Finally, a SIEM that gets cloud detection and response
Delivering more cloud detection and response features directly into our SIEM
.jpg)
Elastic eliminates the need for a separate cloud detection and response (CDR) tool by being the first to integrate cloud detection and response capabilities directly into an AI-driven security analytics solution — the future of SIEM. Legacy solutions have complex workflows and lack cloud-specific context, making them inadequate for the scale and complexity of cloud environments. Standalone CDR tools often generate vast amounts of fragmented data that are difficult to analyze in real time and fail to correlate threats across diverse data sources. CDR is key to actively finding and addressing cloud-based threats quickly. Elastic Security ensures seamless, real-time incident response, empowering organizations to efficiently manage and secure their cloud workloads.
Over the past two years, we’ve integrated cloud security and CDR capabilities directly into the SIEM, enhancing how modern organizations detect and respond to threats more effectively. In Elastic Security 8.12, we launched cloud security posture management (CSPM) capabilities for all cloud security providers (CSPs) — AWS, Microsoft Azure, and Google Cloud Platform (GCP) — laying the foundation for streamlined cloud security posture. With Elastic Security 8.16, we’ve expanded these capabilities to meet the growing customer demands for advanced analytics and cloud security across diverse cloud assets, including third-party, cloud-native application protection platforms (CNAPP), vulnerability management tools, and open source Cloud Native Computing Foundation (CNCF) tools.
Combining core CDR capabilities into a SIEM
Today, we are delivering new features like agentless ingestion, cloud asset inventory, extended protections, and graph view that enables out-of-the-box correlation and context enrichment using customers’ existing data. All of these features are powered by the Elastic Search AI Platform that provides the visibility, context, and security needed for cloud, hybrid, and on-prem environments — all from within a single platform.
“Increasingly dynamic cloud environments are presenting visibility challenges for security with 44% reporting that threat detection and response is more difficult to conduct in cloud environments," said Dave Gruber, principal security analyst at ESG. “SOC teams need to address this cloud visibility gap by collecting, processing, monitoring, and acting upon information from an assortment of cloud security telemetry sources spanning multiple hyperscale cloud providers. Elastic Security’s vendor-agnostic approach to CDR, with the ability to easily ingest and normalize cloud data out of the box, enables security teams to surface critical insights at the speed and scale of the cloud directly with their SIEM.”
“We combined CDR and AI-driven security analytics to reduce tool fragmentation and centralize data, empowering the security teams to protect their cloud environments effectively,” said Santosh Krishnan, general manager of Elastic solutions. “This comprehensive approach maximizes efficiency, lowers the total cost of ownership (TCO), and alleviates the burden on security teams. Ultimately, Elastic Security ensures organizations stay ahead of evolving threats while leveraging the full benefits of CDR.”
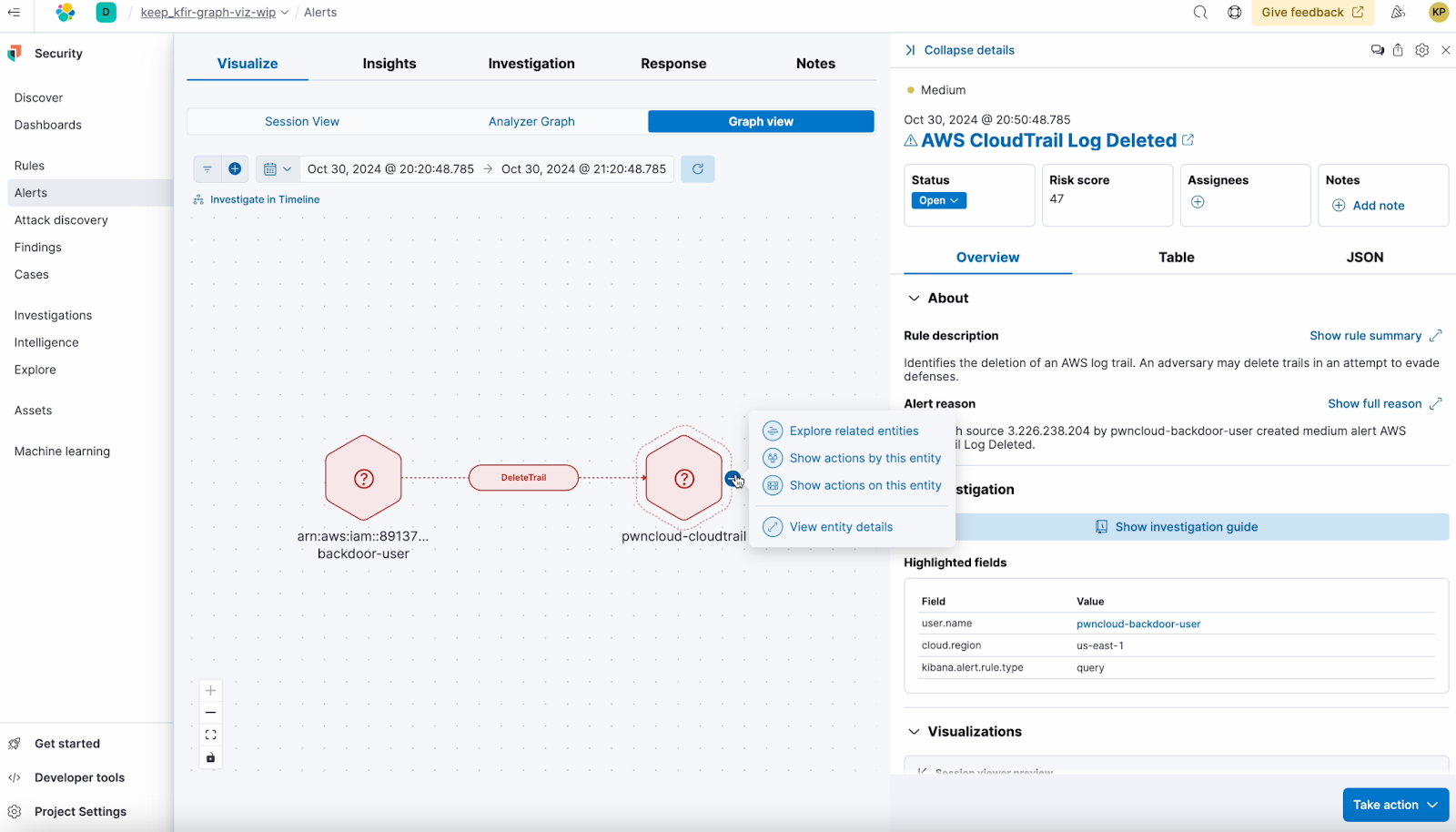
Elastic Security simplifies threat detection by empowering practitioners to uncover hidden insights and connect the dots through context-rich investigations, such as graph view. This visual approach enables analysts to easily identify relationships between entities, events, and actions from sources like cloud audit logs, flow logs, identity logs, and third-party cloud security context.
By visualizing this data, analysts can quickly detect patterns and pinpoint root causes without writing complex queries or manually piecing together data from multiple tabular views. Initially available in Elastic Cloud Serverless deployments for AWS CloudTrail, this capability will soon expand to other environments and data sources — further enhancing investigation efficiency and accelerating threat detection.
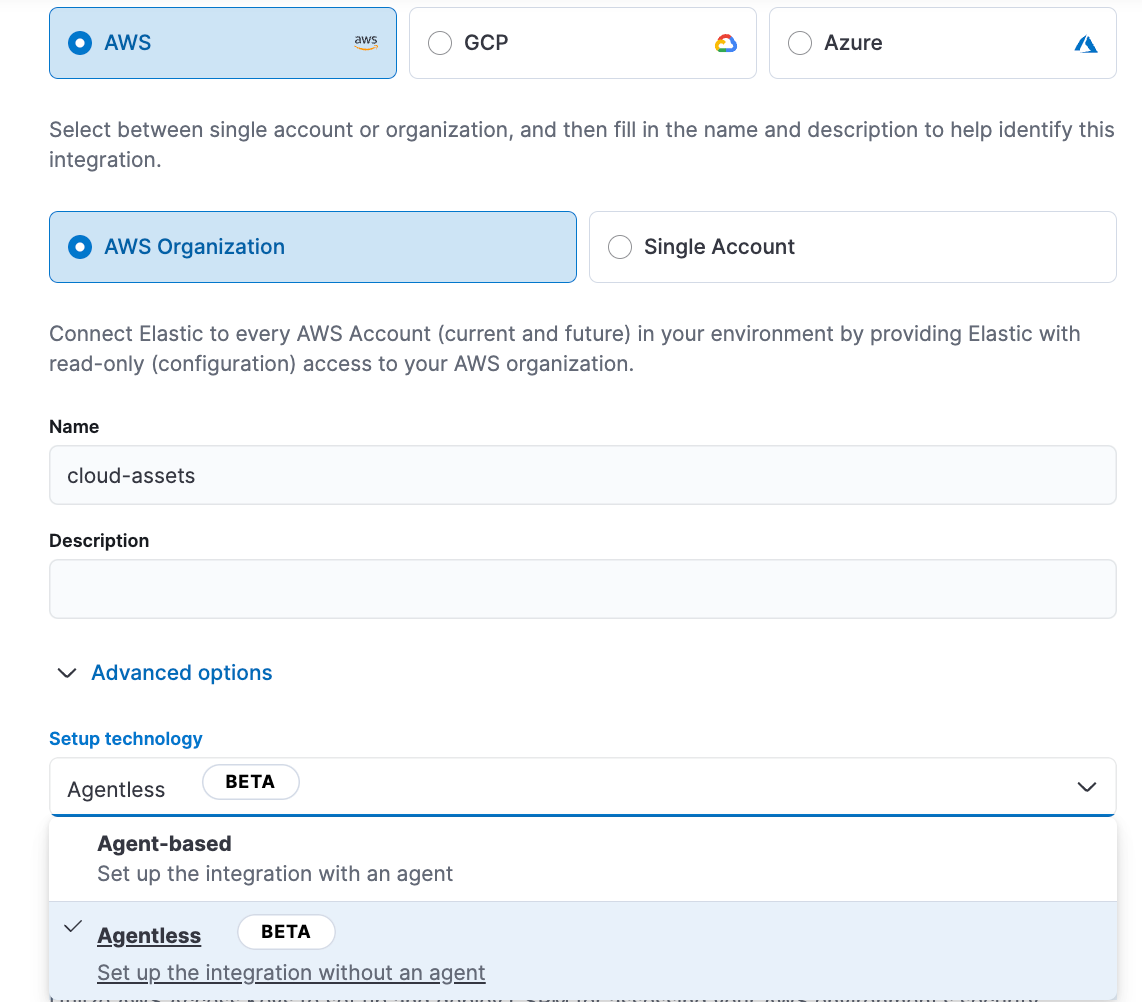
Elastic Security simplifies deployment with agentless data integration, enabling analysts and practitioners to start collecting cloud data in minutes without the need for installation on customer environments. This reduces operational overhead while providing a comprehensive view across multi-cloud environments, ensuring that security teams can keep pace with the rapid growth of cloud resources. Currently, Elastic supports agentless deployment for CSPM and the new asset discovery integration — now in public beta — with additional integration coming soon.
Elastic Security addresses the issue of tool fragmentation and lack of comprehensive context by integrating data from leading cloud security and open source CNCF tools like Wiz, Falco, and AWS Security Hub. The extended protection integrations bring together insights, such as vulnerabilities from Wiz, alerts from Falco, and posture findings from AWS Security Hub, alongside the affected entities. This comprehensive view enables practitioners to quickly assess the full risk context and prioritize their response effectively.
This data-centric approach offers vendor-agnostic classifications, rules, and workflows, streamlining investigations and boosting productivity.
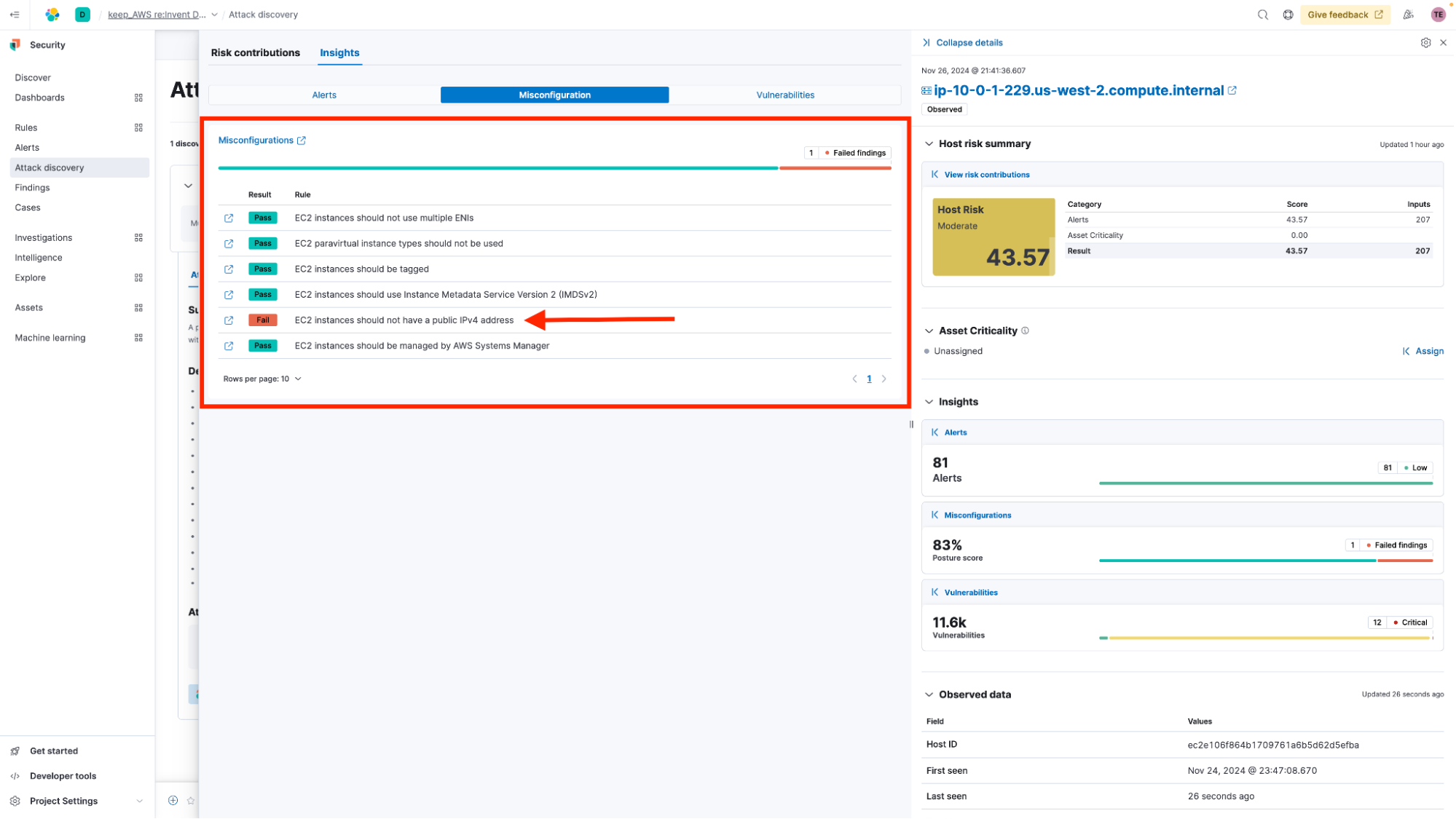
In this example, we can see a configuration finding indicating that this host has a public IPv4 address coming from AWS Security Hub, which Elastic has seamlessly integrated and normalized into the workflow.
By taking care of ingesting data from sources like AWS Security Hub, Wiz, and others, normalizing it, and surfacing it in the right place, Elastic ensures that — regardless of the source — this data is actionable. Analysts don’t need to jump between platforms or spend time deciphering raw data. Instead, they’re empowered to contextually investigate and respond to detected threats all within their existing workflow.
Building off foundational CDR capabilities
These enhancements build on Elastic Security’s robust foundation, which already includes over 200 prebuilt cloud detection rules and anomaly detection jobs, more than 100 cloud integrations, runtime security powered by eBPF, and automated response actions. Together, these features provide security teams with the tools they need to stay ahead of evolving threats and secure their cloud environments with confidence.
Try it out
To see this new technology in action, join us at AWS re:Invent booth #1132, or sign up for our webinar, Maximize your investment: Streamline Cloud Detection and Response with Elastic Security.
Existing Elastic Cloud customers can access many of these features directly from the Elastic Cloud console. Not taking advantage of Elastic on the cloud? Start a free trial.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.

