Implementing phishing-resistant MFA: Our data-driven approach

Multifactor authentication (MFA) is widely recognized as an important control to make our accounts more secure by providing protection beyond just passwords. When MFA is enabled, we tend to think our accounts are safe from unauthorized access — but what if we said it's time to rethink this belief?
The next generation of multifactor security: Phishing-resistant MFA
Traditional multifactor authentication methods typically rely on a combination of factors: something the user knows (such as a password), something they have (like a code sent via SMS), or something they are (such as a fingerprint). Phishing-resistant MFA goes far beyond the capabilities of traditional MFA. It is a highly secure authentication method that uses multiple layers of protection to ensure enhanced security. It is immune to phishing attacks and responds only to valid requests from known and trusted parties. This approach involves a strong, trusted relationship through cryptographic registration. This type of MFA uses authentication methods such as fingerprint, face recognition, a PIN, or hardware security keys.
As a distributed, remote-first organization with a workforce spanning thousands of employees worldwide, we acknowledged the profound implications of deploying Phishing-resistant MFA, changing how our employees come to work. But with phishing attacks becoming more complex, we also knew how critical it was to make the switch. Below, we’ll share the steps we took to deploy Phishing-resistant MFA for Elastic® employees and the outcome we achieved.
Why did we take action?
Phishing attacks have grown remarkably sophisticated. Cyber attackers no longer need to spoof websites to engage in credential phishing; now, they can steal user sessions while showing the user a perfectly legitimate site. It all starts with phishing campaigns where attackers trick users into navigating to a proxy site. When users enter their credentials, the proxy site acts as an intermediary, passing the requests and responses between the user and the real website. Things will proceed normally: the legitimate website prompts for MFA verification, the user will enter the additional details as normal, then the website responds with a session cookie, and the user is logged in.
To the user, this all looks normal, but the malicious actor has access to the full session, including the session cookie sent by the legitimate site after the MFA was completed. Once an account is compromised, the attacker can attempt to move laterally, evade detection, and pivot throughout the environment to elevate privileges.
Because Elastic’s employee base is distributed by design and utilizes many SaaS applications, MFA is the primary layer of protection for many Elastic assets. We removed the option to authenticate with SMS some time ago. Still, up until recently we relied heavily on push notifications, mobile authenticators, and time-based one-time passwords (TOTP), with relatively low adoption of FIDO2 authentication factors resistant to these modern, proxy-based attacks.
Click rates for phishing are estimated to increase year over year depending on the industry and the source of the research (more information on Statista). As a member of our InfoSec team, we know that Elastic has a very engaged and security-conscious employee base, but we are also realistic. When a campaign can target hundreds or thousands of users at a time or make use of highly targeted lures, somebody will always click.
We also believe that if our security model fails because somebody clicked a link, that’s on us as a security team.
What did we do?
Between security assessments, industry suggestions, and the lowering barrier of entry for cybercriminals, the Information Security (InfoSec) team decided to adapt our approach to Phishing-resistant MFA urgently. We decided to move to phishing-resistant MFA as a necessary next step to protect our end users from sophisticated phishing attempts. For a long time, our end users bore the responsibility of protecting their accounts and, with proxy-based attackers in the middle, the only way for a user to identify an attempt to steal their session in this way was to notice a change in the URL. With phishing-resistant MFA, our goal was to shift that dynamic, lifting the burden off our end users and placing it on robust authentication protocols like Fast Identity Online (FIDO).
FIDO authentication operates on the premise of employing a distinct set of keys for each user and website. Upon user registration, a unique key pair is generated, consisting of a public key known to the site and a private key securely stored on the user's device. During authentication, the site issues a challenge, and the user's device verifies if the site's identity and domain align with the initial registration. If there's a mismatch, authentication fails, acting as a reliable safeguard against these attacks.
How did we implement Phishing-resistant MFA?
The scope of this effort was extensive — covering all our employees and contractors — with a unique set of challenges. Despite the challenges, we successfully implemented Phishing-resistant MFA across our entire organization within three months. A major factor in this achievement was a dedicated emphasis on data.
We firmly believe that data plays a crucial role in addressing security challenges. Our InfoSec program is powered by Elastic. Internally, we’re customer zero for all of our solutions, which enable us to monitor assets, identities, vulnerability data, and everything around Elastic. All of this information is stored in a centralized location using the power of cross-cluster search.
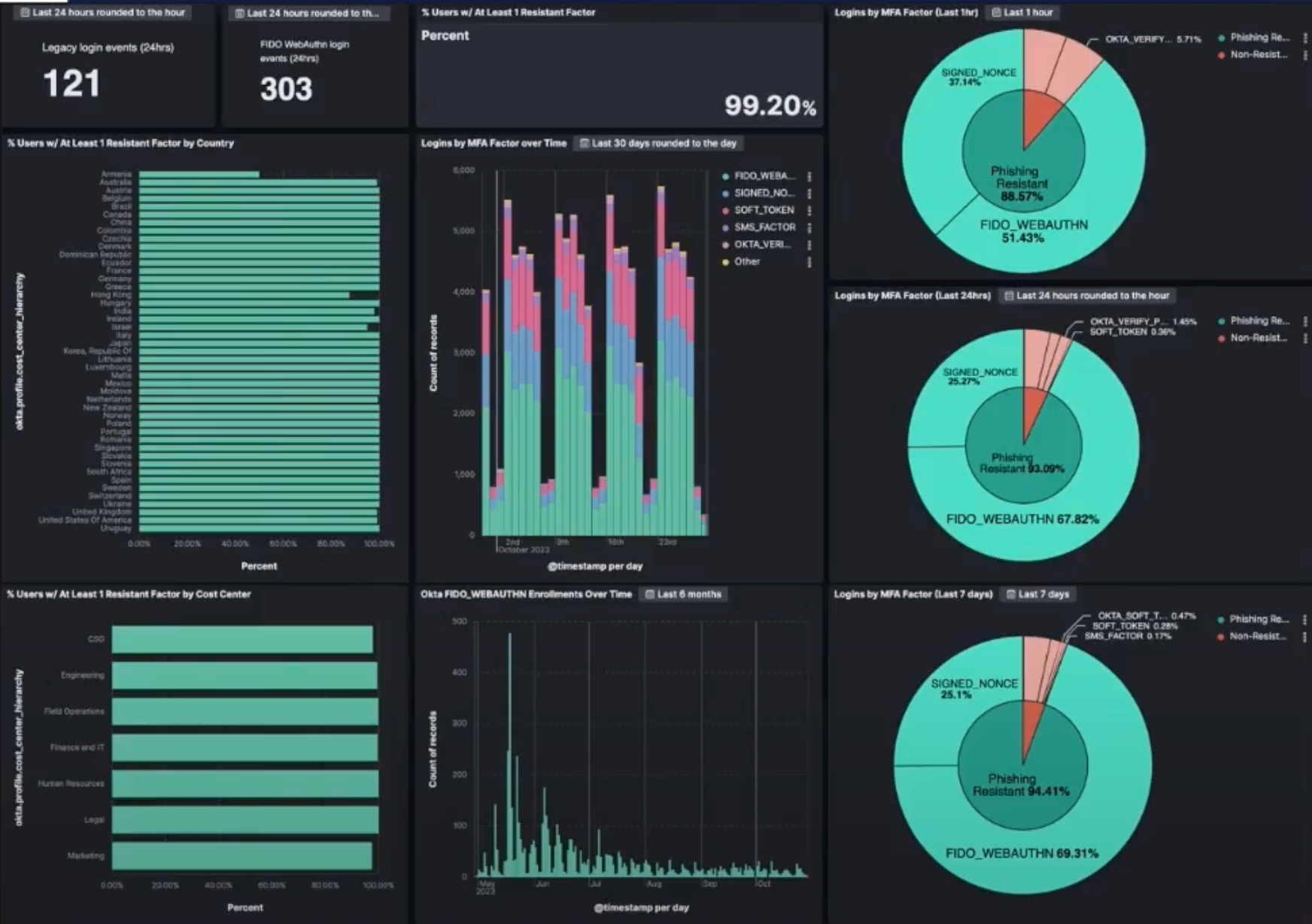
This foundation allowed us to extract meaningful, real-time insights that were critical to achieving our objective. With a single dashboard, we were able to answer pivotal questions, such as the number of users registered with Phishing-resistant MFA, their respective departments, and the countries they were located in. This streamlined communication of insights with senior leadership regarding progress. It allowed us to alert department managers in case of potential delays and facilitated direct communication with individual end-users for reminders and support.
To enhance visibility, we incorporated charts capturing time-series events. These visualizations provide real-time insights into adoption rates, illustrating the number of users actively logging in with FIDO-based authentication factors over the prior hour, 24 hours, and 7 days.
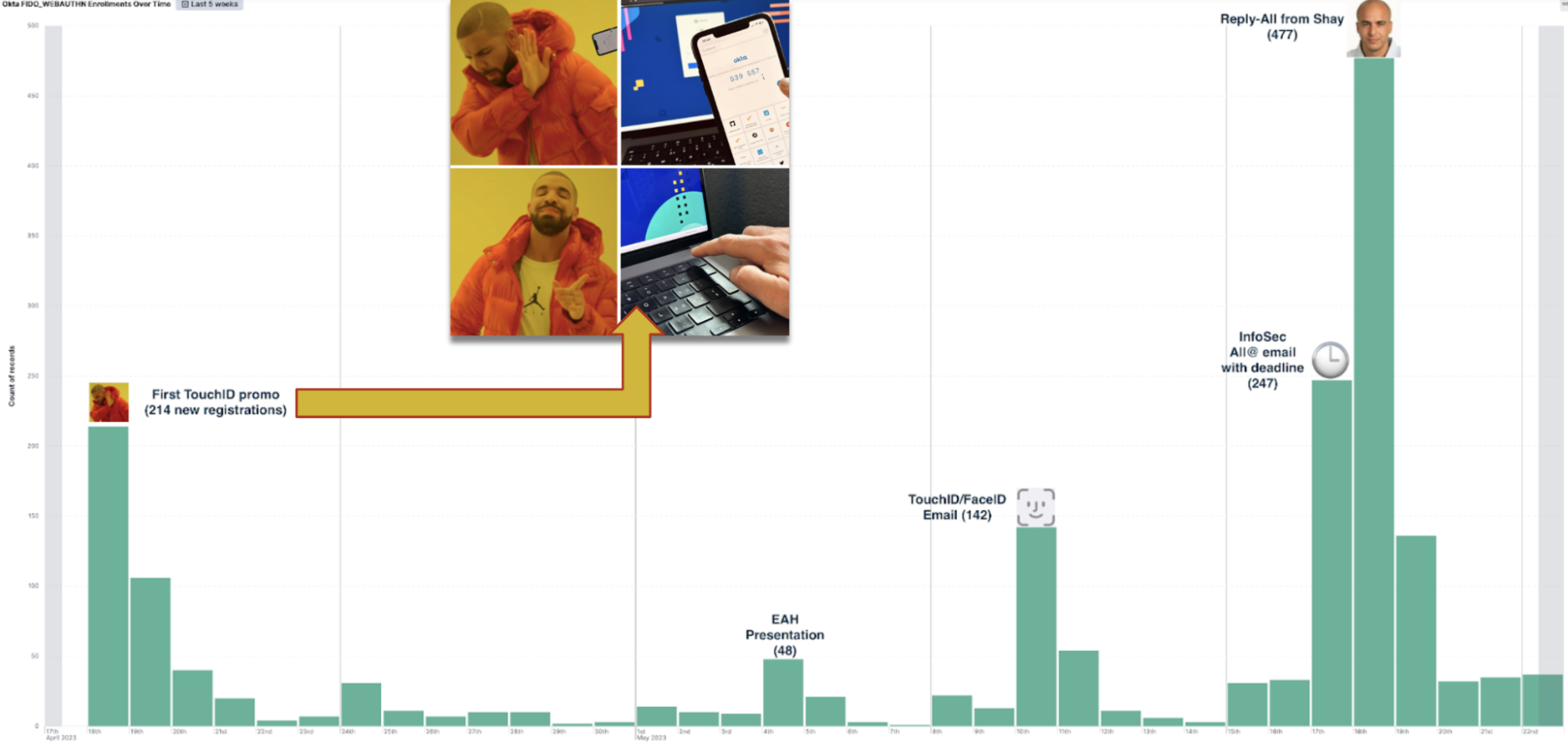
The most exciting part for us was to witness the real-time impact of our communications. We initiated our project by promoting TouchID as the primary authenticator for Phishing-resistant MFA, accompanied by a classic Drake meme. Within just one hour, we observed a significant uptick in engagement from our end users — everyone was loving it. The pivotal revelation for us was recognizing the effectiveness of various communication methods — a reply-to-all email from Elastic's CTO proved to be the most influential in prompting user action. When implementing organization wide changes, we saw the most success with having support from the executive or senior leadership for a comprehensive and successful implementation.
Automation, complemented by valuable data insights, played a pivotal role in propelling our journey toward completion. As these significant changes took place within the organization, it is important to recognize the impact on the InfoSec team, particularly in terms of time constraints. This involves acknowledging the additional time and resources required for monitoring, responding to alerts, and making decisions regarding legitimate Phishing-resistant MFA changes versus potential malicious attempts.
Leveraging the existing data insights, we enhanced our alerts by incorporating additional user context: system owner, host, operating system, username, job title, and alert type. Through the assistance of automation, we efficiently distributed these enriched alerts directly to end users or system owners. They were prompted to confirm awareness of the Phishing-resistant MFA change and decide whether any action or support was needed from the InfoSec team. This approach empowered users to provide context and make informed decisions, allowing them to determine if the situation warranted escalation to the InfoSec team for further investigation or support.
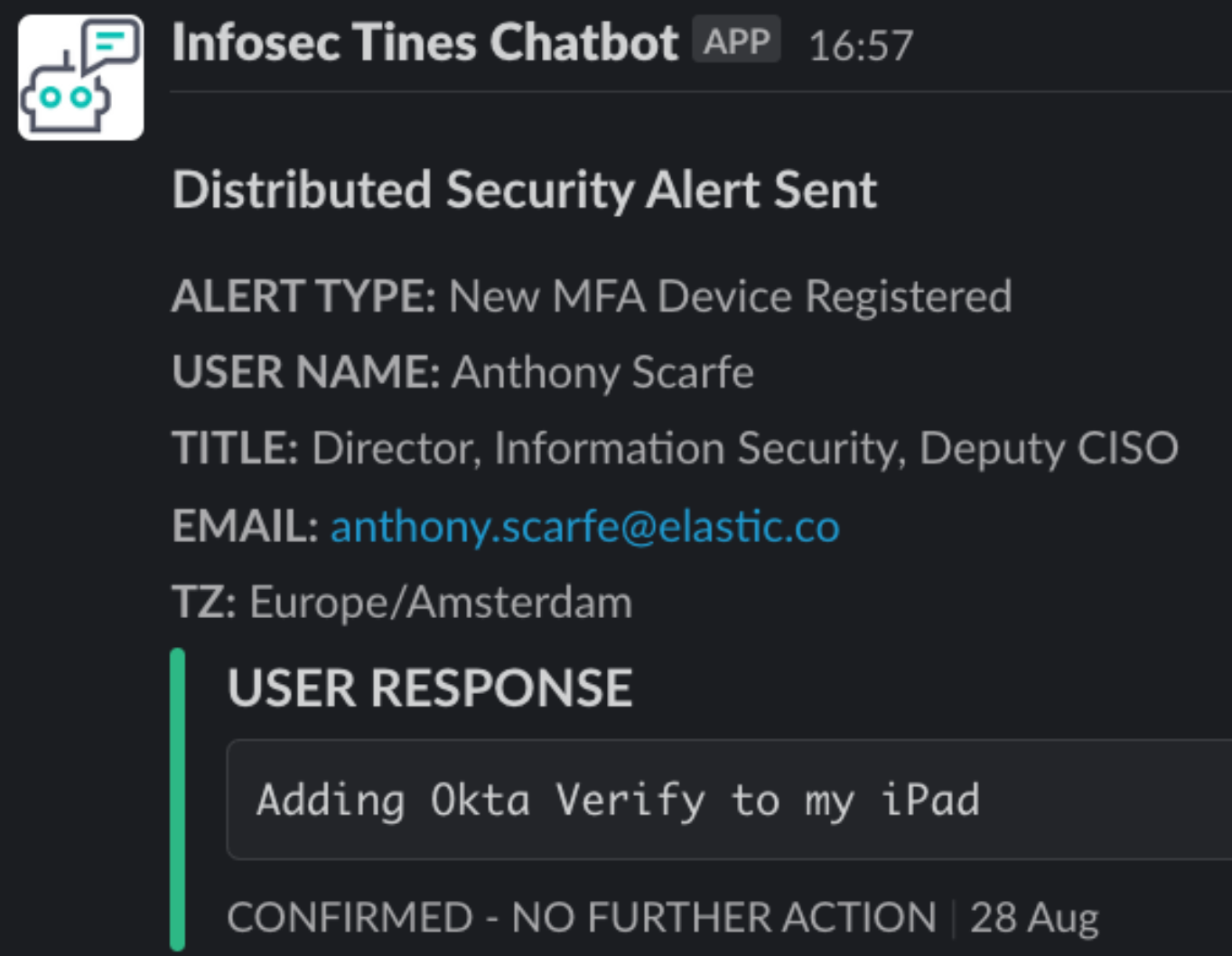
Distributed alerting represents an exciting development for us. Implementing automation and insights has been amazing in saving numerous hours for the InfoSec team that would otherwise have been spent on individual follow-ups. This automation has, in turn, empowered the InfoSec team to concentrate on addressing genuine issues and concerns more effectively.
Upon establishing data insights, improving communication, and efficiently distributing alerts, the need to offer substantial support for our end users became apparent. Our focus extended beyond simple assistance; we actively engaged in educating end users about the significance of Phishing-resistant MFA. Timely support played a critical role in facilitating a prompt adaptation to the implemented changes. We conducted office hours with quick Zoom calls, compiled a list of FAQs to be made available to end users, and ensured a proactive approach to addressing concerns.
Despite the clarity of instructions, end users consistently sought reassurance from the InfoSec team. To provide the needed support, we emphasized these core principles, collectively known as “LAURA” within the Elastic InfoSec team:
Listen to your end user: Actively pay attention to their concerns and feedback.
Acknowledge the situation: Recognize the security challenges and user needs at hand.
Understand how they are feeling: Empathize with the end user's perspective and emotions.
Relate to demonstrate your understanding: Show that you comprehend their point of view and the issues they face.
Act to show willingness to help: Demonstrate proactive measures, indicating a genuine commitment to assisting end users.
Adopting a user-centric approach allowed us to understand the end user concerns and challenges and address them proactively.
What did we achieve?
Multifactor authentication alone is no longer sufficient to protect user accounts against threats. Our team firmly believes that a data-driven, real-time approach that is scalable and user-centered can effectively address these challenges. By harnessing the power of Elastic for automation and keeping data at the forefront, we were able to introduce phishing-resistant multifactor authentication across our entire organization in just three months. With buy-in from the executive team, this approach dramatically reduced our exposure to the ever-changing threat landscape. We hope that our success story will inspire you to embrace these innovative solutions to achieve your security goals.
Learn how our customers have used Elastic Security to protect their businesses against cyber threats.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.