Léargas Security chooses Elastic, replaces Splunk to battle COVID-19 fraud
Léargas Security (Léargas is Gaelic for “insight”) provides clients with actionable insights into anomalous or abstract behaviors through the correlation of data gathered from converged security controls: cyber and physical.
Our company carries the concept of actionable, converged data even further with natural language processing and correlation of dark web, social media, TOR, chan, and additional sources in near real time to expose indicators of compromise and threats against customers and partner organizations.
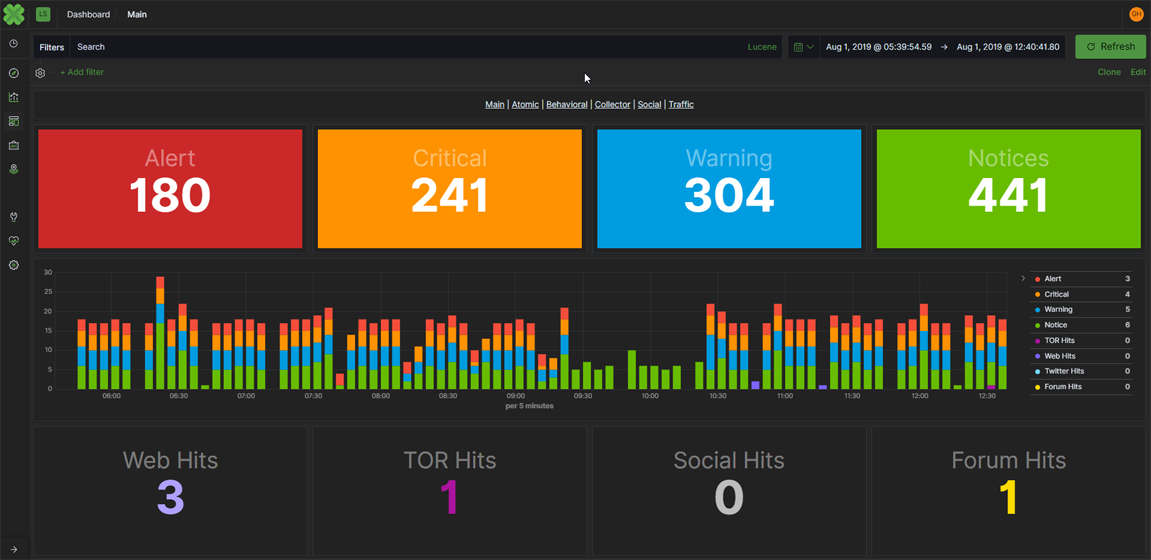
The Léargas platform, built on the open source Elastic Stack, helps reduce the high cost of entry that has traditionally prevented many small- and mid-sized companies from gaining effective visibility into their environments. Behavioral analytics for network security monitoring and intrusion detection services proves invaluable for these companies. Léargas makes this accessible.
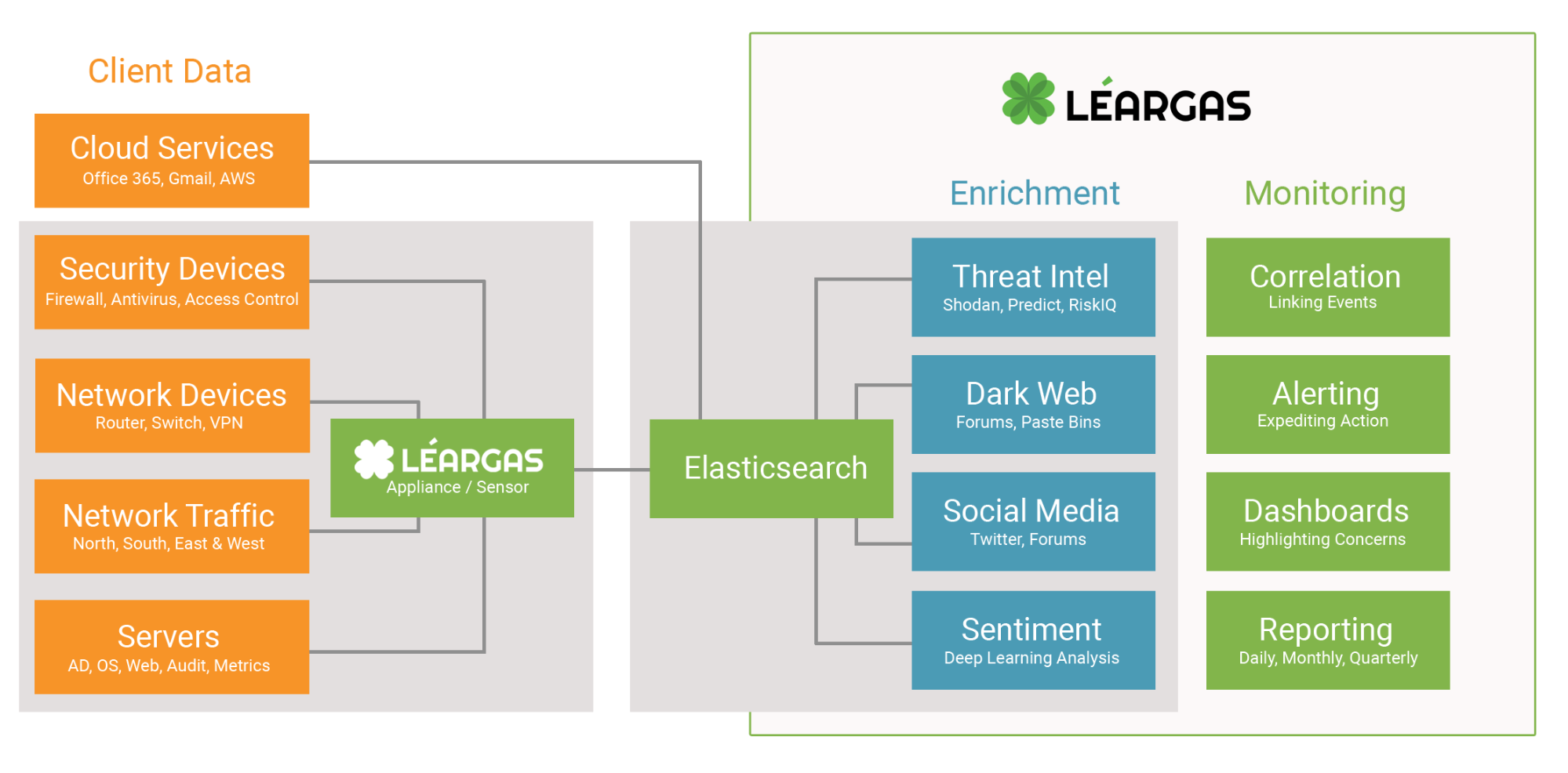
Initially, we created Léargas with the purpose of filling a gap in the converged security space: multi-contextual, multi-dimensional network forensics, enriched with leaked data, physical security control logs, and breach artifacts. As real-world usage scaled beyond initially scoped use cases, it became apparent that our customers needed to develop new capabilities into the platform, including the ability to identify people that may pose a physical threat. We satisfied this need by harvesting data and performing sentiment analysis and behavioral analytics.
Battling COVID-19 cybercriminals
In security, we're always faced with new challenges, which is why the flexibility of our security platform is so critical. The latest challenge is the online threats we’ve seen surrounding COVID-19.
Cybercriminals are evolving rapidly and leveraging real-world events to deceive victims and steal their money. Through the collection and aggregation of data in the Elastic Stack, we are not only observing attacks targeting our users, but also threats originating from the cloud. Often, these attacks are occurring through credential reuse against online services, such as Office365.
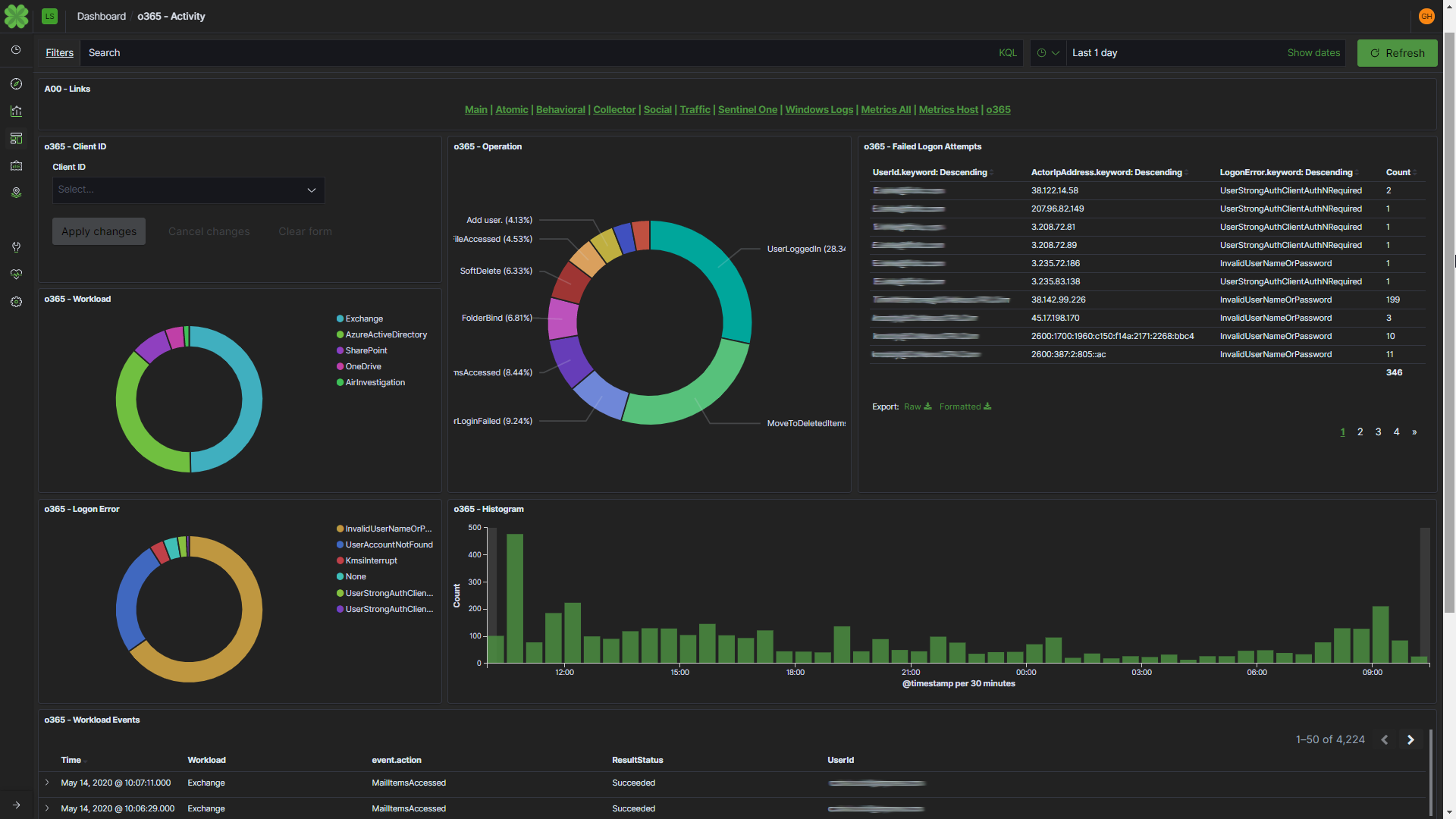
As we draw correlations around the data collected through Elastic and visualized in Kibana, we have been able to see the use of breached accounts from independent organizations as well as well-known platforms leveraged in new COVID-19-related phishing attacks. As we extract the domain names and email addresses used to deliver phishing emails, we can correlate and visualize that data to "follow the sun" of new and revived attacks.
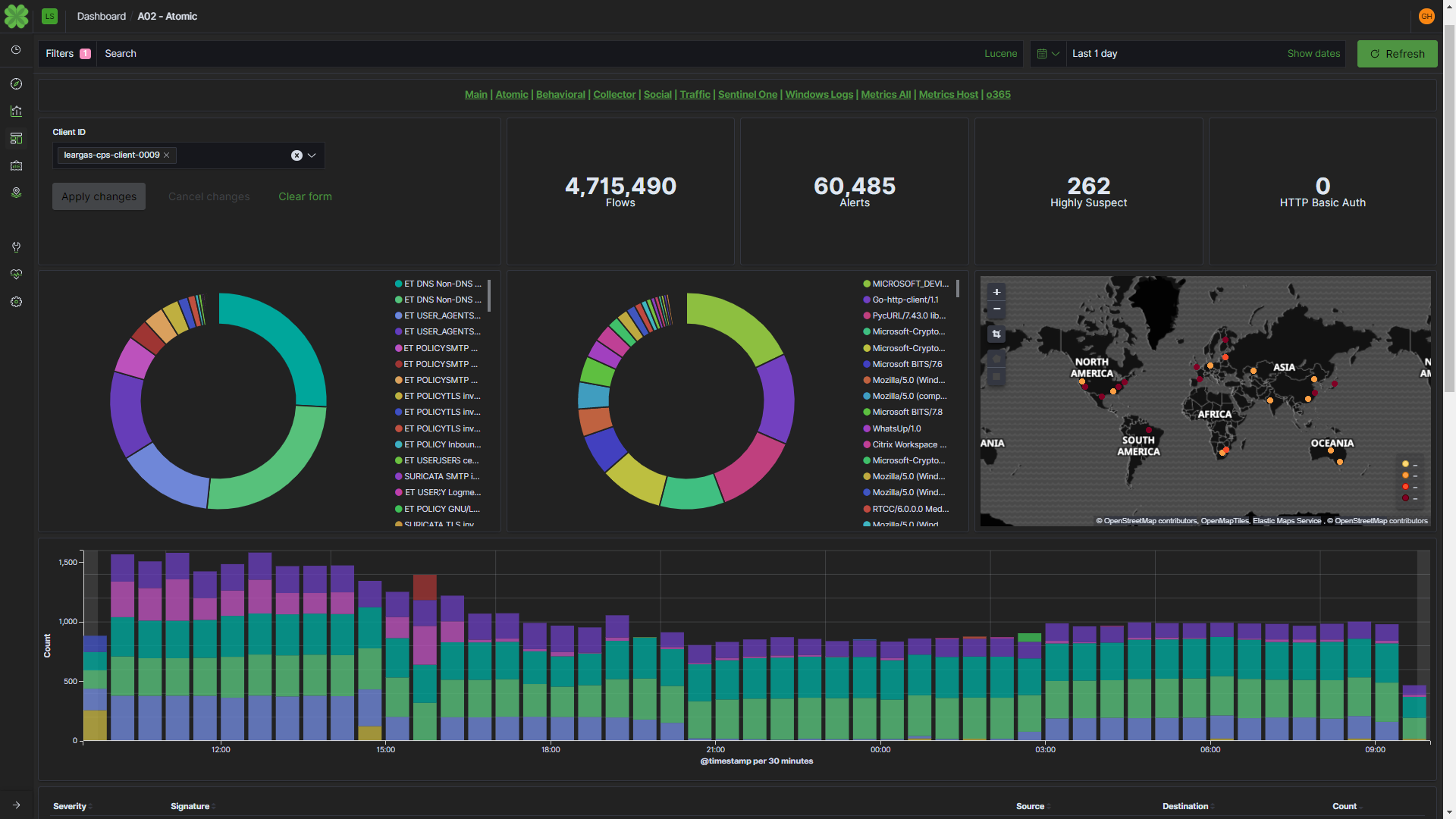
With the ability to continually monitor and react to multi-contextual and multi-dimensional attacks, we can protect every endpoint for our customers. With Beats, Elastic has enabled us to more quickly normalize and correlate data from raw network traffic, audit logs, syslog, and endpoint data without worrying about the volume of endpoint data or speed of search required to perform such correlations at scale.
Fighting COVID-19 required dropping Splunk
We immediately knew that our decision to leverage Elastic as the centerpiece of our search capabilities was the right one. Though we’d originally built the first versions of the platform using Splunk, we found that we simply couldn’t keep up with the licensing costs, as the amount of data we were making decisions around was significant and increasing. The amount of data now seamlessly processed through Elastic is well over 6TB of log data a day — and that’s in COVID-19 data alone.
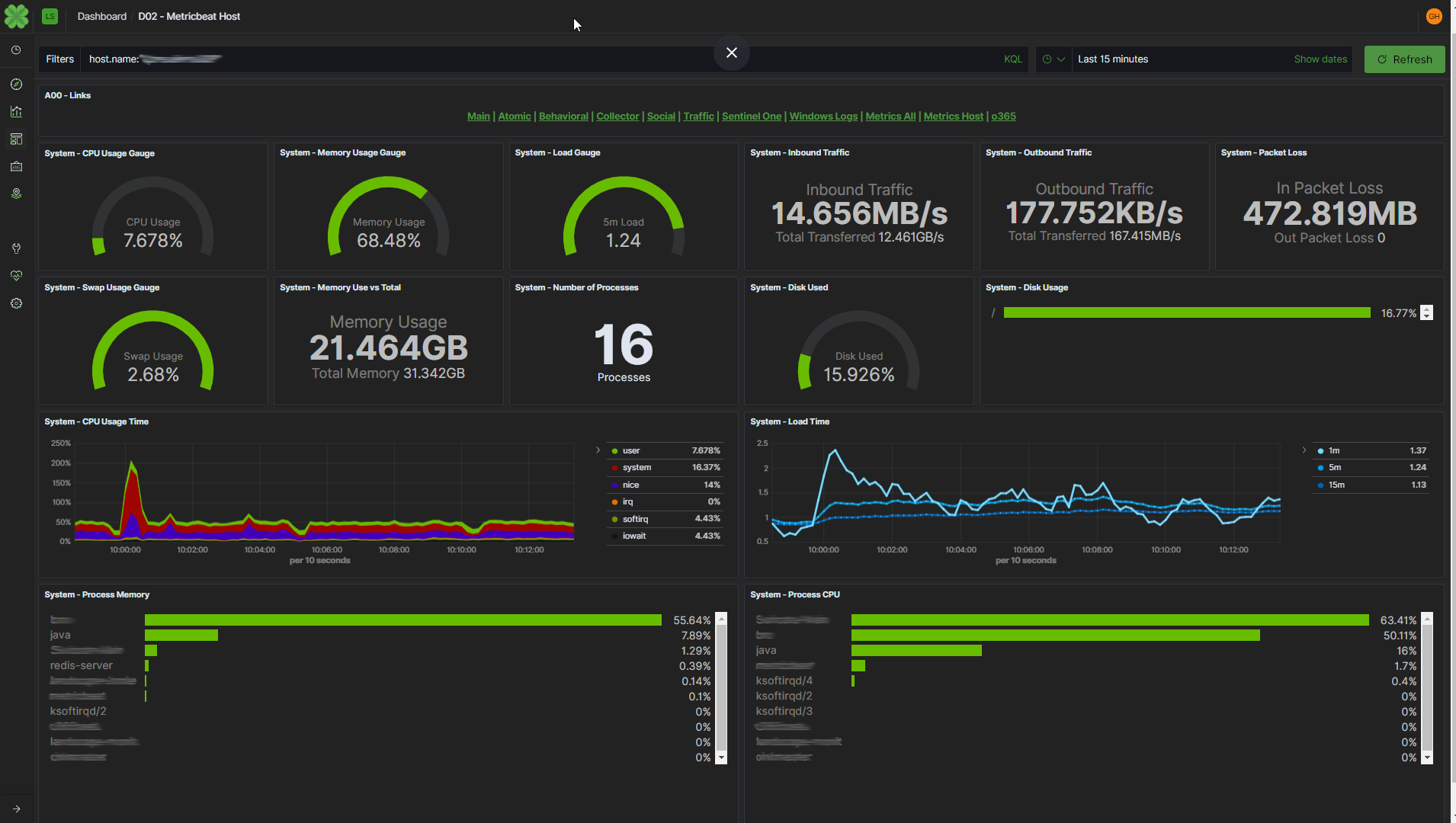
After switching to Elastic, we found significant performance improvements when ingesting and normalizing hundreds of thousands of messages per day from varying sources, including TOR, PasteBin, Chan sites, IRC chat logs, Twitter, and many more.
With Splunk, we found ourselves limited by the number of resources required to properly manage the master node and add additional forwarders, peer nodes, and search heads at the same time. As we needed to increase data ingestion and the ability for analysts to search and correlate data, Splunk’s costs with licensing and hardware resources were inhibiting our growth.
Knowing we could ingest any and all meaningful data with Elastic, the team delved into the online personas, social media accounts, news stories, manifestos, and any other available information about COVID-19 events that could help spot trends in the attacks. As we processed this unstructured data, we realized just how critical this context was in combating COVID-19 threats. This data was used to compile a list of keywords and phrases commonly found to be used by the cybercriminals to focus Léargas’ search and processing cycles. Examples of those initial keywords were coronavirus, corona, COVID, COVID-19, vaccine, and chloroquine. As time went on, we’ve extended the threat data collected to include multi-stage behavioral detections, and malicious file samples extracted from Zeek and analyzed in Elastic.
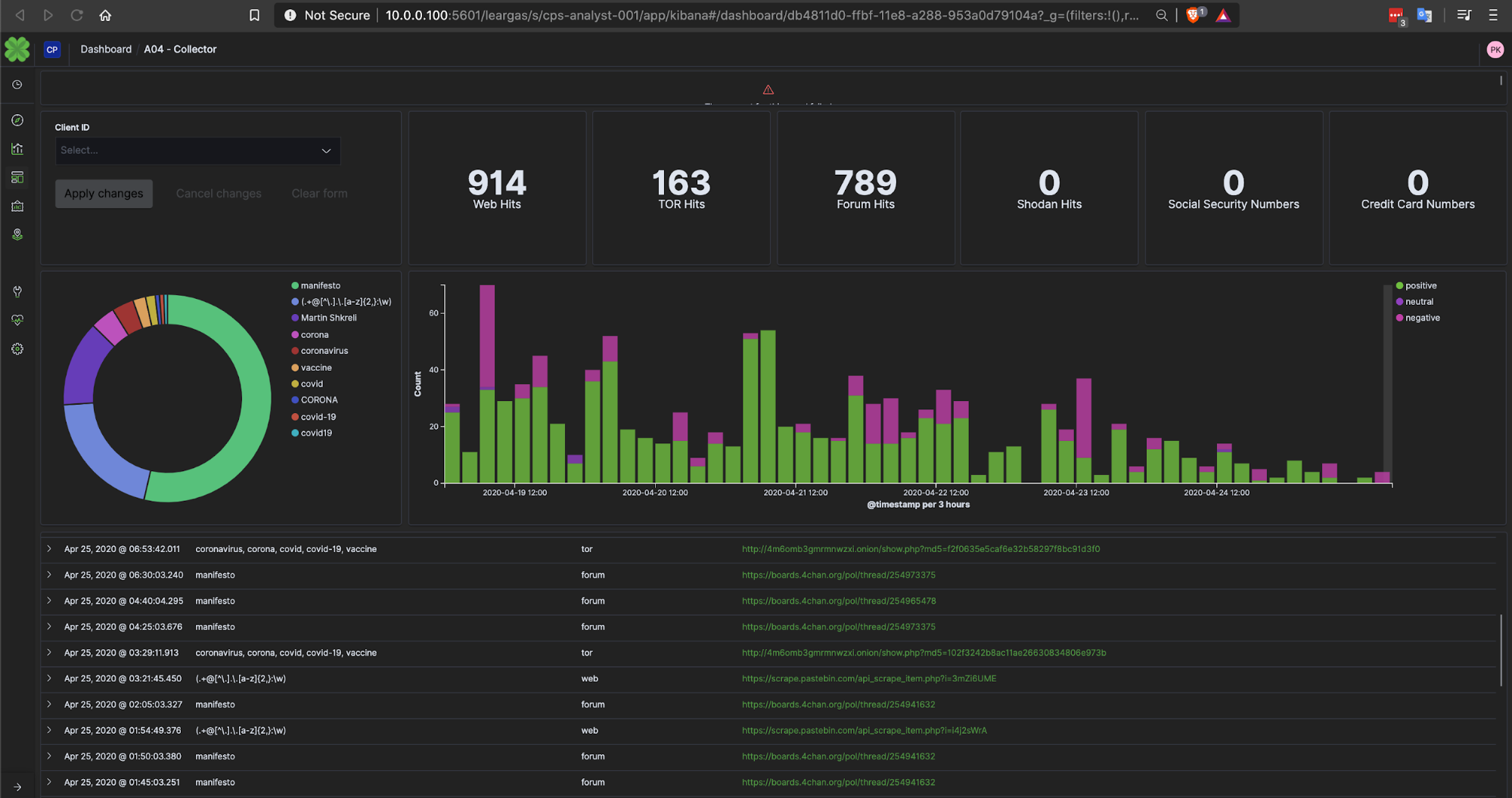
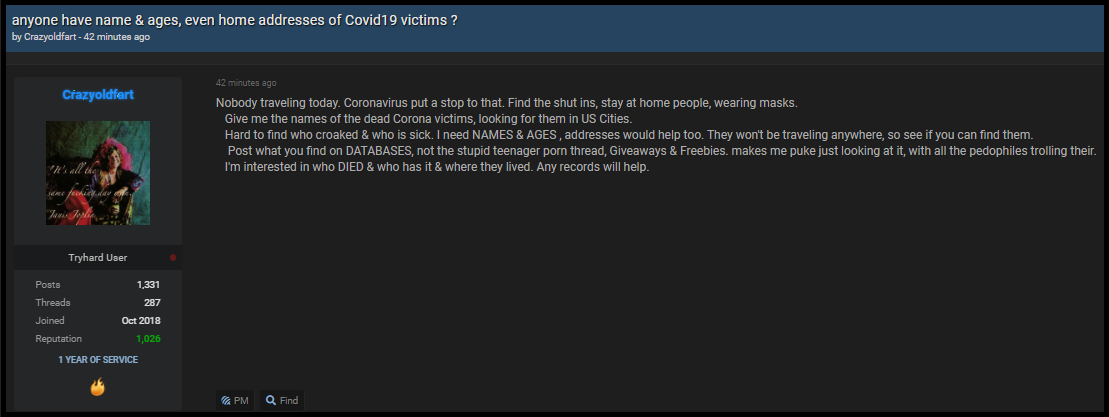
One example we were able to observe and report is shown below, where a cybercriminal is seeking assistance in locating those individuals who died from the coronavirus. The goal of the criminals’ campaign was mass identity theft.
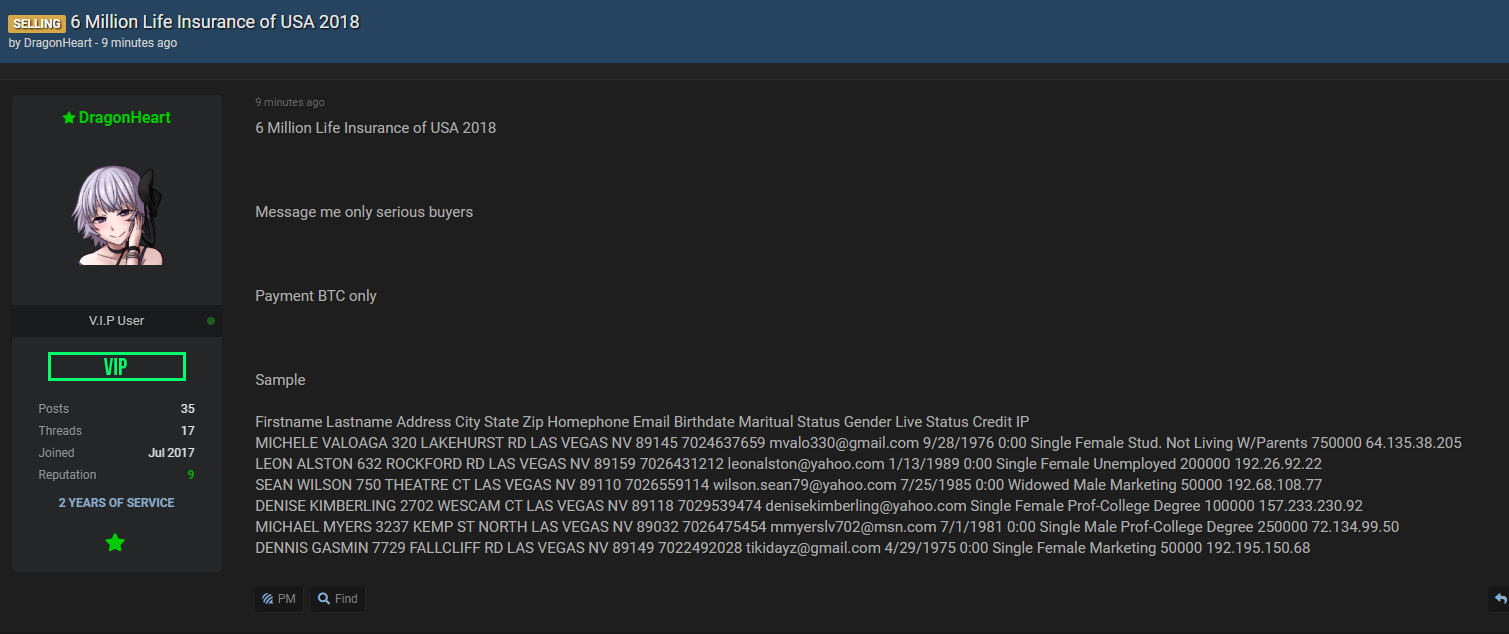
Another example of recent attacks includes COVID-19-related phishing of healthcare and pharmaceutical companies. As users click on links offering important information about COVID-19 vaccines and treatments, credential-grabbing malware and ransomware (such as MAZE) is being deployed.
Stopping phishing with Elastic
With Elastic’s technology, Léargas has been used to stop phishing attacks by correlating the number of emails originating from a single source — along with a known-file hash — and domain name with a TTL value of fewer than 5 minutes (common with Command & Control botnets) delivered to multiple recipients. That information can then be exported into a STIX-formatted file for cybersecurity situational awareness, real-time network defense, and sophisticated threat analysis.
As we continue our journey with Elastic, the team at Léargas Security is hopeful that our efforts can prevent even more attacks (potentially weeks in advance) and that any successes will inspire others to devote resources to ambitious public service projects.
We're proud to say that Léargas Security is providing public threat feeds for the Zeek IDS platform and a Zeek Threat Feed Parser to help organizations ramp up their own defenses.
Those resources can be found at the following links:
- https://github.com/LeargasSecurity/COVID-THREAT-FEED-PUBLIC-LEARGAS
- https://github.com/LeargasSecurity/Zeek-Feed-Parser
We appreciate Elastic’s commitment to providing ongoing support for the many research and threat response teams around the globe. Our choice to drop Splunk and invest in Elasticsearch and the family of Beats was a critical move in getting ahead of COVID-19 fraudsters.
.jpg)
Patrick Kelley, the founder of Léargas Security of Canton, Georgia, is an Information Security veteran with over 20 years of experience.