Elastic surveyed government workers on threat hunting — this is what we found
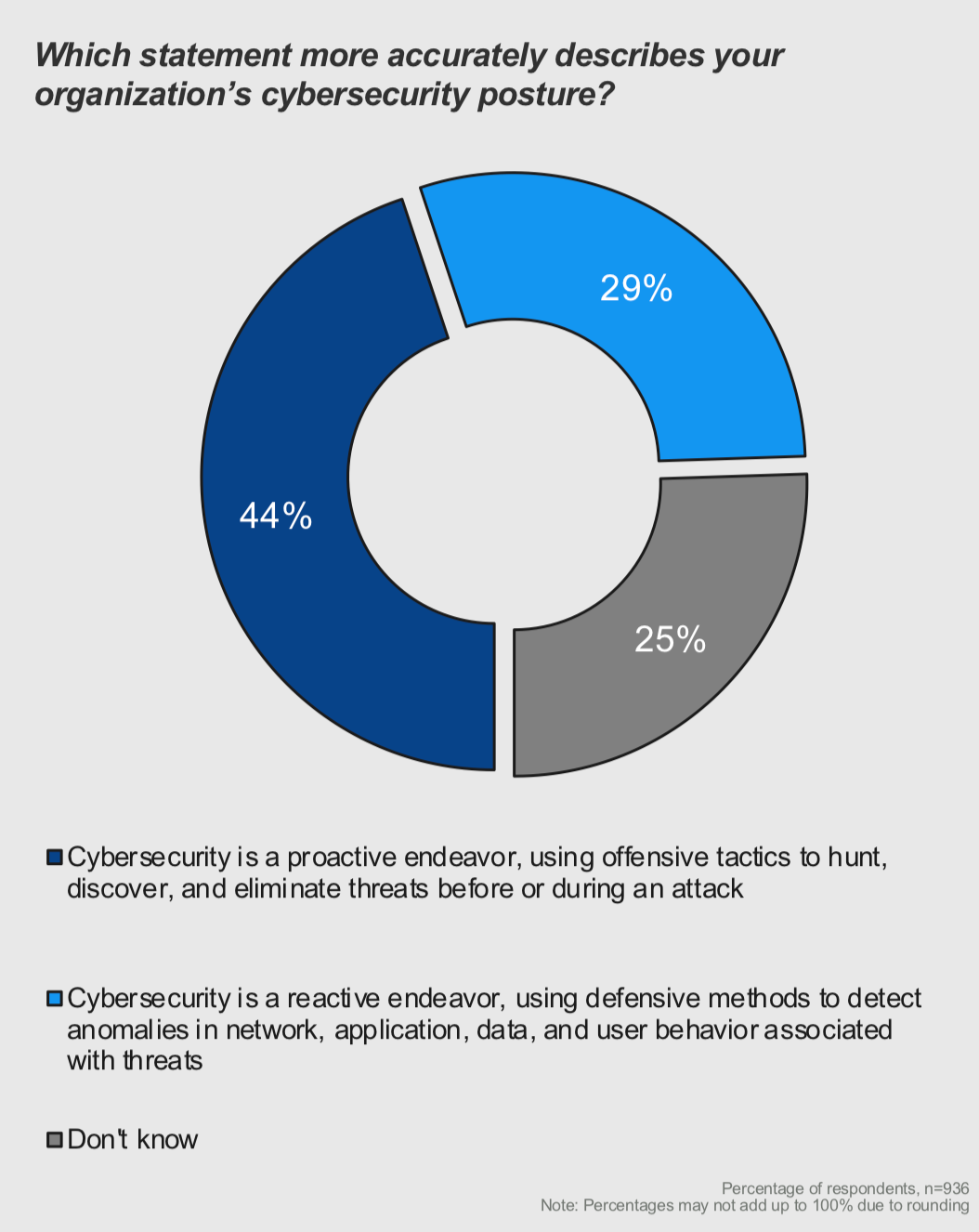
According to an Elastic-sponsored study of threat hunting capabilities within the federal government, 44% of US federal workers surveyed said their agencies engaged in proactive threat hunting cybersecurity tactics. About 29% said their organization sustained a reactive security position, and 25% said they did not know what cybersecurity posture was kept at the federal agency where they were employed.
The survey, at its core, exposes some of the main cybersecurity challenges facing the federal agencies today — challenges such as a massive gap in intrusion awareness and incident response times.
Consider, if you will, that one third of the federal employees responding to the survey said their agencies could detect an active attack on the network within hours. Nine percent said it took days and 5% said weeks. Yet half of the respondents did not know how long it took their organization to detect an active attacker to the network despite having familiarity with their agency’s cybersecurity programs.
In addition, 61% of those responding to the Elastic survey, Threat Hunting in the Federal Government, said they lacked awareness into the types of tools needed to perform threat hunting to prevent and stop cyberattacks.
Successful threat hunting
To address the challenges our study highlights, organizations must shift their mindset from a reactive defense posture to an aggressive offense — one that is always on the hunt for threats, and one that assumes breaches are inevitable.
Having said that, another take away from the survey is that, even though technology such as the Elastic Stack can aid threat hunting operations, agencies need to better understand that threat hunting success hinges on finding and equipping skilled specialists to track adversaries proactively to prevent or contain damage.
Our products and solutions are already helping a myriad of federal agencies on that front with real-time search and analytics at unprecedented speed and scale.
For example, Oak Ridge National Laboratory is harnessing the Elastic Stack in its mission to safeguard the digital information generated by the fastest supercomputer in the world. The US Army Futures Command is enriching, correlating, and rapidly indexing data for more effective insider threat detection with the Elastic Stack. Hill Air Force Base is powering compliance monitoring and securing a geo-dispersed data center using Elastic Cloud Enterprise.
A human problem with a human solution
Overall, the survey highlights that successful threat hunting demands substantially larger visibility into network data, threat intelligence, and systems than what the respondents indicated was currently the case. What’s more, even among those acknowledging threat hunting as a practice in their agency, an alarming number are unsure how long it takes to detect an attacker on the network or what tools are required to access the necessary data for launching threat hunts in the first place.
At the end of the day, cybersecurity is a very human problem and requires trained specialists to root out adversaries who understand how to exploit gaps in intrusion-detection and alert systems. Combining that human intelligence with the best-automated detection and search tools is necessary to root out and stay one step ahead of adversaries — whether or not there’s been a security breach.
Methodology
We sponsored this survey, conducted by the Government Business Council, to bring to light a high-level and broad picture of the security preparedness levels of the federal agencies.
This Government Business Council survey was underwritten by Elastic. It was based on responses from 200 federal employees representing 32 agencies and who were familiar with their agency’s cybersecurity efforts. More than half of the respondents, who were program managers, technical specialists, and administrative officers, said they held the status of at least GS/GM-13, the rank for high-level technical specialists.
George Young is area vice president for public sector at Elastic.