Elastic Security 7.16: Accelerate SecOps with the most powerful Elastic Security yet

In Elastic Security 7.16, multiple new out-of-the-box data integrations for Elastic Agent streamline data ingestion and normalization, powering security operations. The release also introduces full production support for several existing data integrations.
Version 7.16 introduces an expanded set of malicious behavior protections, addressing methods related to initial access, privilege escalation, and defense evasion. It also brings memory threat protection to macOS and Linux, and enhances ECS support for Osquery Manager.
Plus, it powers cross-org collaboration with certified integrations for ServiceNow.
Let’s jump in.
Amplify visibility to accelerate detection and response
Expansive environmental activity and context powers the work of modern security teams, but onboarding data at unthrottled scale — from distributed sources, in diverse formats — can be challenging. Elastic Agent delivers visibility across the attack surface. It’s centrally managed, supports every major operating system, and is covered by the Elastic license, so you can take your deployment global.
New sources of valuable security data
Elastic Security 7.16 ships with new out-of-the-box data integrations — including multiple community-developed and Elastic-validated integrations — that simplify collection and automate normalization with the Elastic Common Schema (ECS), propelling cross-telemetry detection, investigation, and response.
AWS WAF data extends cloud visibility and spots everything from common web exploits to advanced threats.
Cisco Duo events surface authentications throughout the enterprise, powering security analytics.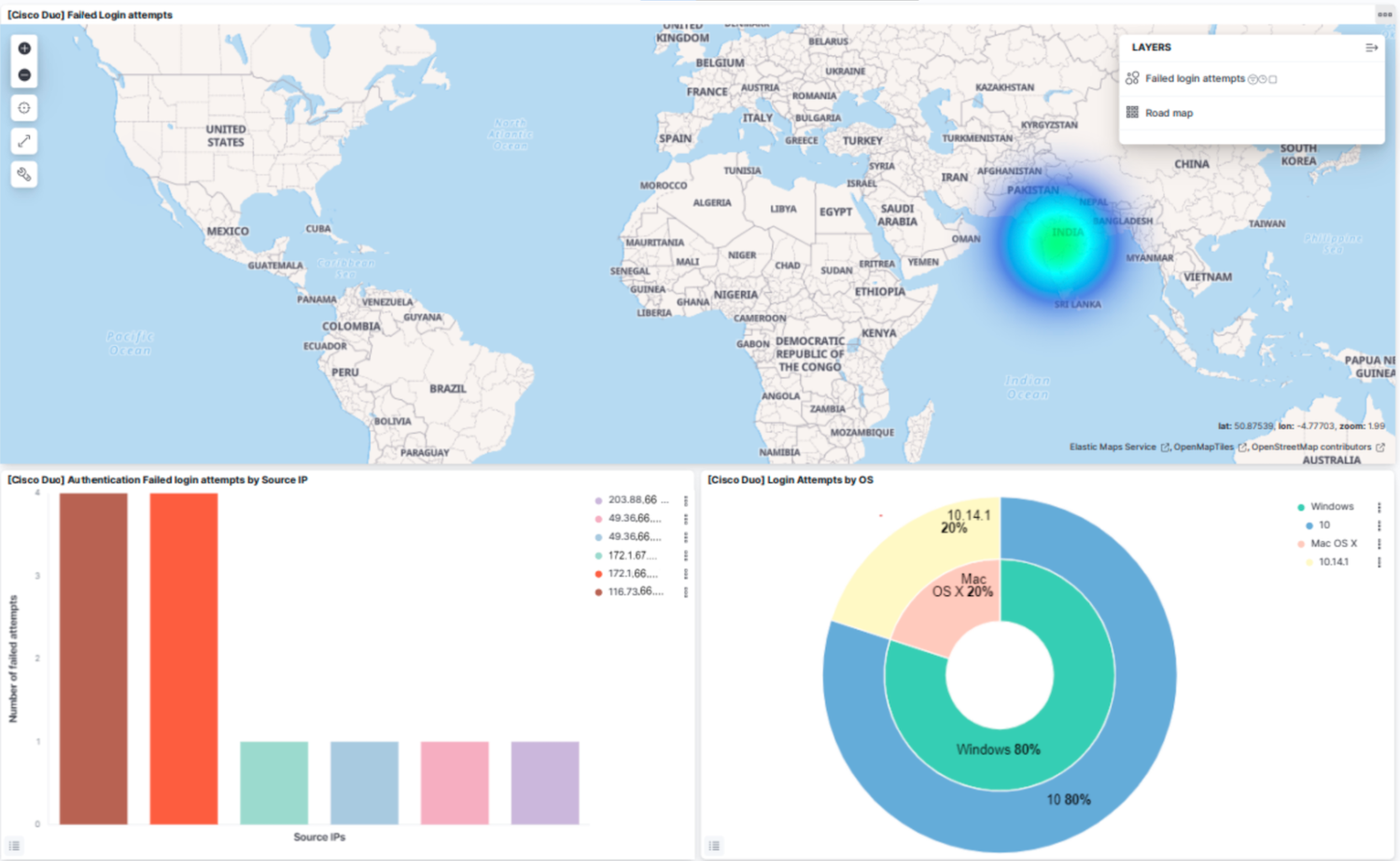
1Password events show authentication attempts, password usage, and other high-stakes activity, enabling cross-environment analysis.
Elastic Agent integrations with production-ready support
The 7.16 release also brings numerous prebuilt Elastic Agent data integrations into general availability, ensuring production-ready support.
Security data sources: Common Event Format (CEF), Check Point firewalls, Cloudflare CDN, CrowdStrike Falcon EDR, CyberArk PAS, Google Cloud Platform (audit logs, firewall logs, VPC flows), Google Workspace, HashiCorp Vault, Juniper SRX, osquery logs, Microsoft Defender for Endpoint, Sophos XG and UTM, custom Windows event logs, ZeroFox platform alerts, and Zoom.
Infrastructure, datastore, and application sources: The 7.16 release also marks the general availability of several security-relevant observability technologies, enabling monitoring via granular analysis of data from DevOps tools (e.g., Docker, Kubernetes, Nginx, Traefik), datastores (e.g., Cassandra, MongoDB, MySQL, PostgreSQL, Redis), and more. Learn more in the Elastic Observability 7.16 blog.
Secure every endpoint with layered protections
Elastic Security autonomously fights back at every stage of the attack lifecycle, applying multiple layers of endpoint prevention and detection — and demonstrating the rapid advancement of Elastic Agent.
Feature | Windows | macOS | Linux |
Malicious behavior protection | Enhanced ↗ | Enhanced ↗ | Enhanced ↗ |
Memory threat protection | Existing ✓ | New + | New + |
Behavioral ransomware prevention | Existing ✓ | Existing ✓ | Existing ✓ |
Malware & ransomware prevention | Existing ✓ | Existing ✓ | Existing ✓ |
Centralized osquery host inspection | Enhanced ↗ | Enhanced ↗ | Enhanced ↗ |
Host response actions | Existing ✓ | Existing ✓ | Existing ✓ |
Centralized detection with host data | Existing ✓ | Existing ✓ | Existing ✓ |
Expanded malicious behavior protections at the endpoint
Elastic Security 7.16 extends malicious behavior prevention — which pairs post-execution behavior analytics with targeted response actions — to stop an expanded set of advanced attack techniques. All analytics are mapped to the MITRE ATT&CK® framework, addressing methods related to initial access, privilege escalation, and defense evasion, including:
- Phishing with a spearphishing attachment, wherein an attacker drops an initial payload via a malicious document or shortcut
- Signed binary proxy execution, leveraging commonly abused living off the land (LotL) binaries and scripts
- Privilege escalation via UAC bypass, which allows adversaries to bypass Windows User Account Control to elevate privileges
These capabilities build on the malicious behavior preventions introduced in Elastic Security 7.15 to stop various techniques for phishing, credential theft, LotL, and achieving advanced persistence.
Memory threat protection for Linux and macOS
The release adds memory threat protection for macOS and Linux systems, uncovering methods sometimes used by advanced threats to evade traditional defenses. It ships with preventions for shellcode (macOS and Linux), reflective ELF injection (Linux), and in-memory Mach-O execution (macOS), plus the preventions for Windows systems delivered in version 7.15.
Osquery Manager now generally available
Elastic Security 7.16 enhances the Osquery Manager integration for Elastic Agent and advances it into general availability, ensuring production-ready support. Osquery Manager equips hunters and investigators with real-time visibility into system data, like running processes, loaded kernel modules, open network connections, and more.
Practitioners can now map saved queries results directly to ECS to return normalized data, ready for immediate analysis.
The release enables administrators to customize the configuration of key settings, such as files paths to monitor and table views, enabling use cases like file integrity monitoring and process auditing.
Streamline workflows with certified ServiceNow integrations
Threats are growing in number and sophistication, and experienced practitioners remain scarce, so it’s vital to maximize the productivity of each analyst. Elastic Security addresses this challenge head-on by eliminating the operational inefficiencies caused by data silos and providing a uniquely effective investigation UI, built-in case management, and a growing set of external workflow integrations.
Elastic Security 7.16 delivers certified applications for ServiceNow Security Incident Response (SIR) and ServiceNow IT Service Management (ITSM), plus a new integration for ServiceNow IT Operations Management (ITOM):
- Elastic + ServiceNow SIR maximizes security analyst efficiency with security orchestration, automation, and response (SOAR).
- Elastic + ServiceNow ITSM coordinates the workload and processes of modern IT teams.
- Elastic + ServiceNow ITOM maximizes uptime by powering proactive IT operations with machine learning.
The SIR and ITSM applications connect with two core Elastic Security functions — alerting and case management — while the new ITOM integration connects with alerting. These connections accelerate investigation and response, reducing risk and raising practitioner productivity:
- Alerting, a core feature of Elastic Security, shortens the interval between threat detection and response initiation. Linking the Elastic alerting workflow with ServiceNow configures Elastic to automatically forward alerts, initiating applicable ServiceNow workflows.
- Case management, also built into Elastic Security, helps standardize and streamline response efforts. Linking the Elastic case management enables analysts to escalate Elastic cases (including case details, data observables, analyst notes, and associated alarms) to ServiceNow in just one click.
Does your organization leverage a different SOAR or ticketing workflow tool? Explore our case management integrations and alerting connectors.
Try it out
Existing Elastic Cloud customers can access many of these features directly from the Elastic Cloud console. If you’re new to Elastic Cloud, take a look at our Quick Start guides (bite-sized training videos to get you started quickly) or our free fundamentals training courses. You can always get started with a free 14-day trial of Elastic Cloud. Or download the self-managed version of the Elastic Stack for free.
Read about these capabilities and more in the Elastic Security 7.16 release notes, and other Elastic Stack highlights in the Elastic 7.16 announcement post.The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.

