The importance of a unified observability solution in security implementation

Observability is critical for effective security implementation. It allows organizations to monitor their systems, applications, and networks in real-time; detect and investigate security incidents; and quickly respond to them. But having multiple tools and solutions for observability can create a fragmented view of the environment, making it difficult to gain a comprehensive understanding of the security posture and respond to threats effectively.
This is where a unified observability solution becomes essential for organizations. It consolidates all data sources into a single platform, allowing security teams to view and correlate data from across the entire infrastructure. This provides a complete picture of the environment and enables security teams to quickly identify and respond to security incidents.
A unified observability solution also enables security teams to create custom dashboards and alerts that provide them with real-time visibility into the security posture. This helps teams to identify potential issues before they become critical and respond to incidents faster.
In this article, we will explore the relationship between observability and security and how they complement each other in helping technology leaders and their organizations create a more robust and secure software environment.
Securing assets through observability
Observability can augment asset visibility and control by providing a more comprehensive view of the systems and applications that are running on those assets. With observability, organizations can gain insights into the performance, health, and behavior of their assets and applications, including metrics, logs, traces, and other telemetry data.
This increased visibility can help organizations to identify and mitigate potential issues and risks, such as security vulnerabilities, performance bottlenecks, and compliance violations. Additionally, observability can provide a more granular level of control over assets by enabling organizations to monitor and manage specific components and processes, rather than just the overall system.
By combining asset visibility and control with observability, organizations can gain a more complete understanding of their digital infrastructure, which can help them to optimize performance, reduce downtime, and improve security posture. This, in turn, can help to ensure that assets are utilized effectively and efficiently, while also minimizing risks and maximizing return on investment.
The intersection of observability and security in the software supply chain
Observability and security are two critical components of modern software systems that are becoming increasingly intertwined. Observability refers to the ability to monitor and understand the behavior of complex systems, while security involves protecting these systems from unauthorized access, manipulation, or disruption. The crossover of observability and security is a natural consequence of the increasing complexity of software systems and the growing sophistication of cyber threats.
Observability can play a critical role in augmenting software supply chains. By providing real-time visibility into the performance and behavior of software systems throughout the development and deployment process, observability can help ensure that software is delivered on time and meets the expected level of quality.
In addition, observability can help improve security by providing real-time insights into potential security threats and vulnerabilities. By monitoring key security metrics, such as login attempts, network traffic, and system logs, observability can help identify and prevent security breaches before they occur. This can help ensure that software systems are secure and reliable and can help prevent costly data breaches or other security incidents.
Observability can also provide insights into user patterns and behavior, which also assist with User Entity and Behaviour Analytics (UBEA), an important part of a sound security system.
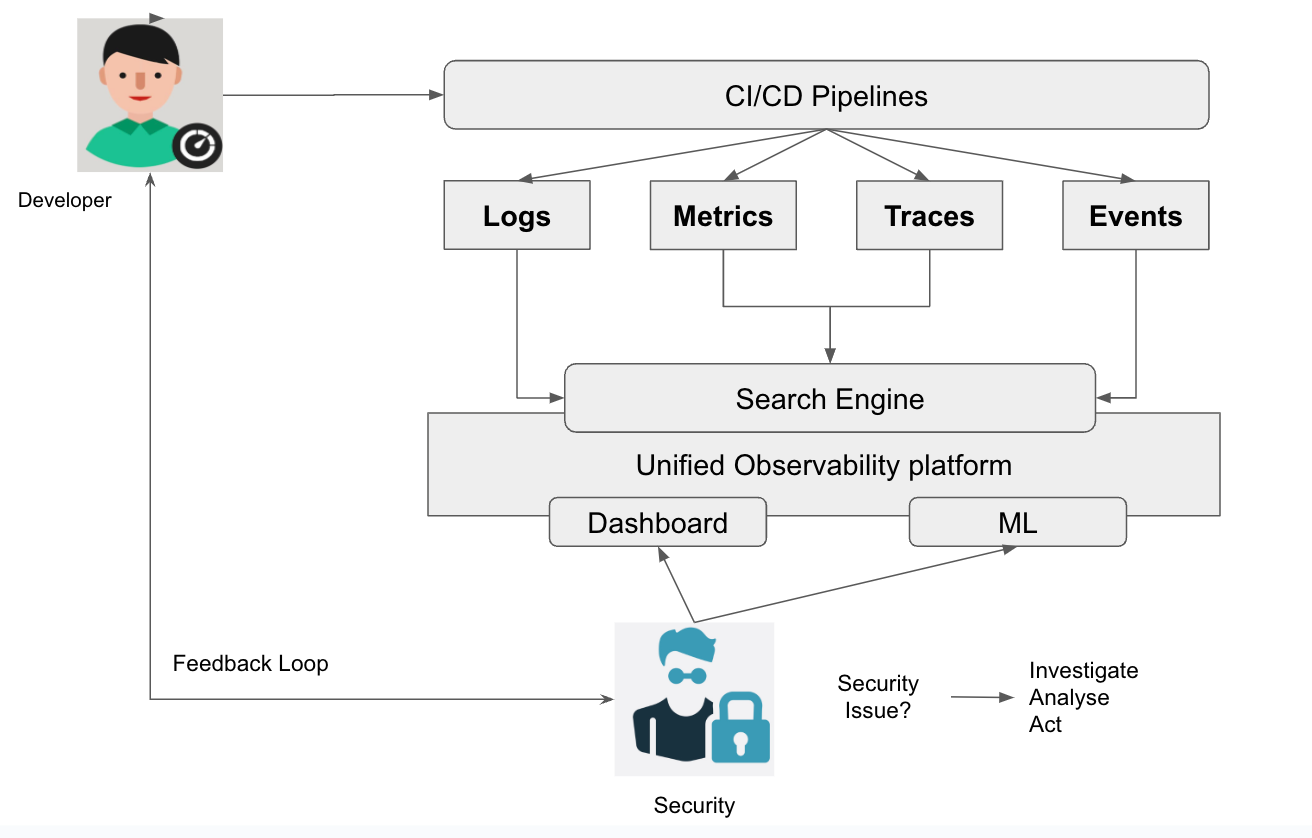
Observability and security: The connection
Observability is essential for detecting, diagnosing, and resolving issues in software systems. It provides visibility into the system's internal state, including its performance, behavior, and interactions with other systems. This information is crucial for identifying problems, optimizing performance, and ensuring the system meets its service level objectives (SLOs).
Security, on the other hand, is focused on protecting software systems from malicious attacks that could result in data breaches, system downtime, or other types of damage. Security measures typically include access controls, encryption, firewalls, intrusion detection and prevention systems (IDS/IPS), and other security-related tools and processes.
While observability and security may seem like separate concerns, they are, in fact, closely linked. Observability is critical for security because it provides visibility into the system's behavior and helps identify anomalous activity that could indicate a security breach. Conversely, security is essential for observability because it protects the system from attacks that could compromise its observability, such as denial-of-service (DoS) attacks or data exfiltration attempts.
For example, suppose a company's observability tools detect an unusual spike in network traffic. In that case, it may indicate a DoS attack, which could be mitigated by implementing security measures such as rate limiting or deploying a web application firewall (WAF). Similarly, security measures such as encryption and access controls can help ensure that observability data remains confidential and is only accessible to authorized personnel.
Observability-driven security
Observability can be used to enhance security in several ways. One approach is to use observability data to detect and respond to security incidents in real-time. For example, by analyzing logs, network traffic, and other observability data, security teams can detect signs of a data breach or other security incident and respond quickly to contain the damage.
Another approach is to use observability data to improve security posture over time. By analyzing observability data, security teams can identify areas of the system that are particularly vulnerable to attack and take steps to improve their security posture.
This is where using machine learning (ML) to enable faster detection and response to security threats comes in very handy. Using ML on your observability implementation provides security teams with tools that they need to analyze and respond to security incidents with ease.
ML helps security teams by reducing manual work and inconsistencies by providing a programmatic approach for:
- Anomaly detection
- Predictive modeling
- Data analysis
- Automated response
For example, if observability data indicates that a particular application is consistently generating errors, it may be a sign that the application has security vulnerabilities that need to be addressed.
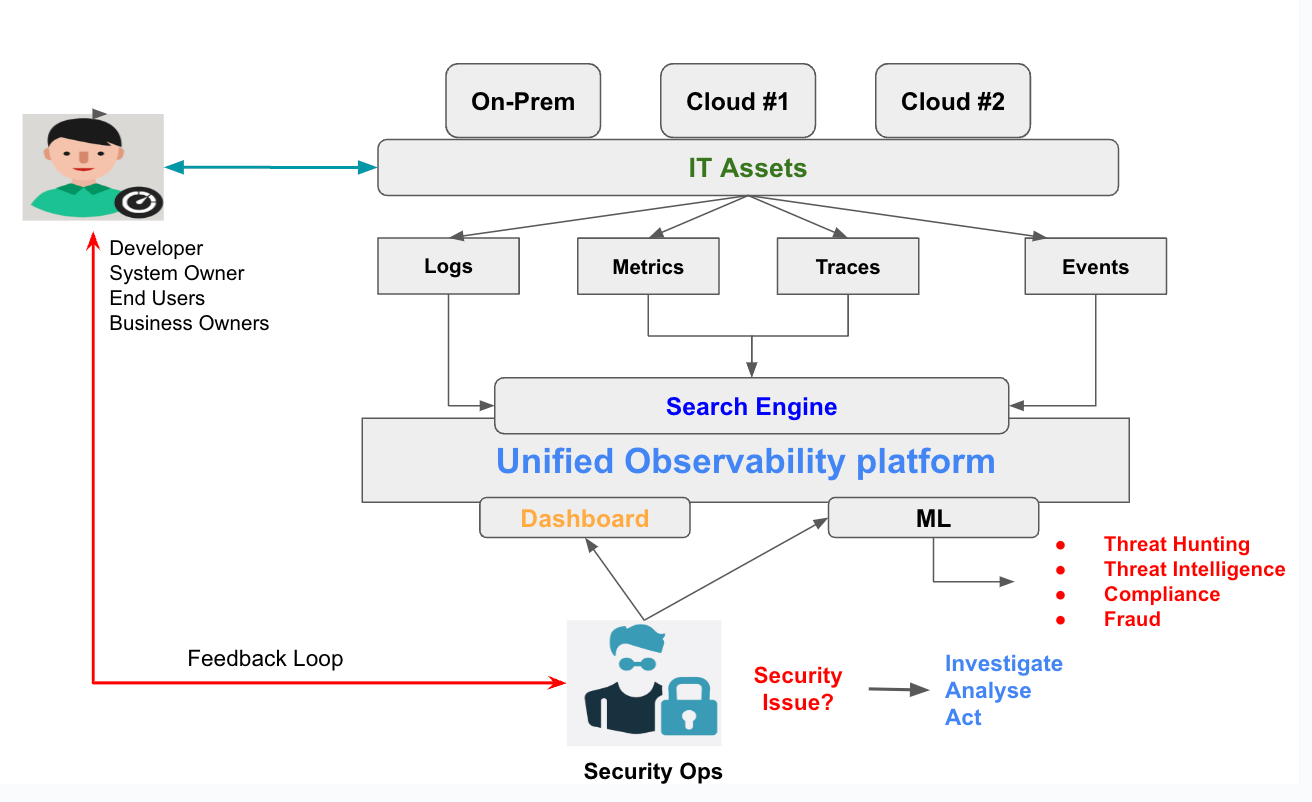
Observability can also help with an incident response by providing valuable context about the system's behavior leading up to the incident. For example, if a security incident results in a system outage, observability data can be used to reconstruct the sequence of events leading up to the outage and identify the root cause of the problem.
Where to go from here?
A unified observability solution provides a comprehensive view of the environment, simplifies the process of analyzing security data, and enables security teams to respond to incidents quickly and effectively.
Observability and security are closely linked because observability data can be used to enhance security posture, detect and respond to security incidents in real time, and provide valuable context for incident response. As software systems continue to grow in complexity and cyber threats become more sophisticated, the crossover of observability and security will only become more important in creating a more robust and secure IT environment.

