Tune detection rules
Using the Elastic Security app, you can tune prebuilt and custom detection rules to optimize alert generation. To reduce noise, you can:
Add exceptions to detection rules.
TipUsing exceptions is recommended as this ensure excluded source event values persist even after prebuilt rules are updated.
Disable detection rules that rarely produce actionable alerts because they match expected local behavior, workflows, or policy exceptions.
Clone and modify detection rule queries so they are aligned with local policy exceptions. This reduces noise while retaining actionable alerts.
Clone and modify detection rule risk scores, and use branching logic to map higher risk scores to higher priority workflows.
Enable alert suppression for custom query rules to reduce the number of repeated or duplicate alerts.
For details about tuning rules for specific categories:
- Tune rules detecting authorized processes
- Tune Windows child process and PowerShell rules
- Tune network rules
- Tune indicator match rules
Organizations frequently use uncommon and in-house applications. Occasionally, these can trigger unwanted alerts. To stop a rule matching on an application, add an exception for the required application.
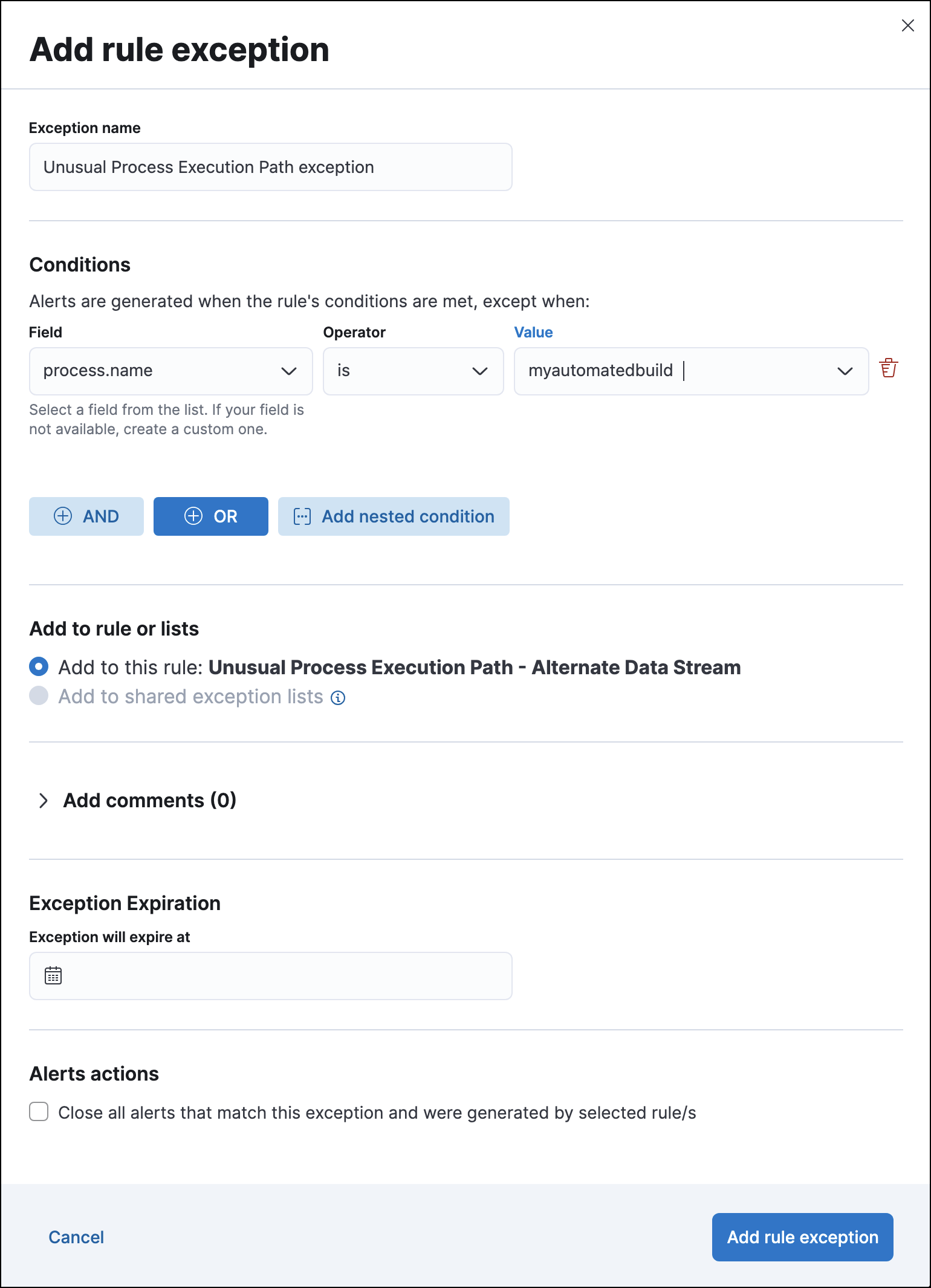
For example, to prevent the Unusual Process Execution Path - Alternate Data Stream rule from producing alerts for an in-house application named myautomatedbuild:
Find Detection rules (SIEM) in the navigation menu or by using the global search field.
In the Rules table, search for and then click on the Unusual Process Execution Path - Alternate Data Stream rule.
The Unusual Process Execution Path - Alternate Data Stream rule details page is displayed.
Select the Rule exceptions tab, then click Add rule exception.
Fill in these options:
Click Add rule exception.
Authorized security testing, system tools, management frameworks, and administrative activity may trigger detection rules. These legitimate activities include:
- Authorized security research.
- System and software management processes running scripts, including scripts that start child processes.
- Administrative and management frameworks that create users, schedule tasks, make
psexecconnections, and run WMI commands. - Legitimate scripts using the
whoamicommand. - Applications that work with file shares, such as backup programs, and use the server message block (SMB) protocol.
To reduce noise for authorized activity, you can do any of these:
- Add an exception to the rules that exclude specific servers, such as the relevant host names, agent names, or other common identifiers. For example,
host.name is <server-name>. - Add an exception to the rules that exclude specific processes. For example,
process.name is <process-name>. - Add an exception to the rules that exclude a common user. For example,
user.name is <security-tester>.
Another useful technique is to assign lower risk scores to rules triggered by authorized activity. This enables detections while keeping the resulting alerts out of high-priority workflows. Use these steps:
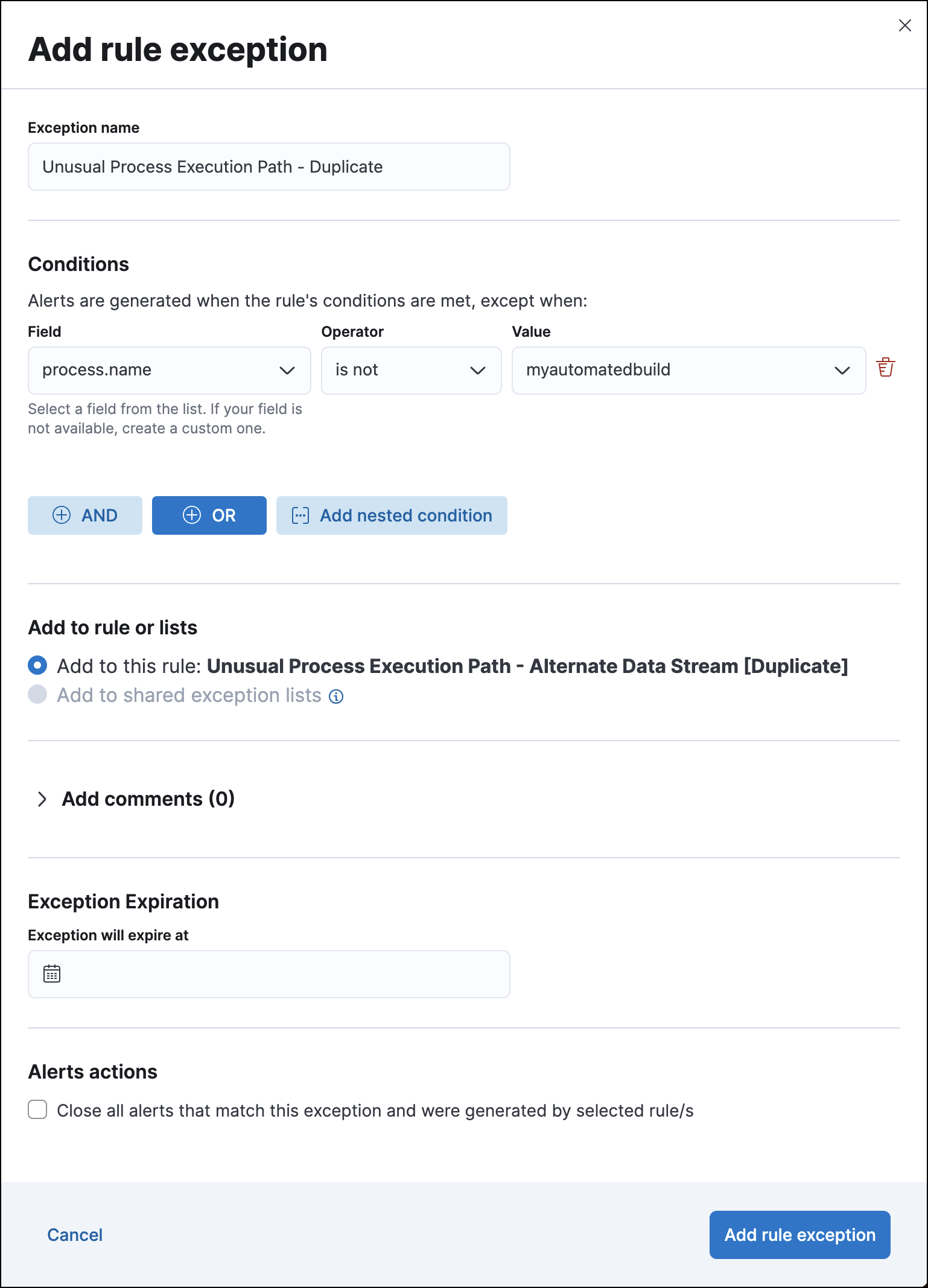
Before adding exceptions, duplicate the prebuilt rule.
Add an exception to the original prebuilt rule that excludes the relevant user or process name (
user.name is <user-name>orprocess.name is "process-name").Edit the duplicated rule as follows:
Click Add rule exception.
Normal user activity may sometimes trigger one or more of these rules:
- Suspicious MS Office Child Process
- Suspicious MS Outlook Child Process
- System Shells via Services
- Unusual Parent-Child Relationship
- Windows Script Executing PowerShell
While all rules can be adjusted as needed, use care when adding exceptions to these rules. Exceptions could result in an undetected client-side execution, or a persistence or malware threat going unnoticed.
Examples of when these rules may create noise include:
- Receiving and opening email-attached Microsoft Office files, which include active content such as macros or scripts, from a trusted third-party source.
- Authorized technical support personnel who provide remote workers with scripts to gather troubleshooting information.
In these cases, exceptions can be added to the rules using the relevant process.name, user.name, and host.name conditions. Additionally, you can create duplicate rules with lower risk scores.
The definition of normal network behavior varies widely across different organizations. Different networks conform to different security policies, standards, and regulations. When normal network activity triggers alerts, network rules can be disabled or modified. For example:
- To exclude a specific source, add a
source.ipexception with the relevant IP address, and adestination.portexception with the relevant port number (source.ip is 196.1.0.12anddestination.port is 445). - To exclude source network traffic for an entire subnet, add a
source.ipexception with the relevant CIDR notation (source.ip is 192.168.0.0/16). - To exclude a destination IP for a specific destination port, add a
destination.ipexception with the IP address, and adestination.portexception with the port number (destination.ip is 38.160.150.31anddestination.port is 445) - To exclude a destination subnet for a specific destination port, add a
destination.ipexception using CIDR notation, and a ‘destination.port’ exception with the port number (destination.ip is 172.16.0.0/12anddestination.port is 445).
Take the following steps to tune indicator match rules:
- Specify a detailed query as part of the indicator index query. Results of the indicator index query are used by the detection engine to query the indices specified in your rule definition’s index pattern. Using no query or the wildcard
***query may result in your rule executing very large queries. - Limit your rule’s additional look-back time to as short a duration as possible, and no more than 24 hours.
- Avoid cluster performance issues by scheduling your rule to run in one-hour intervals or longer. For example, avoid scheduling an indicator match rule to check for indicators every five minutes.
Elastic Security provides limited support for indicator match rules. Visit support limitations for more information.
In cloud-based organizations, remote workers sometimes access services over the internet. The security policies of home networks probably differ from the security policies of managed corporate networks, and these rules might need tuning to reduce noise from legitimate administrative activities:
If your organization is widely distributed and the workforce travels a lot, use the windows_anomalous_user_name_ecs, linux_anomalous_user_name_ecs, and suspicious_login_activity_ecs machine learning jobs to detect suspicious authentication activity.