Elastic Security 8.7 helps security practitioners eliminate alert fatigue, drive MTTR lower, and better secure cloud environments

Elastic Security 8.7 helps security practitioners eliminate alert fatigue, reduce MTTR, and better secure cloud environments through integrated SIEM, cloud security, and endpoint security. This release includes the following new features that bring efficacy and efficiency to the modern security operations center (SOC):
- New data source integrations
- Expanded prebuilt detection content
- Improved detection and response
Security operations centers use SIEM, EDR, and cloud security solutions to detect malicious activity by analyzing their security-related events and information . . . but there are a number of distinct operations they must perform in order to do this effectively.
Their teams must ingest relevant security information, detect threat activity with rules and other analytics, triage the alerts generated by the rules, investigate activity to determine root cause, escalate to other team members, and, finally, respond to remediate the threat. Phew! Through streamlined workflows and automation, Elastic Security 8.7 helps significantly reduce the time needed to detect and respond to these threats.
Advancements in the release empower practitioners to:
- Detect more threats via automated rules and analytics
- Streamline the alert triage process
- Automate the investigation experience
- Expedite the response and remediation of threats
What else is new in Elastic 8.7? Check out the 8.7 announcement post to learn more >>
More security data source integrations
The 8.7 release includes further expansion of its set of one-click Elastic Agent integrations for popular security-relevant sources, such as AWS GuardDuty, Delenia Secret Server, Forcepoint Web Security, Forgerock, Lyve Cloud, Rapid7 Threat Command, Tanium Connect, and Tenable.io. These integrations help security teams integrate relevant security information and events into Elastic Security for SIEM.
The 8.7 release also introduces new ingest health dashboards, providing deep visibility into data ingestion health and performance. These dashboards enable security teams to quickly identify and remediate issues relating to Elastic Agent, integrations, and ingest pipelines, ensuring continuous ingestion of vital security data.
Eliminate alert fatigue
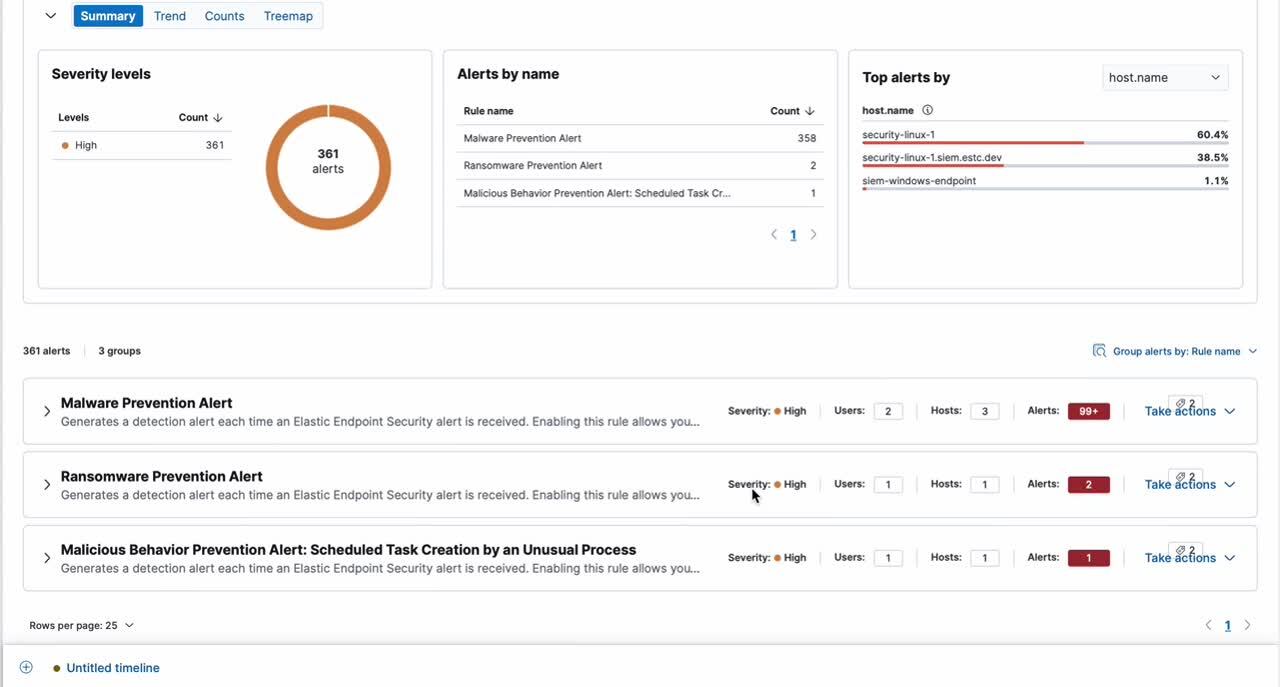
Security practitioners are often met with an alerts page with the helpless feeling of “where do I start?” In 8.7, Elastic Security welcomes charts and grouping capabilities to not only organize your alerts, but prioritize them.
Firstly, before looking at a table of alerts, let’s visualize the most important questions. We now provide a summary panel that outlines severities and alert distributions across rules, hosts, users, and more. We even provide a compact summary when minimizing the charts!
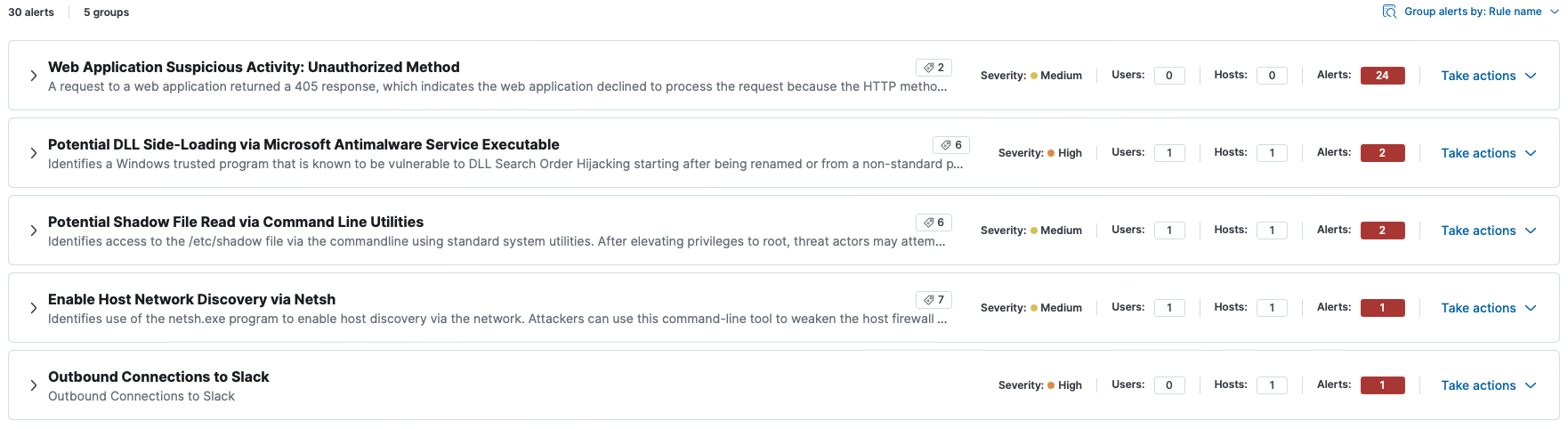
Now you don't have to interact with a table of seemingly endless rows of alerts. With alert grouping, you can select any field to collapse each unique value into a single group. By creating fewer actionable alert categories, this feature helps analysts avoid feeling overwhelmed. And to speed up your processes further, you can take bulk actions for each group, like closing all addressed alerts.
Reduce MTTR
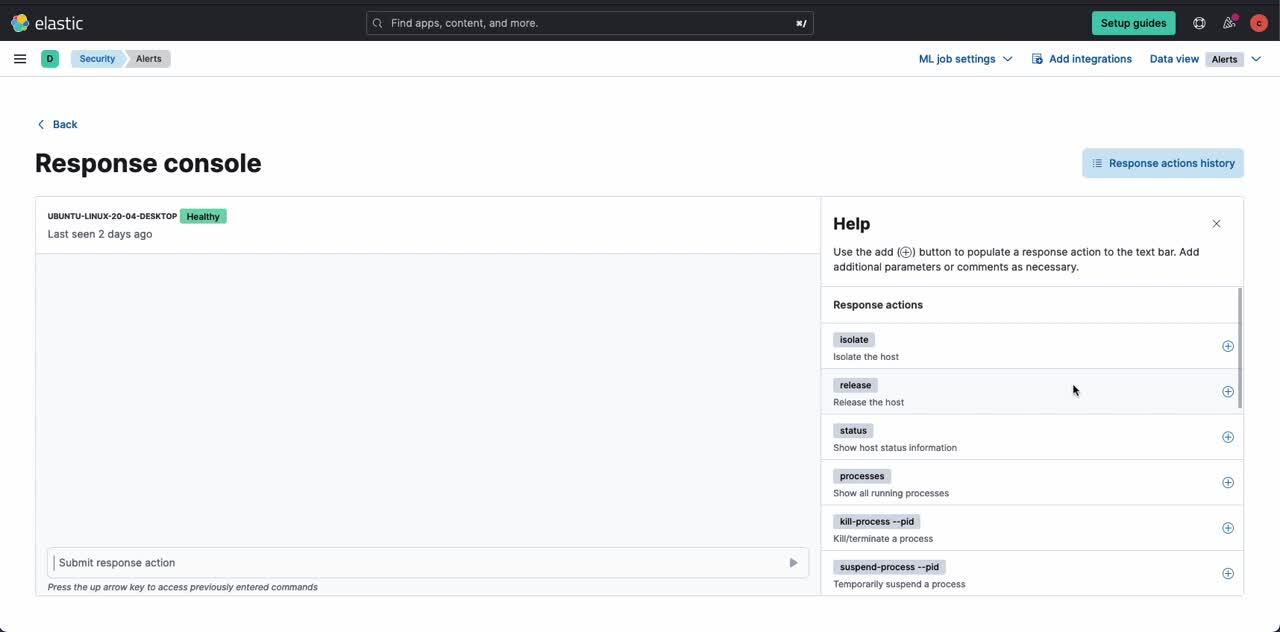
When an endpoint is compromised, it’s critical to gather as much information as quickly as possible about the incident. Elastic Security 8.7 delivers analysts the ability to easily and effectively accelerate response by further expanding upon the capabilities within the response console.
Joining the existing host isolation action and process operations is the getfile action, whereby teams can remotely retrieve files from hosts running the Elastic Defend integration. With just a few clicks in the terminal-like interface, it can easily collect malware files, forensic evidence, and other critical artifacts from hosts for further analysis to better identify and understand security threats. This capability is generally available in 8.7 and accessible via the Elastic Security Enterprise subscription tier on both self-managed and cloud deployments.
Continuously identify and remediate configuration risks in cloud environments with CSPM
Navigating cloud environments can be a daunting task. With countless settings, policies, and interconnected services, it's no wonder that many organizations are struggling to understand and securely configure their cloud infrastructure. In fact, according to a recent Elastic study, nearly half (49%) of organizations adopting cloud-native technologies anticipate that misconfigurations will be the root cause of breaches over the next two years.
With the Cloud security posture management (CSPM) feature, Elastic enables customers to maintain the confidentiality, integrity, and availability of their data in the cloud. CSPM continuously discovers and evaluates the cloud services you're leveraging against hardening guidelines, like the Center for Information Security (CIS) AWS benchmarks, to identify configuration risks like publicly exposed storage buckets, Identity & Access Management (IAM) users without multi-factor authentication (MFA), and networking objects that allow ingress to remote server administration ports.
Once the CSPM feature has discovered and assessed your cloud infrastructure's security posture, an executive security posture dashboard is provided, giving you a bird's eye view of your overall security posture.
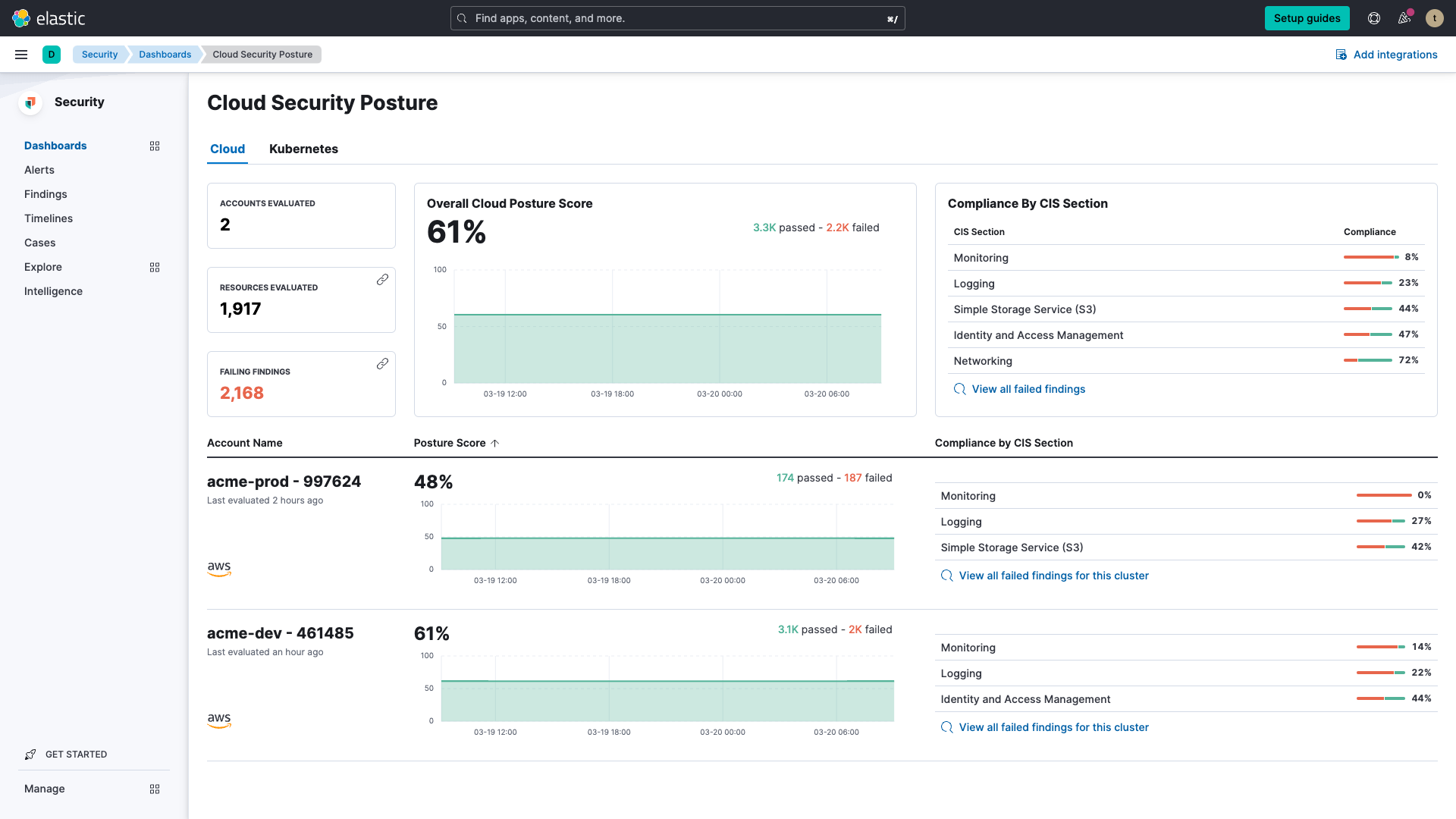
But that's not all! For every security misconfiguration detected in your environment, the CSPM feature also provides step-by-step remediation instructions to guide you along the way in improving your overall cloud security posture. Armed with this information, you can proactively identify, prioritize, and remediate configuration risks to your organization.
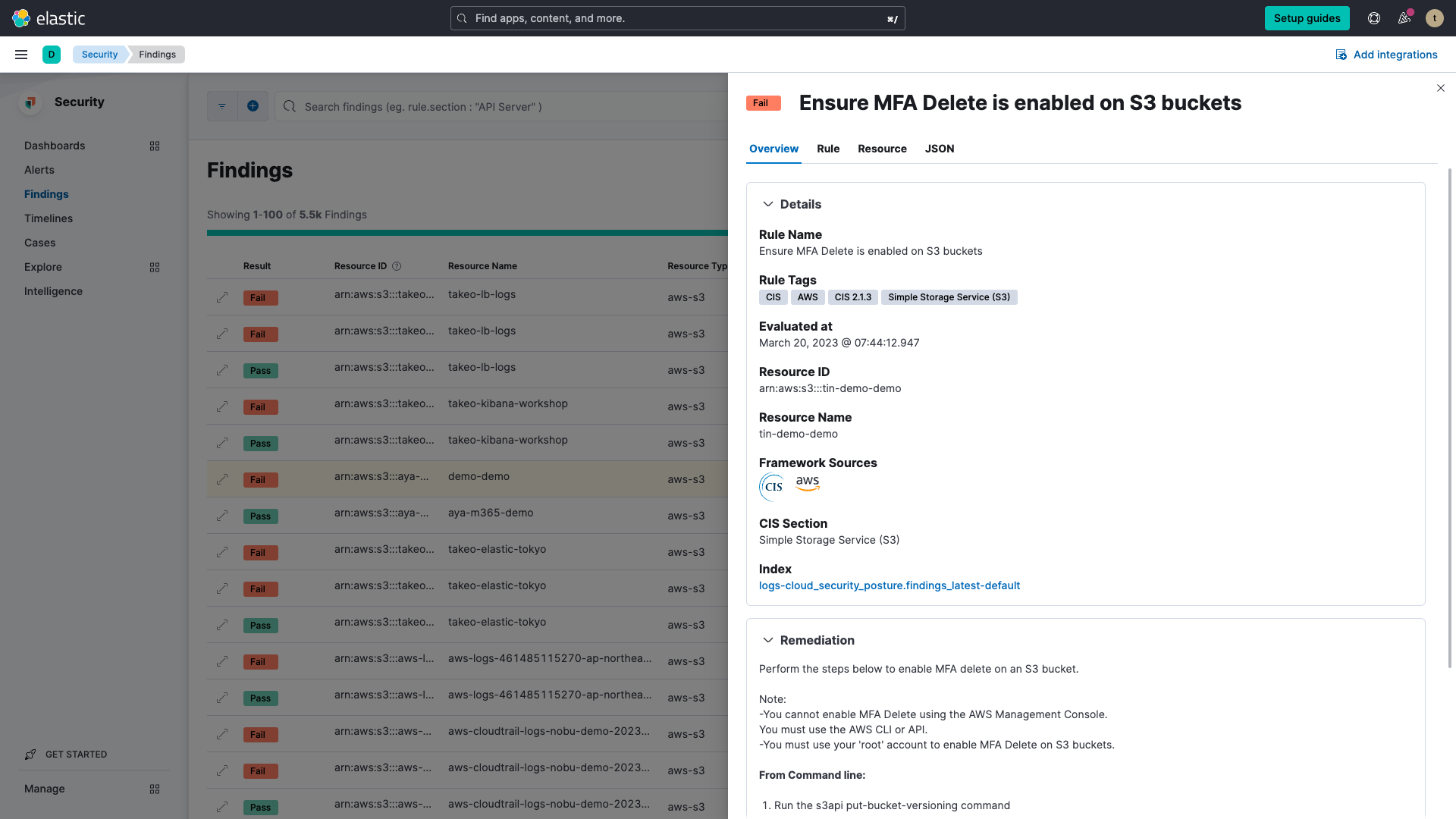
The CSPM feature within Elastic Security for Cloud will be pivotal in helping users harden their cloud environments and minimize their exposed attack surface. This capability is available in beta in 8.7 and accessible in our Elastic Security Standard subscription tier on cloud deployments and in our Enterprise subscription tier in self-managed.
Follow this step-by-step getting started guide to begin evaluating your cloud security posture.
Try it out
Read about these capabilities and more in the release notes.
Existing Elastic Cloud customers can access many of these features directly from the Elastic Cloud console. Not taking advantage of Elastic on cloud? Start a free trial.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.

