Elastic 8.4 introduces SOAR for modern security operations

New in Elastic Security 8.4, Elastic introduces SOAR capabilities to empower modern security operation centers (SOCs) to streamline analyst operations.
Modern SOCs are running headlong into numerous challenges. While the visibility and impact of security operations has become a board-level issue, the resources available to those security teams are still limited. Data is exploding, and correspondingly, the responsibility of the security team has been increasing. Teams are tasked with protecting a perimeter-less, distributed environment while also assessing the risk of SaaS providers and shared services.
To address these challenges, many organizations have begun unifying teams with similar goals in order to share best practices and reduce the skills gap. The walls between observability (those tasked with the operational efficiency and visibility of business applications) and security (those tasked with the assurance and protections of business applications) have found their worlds colliding — now sharing data, workflows, and team expertise. Elastic Security 8.4 delivers the tools that analysts need to streamline their operations workflows to speed up threat hunting and remediation.
What’s new in Elastic Security 8.4?
SOAR for the modern SOC is a force multiplier
Recently, Elastic re-doubled our pledge to open and transparent security, and now, in Elastic Security 8.4, we expand our response capabilities to continue to streamline analyst operations.
The enhanced workflows in Elastic 8.4 combine native response capabilities and configurable alert and case actions with bidirectional integrations with security orchestration, automation, and response (SOAR) vendors. Users can now enjoy integrations with ServiceNow, Swimlane, and Tines, as well as new partnerships with D3 and Torq.
Elastic’s unique approach to SOAR is powered by Elastic Agent. This technology, included with the Elastic Security solution, empowers single-click use case growth across hundreds of data sources as well as management of our endpoint and cloud security protection software. Elastic Agent powers native remediation capabilities accessible to all users, ensuring anyone can begin their SOAR journey without the need to purchase additional technologies.
As use cases for remediation grow and teams require advanced orchestration controls, users can utilize the customizable orchestration capabilities within Elastic Security, or the one-click integrations with other leading SOAR providers. This user-first approach grows with the needs of an organization, offering simplicity and consolidation for all users without enforcing vendor lock-in.
This scale-as-you-grow model enables clients to simplify automation and orchestration workflows and processes in their existing ecosystem by combining native, one-click actions and orchestrations with an API-first approach for first- and third-party integrations. Analysts can now use Elastic Security for their SOAR needs, leverage any of our partner SOAR vendors to extend their orchestration capabilities, or completely customize the response experience with Elastic actions and our API-first approach to all capabilities.
Our open vision for SOAR mirrors our approach to many other technologies, like Elastic Security for Endpoint, which delivers endpoint prevention and detection and powers extended detection and response (XDR). Users deserve choice, so we also offer rich integrations with other endpoint vendors, like CrowdStrike, Microsoft Defender, and SentinelOne. We do what is best for our community, without hesitating to integrate with technologies offering overlapping capabilities.
Many organizations are just getting started with security orchestration, automation, and response. Our native SOAR capabilities help organizations of every kind excel at incident management, and our tightly integrated SOAR partners help them accomplish even more.
Purpose-built response automation interface
A core workflow for planning, building, and executing your response plan is a key component of SOAR. Elastic Security 8.4 introduces a terminal-like interface that enables practitioners to view and invoke response actions quickly, accelerating response. It is accessible just one click away from key analyst workflows, minimizing mean time to respond (MTTR).
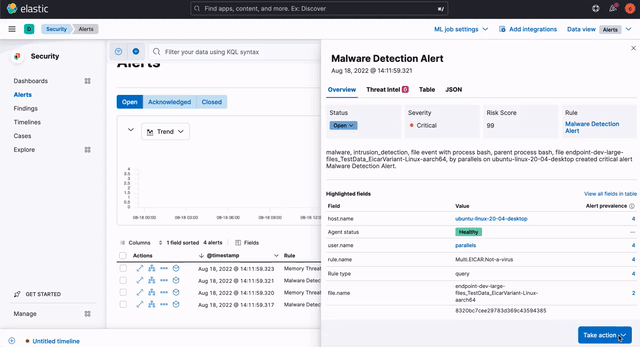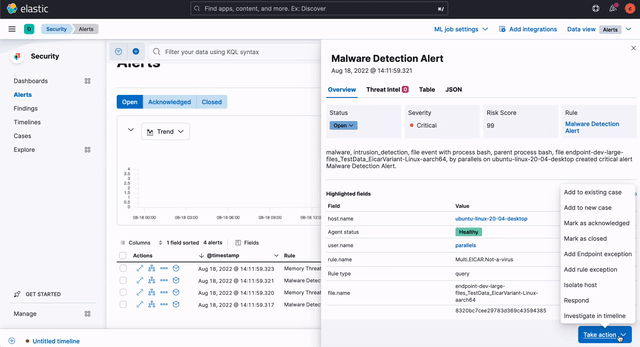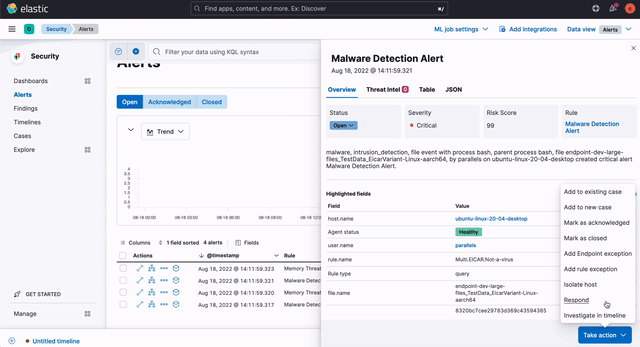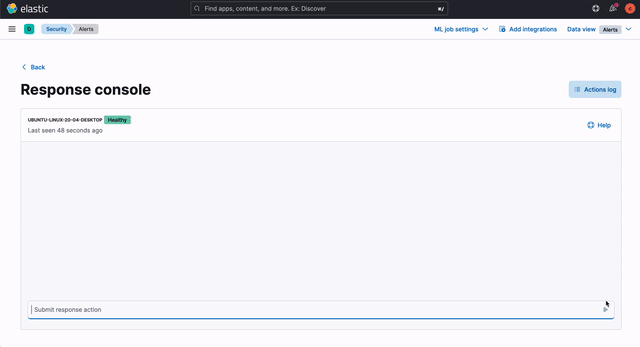
Host isolation — an existing action — arms analysts to quickly disable network connectivity on infected systems, preventing lateral movement while still allowing responders to triage and investigate. This cross-OS response capability (Linux, macOS, and Windows) is joined by three process operations added in version 8.4:
- Enumerate currently running processes
- Suspend process
- Kill process
A new audit interface provides a full record of incident response activity, supporting tight controls and reporting.
These capabilities are generally available (GA) in 8.4 and accessible in our Enterprise subscription tier on self-managed and cloud deployments. Later releases will further expand available response actions.
Self-healing for Windows hosts
Returning an attacked host to a known-good state is another core component of SOAR.
Elastic Security 8.4 introduces self-healing, an automated remediation feature that erases attack artifacts from a system. Now, when malicious activity is identified on a host, self-cleaning automatically returns the host to its pre-attack state by reverting changes implemented during the attack. In this release, we focused on reverting file changes and addressing dropped/created executables, with further remediation functionality coming soon.
Self-healing mode on Windows systems is GA in 8.4 and accessible in our Platinum subscription tier on self-managed and cloud deployments.
Automated alert insights
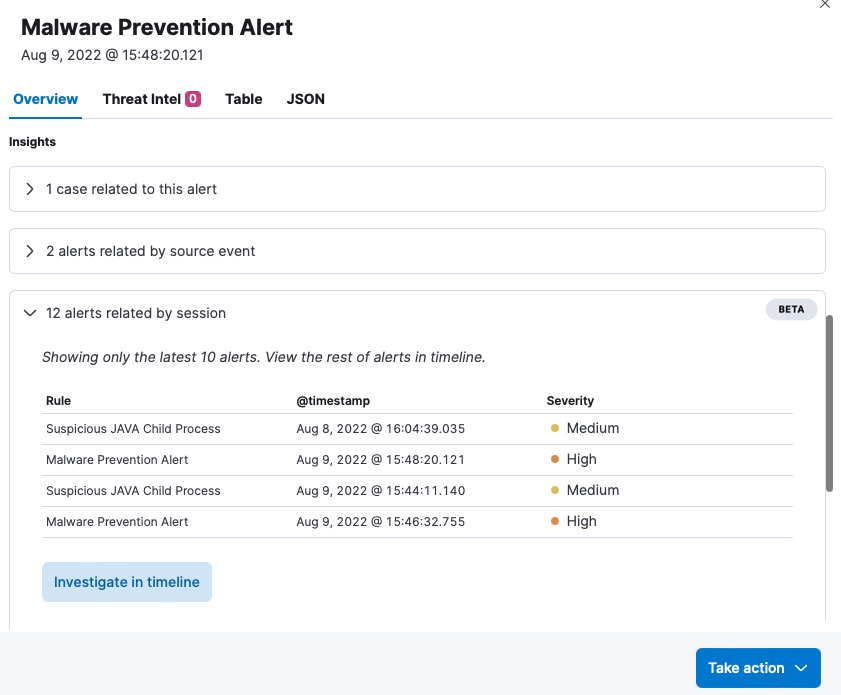
Security analysts expend significant energy connecting the dots between one alert and the other myriad alerts in their environment. Alert fatigue, a combination of alert volume and false alerts, coupled with shortage in trained professionals is a real problem for many organizations. Alert insights, another new capability, guides analysts within their workflow to relevant alerts and cases, accelerating impact assessment and optimizing analyst workflow and experience. At a glance, analysts can view the following:
- Has this alert ever been in a case before?
- Is this alert related to other alerts by key indicators of compromise?
- Elastic-unique groupings based on related alerts in the same user session
In addition, one-click pivots into Elastic’s drag and drop investigative experience, allowing for easy threat hunting and additional analysis.
Alert insights is GA in 8.4 and accessible in the Platinum subscription tier.
Expanded SOAR partnerships
SOAR powers Elastic Security with both native and third-party SOAR integration. In response to customer feedback, new connectors from D3 Security and Torq are forthcoming, further boosting our leadership in third-party SOAR integrations. The connectors will provide turnkey forwarding of Elastic detections, enabling security orchestration, automation, and response.
With D3 and Elastic’s partnership, users of our platforms can automatically escalate enriched alerts and trigger workflow actions with ease via well-defined parameters in both the Elastic and the D3 NextGen SOAR user interfaces. With its codeless automation, cross-stack orchestration, and unmatched scalability, D3 is well-positioned to keep SOC analysts focused on real threats by freeing up the time normally spent on false positives and repetitive tasks.
Amardeep Dhingra, Senior Partner Marketing Manager, D3 Security
We're thrilled to partner with Elastic on a shared mission to help today's security operations teams move at cloud speed and scale. With Elastic's comprehensive detection of advanced threats and Torq's no-code automation, security teams can accelerate response and remediation, delivering unprecedented levels of protection.
Eldad Livni, Co-Founder and Chief Innovation Officer, Torq
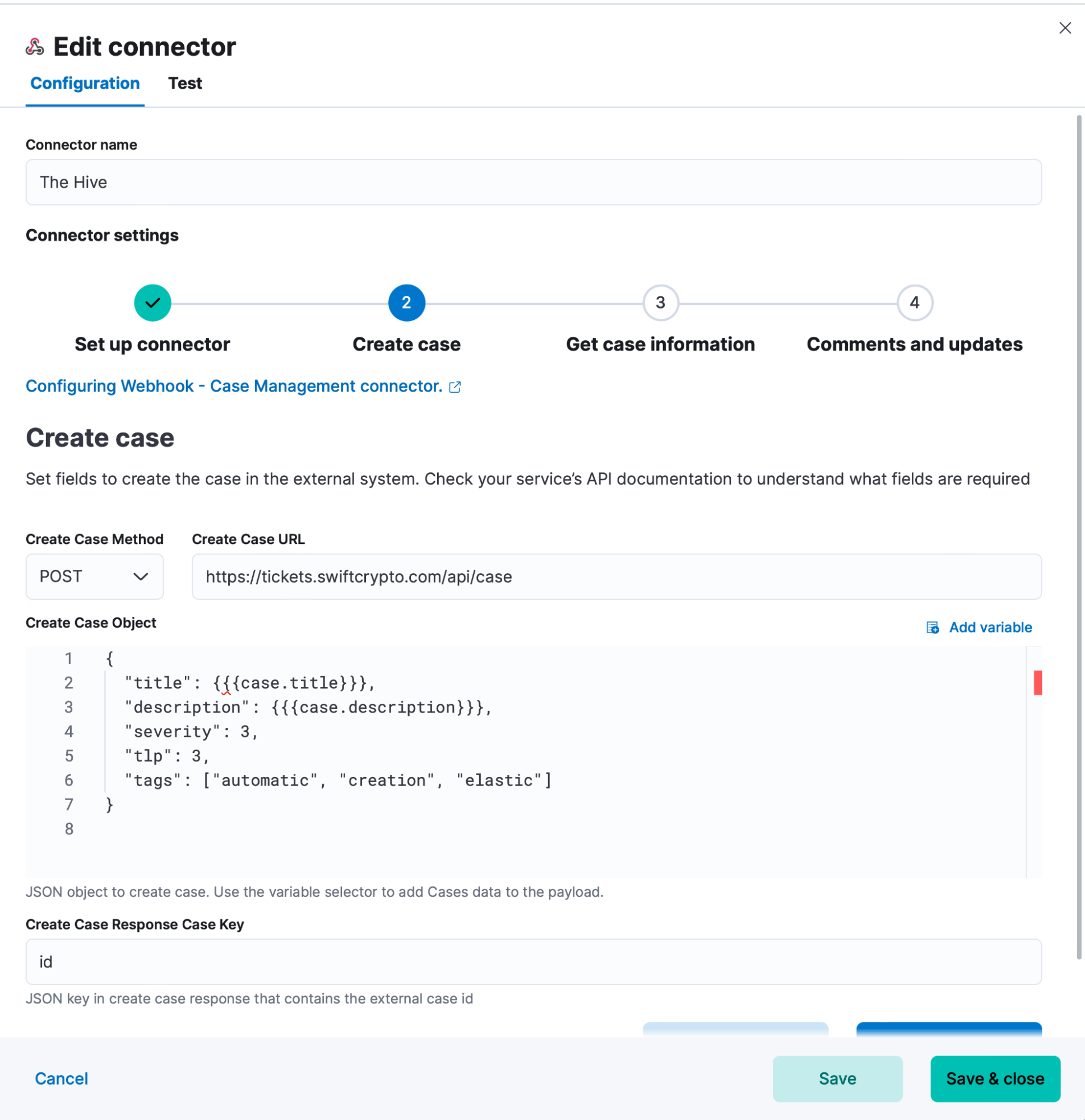
Enhanced customizable orchestration
For any vendors or actions beyond our broad set of integrations, users can build automations with our purpose-built interface. Here, any API call can be built as a connector and then applied as an orchestrated action. An open community of connectors was recently published to provide a jumpstart to any custom controls users require. In Elastic 8.4, we’ve expanded this functionality from alerts to include case actions as well.
What else?
In addition to introducing SOAR capabilities, Elastic 8.4 includes several detection engineering enhancements, including:
- Easy detection of new entities appearing in log data: We’ve introduced a new rule type that alerts users when an unfamiliar term is found in their data sources. When a document is ingested and contains a field value that is different from what has appeared over a specified window of time (i.e. last 7 days), this rule will generate an alert. The appearance of a new host, ip address, or username might indicate an environmental change that could be worthy of examination.
- Rule exceptions extended with Wildcard support: Increased flexibility/easier configuration for exceptions. A new operator (matches) has been introduced when configuring exceptions, allowing users to leverage wildcard expressions (as well as ‘?’ for single character matching).
- Enabling data collection from leading security products: Elastic 8.4 introduces several new one-click integrations in Elastic Agent to easily onboard, analyze, and visualize data from security data sources. New integrations include Azure Firewall, Cisco Identity Service Engine, Cisco Secure Email Gateway, Citrix Web Application Firewall, Mimecast, Proofpoint TAP, and SentinelOne. Our Palo Alto next-gen firewall integration has also been updated to include support for PAN-OS 10.x and all log types.
For a complete list, please refer to our detailed release notes.
Try it out
Existing Elastic Cloud customers can access many of these features directly from the Elastic Cloud console. If you’re new to Elastic, take a look at our Quick Start guides (bite-sized training videos to get you started quickly) or our free fundamentals training courses. You can always get started for free with a free 14-day trial of Elastic Cloud. Or download the self-managed version of the Elastic Stack for free.
Read about these capabilities and more in the Elastic Security Solution 8.4.0 release notes, and other Elastic Stack highlights in the Elastic 8.4 announcement post.
Check out the SOAR Overview Guide.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.


