- Elasticsearch Guide: other versions:
- Getting Started
- Set up Elasticsearch
- Installing Elasticsearch
- Configuring Elasticsearch
- Important Elasticsearch configuration
- Important System Configuration
- Bootstrap Checks
- Heap size check
- File descriptor check
- Memory lock check
- Maximum number of threads check
- Max file size check
- Maximum size virtual memory check
- Maximum map count check
- Client JVM check
- Use serial collector check
- System call filter check
- OnError and OnOutOfMemoryError checks
- Early-access check
- G1GC check
- All permission check
- Starting Elasticsearch
- Stopping Elasticsearch
- Adding nodes to your cluster
- Installing X-Pack
- Set up X-Pack
- Configuring X-Pack Java Clients
- X-Pack Settings
- Bootstrap Checks for X-Pack
- Upgrade Elasticsearch
- API Conventions
- Document APIs
- Search APIs
- Aggregations
- Metrics Aggregations
- Avg Aggregation
- Weighted Avg Aggregation
- Cardinality Aggregation
- Extended Stats Aggregation
- Geo Bounds Aggregation
- Geo Centroid Aggregation
- Max Aggregation
- Min Aggregation
- Percentiles Aggregation
- Percentile Ranks Aggregation
- Scripted Metric Aggregation
- Stats Aggregation
- Sum Aggregation
- Top Hits Aggregation
- Value Count Aggregation
- Bucket Aggregations
- Adjacency Matrix Aggregation
- Children Aggregation
- Composite Aggregation
- Date Histogram Aggregation
- Date Range Aggregation
- Diversified Sampler Aggregation
- Filter Aggregation
- Filters Aggregation
- Geo Distance Aggregation
- GeoHash grid Aggregation
- Global Aggregation
- Histogram Aggregation
- IP Range Aggregation
- Missing Aggregation
- Nested Aggregation
- Range Aggregation
- Reverse nested Aggregation
- Sampler Aggregation
- Significant Terms Aggregation
- Significant Text Aggregation
- Terms Aggregation
- Pipeline Aggregations
- Avg Bucket Aggregation
- Derivative Aggregation
- Max Bucket Aggregation
- Min Bucket Aggregation
- Sum Bucket Aggregation
- Stats Bucket Aggregation
- Extended Stats Bucket Aggregation
- Percentiles Bucket Aggregation
- Moving Average Aggregation
- Moving Function Aggregation
- Cumulative Sum Aggregation
- Bucket Script Aggregation
- Bucket Selector Aggregation
- Bucket Sort Aggregation
- Serial Differencing Aggregation
- Matrix Aggregations
- Caching heavy aggregations
- Returning only aggregation results
- Aggregation Metadata
- Returning the type of the aggregation
- Metrics Aggregations
- Indices APIs
- Create Index
- Delete Index
- Get Index
- Indices Exists
- Open / Close Index API
- Shrink Index
- Split Index
- Rollover Index
- Put Mapping
- Get Mapping
- Get Field Mapping
- Types Exists
- Index Aliases
- Update Indices Settings
- Get Settings
- Analyze
- Index Templates
- Indices Stats
- Indices Segments
- Indices Recovery
- Indices Shard Stores
- Clear Cache
- Flush
- Refresh
- Force Merge
- cat APIs
- Cluster APIs
- Query DSL
- Mapping
- Analysis
- Anatomy of an analyzer
- Testing analyzers
- Analyzers
- Normalizers
- Tokenizers
- Standard Tokenizer
- Letter Tokenizer
- Lowercase Tokenizer
- Whitespace Tokenizer
- UAX URL Email Tokenizer
- Classic Tokenizer
- Thai Tokenizer
- NGram Tokenizer
- Edge NGram Tokenizer
- Keyword Tokenizer
- Pattern Tokenizer
- Char Group Tokenizer
- Simple Pattern Tokenizer
- Simple Pattern Split Tokenizer
- Path Hierarchy Tokenizer
- Path Hierarchy Tokenizer Examples
- Token Filters
- Standard Token Filter
- ASCII Folding Token Filter
- Flatten Graph Token Filter
- Length Token Filter
- Lowercase Token Filter
- Uppercase Token Filter
- NGram Token Filter
- Edge NGram Token Filter
- Porter Stem Token Filter
- Shingle Token Filter
- Stop Token Filter
- Word Delimiter Token Filter
- Word Delimiter Graph Token Filter
- Multiplexer Token Filter
- Stemmer Token Filter
- Stemmer Override Token Filter
- Keyword Marker Token Filter
- Keyword Repeat Token Filter
- KStem Token Filter
- Snowball Token Filter
- Phonetic Token Filter
- Synonym Token Filter
- Synonym Graph Token Filter
- Compound Word Token Filters
- Reverse Token Filter
- Elision Token Filter
- Truncate Token Filter
- Unique Token Filter
- Pattern Capture Token Filter
- Pattern Replace Token Filter
- Trim Token Filter
- Limit Token Count Token Filter
- Hunspell Token Filter
- Common Grams Token Filter
- Normalization Token Filter
- CJK Width Token Filter
- CJK Bigram Token Filter
- Delimited Payload Token Filter
- Keep Words Token Filter
- Keep Types Token Filter
- Exclude mode settings example
- Classic Token Filter
- Apostrophe Token Filter
- Decimal Digit Token Filter
- Fingerprint Token Filter
- Minhash Token Filter
- Remove Duplicates Token Filter
- Character Filters
- Modules
- Index Modules
- Ingest Node
- Pipeline Definition
- Ingest APIs
- Accessing Data in Pipelines
- Handling Failures in Pipelines
- Processors
- Append Processor
- Bytes Processor
- Convert Processor
- Date Processor
- Date Index Name Processor
- Fail Processor
- Foreach Processor
- Grok Processor
- Gsub Processor
- Join Processor
- JSON Processor
- KV Processor
- Lowercase Processor
- Remove Processor
- Rename Processor
- Script Processor
- Set Processor
- Split Processor
- Sort Processor
- Trim Processor
- Uppercase Processor
- Dot Expander Processor
- URL Decode Processor
- SQL Access
- Monitor a cluster
- Rolling up historical data
- Secure a cluster
- Overview
- Configuring Security
- Encrypting communications in Elasticsearch
- Encrypting Communications in an Elasticsearch Docker Container
- Enabling cipher suites for stronger encryption
- Separating node-to-node and client traffic
- Configuring an Active Directory realm
- Configuring a file realm
- Configuring an LDAP realm
- Configuring a native realm
- Configuring a PKI realm
- Configuring a SAML realm
- Configuring a Kerberos realm
- FIPS 140-2
- Security settings
- Auditing settings
- Getting started with security
- How security works
- User authentication
- Built-in users
- Internal users
- Realms
- Active Directory user authentication
- File-based user authentication
- LDAP user authentication
- Native user authentication
- PKI user authentication
- SAML authentication
- Kerberos authentication
- Integrating with other authentication systems
- Enabling anonymous access
- Controlling the user cache
- Configuring SAML single-sign-on on the Elastic Stack
- User authorization
- Auditing security events
- Encrypting communications
- Restricting connections with IP filtering
- Cross cluster search, tribe, clients, and integrations
- Reference
- Troubleshooting
- Can’t log in after upgrading to 6.4.3
- Some settings are not returned via the nodes settings API
- Authorization exceptions
- Users command fails due to extra arguments
- Users are frequently locked out of Active Directory
- Certificate verification fails for curl on Mac
- SSLHandshakeException causes connections to fail
- Common SSL/TLS exceptions
- Common Kerberos exceptions
- Common SAML issues
- Internal Server Error in Kibana
- Setup-passwords command fails due to connection failure
- Failures due to relocation of the configuration files
- Limitations
- Alerting on Cluster and Index Events
- X-Pack APIs
- Info API
- Explore API
- Licensing APIs
- Migration APIs
- Machine Learning APIs
- Add Events to Calendar
- Add Jobs to Calendar
- Close Jobs
- Create Calendar
- Create Datafeeds
- Create Filter
- Create Jobs
- Delete Calendar
- Delete Datafeeds
- Delete Events from Calendar
- Delete Filter
- Delete Jobs
- Delete Jobs from Calendar
- Delete Model Snapshots
- Flush Jobs
- Forecast Jobs
- Get Calendars
- Get Buckets
- Get Overall Buckets
- Get Categories
- Get Datafeeds
- Get Datafeed Statistics
- Get Influencers
- Get Jobs
- Get Job Statistics
- Get Model Snapshots
- Get Scheduled Events
- Get Filters
- Get Records
- Open Jobs
- Post Data to Jobs
- Preview Datafeeds
- Revert Model Snapshots
- Start Datafeeds
- Stop Datafeeds
- Update Datafeeds
- Update Filter
- Update Jobs
- Update Model Snapshots
- Rollup APIs
- Security APIs
- Create or update application privileges API
- Authenticate API
- Change passwords API
- Clear Cache API
- Create or update role mappings API
- Clear roles cache API
- Create or update roles API
- Create or update users API
- Delete application privileges API
- Delete role mappings API
- Delete roles API
- Delete users API
- Disable users API
- Enable users API
- Get application privileges API
- Get role mappings API
- Get roles API
- Get token API
- Get users API
- Has Privileges API
- Invalidate token API
- SSL Certificate API
- Watcher APIs
- Definitions
- Command line tools
- How To
- Testing
- Glossary of terms
- Release Highlights
- Breaking changes
- Release Notes
- Elasticsearch version 6.4.3
- Elasticsearch version 6.4.2
- Elasticsearch version 6.4.1
- Elasticsearch version 6.4.0
- Elasticsearch version 6.3.2
- Elasticsearch version 6.3.1
- Elasticsearch version 6.3.0
- Elasticsearch version 6.2.4
- Elasticsearch version 6.2.3
- Elasticsearch version 6.2.2
- Elasticsearch version 6.2.1
- Elasticsearch version 6.2.0
- Elasticsearch version 6.1.4
- Elasticsearch version 6.1.3
- Elasticsearch version 6.1.2
- Elasticsearch version 6.1.1
- Elasticsearch version 6.1.0
- Elasticsearch version 6.0.1
- Elasticsearch version 6.0.0
- Elasticsearch version 6.0.0-rc2
- Elasticsearch version 6.0.0-rc1
- Elasticsearch version 6.0.0-beta2
- Elasticsearch version 6.0.0-beta1
- Elasticsearch version 6.0.0-alpha2
- Elasticsearch version 6.0.0-alpha1
- Elasticsearch version 6.0.0-alpha1 (Changes previously released in 5.x)
HipChat action
editHipChat action
editUse the hipchat action to send messages to HipChat
rooms or users. To send HipChat messages, you must
configure at least one HipChat account in elasticsearch.yml.
Configuring HipChat actions
editYou configure HipChat actions in a actions array. Action-specific attributes
are specified using the hipchat keyword. You must specify the message
attribute for all hipchat actions. If you omit the account attribute, the
message is sent using the default HipChat account configured in
elasticsearch.yml.
For example, the following action is configured to send messages using a HipChat account that uses the integration profile. Because this type of account can only send messages to a specific room, the only required attribute is the message itself:
"actions" : { "notify-hipchat" : { "transform" : { ... }, "throttle_period" : "5m", "hipchat" : { "account" : "integration-account", "message" : { "body" : "Encountered {{ctx.payload.hits.total}} errors in the last 5 minutes (facepalm)", "format" : "text", "color" : "red", "notify" : true } } } }
|
The name of a HipChat account configured in |
|
|
The message you want to send to HipChat. |
To send messages with a HipChat account that uses the user
profile, you need to specify what rooms and users you want to send the message to.
For example, the following action is configured to send messages to the
mission-control and devops rooms as well as the user website-admin@example.com.
(To send to multiple users or rooms, specify an array of strings):
"actions" : { "notify-hipchat" : { "transform" : { ... }, "throttle_period" : "5m", "hipchat" : { "account" : "user-account", "message" : { "room" : [ "mission-control", "devops" ], "user" : "website-admin@example.com", "body" : "Encountered {{ctx.payload.hits.total}} errors in the last 5 minutes (facepalm)", "format" : "text", "color" : "red", "notify" : true } } } }
To send messages with a HipChat account that uses the v1
profile, you need to specify what room or rooms you want to send the message to.
For example, the following action is configured to send messages to the
server-status room. (To send to multiple rooms, specify an array of strings.)
"actions" : { "notify-hipchat" : { "transform" : { ... }, "throttle_period" : "5m", "hipchat" : { "account" : "v1-account", "message" : { "from" : "Watcher", "room" : [ "server-status", "infra-team" ], "body" : "Encountered {{ctx.payload.hits.total}} errors in the last 5 minutes (facepalm)", "format" : "text", "color" : "red", "notify" : true } } } }
HipChat action attributes
edit| Name | Required | Default | Description |
|---|---|---|---|
|
no |
Default account |
The HipChat account to use to send the message. |
|
no |
- |
The proxy host to use (only in combination with |
|
no |
- |
The proxy port to use (only in combination with |
|
yes |
- |
The message content. Can contain up to 1000 characters. |
|
no |
html |
The format of the message: |
|
no |
yellow |
The background color of the notification in the room:
|
|
no |
false |
Indicates whether people in the room should be actively notified |
|
no |
the watch ID |
The name that appears as the notification sender. Only valid for accounts that use the v1 profile. |
|
no |
- |
The rooms that the notification should go to. Accepts
a string value or an array of string values. Must be
specified when using the v1 profile. At least one room
or user must be specified when using the |
|
no |
- |
The users that the notification should go to. Accepts
a string value or an array of string values. At least
one room or user must be specified when using the |
Configuring HipChat accounts
editYou configure the accounts Watcher can use to communicate with HipChat in the
xpack.notification.hipchat namespace in elasticsearch.yml. Both
v1 and
v2 HipChat APIs are supported.
Watcher provides three HipChat API profiles:
- integration
- Sends messages to a specific room using HipChat’s v2 API Send room notification.
- user
- Sends messages as a particular user through the HipChat v2 API. Enables you to send messages to arbitrary rooms or users.
- v1
-
Sends messages to rooms using HipChat’s v1 API rooms/message.
The
v1profile is provided because it is simple to set up and this API is familiar to many users. That said, HipChat has deprecated the v1 API and is encouraging users to migrate to v2. Both theintegrationanduserprofiles are based on the HipChat v2 API.
If you configure multiple HipChat accounts, you either need to set a default HipChat account or specify which account the notification should be sent with in the hipchat action.
Storing the auth_token in the configuration file or using via updating the
settings now is still supported, but you should use the keystore for this, see
Secure settings.
xpack.notification.hipchat: default_account: team1 account: team1: ... team2: ...
Using the Hipchat integration profile
editYou can use the integration profile to send messages to specific rooms. When
you set an account’s profile to integration, the messages are sent through
HipChat’s v2
Send room notification API.
When you use the integration profile, you need to configure a separate HipChat
account for each room you want to send messages—the account configuration
contains a room-specific authentication token. Alternatively, you can use the
user or v1 profile to send messages
to multiple rooms.
The integration profile only supports sending messages to rooms, it does
not support sending private messages. Use the user
profile to notify a particular HipChat user.
You need a room-specific authentication token to configure an integration
account. To generate an authentication token:
- Log in to hipchat.com or your HipChat server as a group administrator.
- Go to Group admin > Rooms.
- Click the name of the room you want to send messages to.
- Click the Tokens link.
-
Enter a name for the token in the Label field.
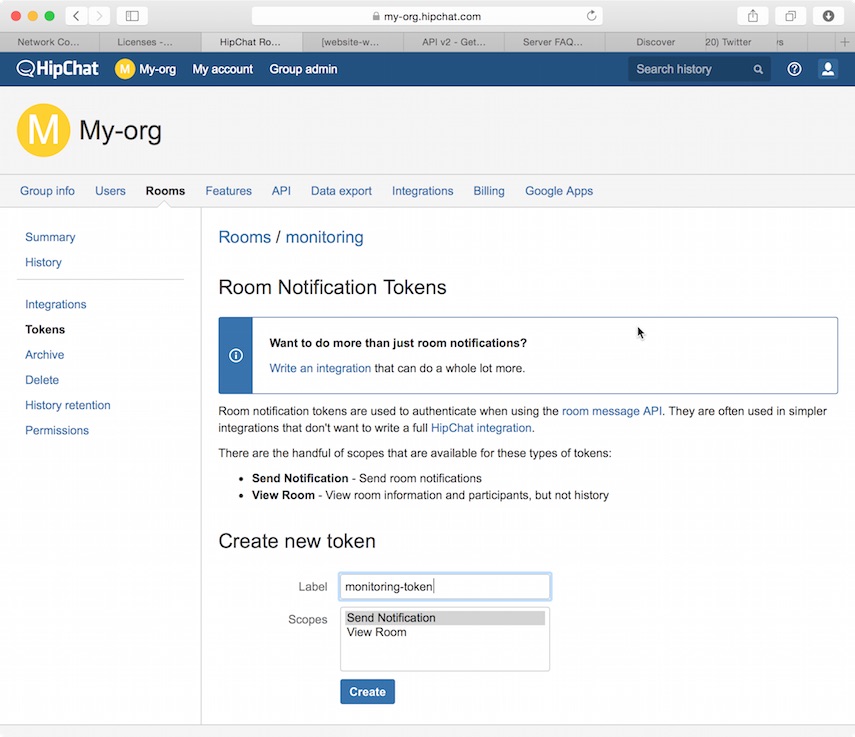
- Select the Send Notification scope.
- Click Create.
-
Copy the generated token so you can paste it into your HipChat account configuration in
elasticsearch.yml.
To configure a HipChat account that uses the integration profile:
-
Set the
typetointegration. -
Set
roomto the name of the room you want to send messages to. -
Set
auth_tokento the room-specific authentication token.
For example, the following snippet configures an account called
notify-monitoring that sends messages to the monitoring room:
bin/elasticsearch-keystore add xpack.notification.hipchat.account.notify-monitoring.secure_auth_token
xpack.notification.hipchat: account: notify-monitoring: profile: integration room: monitoring
You can also specify defaults for the message attributes:
xpack.notification.hipchat: account: notify-monitoring: profile: integration room: monitoring message: format: text color: blue notify: true
Using the HipChat user profile
editYou can use the user profile to send messages to rooms as well as individual
HipChat users. When you set an account’s profile to user, Watcher sends
messages as a particular user through the HipChat v2 API.
Before you can configure a user account, you need to:
- Add a HipChat user for Watcher. When setting the user name, keep in mind that the messages are sent on behalf of this user.
-
Create an API token for the Watcher user:
- Log in to HipChat as the Watcher user.
-
Go to
https://<hipchat-server>/account/api. For example,https://www.hipchat.com/account/api. - Confirm the user password.
-
Enter a name for the token in the Label field.
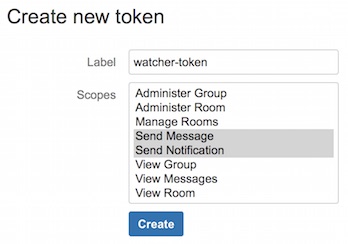
- Select the Send Notification and Send Message scopes.
- Click Create.
-
Copy the generated token so you can paste it into your HipChat account configuration in
elasticsearch.yml.
To configure a HipChat account that uses the user profile:
-
Set the
typetouser. -
Set
userto the email address associated with the Watcher user. -
Set
auth_tokento the Watcher user’s authentication token.
For example, the following configuration creates an account called
notify-monitoring that sends messages to the monitoring room:
bin/elasticsearch-keystore add xpack.notification.hipchat.account.notify-monitoring.secure_auth_token
xpack.notification.hipchat: account: notify-monitoring: profile: user
You can also specify defaults for the message attributes:
bin/elasticsearch-keystore add xpack.notification.hipchat.account.notify-monitoring.secure_auth_token
xpack.notification.hipchat: account: notify-monitoring: profile: user message: format: text color: blue notify: true
Using the HipChat v1 profile
editYou can use the v1 profile to send messages to particular rooms. When you set
an account’s profile to v1, messages are sent through HipChat’s v1
rooms/message API.
The v1 profile uses a deprecated API that is expected to be removed
by HipChat in the future.
The v1 profile only supports sending messages to rooms, it does not support
sending private messages. Use the user profile to send
private messages to HipChat users.
Before you can configure a v1 account, you need to generate a v1 API token:
- Log in to your HipChat server as a group admin.
-
Go to
https://<hipchat-server>/admin/api. For example,https://hipchat.com/admin/api. - Confirm your admin password.
-
Select the Notification type.
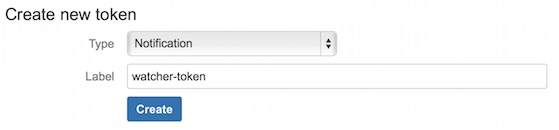
- Enter a name for the token in the Label field.
- Click Create.
-
Copy the generated token so you can paste it into your HipChat account configuration in
elasticsearch.yml.
To configure a HipChat account that uses the v1 profile:
-
Set the
typetov1. -
Set
auth_tokento the v1 authentication token you generated.
For example, the following configuration creates an account called
notify-monitoring:
bin/elasticsearch-keystore add xpack.notification.hipchat.account.notify-monitoring.secure_auth_token
xpack.notification.hipchat: account: notify-monitoring: profile: v1
You can also specify defaults for the message attributes.
xpack.notification.hipchat: account: notify-monitoring: profile: v1 message: format: text color: blue notify: true
On this page