Grant standalone Elastic Agents access to Elasticsearch
You can use either API keys (recommended) or user credentials to grant standalone Elastic Agents access to Elasticsearch resources.
API key authentication is required for Elastic Cloud Serverless. API key authentication is recommended for Elastic Stack deployments in order to avoid exposing usernames and passwords in configuration files.
The following minimal permissions are required to send logs, metrics, traces, and synthetics to Elasticsearch:
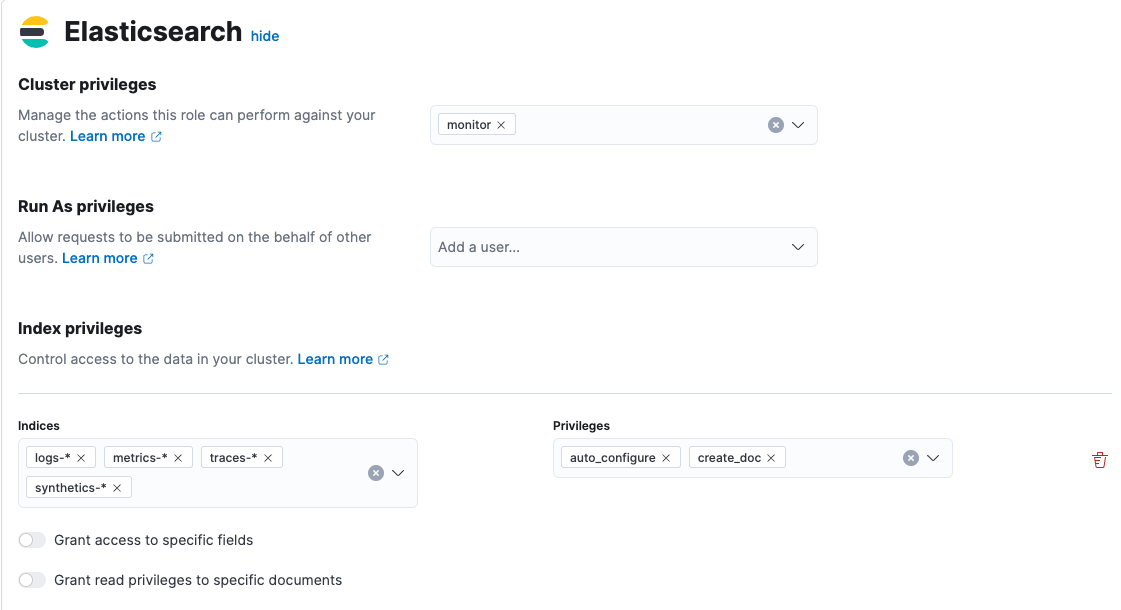
monitorcluster privilegeauto_configureandcreate_docindex privileges onlogs-*-*,metrics-*-*,traces-*-*, andsynthetics-*-*.
API keys are sent as plain-text, so they only provide security when used in combination with Transport Layer Security (TLS). Elastic Cloud provides secure, encrypted connections out of the box! For self-managed Elasticsearch clusters, refer to Public Key Infrastructure (PKI) certificates.
You can set API keys to expire at a certain time, and you can explicitly invalidate them. Any user with the manage_api_key or manage_own_api_key cluster privilege can create API keys.
For security reasons, we recommend using a unique API key per Elastic Agent. You can create as many API keys per user as necessary.
If you are using Elastic Cloud Serverless, API key authentication is required.
To create an API key for Elastic Agent:
In an Elastic Cloud or on premises environment, in Kibana navigate to Stack Management > API keys and click Create API key.
In a Serverless environment, in Kibana navigate to Project settings > Management > API keys and click Create API key.
Enter a name for your API key and select Control security privileges.
In the role descriptors box, copy and paste the following JSON. This example creates an API key with privileges for ingesting logs, metrics, traces, and synthetics:
{ "standalone_agent": { "cluster": [ "monitor" ], "indices": [ { "names": [ "logs-*-*", "metrics-*-*", "traces-*-*", "synthetics-*-*" ], "privileges": [ "auto_configure", "create_doc" ] } ] } }- Adjust this list to match the data you want to collect. For example, if you aren’t using APM or synthetics, remove
"traces-*-*"and"synthetics-*-*"from this list.
- Adjust this list to match the data you want to collect. For example, if you aren’t using APM or synthetics, remove
To set an expiration date for the API key, select Expire after time and input the lifetime of the API key in days.
Click Create API key.
You’ll see a message indicating that the key was created, along with the encoded key. By default, the API key is Base64 encoded, but that won’t work for Elastic Agent.
Click the down arrow next to Base64 and select Beats.
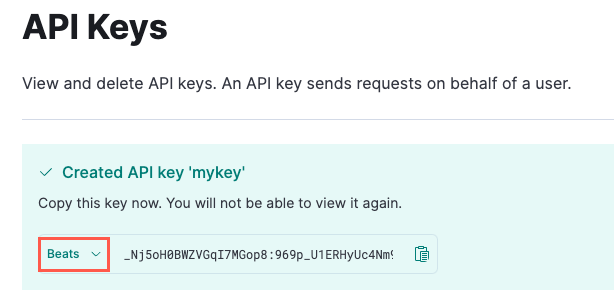
Copy the API key. You will need this for the next step, and you will not be able to view it again.
To use the API key, specify the
api_keysetting in theelastic-agent.ymlfile. For example:[...] outputs: default: type: elasticsearch hosts: - 'https://da4e3a6298c14a6683e6064ebfve9ace.us-central1.gcp.cloud.es.io:443' api_key: _Nj4oH0aWZVGqM7MGop8:349p_U1ERHyIc4Nm8_AYkw [...]- The format of this key is
<id>:<key>. Base64 encoded API keys are not currently supported in this configuration.
- The format of this key is
For more information about creating API keys in Kibana, see API Keys.
Although it’s recommended that you use an API key instead of a username and password to access Elasticsearch (and an API key is required in a Serverless environment), you can create a role with the required privileges, assign it to a user, and specify the user’s credentials in the elastic-agent.yml file.
In Kibana, go to Stack Management > Roles.
Click Create role and enter a name for the role.
In Cluster privileges, enter
monitor.In Index privileges, enter:
Create the role and assign it to a user. For more information about creating roles, refer to Kibana role management.
To use these credentials, set the username and password in the
elastic-agent.ymlfile:[...] outputs: default: type: elasticsearch hosts: - 'https://da4e3a6298c14a6683e6064ebfve9ace.us-central1.gcp.cloud.es.io:443' username: ES_USERNAME password: ES_PASSWORD [...]- For security reasons, specify a user with the minimal privileges described here. It’s recommended that you do not use the
elasticsuperuser.
- For security reasons, specify a user with the minimal privileges described here. It’s recommended that you do not use the