Grant access using API keys
Instead of using usernames and passwords, you can use API keys to grant access to Elasticsearch resources. You can set API keys to expire at a certain time, and you can explicitly invalidate them. Any user with the manage_api_key or manage_own_api_key cluster privilege can create API keys.
APM Server instances typically send both collected data and monitoring information to Elasticsearch. If you are sending both to the same cluster, you can use the same API key. For different clusters, you need to use an API key per cluster.
For security reasons, we recommend using a unique API key per APM Server instance. You can create as many API keys per user as necessary.
To create an API key:
Open the API keys management page in the navigation menu or use the global search field.
Click Create API key.
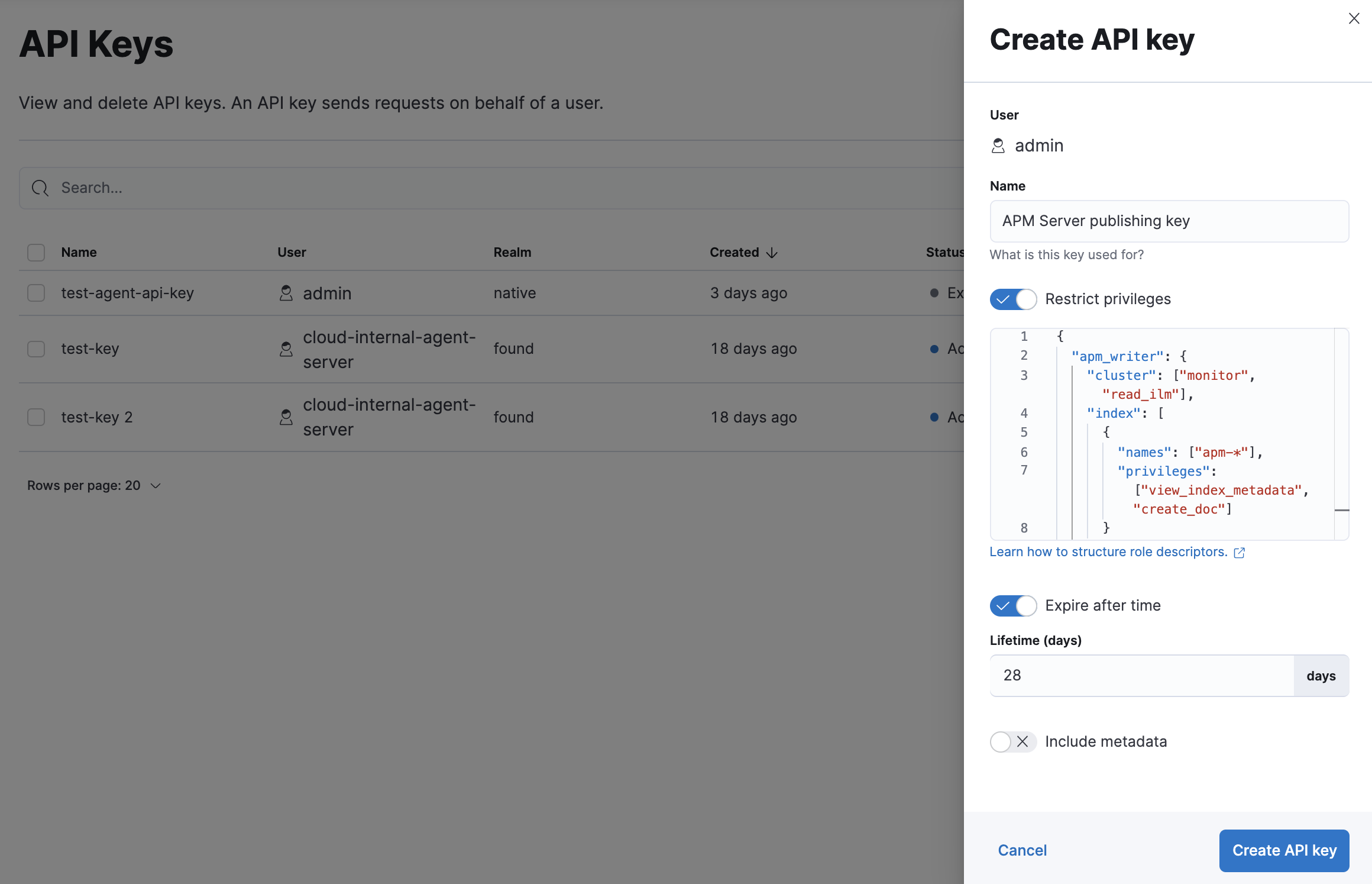
Enter a name for your API key and select Restrict privileges. In the role descriptors box, assign the appropriate privileges to the new API key. For example:
{ "apm_writer": { "cluster": ["monitor"], "index": [ { "names": ["traces-apm*","logs-apm*", "metrics-apm*"], "privileges": ["auto_configure", "create_doc"] } ] }, "apm_sourcemap": { "index": [ { "names": [".apm-source-map"], "privileges": ["read"] } ] }, "apm_agentcfg": { "index": [ { "names": [".apm-agent-configuration"], "privileges": ["read"], "allow_restricted_indices": true } ] }, "apm_tail_based_sampling": { "index": [ { "names": ["traces-apm.sampled"], "privileges": ["read"] } ] } }NoteThis example only provides privileges for writing data. See Use feature roles for additional privileges and information.
To set an expiration date for the API key, select Expire after time and input the lifetime of the API key in days.
Click Create API key.
You must set the API key to be configured to Beats. Immediately after the API key is generated and while it is still being displayed, click the Encoded button next to the API key and select Beats from the list in the tooltip. Base64 encoded API keys are not currently supported in this configuration.
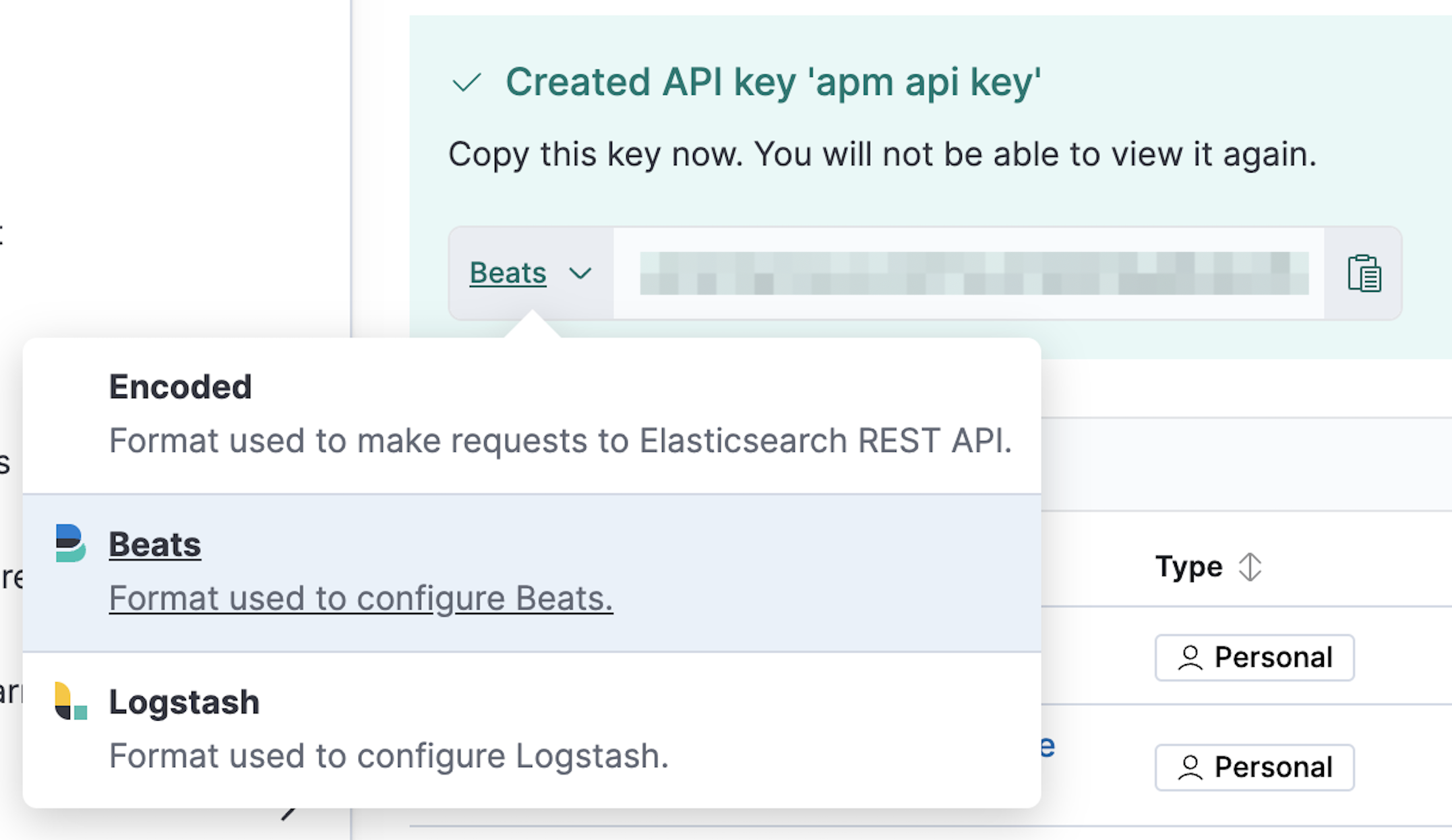
You can now use this API key in your apm-server.yml configuration file:
output.elasticsearch:
api_key: TiNAGG4BaaMdaH1tRfuU:KnR6yE41RrSowb0kQ0HWoA
- Format is
id:api_key(as shown in the Beats dropdown)
To open the API keys management page, find it in the navigation menu or use the global search field. Click Create API key.

Enter a name for your API key and select Restrict privileges. In the role descriptors box, assign the appropriate privileges to the new API key. For example:
{
"apm_monitoring": {
"index": [
{
"names": [".monitoring-beats-*"],
"privileges": ["create_index", "create_doc"]
}
]
}
}
This example only provides privileges for publishing monitoring data. See Use feature roles for additional privileges and information.
To set an expiration date for the API key, select Expire after time and input the lifetime of the API key in days.
Click Create API key. In the dropdown, switch to Beats and copy the API key.
You can now use this API key in your apm-server.yml configuration file like this:
monitoring.elasticsearch:
api_key: TiNAGG4BaaMdaH1tRfuU:KnR6yE41RrSowb0kQ0HWoA
- Format is
id:api_key(as shown in the Beats dropdown)
You can also use Elasticsearch's Create API key API to create a new API key. For example:
POST /_security/api_key
{
"name": "apm_host001",
"role_descriptors": {
"apm_writer": {
"cluster": ["monitor"],
"index": [
{
"names": ["traces-apm*","logs-apm*", "metrics-apm*"],
"privileges": ["auto_configure", "create_doc"]
}
]
},
"apm_sourcemap": {
"index": [
{
"names": [".apm-source-map"],
"privileges": ["read"]
}
]
},
"apm_agentcfg": {
"index": [
{
"names": [".apm-agent-configuration"],
"privileges": ["read"],
"allow_restricted_indices": true
}
]
},
"apm_tail_based_sampling": {
"index": [
{
"names": ["traces-apm.sampled"],
"privileges": ["read"]
}
]
}
}
}
- Name of the API key
- Granted privileges, see Use feature roles
See the Create API key reference for more information.
See the Elasticsearch API key documentation for more information: