What is Zero Trust?
Zero Trust definition
Zero Trust is a security framework based on the principle that users and devices should never be automatically or implicitly trusted, whether inside or outside an organization's network perimeter. By default, it assumes that every access request, regardless of its origin or location, should be strictly and continually verified and authenticated before granting or maintaining access to resources.
As cyber threats become increasingly sophisticated, traditional network security models no longer do enough to protect sensitive data and systems.
Zero Trust is a "never trust, always verify" approach to security. It is proven to be more effective than traditional network segmentation and perimeter-based defenses. It's a forward-looking strategy that provides protection for modern enterprises across complex hybrid cloud environments, local networks, and remote workers, as well as the devices, apps, data, and infrastructure they rely on — wherever they happen to be located.
What is Zero Trust Network Access (ZTNA)?
Zero Trust Network Access (ZTNA) is the fundamental component behind the Zero Trust model. It provides secure access to resources based on user identity and device posture, rather than relying on network location. ZTNA enables organizations to implement granular, defined access controls, providing users with the least privilege necessary to perform their tasks. By limiting user access to only the applications and services they need, the approach minimizes any potential attack surface and reduces the risk of unauthorized lateral movement — a common vulnerability exploited by cybercriminals.
ZTNA denies access by default and sets up one-to-one encrypted connections between devices and the resources they use. This provides secure remote access to specific applications and services while concealing most infrastructure and services. It also allows for location and device-specific access control policies to be implemented, preventing compromised devices from connecting to services.
Why Zero Trust matters
Zero Trust is important because it addresses the limitations of traditional network security models that rely on perimeter defense strategies like firewalls to protect vital data resources and infrastructure. Those traditional approaches aren’t equipped to tackle the rise of advanced threats, insider attacks, and the lateral movement of malicious actors within a network.
In a digital era defined by an increasingly global and disparate workforce, Zero Trust provides a proactive and adaptive security framework that focuses on continuous verification, reducing the risk of unauthorized access and data breaches. And with the growth of hybrid cloud infrastructure and infinitely complex data-driven environments, well-implemented Zero Trust strategies save security teams valuable time. Rather than expending resources managing a poorly integrated patchwork of security solutions and tools, enterprises and their IT teams can focus on the threats that are coming next.
Understanding Zero Trust principles
Zero Trust is founded on essential principles, but there’s no single standard, so their definitions and scope vary across different frameworks. For example, in the US, multiple guidance documents offer differing interpretations of these principles and pillars:
- Cybersecurity and Infrastructure Security Agency (CISA)
- National Institute of Standards and Technology (NIST)
- US Department of Defense (DoD)
- Government Services Administration (GSA)
While the concept of Zero Trust is interpreted differently across industries and organizations, most experts agree on a common set of core principles for the practical and effective deployment of Zero Trust strategy.
Most frameworks begin with three: continuous verification, least privilege access, and the assumption of breach. These provide the baseline, while broader principles expand the strategy to meet real-world demands.
Zero Trust key principles:
- Identity-based access control: Zero Trust emphasizes the importance of verifying and authenticating user identities before granting access to resources. User identities are the primary criteria for determining access privileges.
- Multifactor authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of verification, including passwords, biometrics, and security tokens.
- Microsegmentation: Microsegmentation divides networks into smaller sections, allowing organizations to enforce granular access controls. By limiting lateral movement within the network, Zero Trust minimizes the impact of potential breaches.
- Least privilege: Users are granted the least privilege necessary to perform their tasks. By restricting access rights, you minimize the risk of unauthorized access and data exposure. Limiting the scope of credentials and access paths to a potential attacker gives organizations more time to neutralize attacks.
- Continuous monitoring and validation: The continuous and active monitoring of user behavior, device health, and network traffic to detect anomalies and potential threats allows IT teams to respond rapidly to security events. Once established, logins and connections also periodically time out, requiring users and devices to be continuously reverified.
What are Zero Trust pillars?
The pillars of Zero Trust represent the core parts of a security strategy — from who can access information to how data is monitored and protected. Together, these pillars create a comprehensive framework that helps prevent threats and keep operations secure. Each pillar addresses a specific part of security, and when combined, they create a complete picture that protects an organization from inside and outside threats.
Zero Trust is traditionally defined around a set of core pillars. CISA's model, for example, includes five pillars: identity, devices, network, applications, and data, which represent the critical control points. Visibility, analytics, and automation are often seen as cross-functional elements rather than individual pillars — but that doesn't make them any less critical. They are embedded across the entire Zero Trust Architecture, connecting the dots and ensuring that each part of the system works in sync.
This isn't just theory — it's the same direction taken by respected public sector organizations like CISA, the US Department of Defense, UK’s National Cyber Security Centre (NCSC), and Australia's Cyber Security Centre (ACSC), among others.
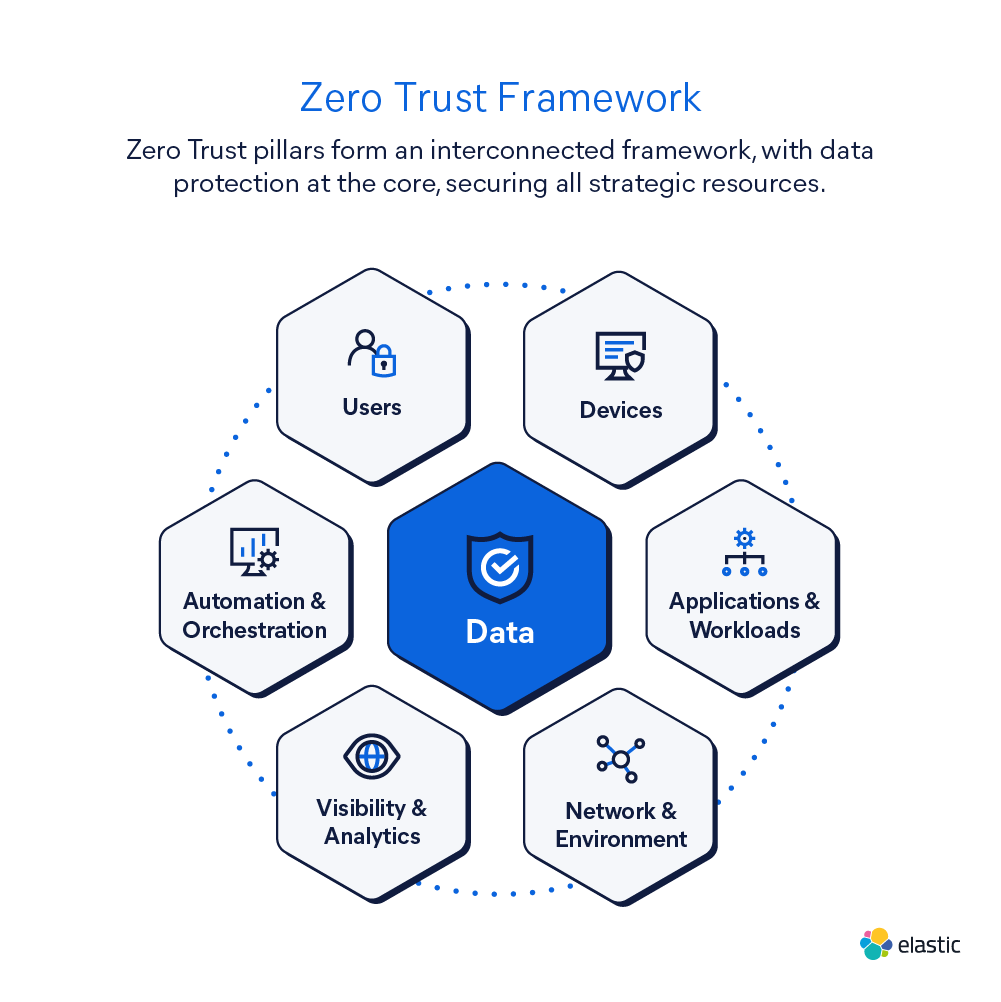
Data should ideally serve as the common, unifying element that connects all Zero Trust pillars. Each pillar — whether it's identity, devices, network, or applications — generates critical telemetry. Without bringing that data together, Zero Trust stays fragmented.
Data serves as the foundation to ensure that policies are informed, responses are accurate, and visibility is complete. It’s how organizations move from siloed controls to truly integrated security operations.
How Zero Trust works
Zero Trust requires continuous verification and monitoring. It relies on technologies and techniques like multifactor authentication (MFA), identity-based access control, micro-segmentation, robust end-point security, and continuous monitoring of user behavior and device health.
By combining these elements, Zero Trust ensures that access is only ever granted based on real-time trust evaluation, rather than the assumed trust of static credentials or network location. The Zero Trust model assumes a breach has already occurred or will occur, so users should never be granted access to sensitive information based on a single verification at the enterprise perimeter.
Zero Trust demands that each user, device, and application be continually verified. It authenticates and authorizes every connection and network flow, relying on a wide variety of data to maintain complete visibility.
The vast majority of attacks have traditionally involved the use or misuse of legitimate, compromised credentials within a network. Once inside a network’s perimeter, bad actors are able to wreak havoc across systems. With the explosive growth of cloud migration and remote work environments, Zero Trust represents a critical evolution of security models to combat today’s cyber threats.
How to implement a Zero Trust Architecture
The successful implementation of a Zero Trust Architecture requires an organization-wide commitment. That includes getting universal alignment on access policies, connecting information across security domains, and securing all connections across the organization.
Adopting Zero Trust effectively requires a systematic approach. Here are three key steps to help organizations transition to a Zero Trust security model:
- Step 1: Assess your existing network infrastructure and security posture to identify vulnerabilities. Defining your attack surface by evaluating weaknesses and discovering areas in need of improvement will help you gauge the scope of your Zero Trust implementation.
- Step 2: Develop a comprehensive access-control strategy based on the principles of Zero Trust. This includes cataloging all of your IT and data assets, defining and assigning user roles, implementing multifactor authentication, establishing granular access controls, and adopting network segmentation techniques.
- Step 3: Deploy the latest technologies and solutions to support your Zero Trust implementation. This may involve implementing identity and access management (IAM) solutions, intrusion detection systems, next-generation firewalls, and security information and event management (SIEM) tools. Regularly monitor and update these solutions to maintain a healthy Zero Trust security environment.
Benefits of adopting Zero Trust security
Zero Trust strategies can yield many benefits, including improved productivity, better end-user experiences, reduced IT costs, more flexible access, and, of course, significantly enhanced security. Adopting Zero Trust offers organizations:
- Improved security posture: At its core, by continuously verifying and monitoring access, Zero Trust reduces both the attack surface and the risk of unauthorized access, eliminating vulnerabilities baked into traditional perimeter-oriented protections.
- Reduced exposure to data breaches: Zero Trust's principle of least privilege and granular access controls limit user access rights, decreasing the likelihood of data breaches, lateral movement, and insider attacks.
- Enhanced visibility and control: Zero Trust provides organizations with precise, real-time visibility into user behavior, device health, and network traffic.
- Rapid response: Zero Trust enables faster threat detection and response.
- Damage mitigation: By restricting breaches to smaller areas through microsegmentation, Zero Trust minimizes the damage when attacks do occur, lowering the cost of recovery.
- Reduced risk and impact: By requiring multiple authentication factors, Zero Trust reduces the impact of phishing attacks and user credential theft. Enhanced verification reduces the risk posed by vulnerable devices, including IoT devices that are challenging to secure and update.
Common challenges of Zero Trust adoption
While Zero Trust offers significant security advantages, its adoption can come with growing pains. Common challenges include:
- Legacy infrastructure
Organizations with legacy systems may find it challenging to integrate Zero Trust principles into their existing network architectures. Legacy systems may lack the necessary capabilities to implement granular access controls and continuous monitoring. Adapting infrastructures built on implicit trust to align with Zero Trust principles requires both knowledge and investment. - User experience
Implementing robust authentication measures and access controls can impact user experience. To ensure a smooth transition to Zero Trust, organizations need to strike a balance between security needs and usability requirements. - Cultural changes
Zero Trust requires a shift in mindset and organizational culture. The transition away from outmoded "trust but verify" procedures can be met with resistance from users accustomed to more permissive access policies. Zero Trust can only be adopted with engagement, cooperation, and full buy-in from senior leadership, IT staff, data and system owners, and users across an organization. - Data silos and interoperability
Security data often resides in disconnected tools, platforms, or departments, making it difficult to unify insights across silos. This fragmentation limits the cross-pillar visibility needed for coordinated threat detection and effective interoperability. Without a single, unified data layer, it’s hard to see the full picture, identify risks, and enforce security policies effectively.
Zero Trust strategy use cases
A Zero Trust strategy can be adapted to meet the unique needs of most organizations. As Zero Trust gains traction across industries, the number of potential use cases continues to grow. Here are just a few examples:
- Securing remote workforces: With the increase in remote work arrangements, Zero Trust helps organizations secure access to corporate resources from potentially untrusted networks and devices.
- Cloud and multi-cloud environments: Zero Trust is well-suited for securing cloud-based applications and infrastructure, ensuring that only authorized users and devices gain access to critical cloud resources.
- Privileged access management: Zero Trust principles are particularly relevant for managing privileged access and mitigating risks associated with privileged accounts.
- Quickly onboarding third parties, contractors, and new employees: Zero Trust makes it easier to extend restricted, least-privilege access to external parties using outside devices not managed by internal IT teams.
Zero Trust with Elasticsearch
Elastic's Search AI Platform and data mesh approach can support the practical application of Zero Trust principles across an entire enterprise. Elastic provides a scalable data platform to bring together all layers of an organization's Zero Trust Architecture. By using Elastic as a unified data layer, you can collect and ingest data from different sources and formats, enabling efficient cross-correlation and analysis at scale in near real time.

Elastic facilitates one of the most foundational capabilities of any effective Zero Trust strategy: a common data operating and analytics layer that provides visibility across the entire architecture, as well as near real-time query and analytics on all relevant data streams. Elastic's uniquely powerful and flexible data platform connects all data and systems in a way that’s both cost-effective and scalable, resulting in a more integrated, accurate, and trustworthy environment.
Explore more Zero Trust resources
- Elastic Security Solution
- The missing piece of your Zero Trust strategy: A unified data layer
- Keeping data actionable in a Zero Trust Architecture
- Does your Zero Trust strategy have a unified data access layer?
- Elastic provides the foundation for the DoD’s pillars of Zero Trust Networking
- Understanding AI in government guide
- Data mesh in the public sector: Pillars, architecture, and examples
- Cybersecurity 101 guide