NEW in Elastic Security 8.15: Automatic Import, Gemini models, and AI Assistant APIs

Elastic Security 8.15 is now available, enhancing our mission to modernize security operations with AI-driven security analytics. Key features include the brand new Automatic Import to streamline data ingestion and onboarding, support for Google’s Gemini 1.5 Pro and Flash large language models (LLMs), a new set of APIs for the Elastic AI Assistant, on-demand file scans for the Elastic Defend integration, and a redesigned way of pivoting between different contexts.
Elastic Security 8.15 is available now on Elastic Cloud — the only hosted Elasticsearch offering to include all of the new features in this latest release. You can also download the Elastic Stack and our cloud orchestration products — Elastic Cloud Enterprise and Elastic Cloud on Kubernetes — for a self-managed experience.
What else is new? Check out the Elastic 8.15 announcement blog to learn more.
Automate SIEM data onboarding with Automatic Import
Introducing Automatic Import, a new generative AI feature in our SIEM solution. This feature automates the normalization of security events, providing broader visibility and rapid data onboarding. With Automatic Import, the time required to create custom integrations is drastically reduced from several hours (or even days) to less than 10 minutes, significantly lowering the learning curve for integration development.
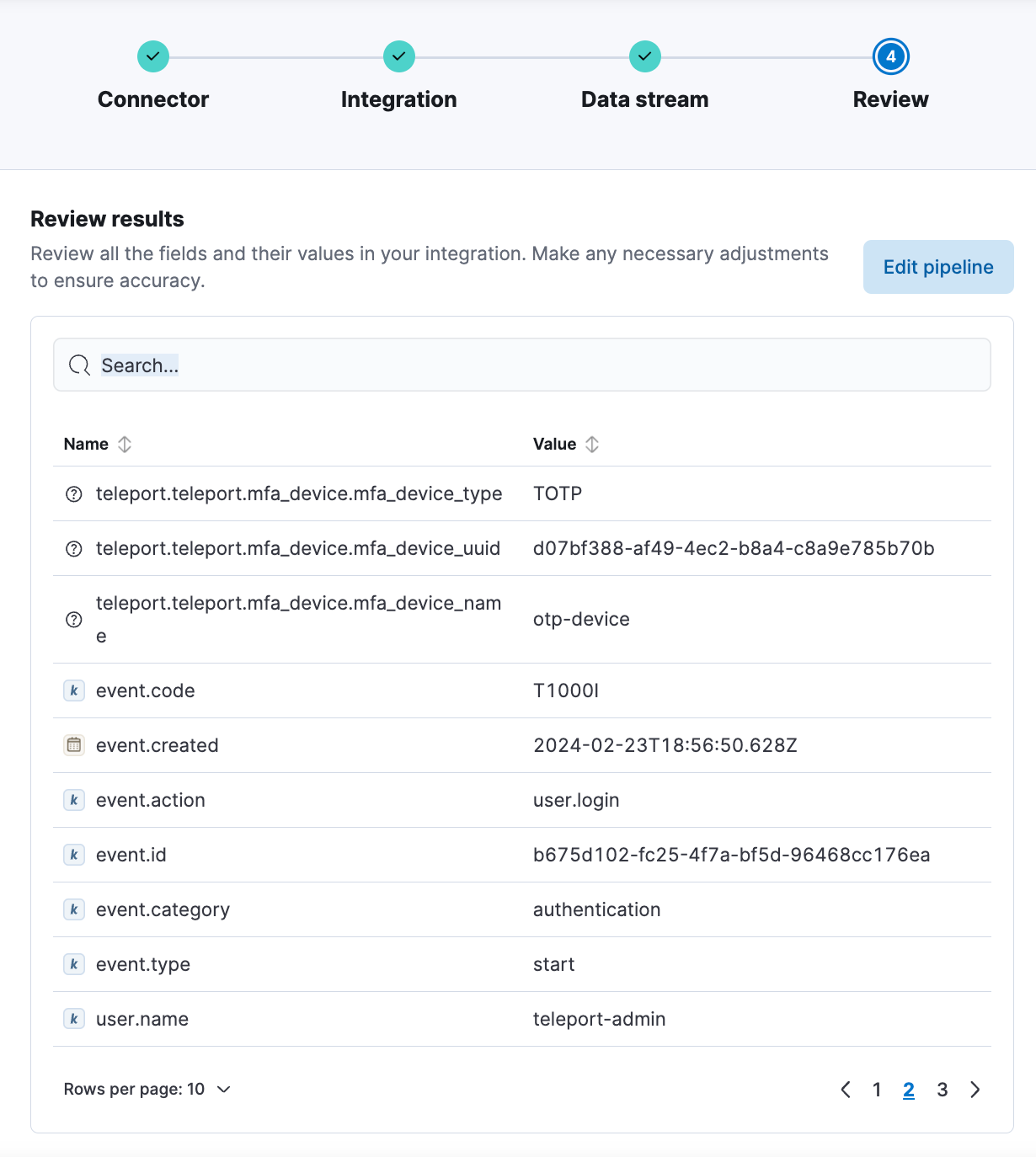
The intuitive workflow allows you to upload sample data you wish to onboard. Automatic Import then maps this data to the Elastic Common Schema (ECS), ensuring that Elastic Security's analytics can leverage your custom data for enhanced threat detection.
To learn more about Automatic Import, please read the blog Elastic accelerates SIEM data onboarding with Automatic Import powered by Search AI.
APIs for interacting with the Elastic AI Assistant for Security
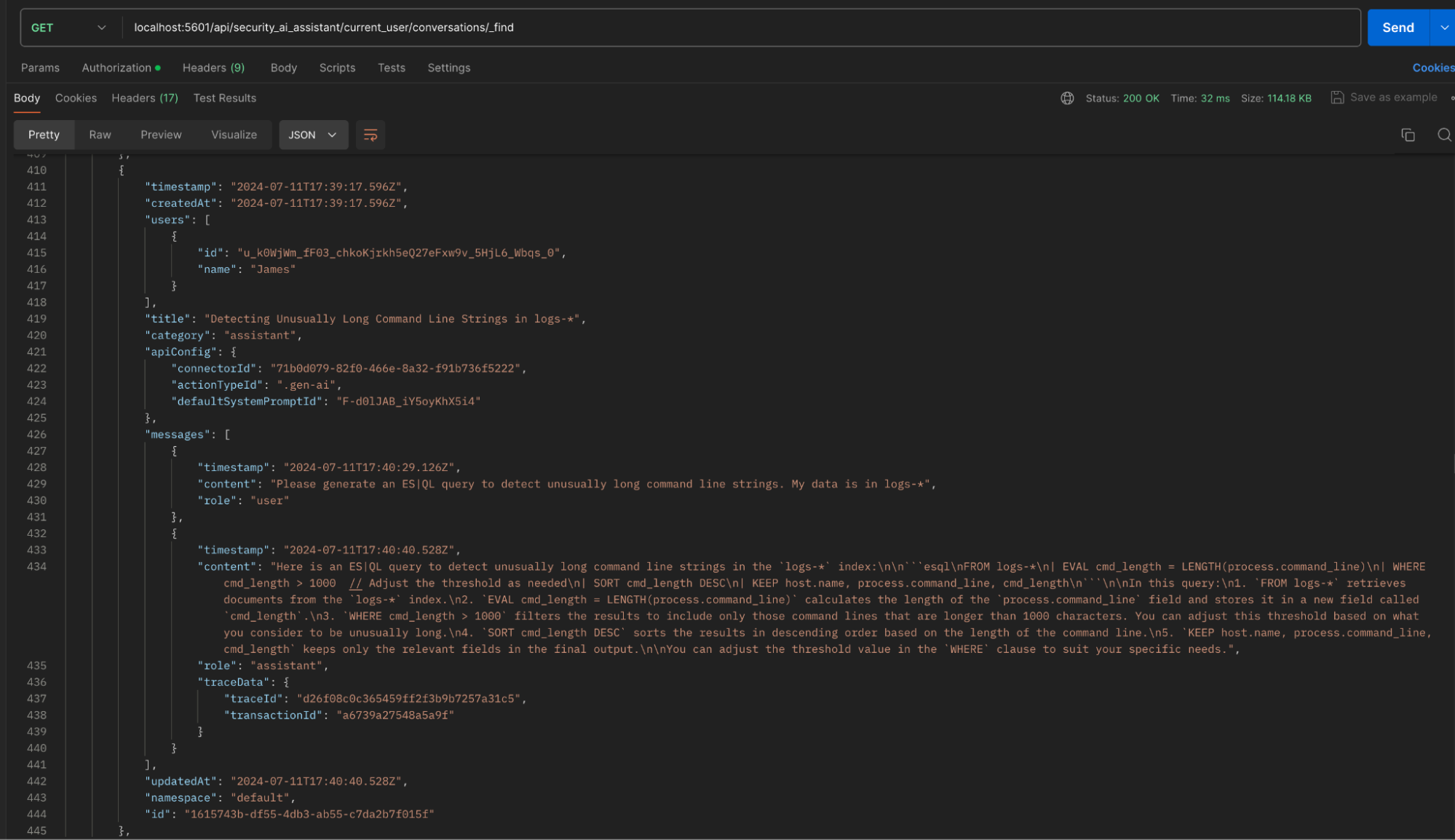
Additionally, we are introducing several APIs to programmatically interact with and configure the Elastic AI Assistant. This includes the ability to introduce Elastic AI Assistant responses (including those that use knowledge base content) as part of any automation or SOAR workflows as well as control features like message and conversation handling, prompt management, and anonymization. When combined with all the existing Elastic Security APIs, users can now build exceptionally powerful playbooks as part of their automation and orchestration strategy.
New LLM integration with Google’s Gemini 1.5 Pro and Flash models

Users of Elastic Security Attack Discovery and Elastic AI Assistant features can now utilize Google’s Gemini 1.5 Pro and Flash LLMs via Google Vertex AI. These models complement the existing Amazon Bedrock, OpenAI, and Azure OpenAI connectors, providing access to the latest and greatest commercial LLMs on the market.
Google’s Gemini 1.5 Pro model offers an extensive context window of 2 million tokens, ideal for users managing large alert volumes and retaining long chat histories.
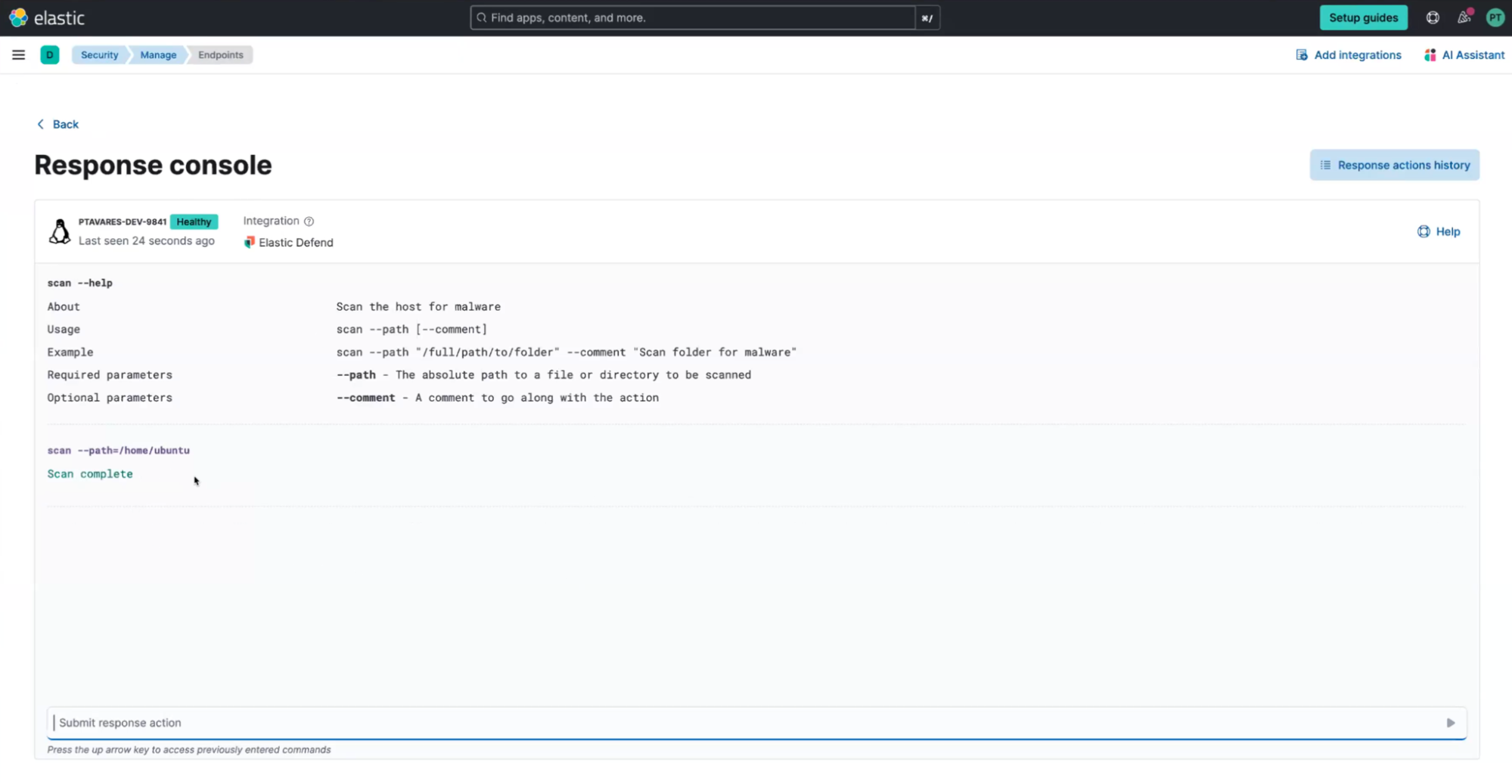
On-demand directory scanning with the Elastic Defend integration
Users can now initiate an on-demand scan of files within a specified directory through our response console workflow. This feature compliments our existing real-time protections provided by the Elastic Defend integration, which automatically scans for malware as files are created, modified, and executed. By allowing scans of specific directories at their discretion, users gain an additional layer of security and peace of mind. This capability can be particularly useful for compliance purposes, ensuring that file systems are thoroughly scanned and verified to be free of malware during audits or regulatory checks. Additionally, administrators can run comprehensive scans upon deployment to ensure the integrity of the file system, providing reassurance that no malware has been missed.
This feature underscores our dedication to delivering adaptable and comprehensive endpoint security. This capability is generally available (GA) in Elastic Security 8.15 for every OS protected by Elastic Defend — accessible via the Elastic Security Enterprise subscription tier for self-managed and cloud deployments and as a part of our serverless offering, Endpoint Complete subscription.
Enhanced investigative context pivoting
The reimagined alert experience, first introduced in Elastic Security 8.10, brought an entirely new prebuilt, investigative experience to alerts by providing insights to the analyst, such as related entities, correlated events, and visualization previewing. Over the last few releases, this experience has been steadily improving by extending the alert experience to all events and bringing the new design to the investigative workspace called Timeline.
Now in Elastic Security 8.15, we allow pivoting between experiences without changing the primary context. For instance, a user can be viewing an alert and then preview correlated alerts, related events, and details about the host and user entities. This enables the user to see other Elastic Security experiences without disrupting their core workflow like alert investigation.
Try it out
Read about these capabilities and more in the release notes.
Existing Elastic Cloud customers can access many of these features directly from the Elastic Cloud console. Not taking advantage of Elastic on cloud? Start a free trial.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.