What’s new in Elastic Security 7.15: End threats at the endpoint…and beyond
Elastic Security 7.15 further arms the SOC to achieve extended detection and response (XDR).
Malicious behavior protection applies behavior analytics to prevent attack techniques often leveraged by named threats by performing dynamic, stateful correlation of on-host events, and then reacting instantly to disrupt attacks before they cause damage.
Memory threat protection now safeguards Windows hosts, stopping attacks designed to evade most other defenses.
To accelerate response and prevent damage and loss, 7.15 adds host isolation for cloud-native Linux systems, making the capability now available on every OS protected by Elastic Agent.
Let’s dive in.
End threats at the endpoint
Malicious behavior protection for Linux, Windows, and macOS
Malicious behavior protection, new in 7.15, buttresses existing malware and ransomware prevention with dynamic prevention of post-execution behavior. This new layer of prevention equips Elastic Agent to protect Linux, Windows, and macOS hosts from a broad range of attack techniques often leveraged by named threats. Prevention is achieved by pairing post-execution analytics with response actions tailored to stop the adversary at the initial stages of attack.
Each protection is mapped to the MITRE ATT&CK® framework, addressing attack techniques related to Initial Access, Execution, Persistence, and later tactics. The release protects against advanced attack techniques with prebuilt correlation rules for stopping methods such as:
- Credential theft via memory dump
- Phishing techniques
- Living off the land (LotL) techniques, which hijack built-in OS capabilities to conduct attacks while avoiding detection and other methods of defense evasion
- Advanced persistence techniques, which adversaries use to maintain a foothold across restarts, changed credentials, and other interruptions
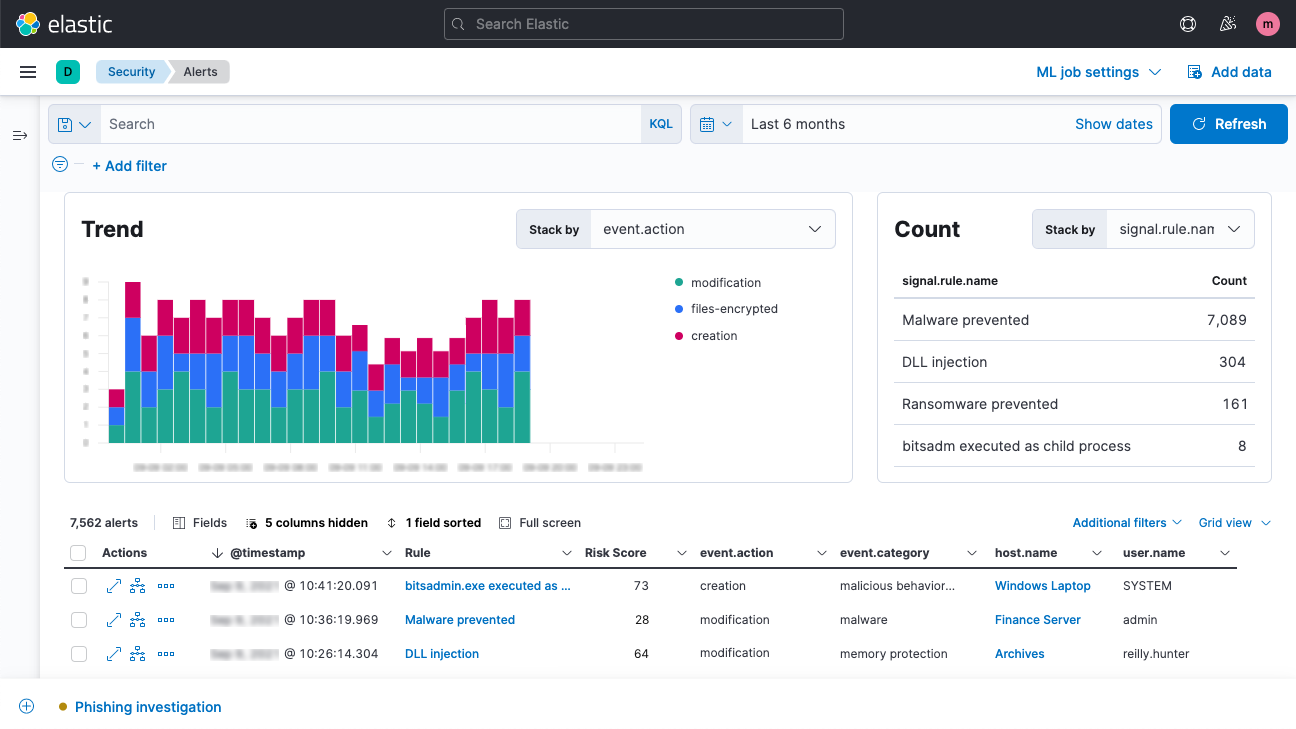
Memory threat protection for Windows endpoints
Memory protection stops many of the techniques used for process injection via shellcode, whereby an attacker attempts to avoid detection by executing an attack from memory instead of from on-disk, where most detection tools operate. Adversaries leverage in-memory attacks to evade common defensive technologies, and it has long been a key method for several named threat groups, including APT28, which used it to attack the Democratic National Committee.
Elastic Security 7.15 prevents memory manipulation via shellcode, stopping sub-techniques such as thread execution hijacking, asynchronous procedure call, process hollowing, and process doppelgänging, providing organizations another layer of prevention against attacks engineered to evade less sophisticated security technologies.
Host isolation for cloud-native Linux environments
Elastic Security 7.15 enables analysts to quarantine Linux hosts via a remote action invoked from Kibana. With one click, analysts can respond to malicious activity by isolating a host from a network, containing the attack and preventing lateral movements. Host isolation was introduced for Windows and macOS in version 7.14, and is now available on every OS protected by Elastic Agent.
We’re implementing this capability on Linux systems with the cloud-native extended Berkeley Packet Filter (eBPF) technology, a reflection of our commitment to technologies that enable users to observe and protect modern cloud-native systems in the most frictionless way possible. More on our continuing efforts in cloud security can be found in our recent announcements on joining forces with build.security and Cmd.
Ingest and analyze data from across your org
Our latest release helps security teams achieve visibility across their attack surface via new and enhanced integrations with Carbon Black EDR, CrowdStrike Falcon, Cloudflare, Hashicorp Vault, and Palo Alto Networks Cortex XDR.
Carbon Black EDR integration
Integration with VMware Carbon Black EDR enables organizations to easily ingest endpoint activity. As with all Elastic-built connectors, logs are formatted for Elastic Common Schema (ECS), enabling immediate use with Elastic Security dashboards, detection content, and more.
CrowdStrike Falcon integration
The new CrowdStrike Falcon integration for Elastic Agent goes beyond collecting Falcon platform alerts. Built on the Falcon Data Replicator, it delivers deep visibility by enabling the granular collection and long-term analysis of raw endpoint events and platform audit data.
Cloudflare integration
Elastic Security has a new integration with Cloudflare, one of the largest content delivery networks (CDN) in the world that handles 5-10% of global internet traffic. The integration makes it easy to ingest logs, enabling cross-environment monitoring of network-borne threats and end-to-end detection and response.
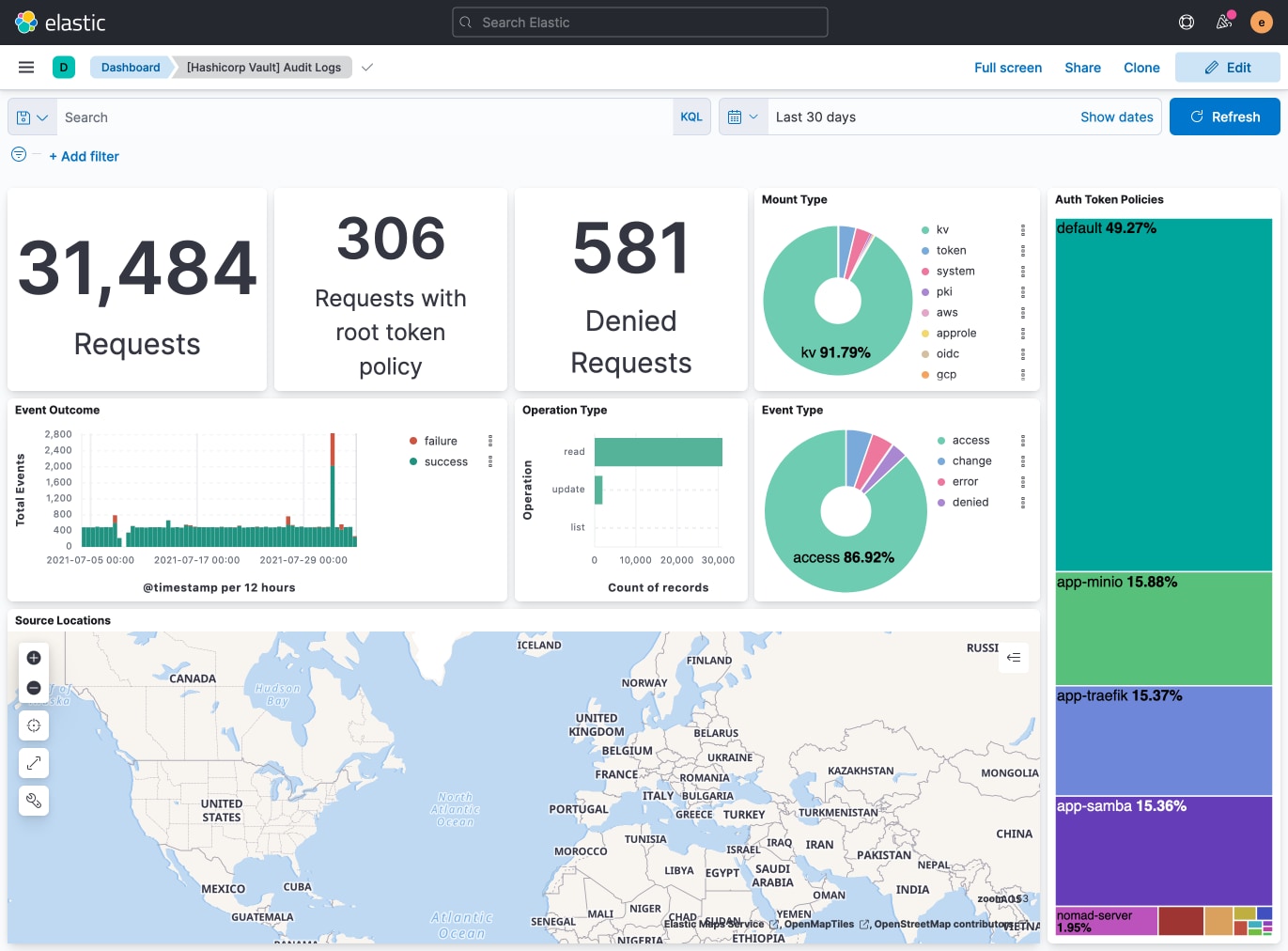
Hashicorp Vault integration
7.15 enables the ingestion of logs from Hashicorp Vault, a tool for securely storing and using API keys, passwords, certificates, and other secrets. With the integration, Elastic Agent collects audit logs, operational logs, and telemetry data. The audit logs reveal which users are accessing which secrets, without revealing the secrets themselves. To enable easy monitoring, data can be visualized on a prebuilt Kibana dashboard.
Palo Alto Networks Cortex XDR
The new Palo Alto Network Cortex XDR integration supports ingestion of alerts and associated events from Cortex XDR, with data mapped to ECS. This data enables SecOps teams to leverage findings across cloud, network, and endpoint data sources from Cortex XDR during incident response and threat hunting within Elastic Security.
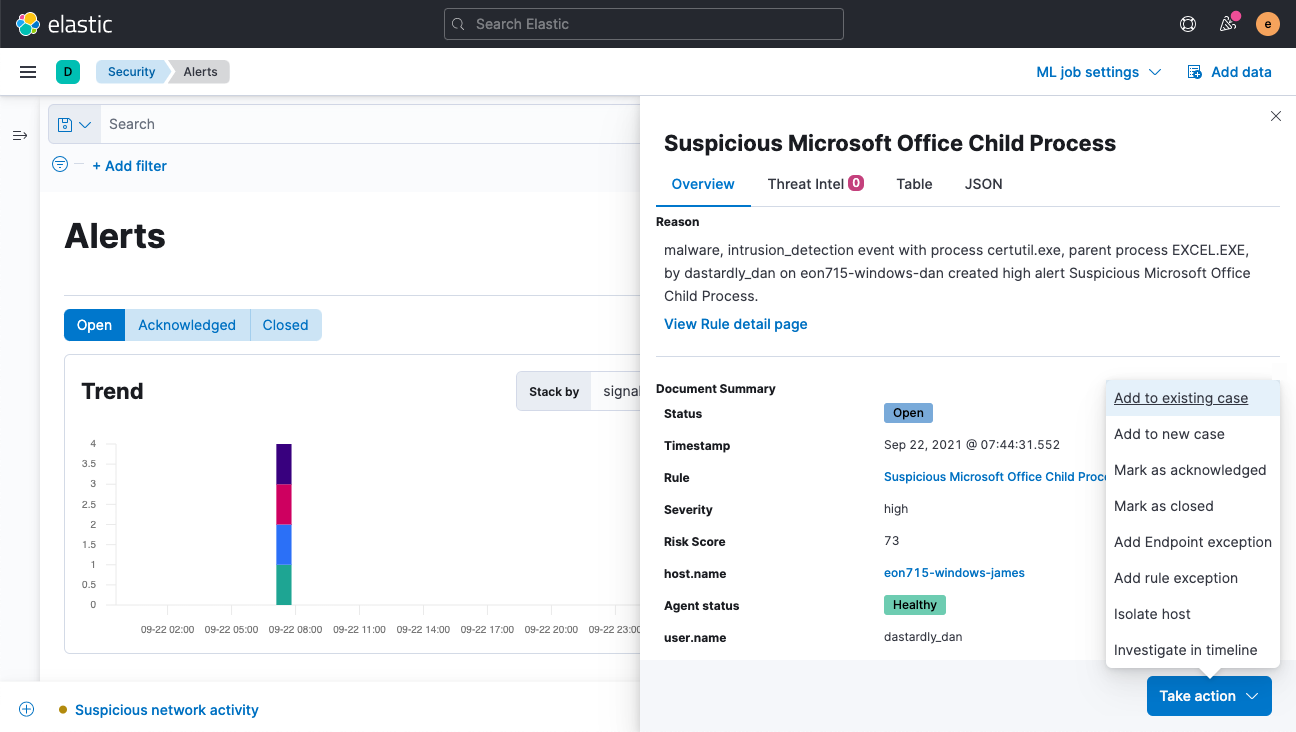
Triage alerts faster
Atop the updated Alerts page, an Alert status filter (Open, Acknowledged, Closed) enables quick filtering of every widget, including the Trend chart, the new Count view, and the Alerts table.
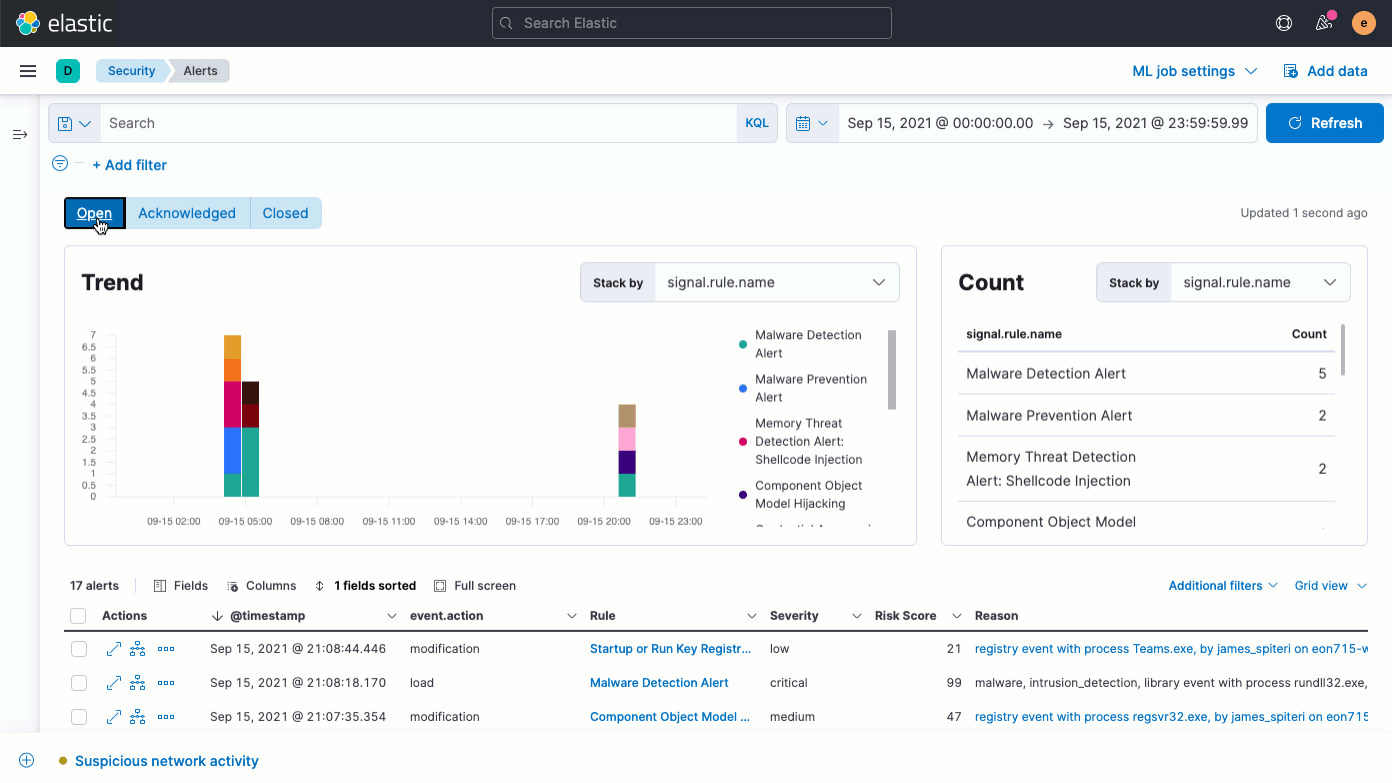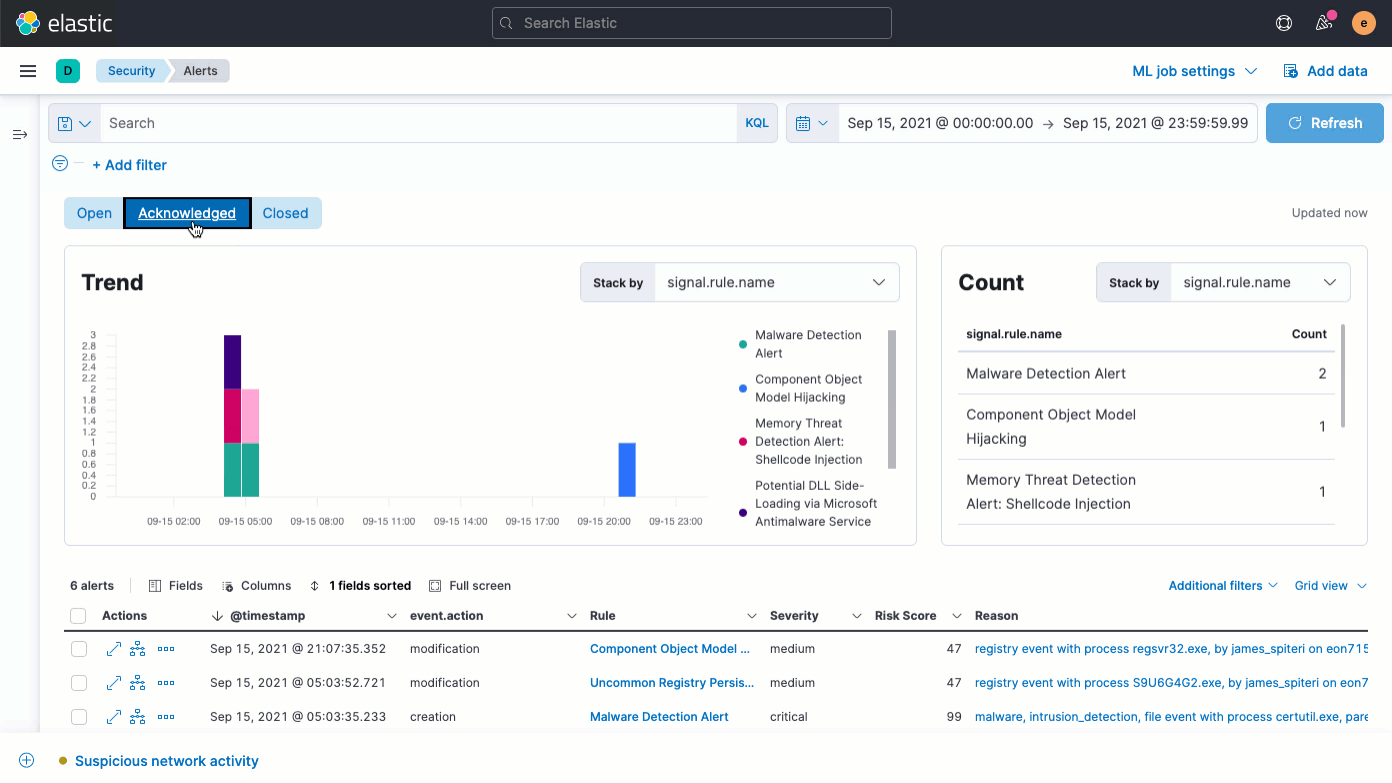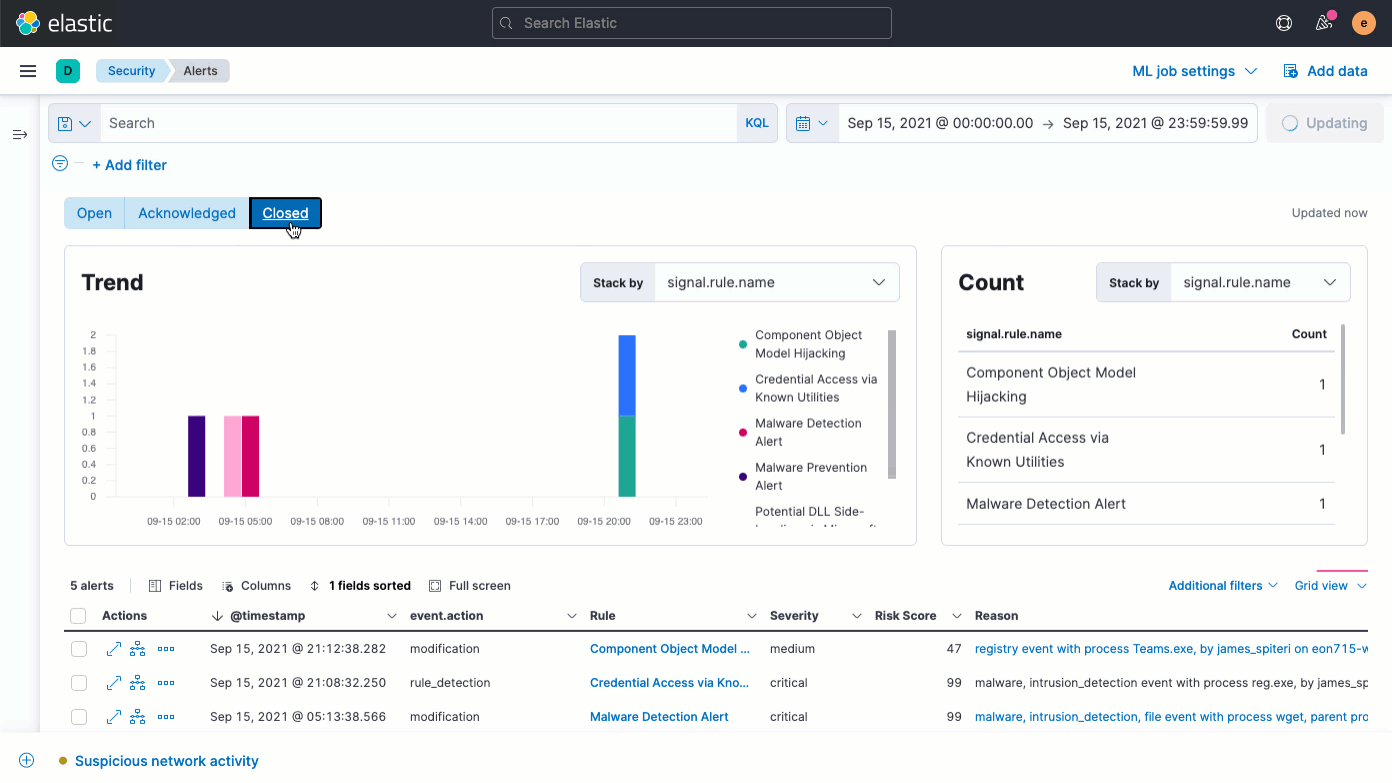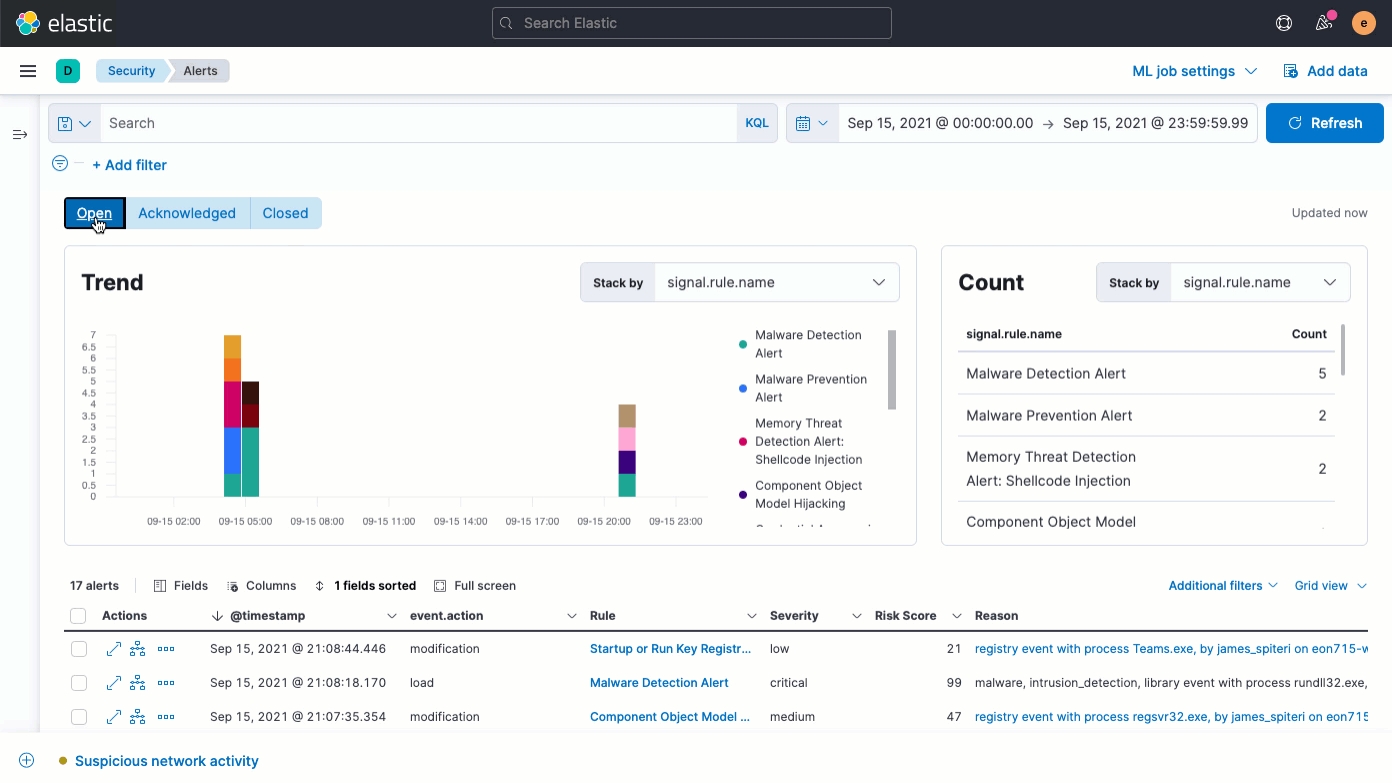
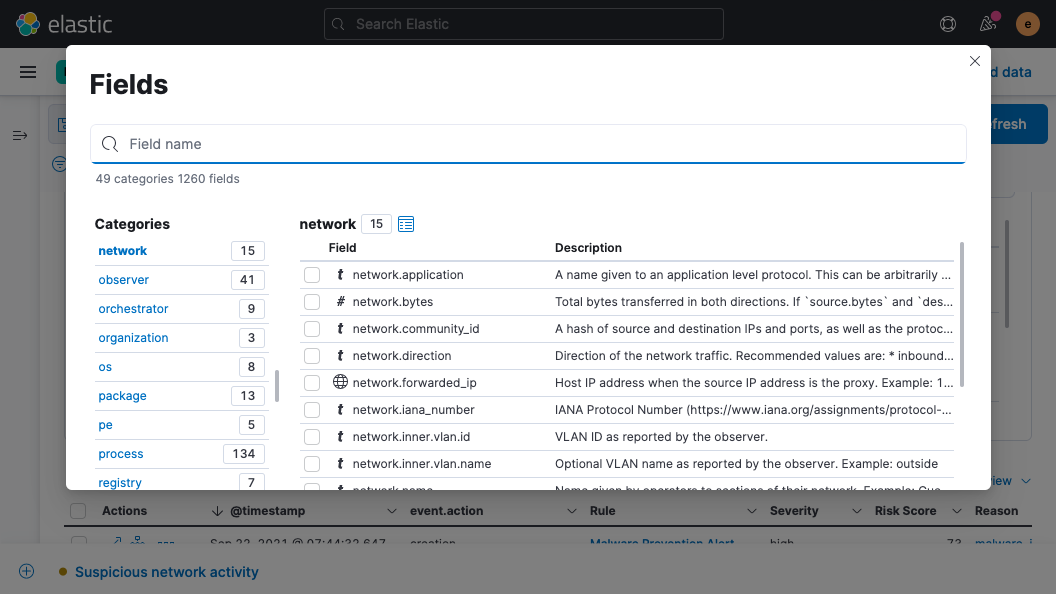
The Alerts table has been improved in several ways. Of greatest note, it now features the Reason field, which conveys why an alert has triggered. An updated Fields browser gives analysts greater control over the columns in the Alerts table, organizing fields by category and providing descriptions alongside field names to help practitioners leverage the full power of Elastic Common Schema (ECS).
With an updated Alerts flyout, analysts can view a summary of the alert and quickly understand why it was generated. Hover actions provide new ways to interact with the alert table or an investigation timeline. The flyout also provides several ways to take action on an alert, such as adding the alert to a new or existing case, changing the alert status, isolating an alerting host (for hosts running Agent with the endpoint security integration), and initiating an investigation.
Inspect hosts with osquery on Elastic Agent
Osquery Manager delivers several exciting enhancements in the 7.15 release:
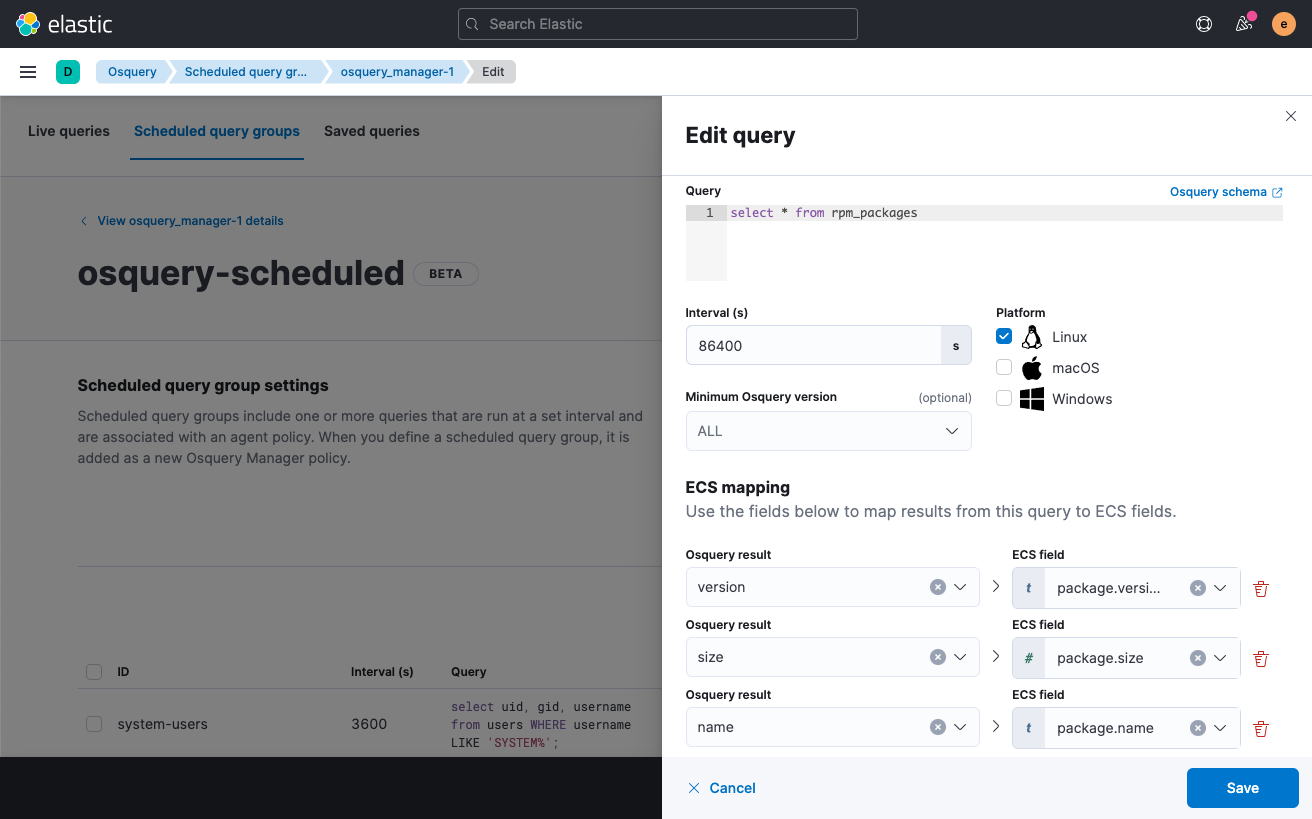
Standardize scheduled query results with ECS
When defining scheduled queries, you can now map query results to ECS fields to standardize your osquery data for use across detections, machine learning, and any other areas that rely on ECS-compliant data. This capability greatly increases the value of the queries you run by making those results more readily usable across the Elastic Stack.
Access controls for osquery
7.15 gives security teams more control over who can access osquery and view results. Previously, only superusers could use osquery, but access to this feature can now be granted as needed, empowering administrators to delegate who can run, save, or schedule queries:
- With a free and open Basic license, organizations can grant
All,Read, orNoaccess to superusers and non-superusers alike — improving administrative control and enabling non-superusers access to osquery. - With a Gold license, organizations can achieve finer-grained control. For example, they can constrain who's allowed to edit scheduled queries, or allow certain users to run saved queries but prevent ad-hoc queries.
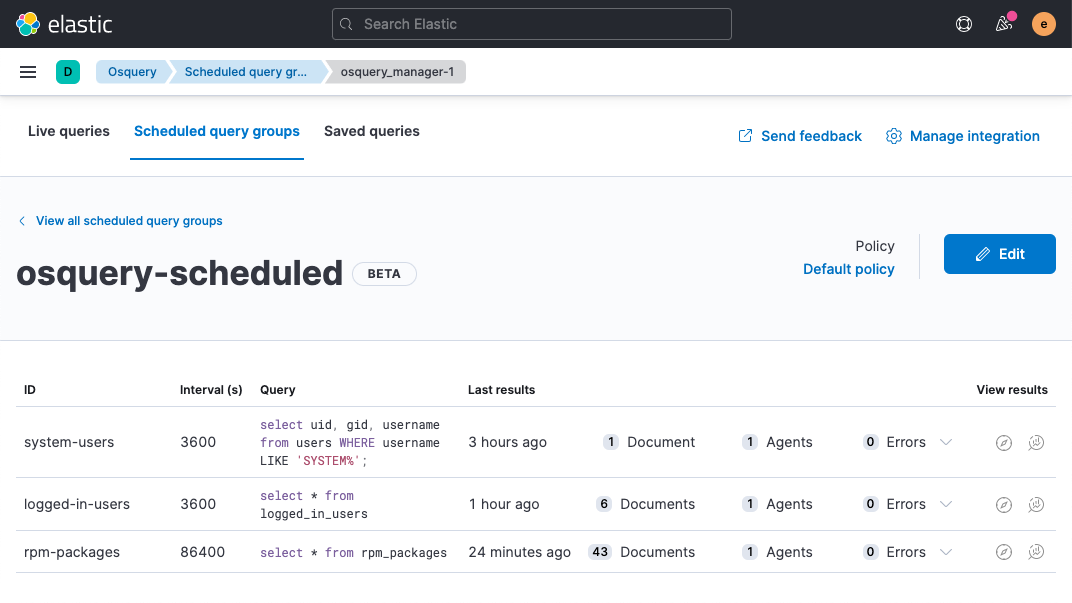
Scheduled query status at a glance
Scheduled query groups now show the status of individual queries within a group, allowing analysts to understand at a glance whether there are any results to review or issues to address. Surfacing this information can also help analysts tune queries and resolve any errors.
Try it out
Existing Elastic Cloud customers can access many of these features directly from the Elastic Cloud console. If you’re new to Elastic Cloud, take a look at our Quick Start guides (bite-sized training videos to get you started quickly) or our free fundamentals training courses. You can always get started with a free 14-day trial of Elastic Security. Or download the self-managed version of the Elastic Stack for free.
Read about these capabilities and more in the Elastic Security 7.15 release notes, and other Elastic Stack highlights in the Elastic 7.15 announcement post.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.