Collecting Windows telemetry with Elastic: An introduction to the ETW Filebeat input
.jpg)
In the world of security, being able to use system telemetry of Windows hosts opens new possibilities for monitoring, troubleshooting, and securing IT environments. Recognizing this, Elastic has introduced new capabilities focused on Event Tracing for Windows (ETW) — a powerful Windows-native mechanism for capturing a vast array of system and application events. With these new additions, Elastic users can capture, analyze, and visualize Windows telemetry using Elastic's Search AI Platform.
What is ETW?
ETW is a lightweight, high-performance Windows-native mechanism for logging detailed event data about system performance and activity. Unlike traditional Windows event logs, ETW enables users to gather low-level telemetry that can be tailored for different providers and scenarios from system performance insights to application-specific diagnostics.
Motivation for integrating ETW in Elastic
ETW has been widely used for diagnostics and performance monitoring within Windows environments, but collecting and managing ETW data traditionally required complex setups. By integrating ETW capabilities directly into Elastic, our goal is to simplify this process, making it easier to collect, filter, and analyze ETW events alongside other system and application logs within Elastic.
Deep dive: Filebeat ETW input
The centerpiece of Elastic’s new ETW capabilities is the ETW input for Filebeat. This new input allows Filebeat to directly subscribe to ETW providers, simplifying the way ETW data can be gathered, transmitted, and processed. Here’s an in-depth look at how it works and how you can use it.
How the Filebeat ETW input works
The Filebeat ETW input subscribes to ETW sessions on a Windows host. An ETW session is a logical grouping of events from ETW providers, which are essentially sources of telemetry data, such as Windows Kernel and application providers.
The ETW input in Filebeat uses this subscription mechanism, gathering data in real time and shipping it to Elasticsearch for analysis and visualization. It can operate in three flexible modes and adapt to a range of data collection scenarios for both real-time and historical data needs:
Creating a new session: In this mode, Filebeat initializes a new ETW session on the Windows host to capture events from user-mode providers. This setup is ideal for scenarios requiring real-time data from applications or services currently running on the system. By creating a dedicated session, users can gather specific telemetry without affecting or relying on pre-existing ETW sessions on the system.
Attaching to an existing session: Filebeat can also attach to an already active ETW session, collecting ongoing event data generated within that session. This approach is useful for environments where ETW sessions are already in use. It allows administrators to capture events alongside other monitoring workflows without duplicating sessions or impacting system performance.
Reading from a prerecorded .etl file: In some cases, ETW data may be recorded in advance and stored in .etl files. Filebeat can parse these files, enabling users to analyze historical event data. This mode is particularly valuable for retrospective analysis, where users may want to investigate previous system or application behavior based on ETW data captured earlier.
This flexibility in operational modes allows Filebeat’s ETW input to adapt to diverse use cases — whether for real-time monitoring, forensic analysis, or operational troubleshooting.
Technical workflow overview
Once the mode is set, the ETW input follows a streamlined process to gather and send data to Elastic:
Provider subscription: Filebeat initiates a subscription to one or more ETW providers based on user configuration, whether by creating a new session or connecting to an existing one.
Data collection: Events are captured from the active ETW session or parsed from .etl files. ETW records are collected, parsed, and converted into JSON objects to ensure they are structured consistently for valid ingestion. This transformation prepares the data for smooth indexing in Elasticsearch, allowing it to be seamlessly integrated with other log and metric data within Elastic.
Transmission to Elasticsearch: Once events are collected, they’re sent to Elasticsearch for storage and analysis — and ready for visualization within Kibana.
Example use case: Configuring the ETW input
To demonstrate how the Filebeat ETW input can be configured to capture data from a specific ETW provider, let’s take the example of monitoring the Microsoft DNS Server provider.
To configure the Filebeat ETW input for monitoring DNS events, we can use the logman command-line utility, which provides insight into available ETW providers and their details. logman allows us to list all available providers, view the manifest of each one, and examine details like filterable keywords, trace levels, and other configurations.
Before configuring Filebeat to collect events from a specific provider, you may want to view all available ETW providers in your system. To see the full list of providers, run the following command:
PS> logman query providersExample output:
Provider GUID
-------------------------------------------------------------------------------
Microsoft-Windows-Kernel-Process {75A03DF8-6A47-4C6C-B0A0-FB37A13CA342}
Microsoft-Windows-Kernel-File {EDD08927-9CC4-4E65-B970-C2560FB5C289}
Microsoft-Windows-Kernel-Network {7DD42A49-5329-4832-8DFD-43D979153A88}
Microsoft-Windows-DNSServer {EB79061A-A566-4698-9119-3ED2807060E7}
Microsoft-Windows-PowerShell {A0C1853B-5C40-4B15-8766-3CF1C58F985A}
...This command outputs a list of available ETW providers, showing each provider’s name and unique GUID. By locating the provider of interest, you can note its name and GUID for configuration purposes.
To see more details about a particular provider as the Microsoft DNS Server, run in a command shell:
PS> logman query providers "Microsoft-Windows-DNSServer"An example output would be:
Provider GUID
-------------------------------------------------------------------------------
Microsoft-Windows-DNSServer {EB79061A-A566-4698-9119-3ED2807060E7}
Value Keyword Description
-------------------------------------------------------------------------------
0x0000000000000001 QUERY_RECEIVED
0x0000000000000002 RESPONSE_SUCCESS
0x0000000000000004 RESPONSE_FAILURE
0x0000000000000008 IGNORED_QUERY
0x0000000000000010 RECURSE_QUERY_OUT
0x0000000000000020 RECURSE_RESPONSE_IN
0x0000000000000040 RECURSE_QUERY_DROP
...
0x8000000000000000 Microsoft-Windows-DNSServer/Analytical Microsoft-Windows-DNS-Server/Analytical
0x4000000000000000 Microsoft-Windows-DNSServer/Audit Microsoft-Windows-DNS-Server/Audit
Value Level Description
-------------------------------------------------------------------------------
0x02 win:Error Error
0x03 win:Warning Warning
0x04 win:Informational Information
PID Image
-------------------------------------------------------------------------------
0x00000354 C:\Windows\System32\dns.exe
0x00000354 C:\Windows\System32\dns.exeFrom this output, we can see that the provider Microsoft-Windows-DNSServer offers several keywords for filtering specific event types, such as QUERY_RECEIVED, RESPONSE_SUCCESS, RESPONSE_FAILURE, and others — each represented by a unique hex code. Additionally, it provides levels (Error, Warning, Informational) that specify the severity of events that can be captured.
The Filebeat ETW input offers filtering options that allow you to capture only relevant events from a specific provider:
match_any_keyword: Captures events if they match any one of the specified keywords. This is useful when you want to monitor a range of event types that don’t necessarily occur together.
match_all_keyword: Captures events only if they match all specified keywords. This option is ideal for highly specific event monitoring where events must meet multiple criteria simultaneously.
trace_level: Filters events based on their severity level, allowing you to specify whether to capture only errors, warnings, or informational messages. This can help to focus monitoring efforts on high-priority issues.
The output from logman lists various event types with corresponding keywords, allowing you to select specific events to monitor. For example, if you want to track recursive queries, you might look for keywords like RECURSE_QUERY_OUT, RECURSE_RESPONSE_IN, or RECURSE_QUERY_DROP. To filter specifically for these recursive query events, you would calculate the bitmask sum of their values:
1. Identify the hex values for each keyword:
RECURSE_QUERY_OUT: 0x0000000000000010
RECURSE_RESPONSE_IN: 0x0000000000000020
RECURSE_QUERY_DROP: 0x0000000000000040
Microsoft-Windows-DNSServer/Analytical (to ensure Analytical events are captured): 0x8000000000000000
2. Add these values together:
0x8000000000000000 + 0x0000000000000010 + 0x0000000000000020 + 0x0000000000000040 = 0x8000000000000070
This resulting bitmask, 0x8000000000000070, would be used in the match_any_keyword configuration to capture only these specific recursive query events.
This approach allows for granular control over the data the ETW input ingests, ensuring you collect only events that are relevant to your monitoring needs.
Introducing ETW-based integrations
Beyond the Filebeat ETW input, we’re also introducing two integrations that simplify ETW data collection for specific use cases.
Microsoft DNS Server integration
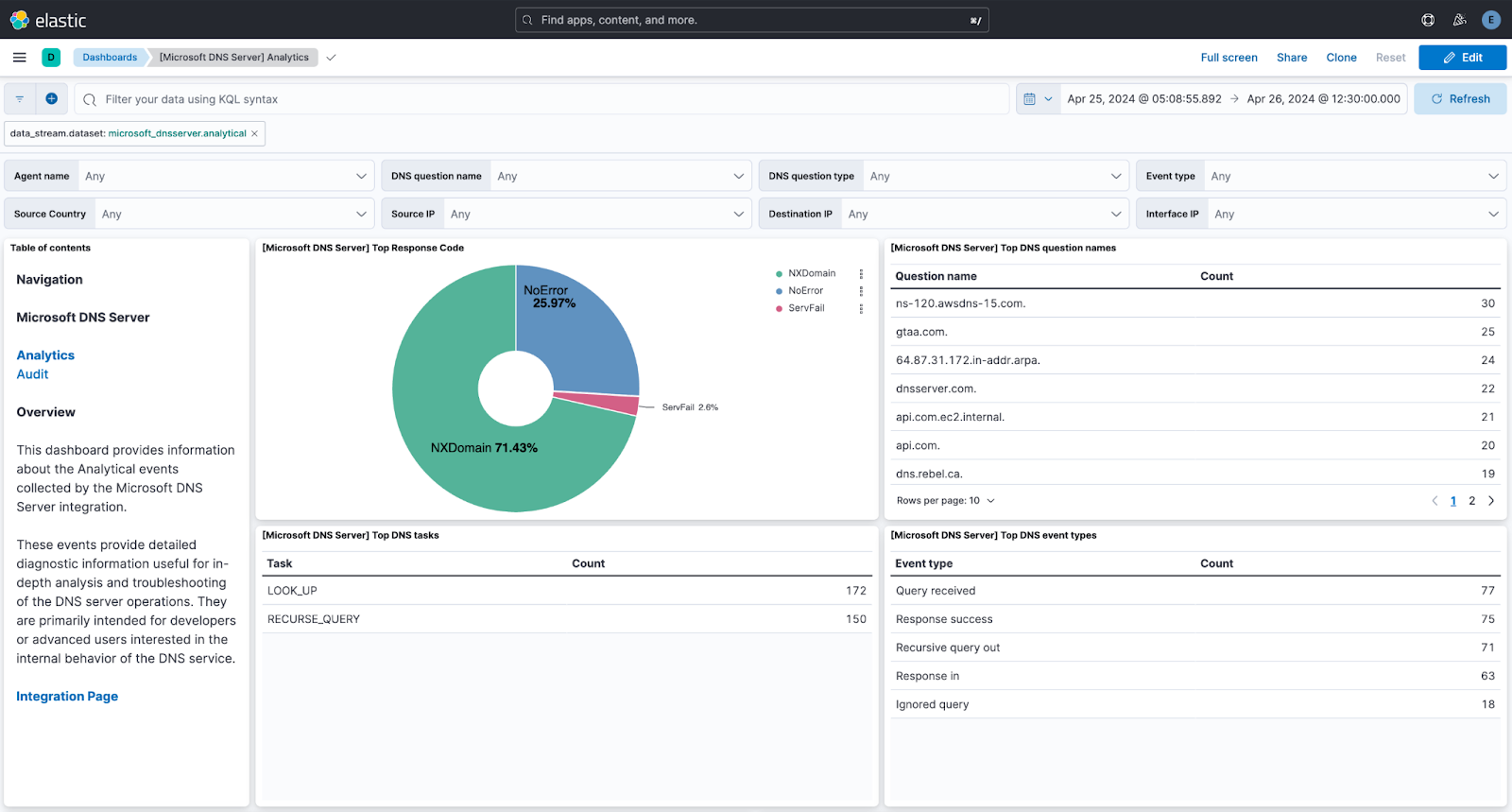
Monitoring DNS server analytical logs is essential for maintaining the security and performance of network infrastructure. Common types of DNS attacks — DNS hijacking, DNS tunneling, various denial-of-service (DoS) attacks, and DNS cache poisoning — mean significant risks to organizations. Windows DNS analytical logging is a vital event source that administrators and security analysts require visibility into. It provides detailed insights into every DNS transaction occurring both internally and externally on a network.
The Microsoft DNS Server integration focuses specifically on gathering DNS server Audit and Analytical logs. With this integration, organizations can easily track and analyze DNS queries, responses, and error rates — facilitating a deeper understanding of DNS activity. The prebuilt dashboards included in the integration allow users to dive into DNS activity analysis without the need for complex configuration or extensive setup.
Custom ETW integration
The custom ETW integration enables users to ingest ETW events into Elastic, offering the flexibility to configure the integration with any compatible provider or to read from prerecorded .etl files.
This adaptability allows users to capture provider-specific data — application logs, system performance metrics, or historical event data — tailored to their monitoring needs.
Try the ETW input
The new ETW input in Elastic reveals powerful possibilities for monitoring and securing Windows environments. Users can now collect detailed telemetry from Windows applications and services that rely on ETW, allowing for real-time insights into system performance, application behavior, and potential security risks.
This capability is complemented by built-in integrations, such as the Microsoft DNS Server integration, that make it simple to gain immediate, actionable insights without complex setup.
These new features are just the beginning of what ETW can bring to Elastic users. We’re excited for you to try out these features, explore new use cases, and share your feedback to help us continue evolving ETW capabilities within Elastic. To get started, visit the ETW input page for setup instructions, or explore these features with a free trial on Elastic Cloud.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.