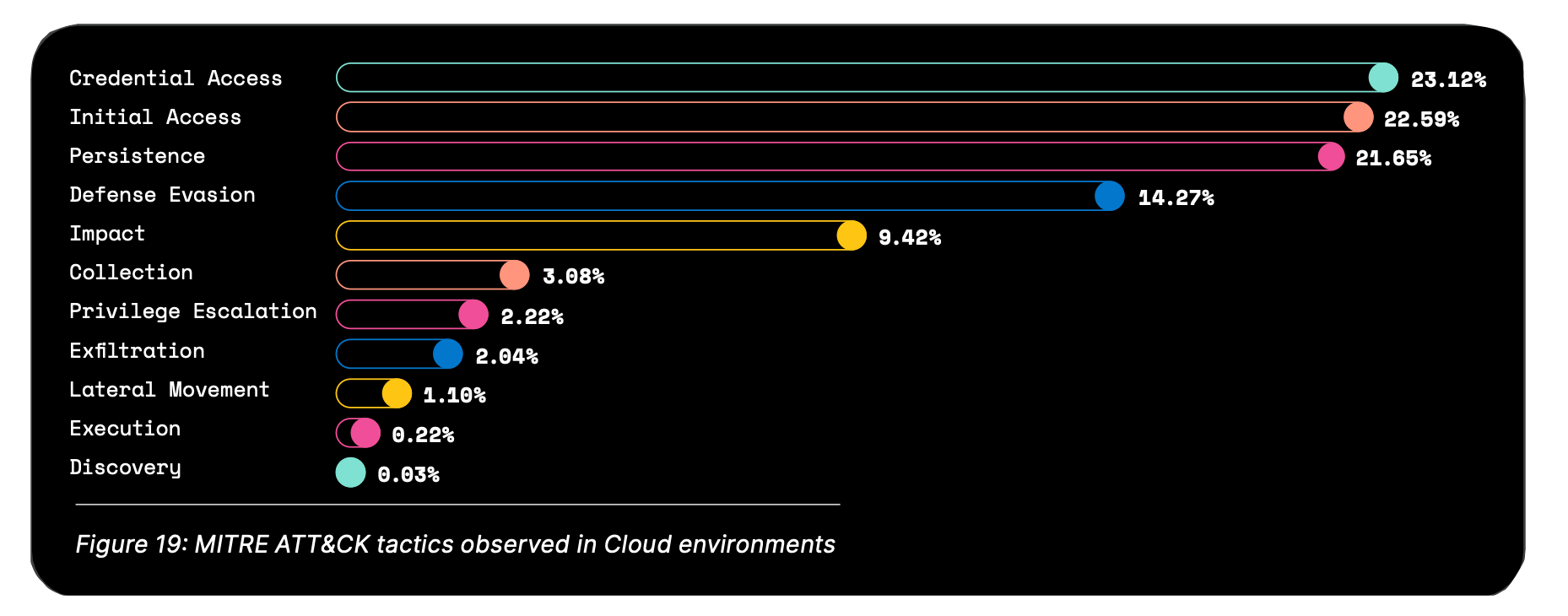
Accounting for 23.12% of all cloud behaviors, the prevalence of Credential Access is observed mostly in Microsoft Azure environments. Specifically, Elastic Security Labs observed a 12% increase in Brute Force techniques — making up almost 35% of all techniques in Microsoft Azure.
Organizations must be aware of the increase in Brute Force attacks, an item seen multiple times in different environments throughout our report. The emphasis on Credential Access goes a step further for the endpoints in our telemetry.
Credential Access in endpoint telemetry
While it maintains a smaller portion of endpoint behavior, we’d like to call out Credential Access in conjunction with its prevalence in the cloud.
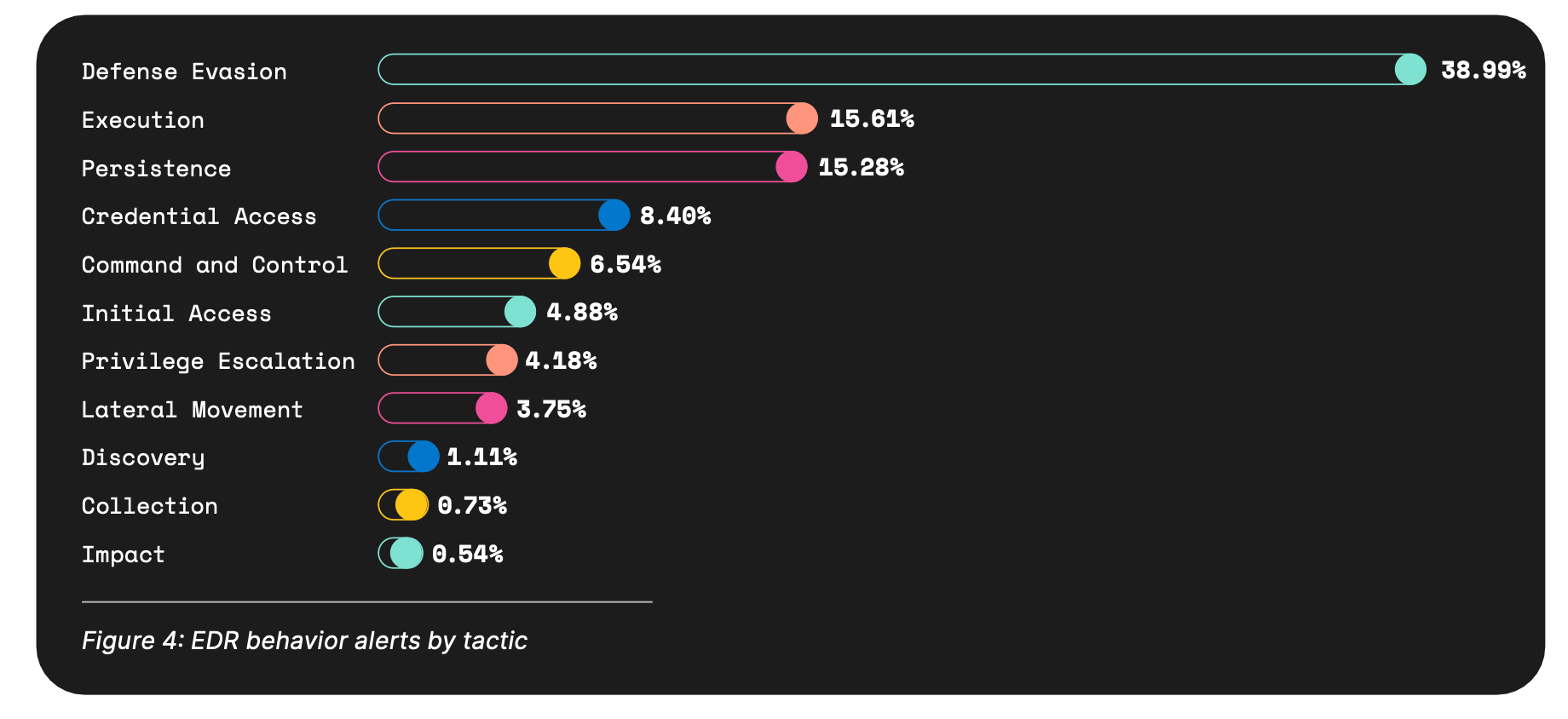
Ranking as the fourth most prominent threat tactic, Credential Access is important to note based on the rise in information stealers and access broker networks. This seemingly minor increase of 3% since last year hardly captures the impact that threat actors have achieved with legitimate stolen credentials.
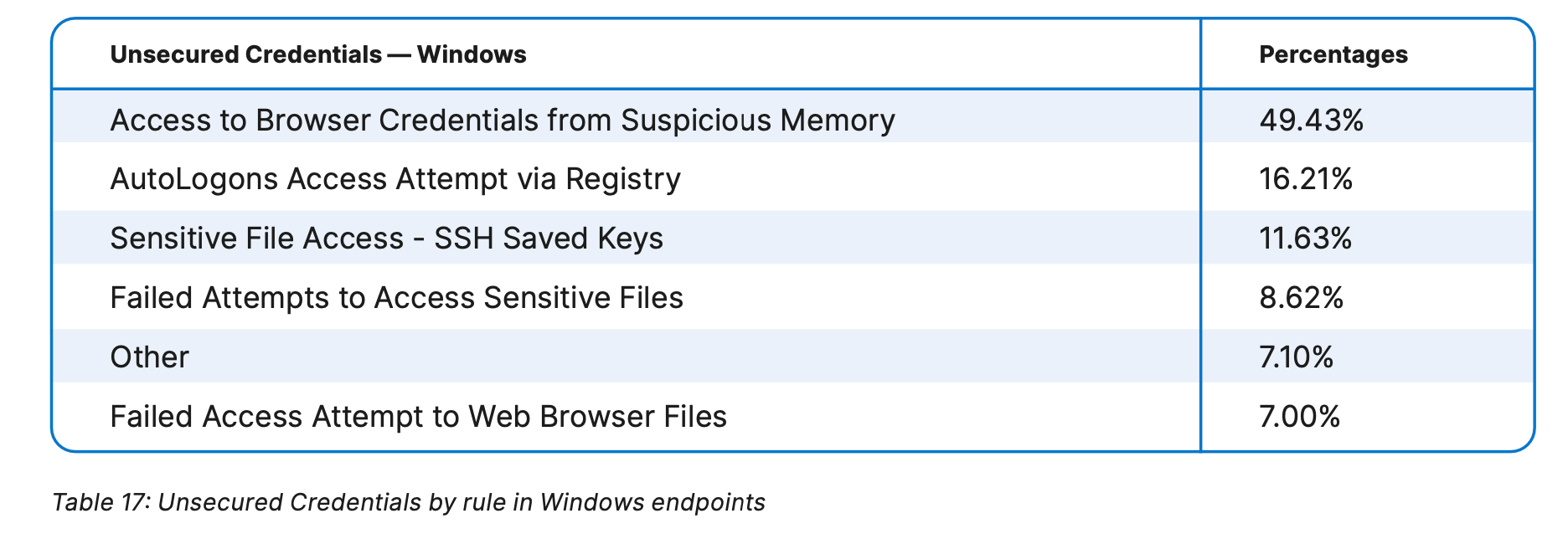
The emphasis here involves techniques like Unsecured Credentials, which rose 31% in Windows endpoints from last year’s analysis. Within Unsecured Credential techniques, Elastic observed that nearly 50% involved stealing credentials from browsers.
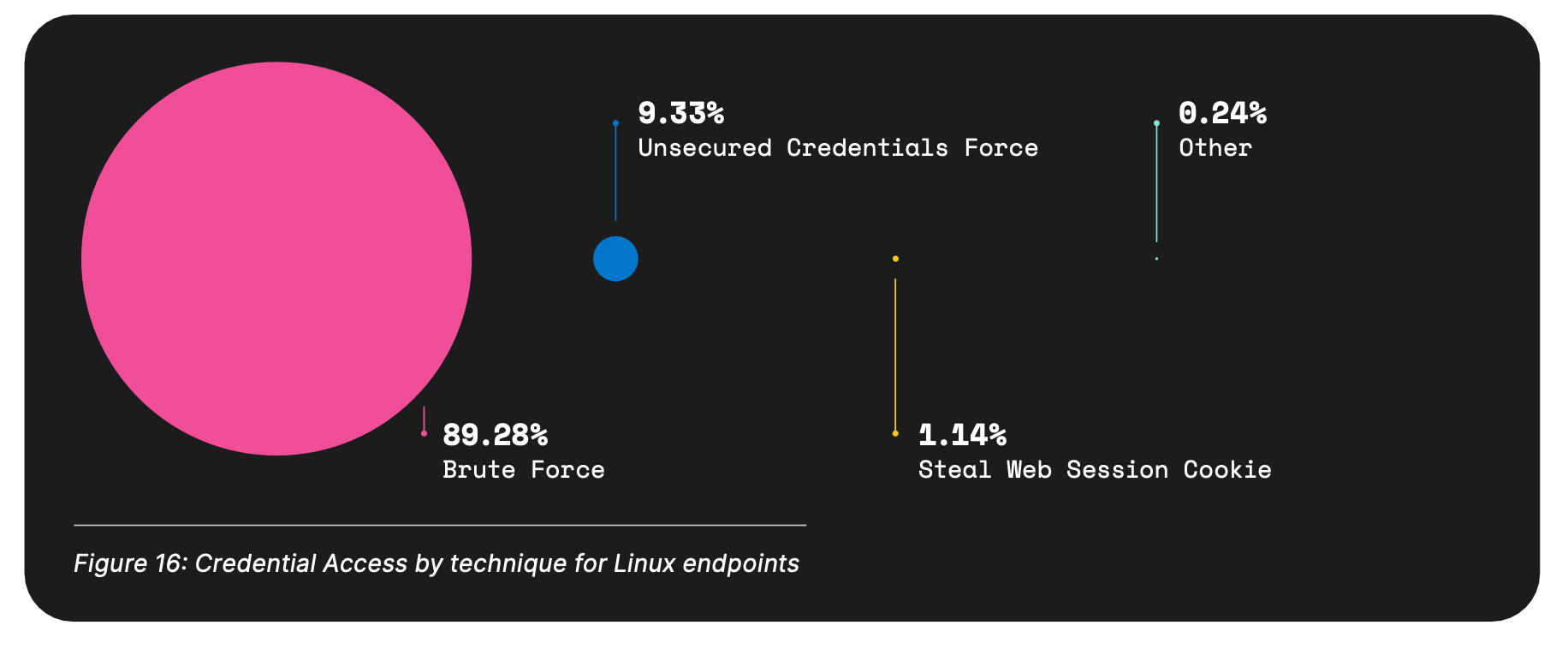
Another example of the rising popularity of Brute Force attacks can be found within Linux environments. While endpoint behaviors account for only 3.2% of the total, 89% of those behaviors involve Brute Force attacks — highlighting the importance of Linux infrastructure, which remains public-facing while maintaining organization-critical applications.
Efforts to mitigate Defense Evasion tactics in security tools have been successful as seen with a 6% decrease in behaviors over the last year. Despite this, threat actors will continue using every available weapon to attack.
A global overview
The Elastic Global Threat Report is made possible thanks to Elastic’s powerful Search AI Platform. We gain our global visibility from Elastic’s foundation in search, resulting in exceptional visibility and an incredible capacity for detecting security threats. Our users share hundreds of millions of events with us every year, generated by Elastic sensors as well as a robust ecosystem of third-party technologies. Not only does this enable Elastic Security to implement regular feature improvements, but it also enables Elastic Security Labs to discover and disrupt previously unknown threats.
This ocean of information provides an additional opportunity to us as custodians — we can share these details with our colleagues in the security community at large. We choose to do this annually to provide readers with actionable information.
Safely explore the threat landscape
Elastic Security Labs is dedicated to providing crucial, timely security research to the intelligence community — whether you’re an Elastic customer or not. The discoveries in this report reinforce something we’ve known for a long time: defender technologies are working. The emphasis on Defense Evasion to navigate and disable these technologies along with the fact that attackers are investing in ways to gather legitimate credentials . . . these findings (and many more) reinforce the importance of well-tuned security products and policies.
Understand these insights and so many more with the free 2024 Elastic Global Threat Report.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.