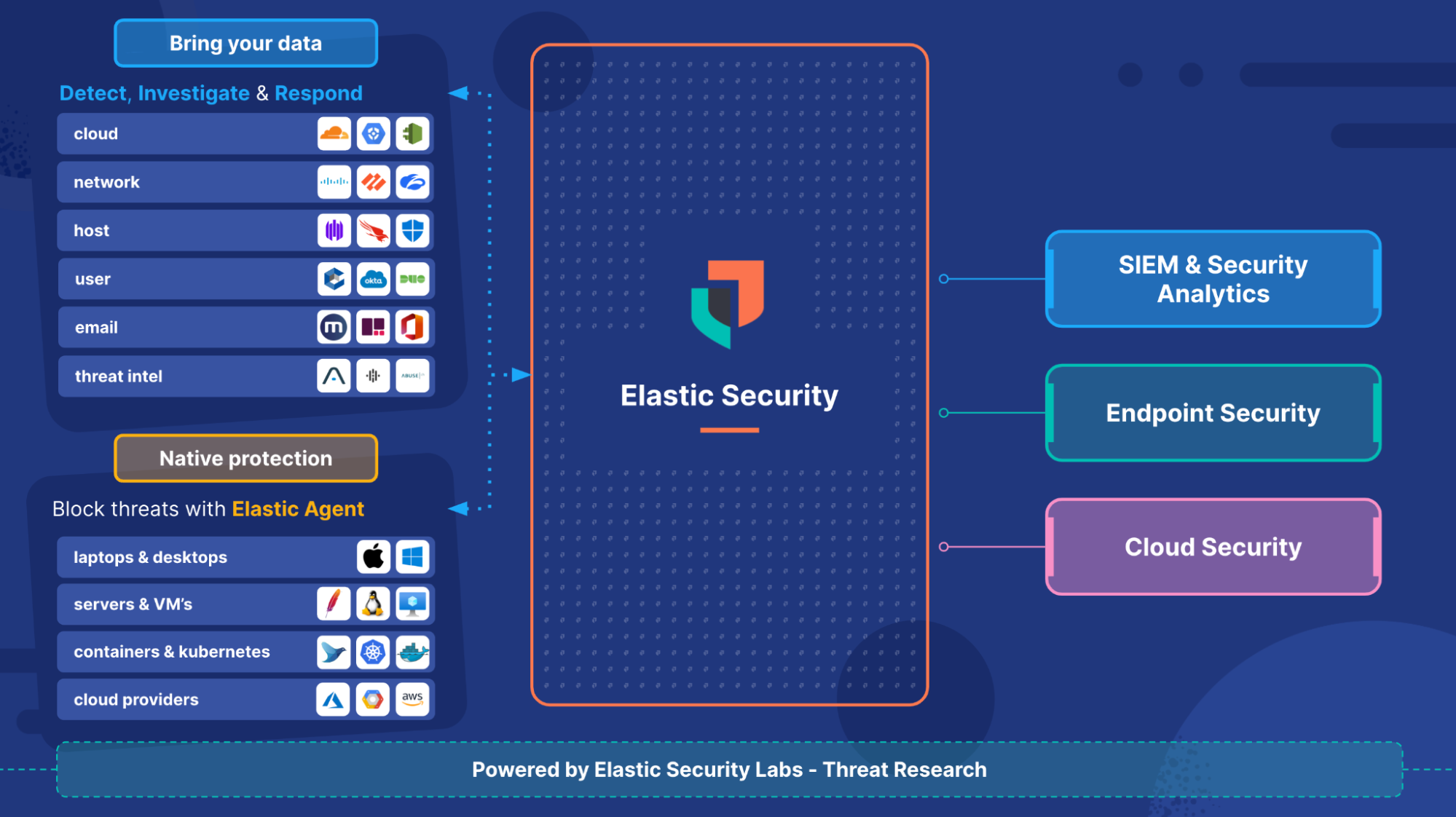
Demystifying Elastic Security for Cloud and its capabilities

Moving to the Cloud introduces unique security challenges
It's no surprise that organizations are moving to the cloud to innovate — to meet the growing demands of their customers and digital transformation. Organizations want to build applications that are fast and scalable. They want to make use of the latest cloud-native capabilities like containers, orchestrators, microservices, APIs, and declarative infrastructure.
However, this also means security in the cloud cannot be an afterthought. It needs to go hand-in-hand with application development in the cloud. When we talk to security teams, they face unique challenges when it comes to protecting the cloud, including:
- Lack of visibility: What is present in my organization’s cloud infrastructure — services, repositories, code base, infrastructure being deployed?
- Posture and vulnerabilities: What is the risk posture of my cloud assets? Are they configured properly? Are there any vulnerabilities in my runtime environment?
- Runtime security: How can I get continuous visibility and maintain immutability for my runtime infrastructure? What are the events and activities in my cloud and container environment?
- Automation and integrations: How can I consolidate events and logs from multiple cloud environments into a single place? How can I get my security teams and devops teams to collaborate to protect cloud-native applications?
An integrated approach combining security analytics with CNAPP
As noted in the Cloud Security March 2023 announcement last week, “Elastic Security is the only security analytics solution that is a complete Cloud Native Application Protection Platform (CNAPP) for AWS.”
I want to provide a little more context into why this integrated approach is essential to address cloud security challenges.
Much like any industry, cloud security is heavily fragmented, with many acronyms (KSPM, CSPM, CWP) and buzzwords for security teams to navigate through the noise and understand how to secure their infrastructure. An integrated approach that is bringing these disparate security and protection capabilities into a single platform is called Cloud Native Application Protection Platform (CNAPP).
According to Gartner, “CNAPP offerings allow an organization to use a single integrated offering to identify risk across the entire life cycle and disparate elements of a cloud-native application.”
Elastic’s CNAPP features and workflows are built on top of our strong security analytics and SIEM capabilities. The combination provides a unified view of risk in the cloud environment all the way from posture to runtime and correlates that with 100+ detection rules catered toward cloud and container environments like privilege escalation, container escape, and more.
Let's take an example scenario: You are reviewing the Elastic Cloud Posture Dashboard and you come across a new high risk misconfiguration — Root MFA is disabled. This is potentially high risk because MFA needs to be enabled for your root accounts. As you dig into this incident further, not only can you dive into the details of how to fix this high risk misconfiguration, but you can also correlate this data with AWS CloudTrail logs or AWS Security Hub events by quickly searching for the resource type to investigate who was the user behind the failed misconfiguration.
Further, you can move laterally to understand what else this user is up to — do they have access to the running containers? Have they attempted any other privilege escalations or malicious activities within the runtime environments? You can then use the flexible policies to prevent the user from making any further modifications within the entire container filesystem. Further, you can escalate this issue and open a case for remediation, reducing the potential of human error from pivoting between numerous disconnected systems.
Traditionally, if your SIEM or security analytics solution and cloud security solution are separate, it would add complexity to the investigation, as some of them can be answered from data in your SIEM, and some from the cloud security platform. There would be no easy way to correlate the data between the platforms, or it could be very expensive if you had to transfer data/alerts between one platform or another.
However, with Elastic’s resource based pricing model, we are able to offer SIEM, Endpoint, and Cloud Security use cases as a unified integrated solution where customers are charged based on data consumption and not as separate solutions.
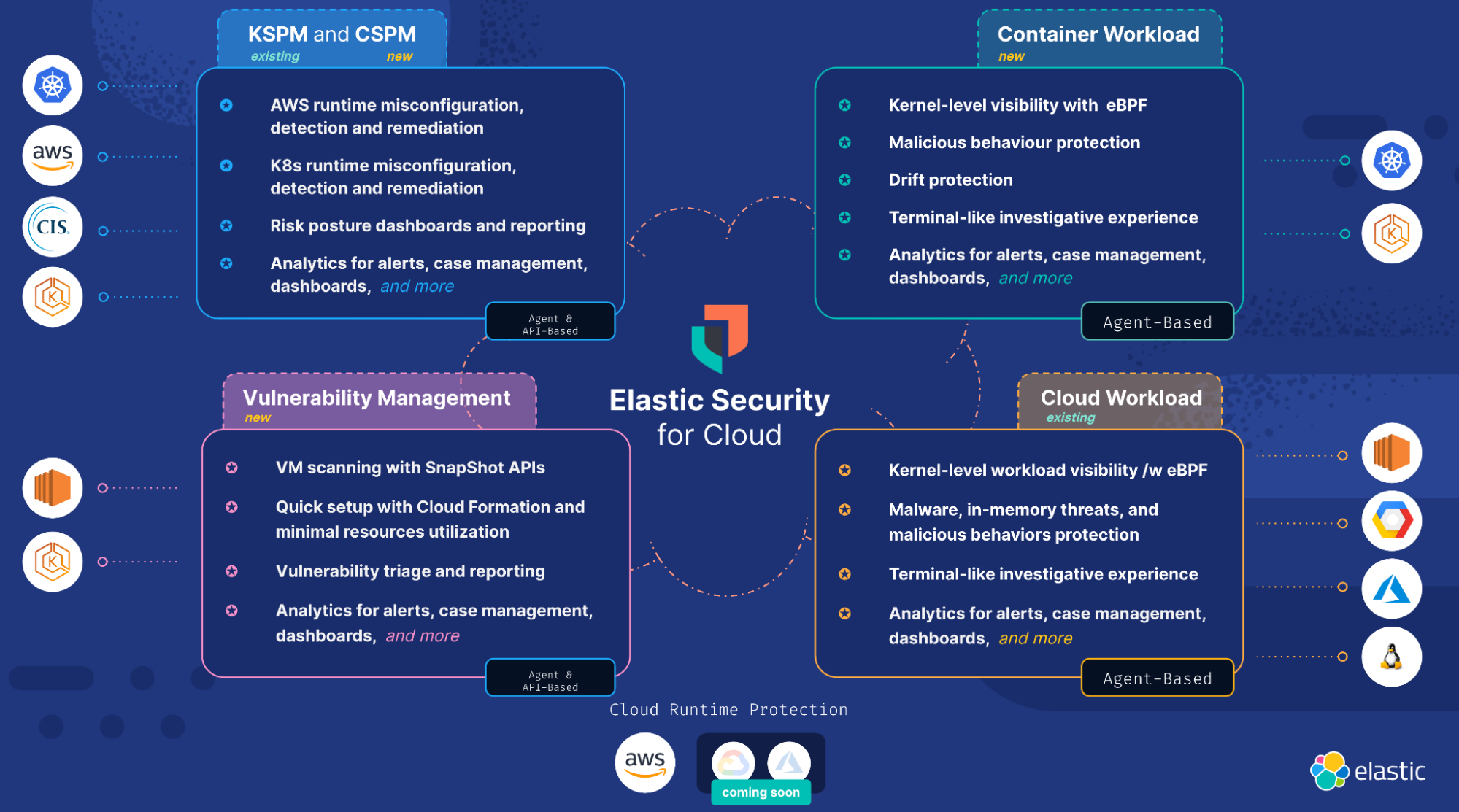
The 4 tenets of cloud native protection
In order to protect the full lifecycle of cloud native applications, Elastic’s Cloud Security capability has four important pillars:
1. Cloud and Kubernetes Security Posture Management (CSPM and KSPM)
Elastic’s CSPM and KSPM features continuously check the organization’s AWS cloud services like S3, CloudTrail, etc. and Kubernetes clusters like EKS. CSPM then compares the organization’s cloud configurations against CIS benchmarks. The results of the evaluation are available in the Elastic platform, where they can prioritize their top failed configurations and sort and search by fields like resource type, id, and rule name. Organizations also get step-by-step remediation instructions to fix the configuration issues and improve their security posture. We also provide a Risk and Posture dashboard, which provides an overall executive dashboard that is aggregated and broken down across multiple AWS accounts.
Learn more about getting started with CSPM.
Supported today: CIS benchmarks for AWS, EKS, Native or Vanilla Kubernetes
2. Cloud Vulnerability Management
Elastic's Vulnerability Management uncovers vulnerabilities in the customers' AWS infrastructure. We are leveraging open source technologies that make use of SnapShot APIs so that the resource utilization to perform the vulnerability scanning is minimum in customers' environments. This architecture choice keeps the sensitive customer IP like VM and container images in the customer's environment, only reporting back findings to the Elastic Security solution. We drastically reduced the time to onboard and set up a new integration like Elastic Vulnerability Management by providing an AWS CloudFormation template. Further, we are providing out of the box vulnerability triaging workflows, which allows users to view a list of vulnerabilities, prioritized by exploitability and severity. We also provide detailed information about the vulnerability and the fix version from the NVD database. The beginning of our vulnerability journey will be launched in the upcoming Elastic releases, with full container scanning and SBOM for vulnerability management to follow soon!
3. Cloud Workload Protection
Building on the expertise in Linux kernel and eBPF-based instrumentation, workload runtime protection capabilities launched in the 8.5 release. Cloud Workload Protection enables deep visibility into AWS EC2 workloads by monitoring and instrumenting key runtime security signals like process, file, and network. This is coupled with prevention, detection, and response capabilities delivered via the Elastic Agent. As Gartner noted in the latest CNAPP Market Guide, while agentless scanning techniques have become popular, the in-workload agent approach is a core capability that provides the best prevention and response. Elastic truly differentiates in this capability by providing a powerful terminal-like investigative experience that can be highly customized to the organization's workloads’ data filtering requirements.
Generally Available from 8.5 release
Learn more about getting started with Cloud Workload.
Supported today: Any Linux workload officially supported by Elastic Agent
4. Container Workload Protection
With the rising popularity of containers and Kubernetes, Elastic Container Workload Protection provides Amazon EKS users with deep kernel-level visibility via eBPF into container and Kubernetes runtime signals and metadata. Because of the immutable nature of container environments, devops teams are looking for ways to prevent any drift in their runtime container images. Elastic is launching a powerful feature that allows organizations to write extremely flexible policies around the expected behavior in the container. Any deviation from the expected behavior will be blocked from executing in runtime or alerted in the SIEM, thereby providing powerful prevention and detection capabilities in the container. Container Runtime Workload Protection is set to launch in upcoming Elastic releases.
The below image provides a snapshot view of the four tenets of Elastic Security for Cloud.
Try it out
Existing Elastic Cloud customers can access many of these features directly from the Elastic Cloud console. If you’re new to Elastic, take a look at our Quick Start guides (bite-sized training videos to get you started quickly) or our free fundamentals training courses. You can always get started for free with a free 14-day trial of Elastic Cloud, check out siem pricing, or download the self-managed version of the Elastic Stack for free.
Learn more about Elastic Security for Cloud, and check out our introductory webinar.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.

