Elastic SIEM is free and open for security analysts everywhere
Editor’s Note — August 19, 2020: The Elastic SIEM solution mentioned in this post is now referred to as Elastic Security. The broader Elastic Security solution delivers SIEM, endpoint security, threat hunting, cloud monitoring, and more. If you're looking for more specific information on Elastic Security for SIEM use cases, visit our SIEM solution page.
Have you heard the news? Elasticsearch is open source, again.
Security teams must protect attack surfaces that are becoming bigger and more distributed due to the growth of remote work, cloud infrastructure, and other dynamics. These teams understand that meeting this challenge at scale requires the successful incorporation of the appropriate technology into their security operations program. While security information and event management (SIEM) solutions are designed to help analysts detect and respond to potential security threats, there are fundamental limitations with many widely deployed SIEM solutions that often hamstring analysts.
Securing your organization against cyber threats is tough enough in normal times. Unfortunately, during challenging times, the threat landscape gets even more treacherous. Regional, national, or global events, such as elections, major sporting events, or even a global health crisis can exacerbate the challenge. The greater adoption of wide scale telecommuting carries its own risks — with workers operating from unsecured environments, on personal or repurposed equipment, and following processes that might not have been carefully reviewed or tested.
What is Elastic SIEM?
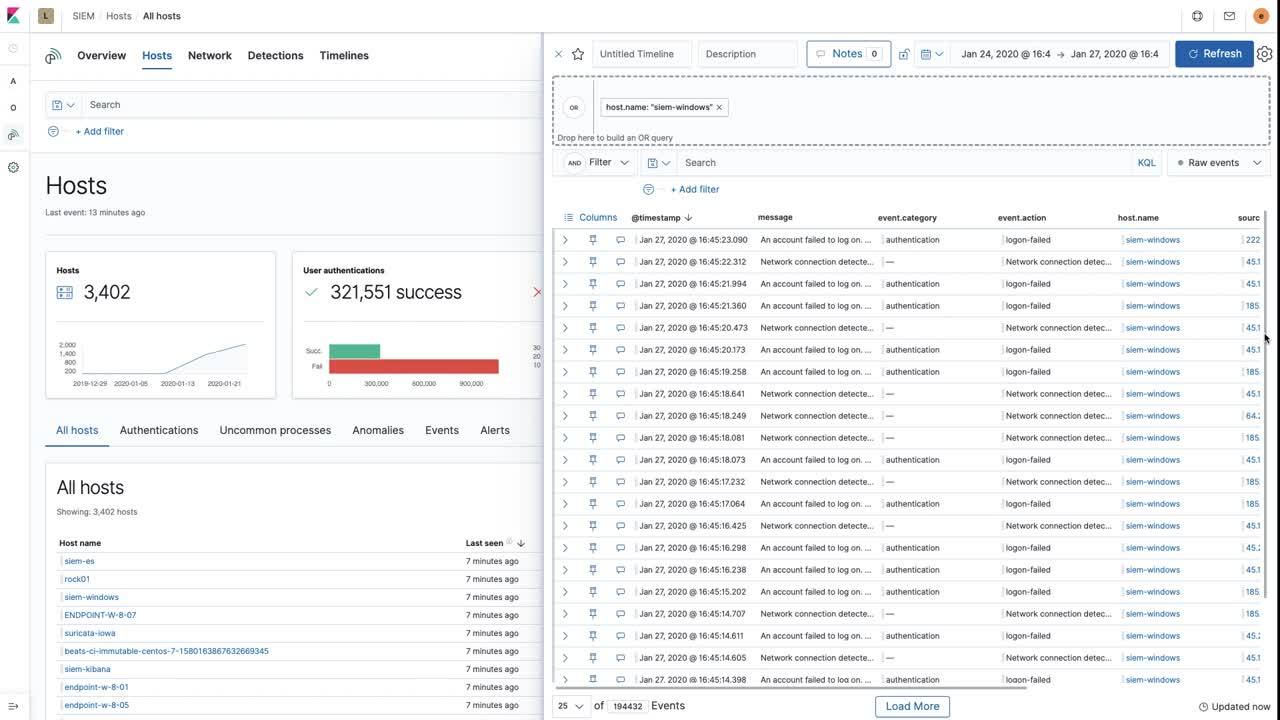
The free and open Elastic SIEM is an application that provides security teams with visibility, threat hunting, automated detection, and Security Operations Center (SOC) workflows. Elastic SIEM is included in the default distribution of the most successful logging platform, Elastic (ELK) Stack software. It ships with out-of-the-box detection rules aligned with the MITRE ATT&CK™ framework to surface threats often missed by other tools. Created, maintained, and kept up-to-date by the security experts at Elastic, these rules automatically detect and address the latest threat activity. Severity and risk scores associated with signals generated by the detection rules enable analysts to rapidly triage issues and turn their attention to the highest-risk work. If you need to deploy a SIEM solution today and see immediate value, we provide the best and easiest way to do it.
Elastic SIEM packs a lot of power. Built with the speed and scalability of Elasticsearch as its underlying search platform, it maintains analyst velocity with:
- An overview page to show SOC status and security posture
- Dashboards for threat hunting and situational awareness
- Integration with Elastic Maps, Elastic Lens, and the rest of Kibana
- A detection engine for automated detection
- A unique timeline investigator with investigation templates for analysts
Organizations use these capabilities to eliminate blind spots and arm analysts to drive down mean time to detect (MTTD) and mean time to respond (MTTR).
Why free SIEM?
Elastic is on a mission to help organizations improve their security posture by eliminating blind spots and arming their analysts with the products and workflows they need to protect data and infrastructure. Spurred by the security community’s widespread adoption of the Elastic Stack for threat hunting, fraud detection, and security monitoring, we wanted to make it even easier for users to deploy our products for security. We first worked in collaboration with our community to develop Elastic Common Schema (ECS), which streamlines the normalization of data from disparate sources — whether from network and host technologies or cloud infrastructure and applications. We launched Elastic SIEM in June 2019, introducing the industry’s only free and open SIEM packaged with actively maintained SIEM detection rules.
We demonstrated the latest Elastic SIEM capabilities to dozens of visitors at our RSA 2020 conference booth in San Francisco. After nearly every demo, when asked about the licensing costs, we were pleased to be able to answer that everything we’d just showed was free and open to use. “Wait, you mean a trial?” “No, forever.” “Really?” “Yes.”
Get started and deploy at scale for free
Free and open might be new to SIEM, but it is not new to Elastic. For years, organizations have built security analytics projects for threat hunting and SIEM on the Elastic Stack. They have enjoyed unlimited scale, unlimited-duration proofs of concept with no licensing cost, and none of the vendor headaches usually associated with evaluating new enterprise software. We’re building on this with Elastic SIEM, which is available for download to run on-premises, in a virtual or containerized environment, or in your cloud or ours.
Resource-based pricing for commercial extensions
The free and open Elastic SIEM provides a solid base for SOC operations to use at any scale and for as long as they need it. Elastic also provides commercial extensions to Elastic SIEM that take it to the next level, including integration of machine learning-based anomaly detection, external alert notifications, and integration with third-party case/ticket management platforms, incident response systems, and SOAR platforms.
SIEM vendors typically charge their customers based on data ingestion rate, such as average events per second (EPS) or daily indexed volume (DIV). This licensing model has several drawbacks. First, it creates a financial disincentive for organizations to collect and ingest the data that might actually help them detect threats more effectively. Second, it creates a situation where some security data is “dropped on the floor” or sent to another storage area where special processes need to be invoked to ever look at it. Third, it creates an unpredictable and uncomfortable budgeting situation for these organizations planning for expansion of data.
In contrast, our resource-based pricing does not charge by data ingestion rate, nor by seat. Instead, it allows you to pay only for what you use in terms of resources supporting your security operations. You get to choose how much data you ingest, how long you retain it, and what kind of security workflows you enable on the data.
Why open SIEM?
What do we mean by open? It’s way more than just “open source” or “open code,” which have defined a new age of disruptive approaches to SIEM. Our users value the open community, open roadmap, open data model, and an open approach to detections.
Open community
One of the things that users tell us they love about Elastic from both a cultural and technological perspective is the community. If you have any questions, the Elastic community’s got your back. When it comes to SIEM, our team members answer user questions daily on the SIEM Discuss Forum and in our public #siem Slack channel, as well as in other places we engage with users.
Community is especially critical in cybersecurity. The security space isn't about a single tool or individual, but rather how teams collaborate across organizations, geographies, datasets, and practices to protect valuable data and infrastructures against threats. With Elastic SIEM, Elastic actively fosters this security community — whether through our products, partnerships, sponsorships, training, or the amazing original research coming out of the Elastic community itself.
Many organizations have used Elastic as their security analytics platform and home-baked SIEM solution for years. For example, SANS, one of the leaders in security training and certification, has long used Elasticsearch as a training platform for SIEM, not to mention the many other tools and training programs that leverage Elastic for threat hunting, insider threat, and fraud detection.
Open roadmap
Another powerful aspect of open development practices that we’ve adopted is an open roadmap and issue tracker. Whether you are just trying to figure out what we are focused on or chasing down a specific enhancement request, you can just jump into the public Github issues, start educating yourself, upvote topics, and file new ones. You’ll see our designs for future directions completely in the open, as well as our engineers engaging in triaging and getting more details on your ideas. We also accept contributions, which is another way to move the needle.
Open data model
In the Elastic Stack, every piece of information you add is “just another index” in our open data model. Data is stored as JSON, with no proprietary formats. We clearly document our schema assumptions in ECS, which is community-driven and extensible. This means no vendor lock-in.
Elastic SIEM includes “inspect” functions so you can see the actual queries used by the app. Our SIEM rules are published and fully documented, so you can see and understand the detection logic — no “black box” detections here. Even our machine learning-based anomaly detection jobs are readily viewable and can be copied and edited to create your own custom jobs. Want to add another data source to SIEM? No problem. On top of that, we never rate-limit your ability to get data out; it’s your data and you have the control.
Try it for yourself
Want to give Elastic SIEM a spin? Try Elastic SIEM on Elasticsearch Service on Elastic Cloud, or check out an Elastic SIEM demo. Already have ECS-formatted data format in Elasticsearch? Just upgrade to 7.6 of the Elastic Stack to get your SOC rolling.
Want to experience Elastic Security live? Virtually participate in an Elastic{ON} Tour event.
Learn more about SIEM with the SIEM Overview Guide.