Introducing 7.16.2 and 6.8.22 releases of Elasticsearch and Logstash to upgrade Apache Log4j2

We are pleased to announce new versions of Elasticsearch and Logstash, 7.16.2 and 6.8.22, to upgrade to the latest release of Apache Log4j and address false positive concerns with some vulnerability scanners. Elastic also maintains ongoing updates via our advisory to ensure our Elastic customers and our communities can stay up-to-date on the latest developments.
December 10th started with the public disclosure of the Apache Log4j vulnerability - CVE-2021-44228 affecting the popular open source logging framework adopted by several Java based custom and commercial applications. This vulnerability, affecting versions 2.0-beta9 through 2.14.1 of Log4j2, and is already being exploited by nation state attackers and ransomware groups, such as APT35 and Hafnium. Research by Google using Open Source Insights estimates that over 35,000 packages (over 8% of Maven Central repository) have been impacted by the recently disclosed vulnerabilities, as of December 16th.
Apache Log4j released a fix to this initial vulnerability in Log4j version 2.15.0. However the fix was incomplete and resulted in a potential DoS and data exfiltration vulnerability, logged as CVE-2021-45046. This new vulnerability was fixed in Log4j2 version 2.16.0. However, version 2.16.0 itself was also found vulnerable to another DoS vulnerability, leading to a new CVE-2021-45105, and the eventual release of Apache Log4j2 version 2.17.0.
In our advisory post, we identify several mitigations that are effective on versions of Elasticsearch and Logstash even when using a vulnerable version of Log4j. Elasticsearch and Logstash versions 7.16.1 and 6.8.21 also fully mitigate CVE-2021-44228 and CVE-2021-45046. Despite these versions providing full protection against all known CVEs, they may trigger false positive alerts in vulnerability scanners that look at only the version of the Log4j dependency. We understand that while that may not lead to risk, some deployments and customers may still be concerned about compliance implications.
Introducing Elasticsearch 7.16.2 and Logstash 6.8.22
Today, we’re pleased to announce the availability of new versions of Elasticsearch and Logstash, 7.16.2 and 6.8.22 respectively, which upgrades Apache Log4j2 to version 2.17.0. We also retain the mitigations delivered in 7.16.1 and 6.8.21. The sum of mitigations against Log4j mitigations delivered in 7.16.2 and 6.8.22 include:
- Log4j upgraded to version 2.17.0
- JndiLookup class is completely removed to eliminate the attack surface area provided by the JNDI Lookup feature and associated risk of similar vulnerabilities
- log4j2.formatMsgNoLookups=true is set to disable one of the vulnerable features
Please refer to the Elastic advisory to stay up-to-date on the latest on all Elastic products and related mitigations.
While patching systems represents the best approach to stay ahead of these vulnerabilities, there may be instances where patching is delayed due to dependencies or unmanaged/rogue systems lurking within the environments. Elastic Security users can also leverage the power of detection and event correlation, using Elastic Endpoint, Auditbeat, and threat hunting capabilities, to identify any active exploitation of the Log4j2 vulnerability in the environment. Refer to Elastic’s blog on this topic to learn how Elastic can help.
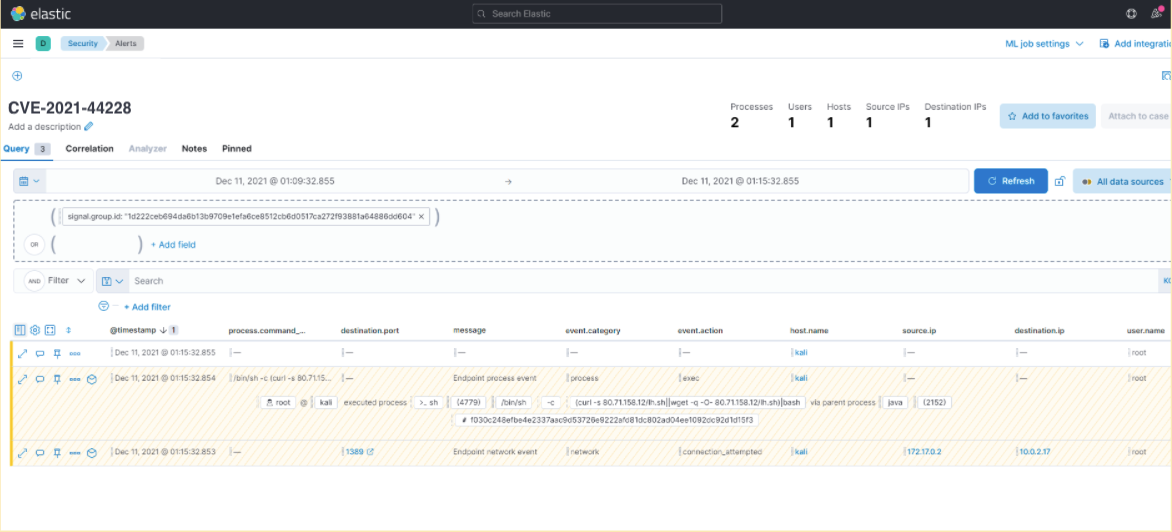
Existing Elastic Security can access these capabilities within the product. If you’re new to Elastic Security, take a look at our Quick Start guides (bite-sized training videos to get you started quickly) or our free fundamentals training courses. Refer to the documentation online to see how you can upgrade your Elasticsearch and Logstash deployments. You can always get started with a free 14-day trial of Elastic Cloud. Or download the self-managed version of the Elastic Stack for free.
Reference Material
https://logging.apache.org/log4j/2.x/security.html
https://security.googleblog.com/2021/12/understanding-impact-of-apache-log4j.html
https://thehackernews.com/2021/12/hackers-begin-exploiting-second-log4j.html
https://www.cert.govt.nz/it-specialists/advisories/log4j-rce-0-day-actively-exploited/

