What is user behavior analytics (UBA)?
User Behavior Analytics (UBA) definition
User Behavior Analytics (UBA) is the practice of collecting and analyzing user activity data to create a baseline of their normal behavior patterns and preferences. By developing these baselines for each user and monitoring their real-time activity against it, UBA helps organizations spot irregularities. When suspicious behavior occurs, teams can identify potential security threats, unauthorized access attempts, and data breaches.
How does UBA work?
User behavior analytics works by collecting and analyzing user activity data in your system or network. Here is a quick overview of how it operates:
First, UBA gathers data on a user from various sources and regions across your IT environment, such as log files, network traffic, and application usage. UBA establishes a baseline of normal behavior for the user (including common activities and interactions that the user engages in as well as passive information such as the user's geographic location) through a process called behavioral profiling.
Next, UBA applies machine learning, statistical modeling, and other advanced analytics to detect deviations from the user's baseline or the behavior of peers that could indicate unauthorized access attempts and other security threats. It examines these anomalies to determine their potential risks, then assigns risk scores based on their severity.
If the anomaly detection exceeds the risk threshold of a detection rule, the technology alerts the security team, who can then investigate and respond to the potentially malicious activity.
UBA ensures users' baselines are not stagnant, constantly evolving to improve users behavioral profiles with each action. Machine learning constantly updates analytics by looking for new activity patterns and other new data. This helps it get better at spotting anomalies as time goes on.
Why is user behavior analytics important?
User behavior analytics helps organizations detect and respond to threats using user accounts, such as insider threats, compromised accounts, and privilege misuse and abuse. Indicators of insider threats and account takeover include:
- The user accessing a database they have never used before and downloading sensitive data
- The user downloading unusually large amounts of data
- The user exploring/accessing suspicious systems or applications
- The user’s behavior significantly differs from others who do the same job
UBA can detect external attackers and other outside threats as well. Some examples of external attacks include:
The user logging in from an unusual location, suggesting account compromise
- Brute force attacks, such as repeated failed login attempts or strange login patterns that may indicate an attacker attempting to gain access
- Suspicious network activity, such as command-and-control communication or data exfiltration attempts
- Other malicious behavior, such as attempts to escalate privileges, exploit vulnerabilities, or perform unauthorized actions
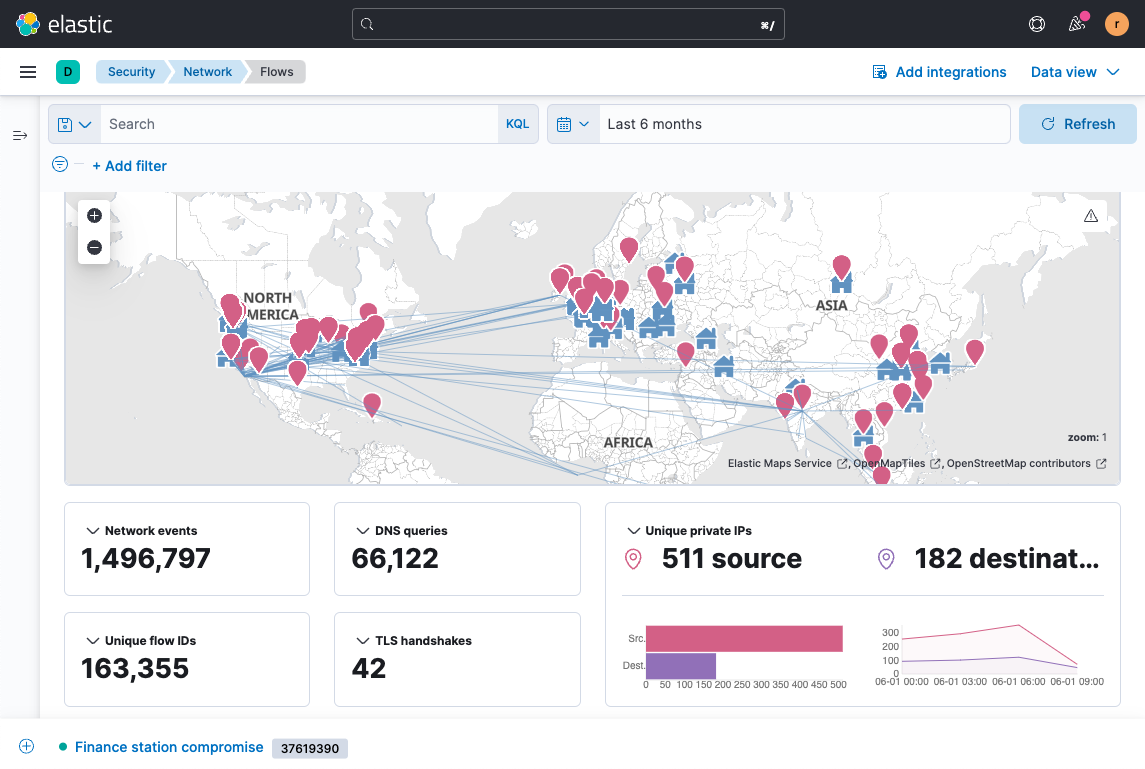
UBA allows teams to analyze user activities leading up to a security incident, understand the scope of the incident, and take appropriate actions to mitigate the impact. Analysts are provided evidence-based starting points for investigation, rich visualizations for effective analysis, and direct access to data for rapid response. By monitoring user behavior for policy violations, UBA can detect potential insider threats and also help your organization adhere to compliance requirements.
UEBA continually adapts based on changes in overall user patterns to fine-tune what triggers its alert threshold. For employees doing the same work, it creates peer-group comparisons, allowing detection of anomalies relative to peers. This way, shared changes in user profiles are less likely to present as anomalies requiring investigation and user accounts without enough data for a baseline can have their activity benchmarked against their peers.
What is User and Entity Behavior Analytics (UEBA)?
User and Entity Behavior Analytics (UEBA) is a cybersecurity concept that was coined by analyst firm Gartner in 2015. UEBA reflects an expansion of the goals of UBA.
UEBA broadens the intention of UBA by not only analyzing user behavior but also looking at the behavior of other entities within your system, such as devices and endpoints. UEBA evaluates the activity of users and entities to get a clear view of the overall security picture. By monitoring and correlating various data points, such as user behavior, host activity, and network traffic, UEBA identifies anomalies that could indicate malicious activity.
Both UBA and UEBA can be integrated with other security systems and tools, such as security information and event management (SIEM) systems, data loss prevention (DLP) solutions, and EDR. These integrations enhance your system’s overall security by giving you a more comprehensive, integrated view of threats and incidents.
What is the difference between UBA and Endpoint Detection Response (EDR)?
The difference between UBA and EDR is that endpoint detection and response is a cybersecurity solution that monitors and responds to security incidents at the endpoint level. Endpoints are laptops, servers, and other devices connected to a network. UBA, in contrast, focuses on analyzing and monitoring the behavioral patterns of individual users within a system or network.
EDR deploys sensors to these endpoints and collects data directly from them. EDR is designed to detect and respond to a wide range of endpoint-based threats, including malware infections and unauthorized access attempts. Security teams can use UBA and EDR in tandem as part of a defense-in-depth cybersecurity strategy.
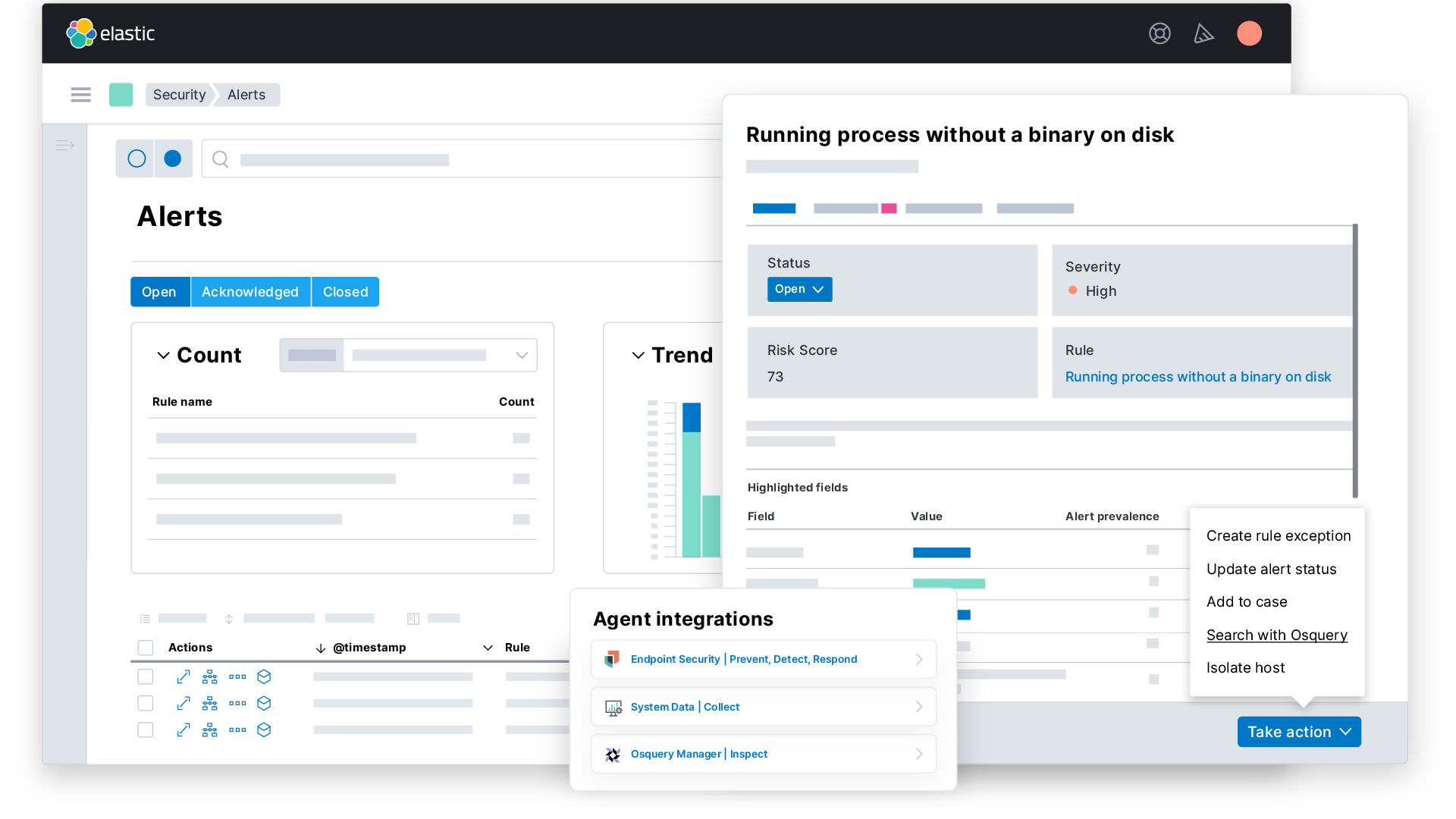
Challenges and limitations of user behavior analytics
There are a few challenges of user behavior analytics to consider:
- UBA relies on accurate and comprehensive data to generate meaningful insights. Having incomplete or inconsistent data sources or other data quality issues will limit its effectiveness.
- The disadvantage of UBA as a non-deterministic analytics tool means that it can’t be expected to detect every true positive.
- Conversely, UBA algorithms can produce false-positive alerts for normal user behavior. This can create unnecessary work for your team.
- You may encounter privacy and ethical concerns if you are collecting and analyzing user data for UBA. Your organization needs to make sure that proper consent and privacy measures are in place.
- UBA handles large volumes of data generated by all the users in your network. For ill-prepared technologies, processing and analyzing such vast amounts of data could strain system resources.
Your organization can overcome these challenges by investing time into proper data hygiene, normalization, and storage practices. Other priorities might include ensuring privacy compliance and combining UBA with other security measures for a comprehensive defense strategy.
Security with Elastic
Harness the state-of-the-art security analytics of Elastic Security to prevent, investigate, and respond to threats quickly and at scale. Elastic Security enables:
- Continuous monitoring: Collect and prepare data from across your digital environment, retain it indefinitely, and analyze it efficiently.
- Investigation and response: Give your team fast access to years of data, nimble workflows, and end-to-end collaboration capabilities.
- Automated threat protection: Reduce risk by monitoring and protecting your full digital environment in real time.
- Threat hunting: Get the speed, valuable insights, and rich context you need to hunt down surprise threats as well as expected ones.
Get started with Elastic Security today to protect your organization tomorrow.